Let's Encrypt
A Free, Automated and Open Certificate Authority

Outline
-
Introduction
-
Let's Encrypt Design
-
Let's Encrypt Implementation
-
Conclusion
Introduction
- Enterprises need high-level security : e-Business applications, online trading, banking and web service-based business process automation.
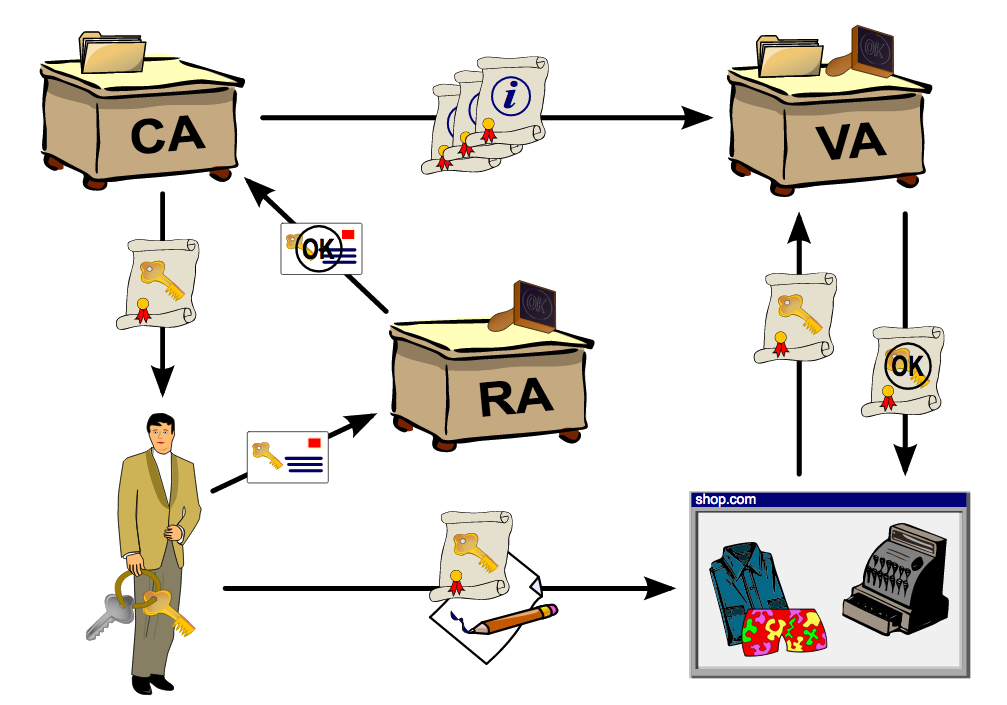
- Public Key Infrastructure (PKI) is one of security technology.
- PKI is a system involving digital certificates, certification authorities (CAs), and registration authorities (RAs) that verify and authenticate the validity of certificate from each party involved in an electronic transaction.
Introduction (cont.)
The biggest obstacle to Hypertext Transport Protocol Secure (HTTPS) deployment :
- complexity
- bureaucracy
-
cost
Introduction (cont.)
In 2015, Electronic Frontier Foundation released Let’s Encrypt.
- automates the certificate management on servers
- provides simple tools to manage HTTPS
- do not need email validation and complex configuration
- automatically manages the renewal process
-
free of charge
Let's Encrypt Design
Let’s Encrypt aims to automatically configure an HTTPS server with trusted certificate.
This is done by executing an open source certificate management agent on each of the web application servers.
Domain Validation
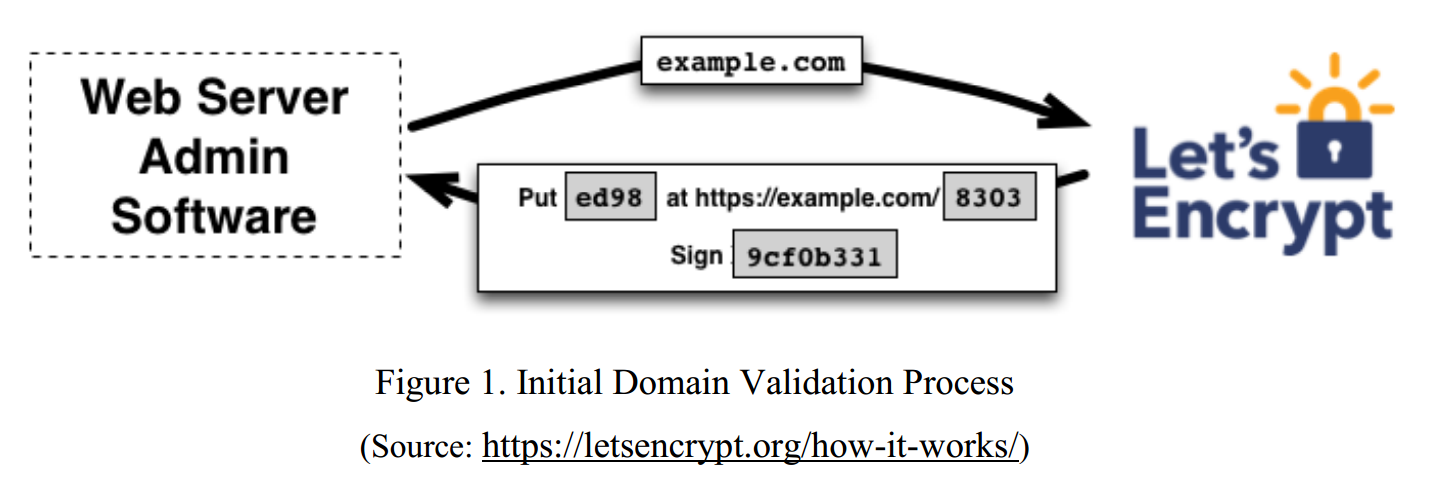
Domain Validation (cont.)

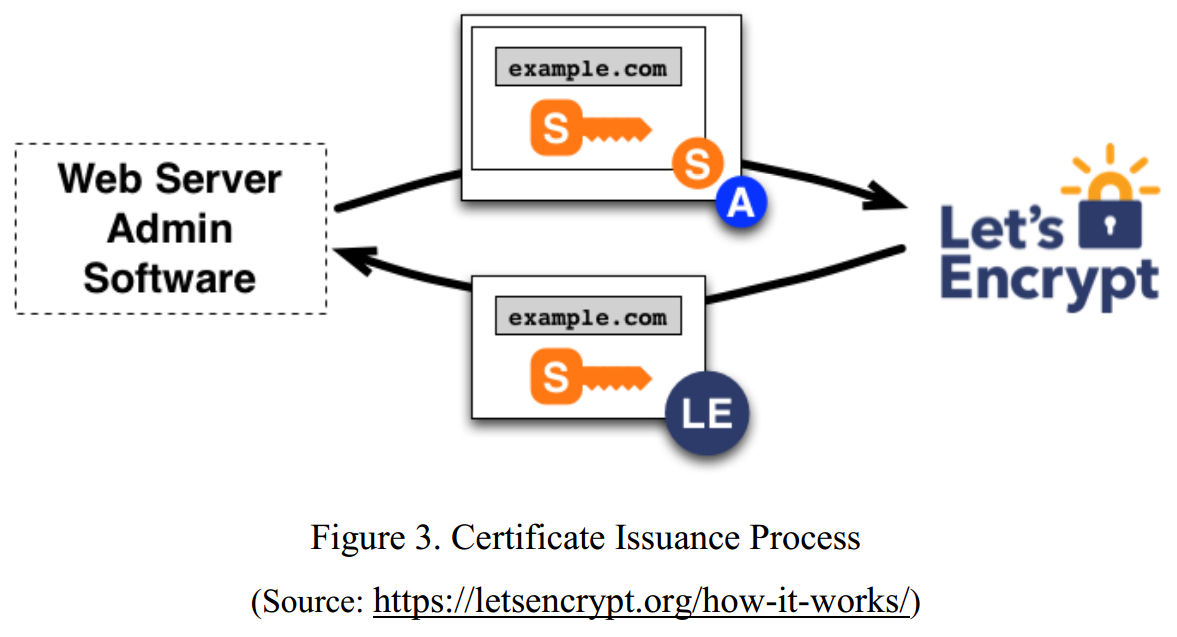
Certificate Issuance
Implementation
cd /srv/apps/
wget https://dl.eff.org/certbot-auto
chmod a+x certbot-auto
#APACHE
./certbot-auto --apache -d www.domain.com
# NGINX
sudo service nginx stop
./certbot-auto certonly --standalone -d www.domain.com
sudo service nginx start
# Renew Certificate
crontab -e
0 3 * * * /srv/apps/certbot-auto renew
# Apache
Implementation

“the growth of HTTPS has increased four-fold since Let's Encrypt was launched.”
-- Mozilla
Source: https://blogs.akamai.com/2016/04/how-has-lets-encrypt-impacted-web-security.html
Conclusion
- Web access security is an important aspect of e-business solutions.
- One of the internet protocols widely used to secure communication between clients and web-based application servers is HTTPS.
- The majority of websites do not implement HTTPS due to the technical complexity and high cost of obtaining a digital certificate.
- To improve the number of HTTPS implementation, Internet Security Research Group developed Let’s Encrypt, a free, automated and open Certificate Authority (CA).
- There are two steps for managing digital certificates from Let’s Encrypt. The agent proves that it has the control of a domain, and then it requests, renews, and revokes certificates for that domain.
- Since its first launch in 2015, more than 2 million domains, from personal to business, have been using digital certificates from Let’s Encrypt.
- This emerging technology provides advantages for better e-business security over the internet.