Two Factor Authentication
Multi factor authentication
- verifies users identity by (at least) two different means
- because:
- can't force a user to pick strong enough password
- can't stop hackers from compromising your DB
- Means of verification, present something
- you know(a secret, password)
- you have(a possession, token)
- you are(a physical evidence, biometrics)
What mean of verificatoin is
Opening a door with a key
Fingerprint scan
Requiring pet name
USB key
SMS token
Facial recognition
Using ATM(cash machine)
SSH
Time based one time password(TOTP)

- timestamp, number of seconds from epoch
- in practice, because of external factors(eg. network latency, typing speed) number of 30 second intervals is used
ROTP
def generate_otp(input, padded=true)
hmac = OpenSSL::HMAC.digest(
OpenSSL::Digest.new(digest),
byte_secret,
int_to_bytestring(input)
)
offset = hmac[-1].ord & 0xf
code = (hmac[offset].ord & 0x7f) << 24 |
(hmac[offset + 1].ord & 0xff) << 16 |
(hmac[offset + 2].ord & 0xff) << 8 |
(hmac[offset + 3].ord & 0xff)
if padded
(code % 10 ** digits).to_s.rjust(digits, '0')
else
code % 10 ** digits
end
endtotp = ROTP::TOTP.new("secret", # required, Base32 encoded
interval: 30,
digits: 6,
digest: 'sha1'
issuer: 'app-name'
)
code = totp.now # => "323207"
totp.verify(code) # => true
sleep(30)
totp.verify(code) # => false
totp.vefify_with_drift(code, 30) # => true# @param [Integer] drift the number of seconds # that the client and server are # allowed to drift apart
https://github.com/mdp/rotp/blob/master/lib/rotp/totp.rb#L41
Exchangeing secrets
(in the web apps)
- share the secret as a string
- useful for devices without camera, like browser extensions
- generate secret via QR code
- standardized QR payload format
otpauth://TYPE/LABEL?PARAMETERS otpauth://totp/flufy@cat.com?secret=abc123&issuer=cat
Integration with Devise
Usefull:
- generator
- migrations
- concern(except naming)
- backup codes plugin
Useless:
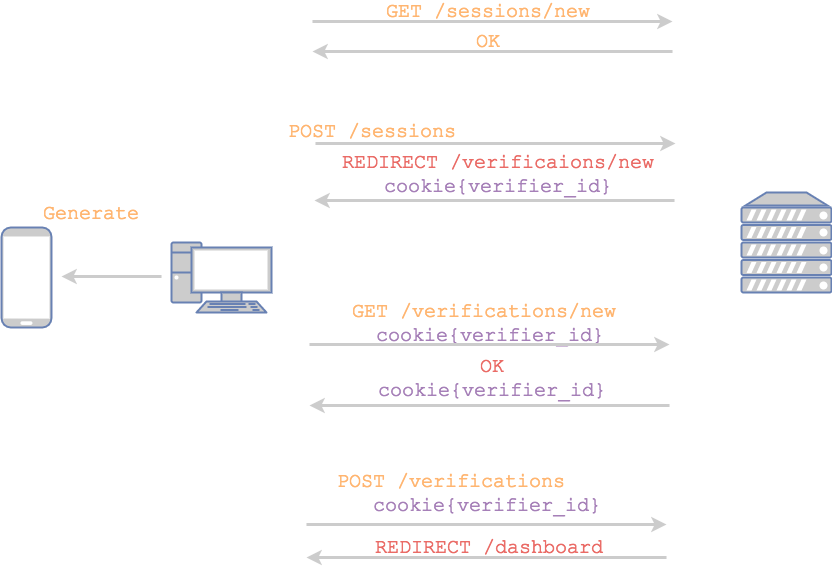
- devise strategy
- default workflow does not support 2 step verification
- all the pieces are there just need to glue it together
- allows for flexible integration, custom tailored to your business process
- you are unable to salvage, all library logic
Two step verification