Resource Plugin Vulnerability
Lightning Talk
[GUM] groovy.mn
April 8th 2014
CVE-2014-0053
INFORMATION DISCLOSURE
IN GRAILS APPLICATIONS
What?
Resources Plugin 1.0.0 -- 1.2.5
Grails 2.0.0 -- 2.3.6
When?
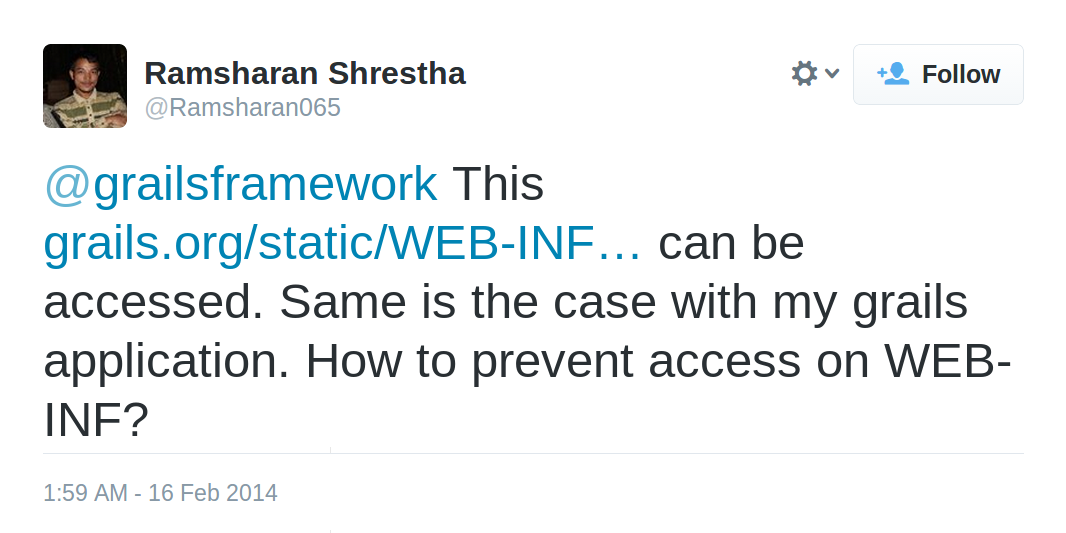
Feb 16th 2014
Feb 19th 2014
Feb 20th 2014
Default Config.groovy fixed:
How?
/static/WEB-INF/...
Anything in these directories (within your WAR)
imagination.use { //Sensitive Information //Entire CodebaseyourBase.all.belongsTo(us) }
Reproduce (prior to Grails 2.3.6)
$ gvm use grails 2.3.5 $ grails create-app vuln$ cd vuln $ grails compile $ grails run-war
curl http://localhost:8080/vuln/static/WEB-INF/classes/UrlMappings.classWhy?
Configurable Pipeline
Redirect ad-hoc resources to
/static/... ('static' is configurable)
oversight
Now what?
Upgrade resources 1.2.6+
runtime ":resources:1.2.7"
Ditch Resources
--
Go Asset Pipeline
Mitigation
Filter at proxy/balancer level
Prevent access to resources under /WEB-INF and /META-INF in the reverse proxy (if one is used)
Configure Resources
includes/excludes
grails.resources.adhoc.includes = ['/images/**', '/css/**', '/js/**', '/plugins/**'] grails.resources.adhoc.excludes = ['**/WEB-INF/**','**/META-INF/**']
Security
Configure security mechanisms to secure unknown entities.
grails.plugin.springsecurity.rejectIfNoRule = true
Guilty until proven innocent.
Container
Tomcat Valves
4 example
@See StandardContextValve
FIN
colin.harrington@objectpartners.com
cve-2014-0053
By Colin Harrington
cve-2014-0053
- 2,433