Trust teams, but verify
Tech Exchange 2018
ThoughtWorks
Zhang Yuchen
What is "Trust teams, but verify"?
- How do we present trust?
- Why we need to verify?
- What is verify, and verify?
- Security should not bind with domain - Noodle Restaurant
Mars Company
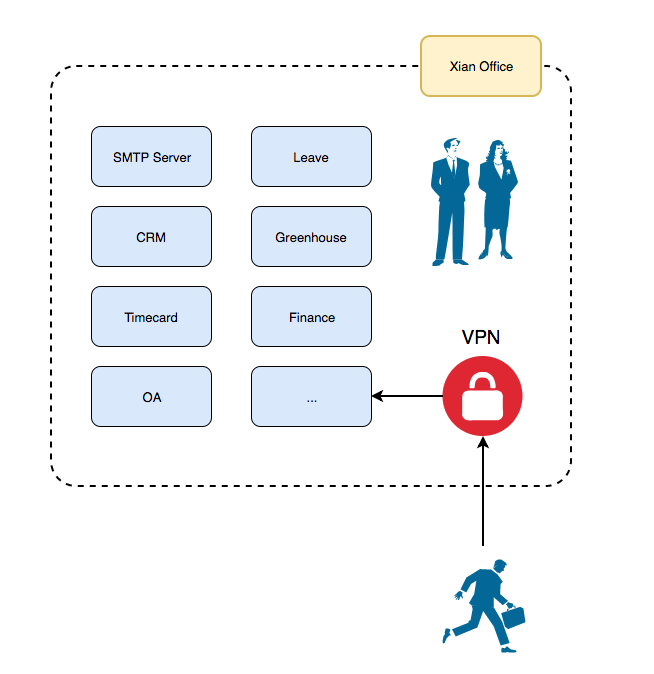
Mars Company II
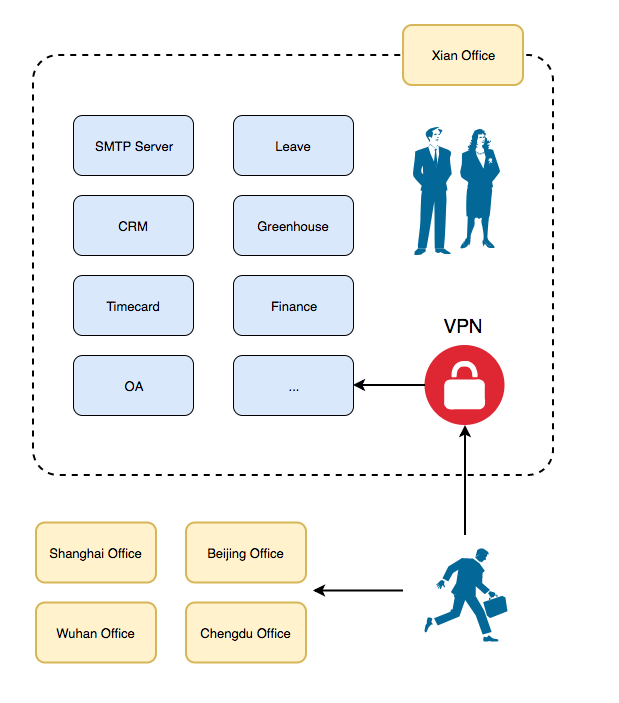
Mars Company III
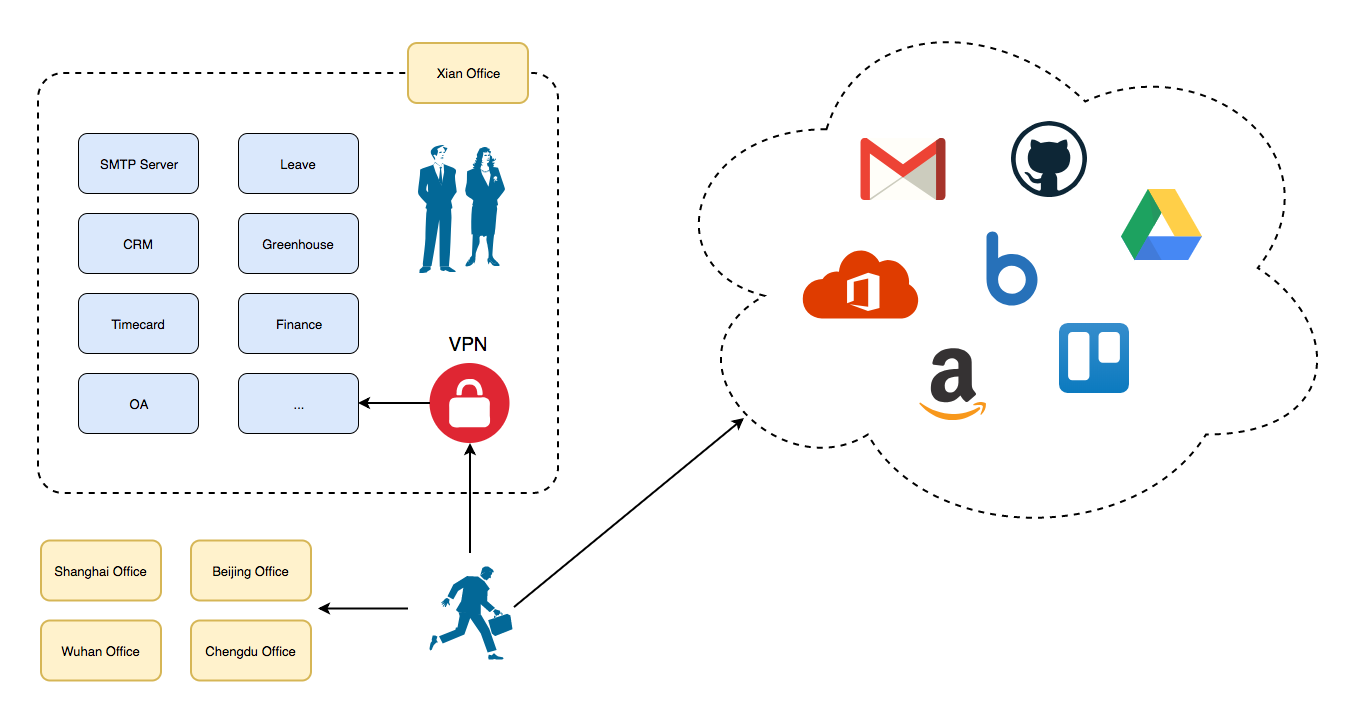
Problems
- Identity everwhere
- Authentication & Authorization & RBAC
- Bad user experience
- Perimeter Security Model
- Internal resources need to be exposed
- If someone breaks in, everything is gone
- Perimeter is growing, location changes
Assumption: facing zero trust network
A Zero Trust (ZT) architecture abolishes the idea of a trusted network inside a defined corporate perimeter. Zero Trust mandates the creation of microperimeters of control around an enterprise's sensitive data assets and provides visibility into how it uses data across its ecosystem to win, serve, and retain customers.
Zero Trust Network
Always verify
Google BeyondCorp
- access depends solely on device and user credentials, regardless of a user’s network location
- all access to resources, should be fully authed\authzed\encrypted upon on your device
- fine-grained control in different parts of resources, eg: mail application or code
- for user, no VPN
- local and remote access to enterprise resources should be same and just few latency
Google BeyondCorp - comps
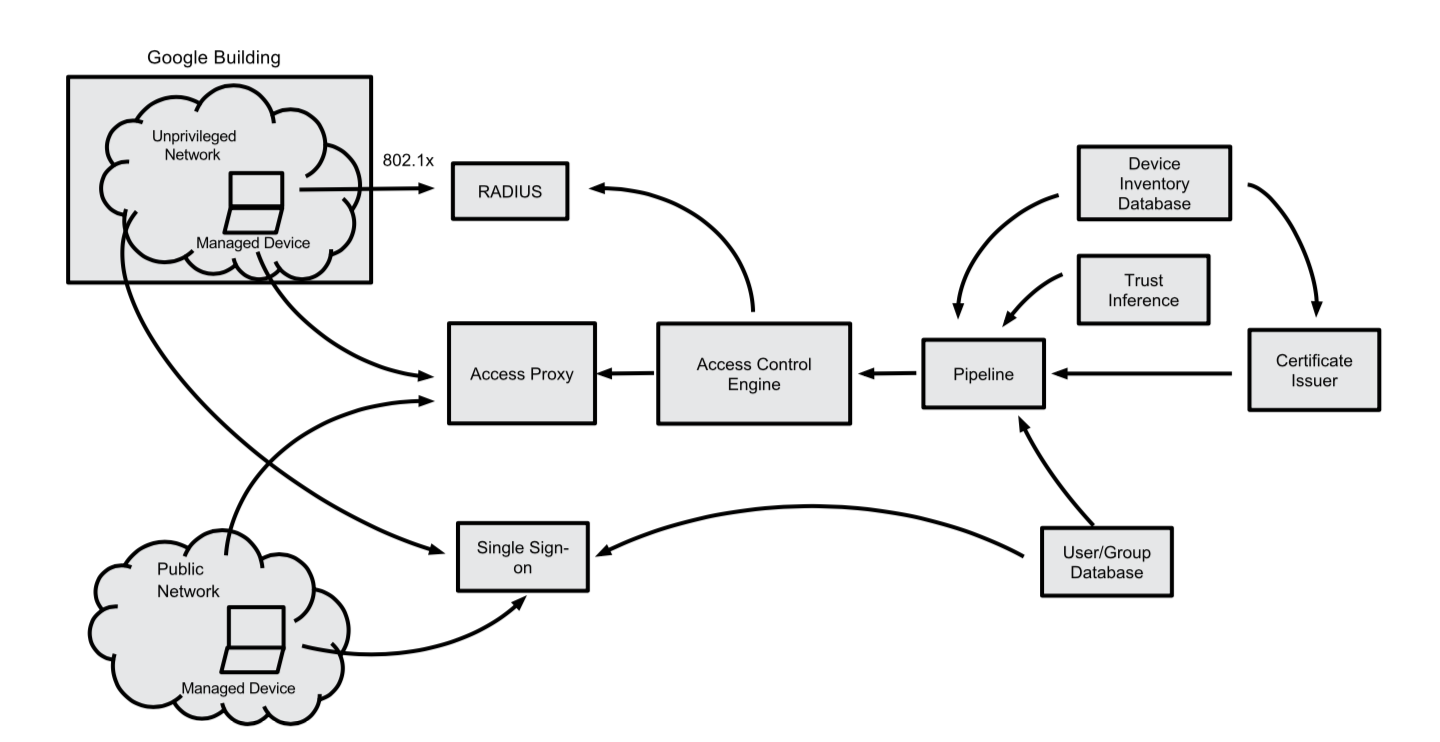
- Securely Identifying the Device
- Device Inventory Database
- Device Identity
- Securely Identifying the User
- User and Group Database
- Single Sign-On System
- Removing Trust from the Network
- Deployment of an Unprivileged Network
- Use RADIUS to assign devices to network
- Externalizing Application and Workflow
- Internet-Facing Access Proxy
- Public DNS
- Implementing Inventory-Based Access Control
- Trust Inference for Devices and Users
- Access Control Engine