Privacy by Design
- The CIO Challenge
Dr Neil Williams
neil@tilix.uk


InfoSec 3x3
-
Discerning Customers
-
CIO Audit
-
GDPR


Source: Deloitte
Security & Privacy are Critical
The Commissioners





GDPR Components
3rd Party
Information
Governance
Privacy by
Design
Breach
Notifications
Unambiguous
Consent
Data Protection Officer
GDPR @ Tilix

Privacy by Design is imposed as a key requirement in the GDPR. As such, it makes sense to start thinking of privacy as a key part of all your new processes, projects and contracts. You should actively ensure that privacy has priority in the initial discussions for these activities. As part of your organ- isation’s PMP, these should serve as guiding principles when planning out the programme and selecting tools.
It is now known that privacy is a key aspect of doing busi- ness in the digital world. In the past, privacy was an item that was given scant regard by many organisations. However, a cultural shift in organisational behaviour is required. This involves making Privacy by Design a key step that must be considered as part of the setup of each new policy, business process, project and contract under development. Starting now, mandating a Privacy by Design approach will ensure that new business activities are automatically fit for purpose from a GDPR perspective. This will save significant effort and cost through avoiding the need to retrofit privacy into these activities.
Now, where do you start? As business solutions or capabilities are developed, the datasets that they will interact with should be identified and the business processes should be modelled. When modelling these processes and their interaction with personal data, the requirements of GDPR and privacy best practices should be incorporated at the outset.
The Role of Tech
Paper‐based processes should be avoided whenever possible and technology should form a significant part of the solution. That said, all electronic processing should have its own set of safeguards to protect the systems that facilitate GDPR opera- tions and reporting.
In relation to Privacy by Design, the GDPR outlines that organisations should build data protection into products throughout their lifecycle and that all necessary safeguards be integrated into those systems. The GDPR also specifically highlights data minimisation and pseudonymisation as privacy‐enhancing tools. As such, these should also be considered when designing any GDPR compliance technology solution and leveraged where feasible and/or necessary to maximise compliance.
Leverage Privacy by Design
Determining Feasibility
Bear in mind:
✓ The availability of appropriate technology
✓ The nature of the personal data processing being carried
out
✓ The risks to individuals (and their severity)
✓ The cost of implementation
Your GDPR compliance technology solution should incorporate:
- Automation
- Workflow
- Audit
- Reporting Capabilities
Proving Accountability
The GDPR Front Line
Line of business leader or business unit manager need to think through how your team interacts with customers or employees and how this might potentially change moving forward as a result of GDPR.
We need to assess:
- Personal data that we’re responsible for
- Personal data our team's process
- Personal data our team's ingest and forward to other entities.
Today we will look at:
- Marketing
- Customer Ops
- HR
- Supplier Hub
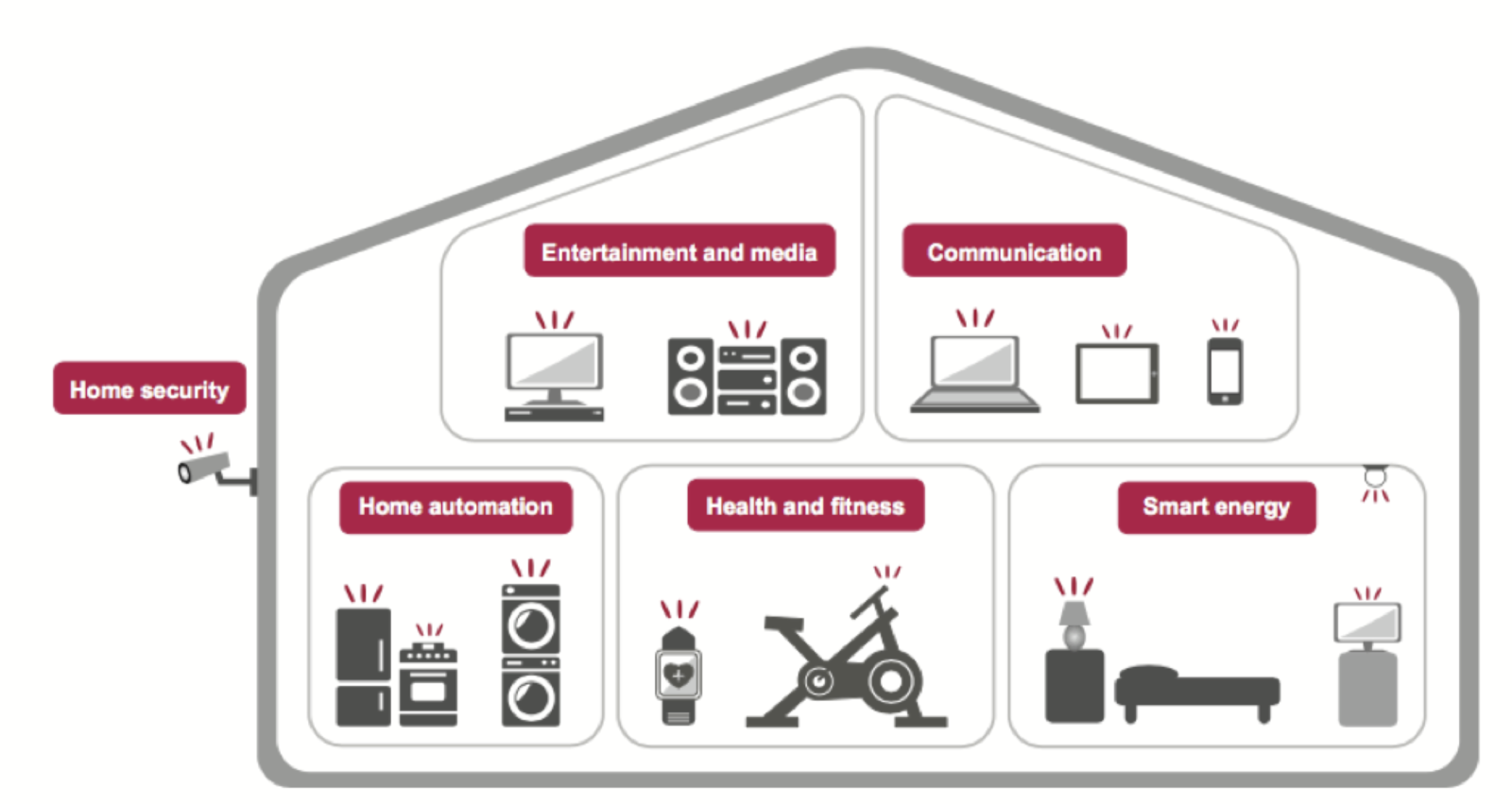
- Smart Home

Customer Operations

Human Resources
?? Minutes
Consent
Typically, consent has been assumed on the basis of employment with a company.
Now, HR teams will need to create consent forms for employees to sign outlining explicit consent for certain personal data processing activities.
Like customers, employees must be provided with a clear understanding of how their personal data is processed within the company and why.
Increased Employee Rights
Including the right to be forgotten. In certain cases, an employer may be required to erase certain employee data when an employee has withdrawn consent for processing.
Legal Review
Employers will need to reconsider the ‘lawful purposes’ by which employee data is processed. This will likely require review and approval by your legal team.
Supplier Hub


Consumer Concerns About IoT
The world's biggest IoT project?
30
53
million
million
comms hubs
meters
Source: GSMA

Dr Neil Williams
neil@tilix.uk

