Vishal Patel
Cyber Security Enthusiast
Part time Bug Hunter
Student of Gujrat Forensic Sciences University
What is Wireshark?
-
Network packet/protocol analyzer.
-
Captures network packets (Link Layer PDUs) ,Analyzes it's contens.
-
Multi-platform (Windows, Linux, OS X, Solaris, FreeBSD, NetBSD, and others).`
-
You could think of the nework packet analyzer as a measuring device used o examine what's going on inside a network cable, just like a Voltmeter is used by and electrician to examine what's going on inside the electric cable (but at a higher level, of course).
Features
- Deep inspection of thousands of protocols.
-
Live capture and offline analysis.
-
Rich VoIP analysis.
-
Live data can be read from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI, and others.
-
It can only capture on networks supported by pcap.
What we can?
- Capture network traffic.
- Decode packet protocols using dissectors.
- Define filters – capture and display.
- Monitor the packets.
- Analyze problems.
Some examples people use Wireshark for:
- Network Administrators : Troubleshoot Network Problems
-
Network security engineers: examine security problems
- Developers: debug protocol implementations
- People: learn network protocol internals
Background
- Initiated by Gerald Combs under the name Ethereal.
-
First version was released in 1998.
-
The name Wireshark was adopted in June 2006.
-
Quite Similar to TCPdump.
What Wireshark can't do?
- Wireshark isn't an Intrusion detection system.
- Wireshark will not manipulate things/packets on the Network.
Wireshark Interfaces
Practical
Case Study
Analysis of scada system.
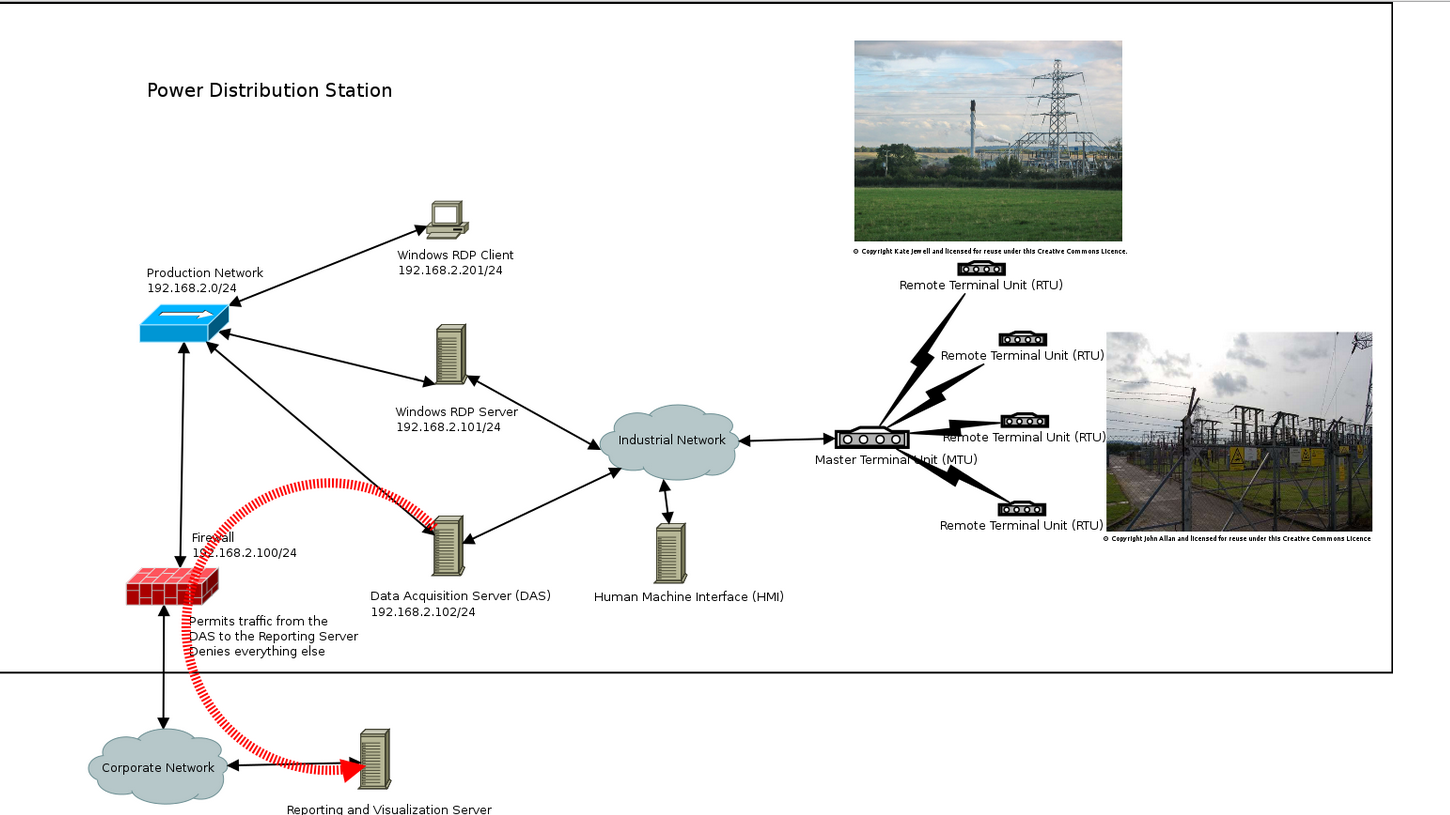
Network Documentation
• Here there are four RTU (Remote Terminal Unit) which are connected to the MTU (Master Terminal Unit) of Industrial network.
• A windows RDP client (IP: 192.168.2.201/24) send the request to the windows RDP server (IP:192.168.2.101/24).
• Through the Production network (IP: 192.168.2.0/24) the requests are Transmitting from the client to server.
• Now the request is received by the server and then sent to the Data Acquisition server (IP: 192.168.2.102/24) for gaining data of the request.
• HMI (Human Machine Interface) is used for handle the industrial machines and network.
• Now the relevant data of request are goes back to the client through production network.
• If server found any intrusion from the client then the request will goes for reset to client, otherwise the client will get the output.
• There is also a firewall exist for monitoring and denying from the unauthorized access or harmful services.
• DAS (Data Acquisition Server) will also make a mirror file that is store in the Reporting and visualization server. Here, which are connected to corporate network .Firewall don’t allow any other IP's to access the Reporting and visualization server. It is just use for Security and Backup purpose.
Title Text
Subtitle
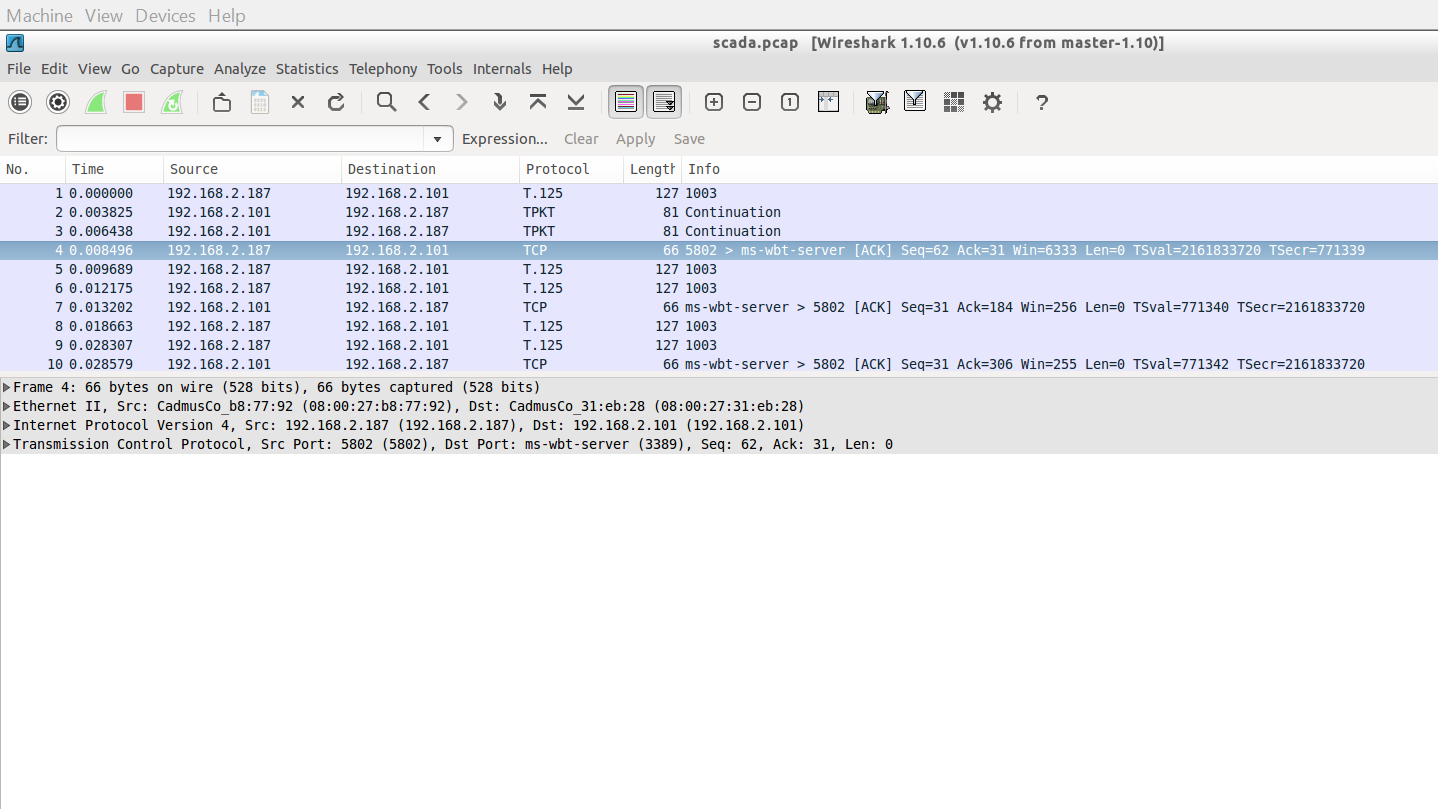
• Scada.pcap file contains the information about the packets
• Here, An image shows different columns that contains the information related to packets . • We can show here the details such as time , source IP address of packets(Client IP) ,destination IP of packets(Server IP) ,protocols which are used for transfer the data or packets , Length of the packet(Size) and the Info: which shows communication details of the client and server • Here, first line shows the 192.168.2.187 is the client that sent the request for ack= Acknowledgement to the 192.168.2.101 server using the T.125 protocol. • Now the communication between the two IP's are running after sometime the server gets one kind of intrusion in the network.
Title Text
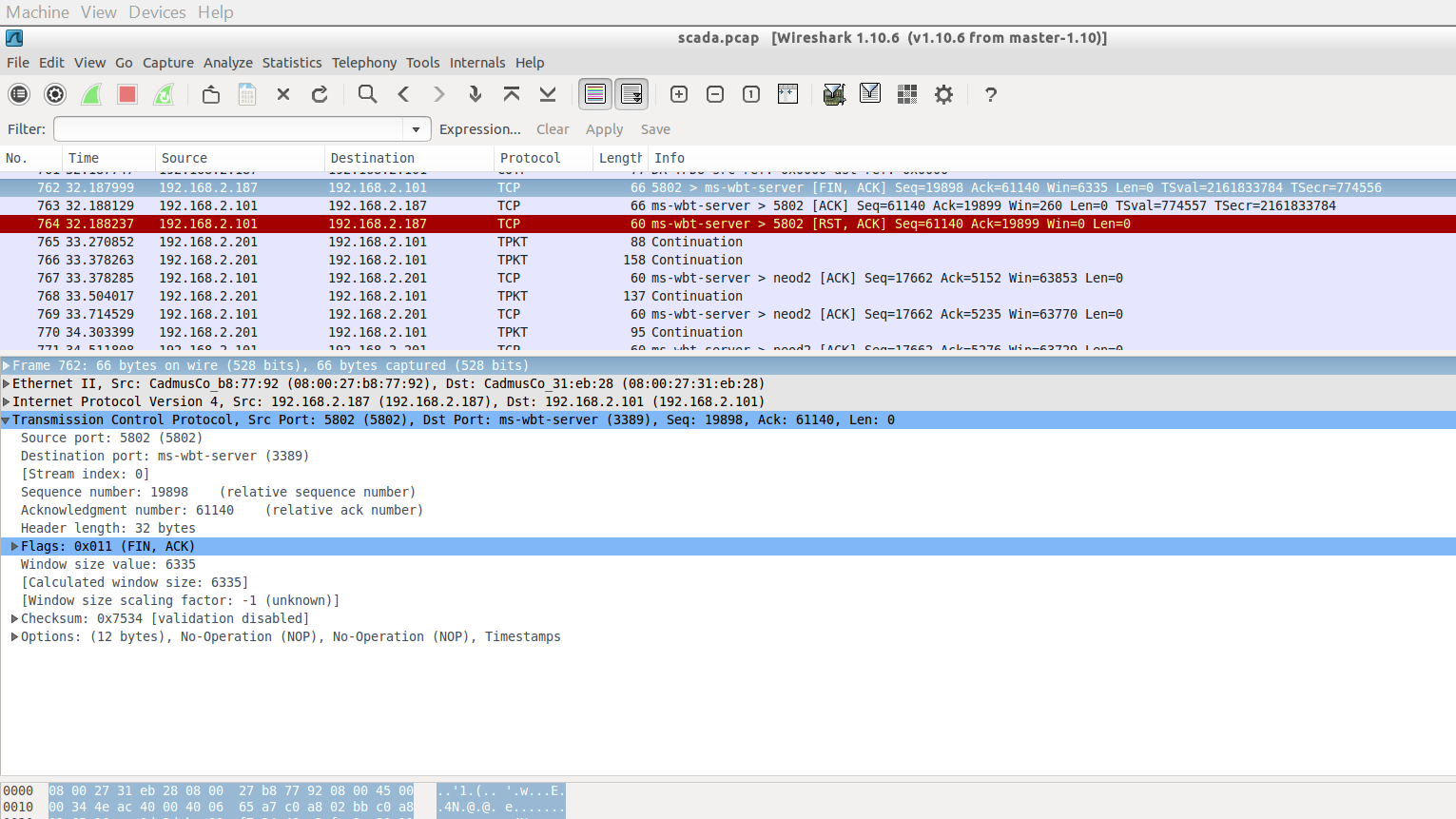
Conversation between 192.168.2.101 & 192.168.2.187
• Here, the red line in screen shows the intrusion in the server. the red line information shows here the communication has been finished (5802> ms-wbt-server [FIN, ACK]) between the 192.168.2.187 and 192.168.2.101 IP's.
• Here, we found that the intrusion is done by port number 5802 so now we have to find the information about that port.
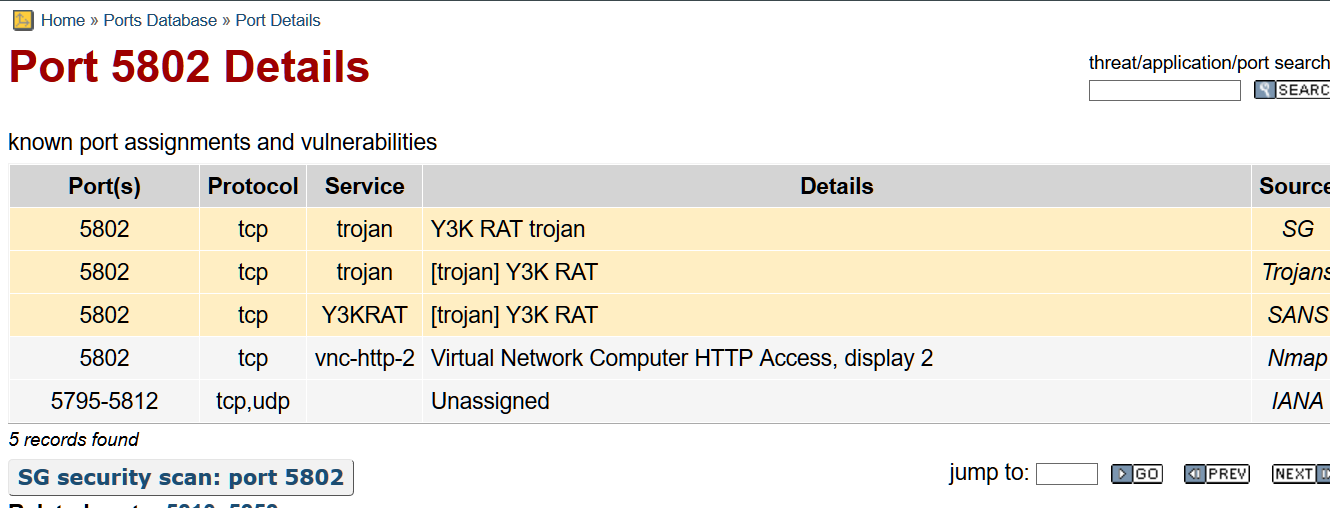
•Port number 5802 is an open port which is used by the TCP protocol and the Trojan and Y3KRAT services are used for the intrusion in to the network.