Detecting the Behavioral Relationships of Malware Connections
By eldraco
Detecting the Behavioral Relationships of Malware Connections
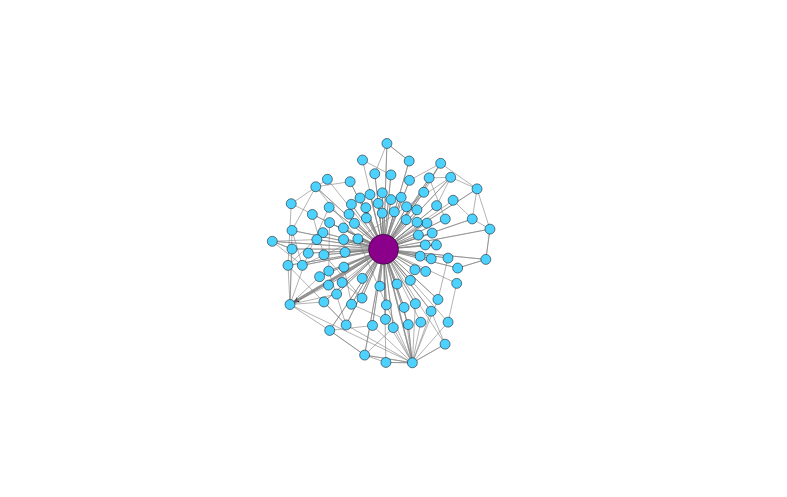
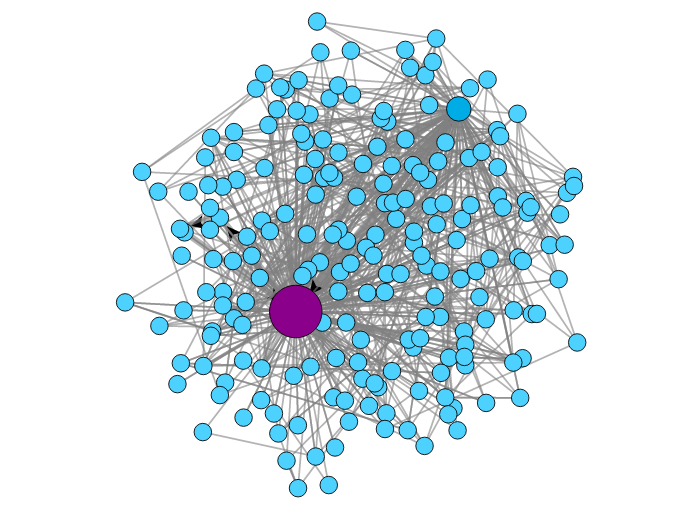
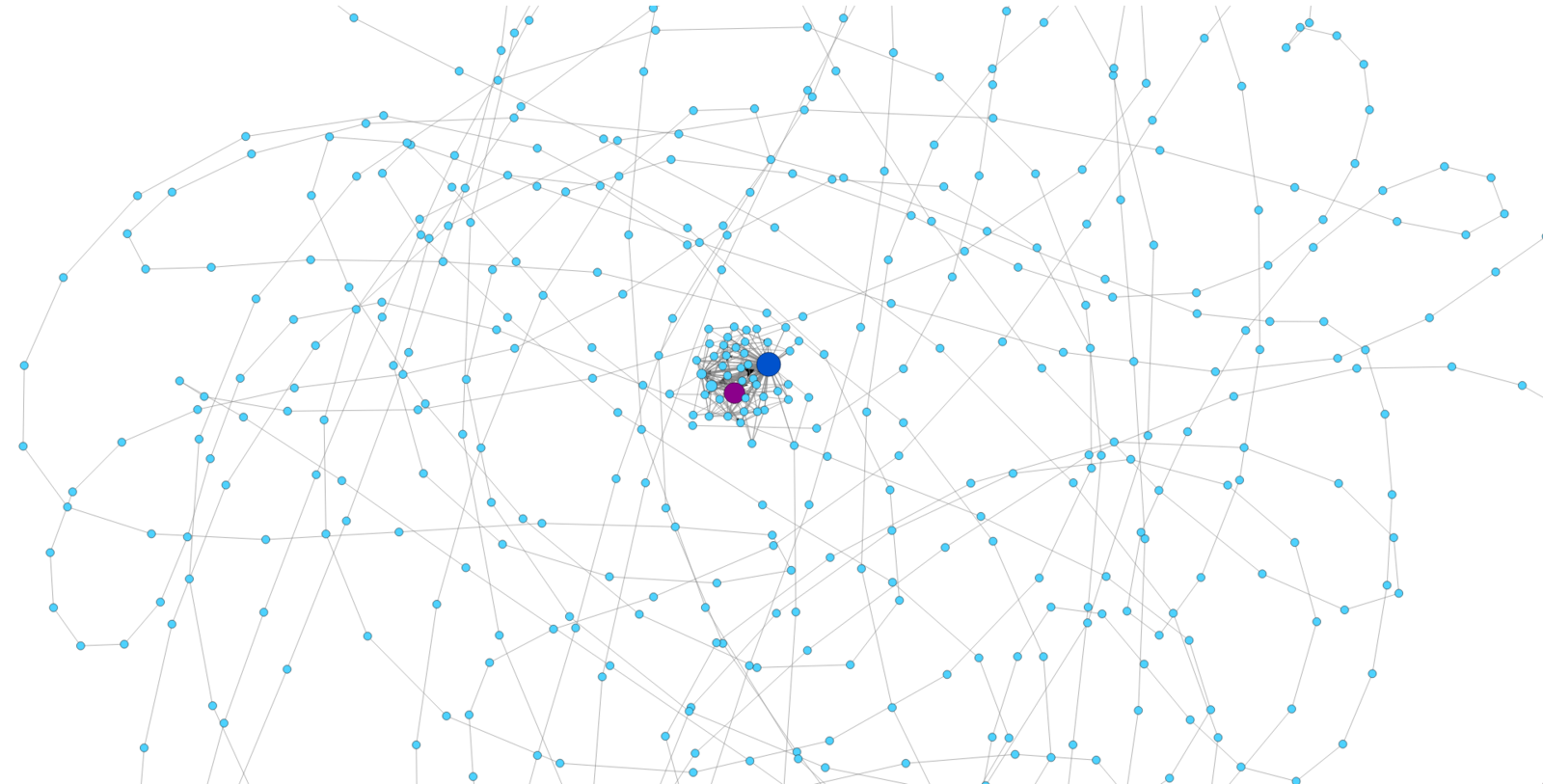
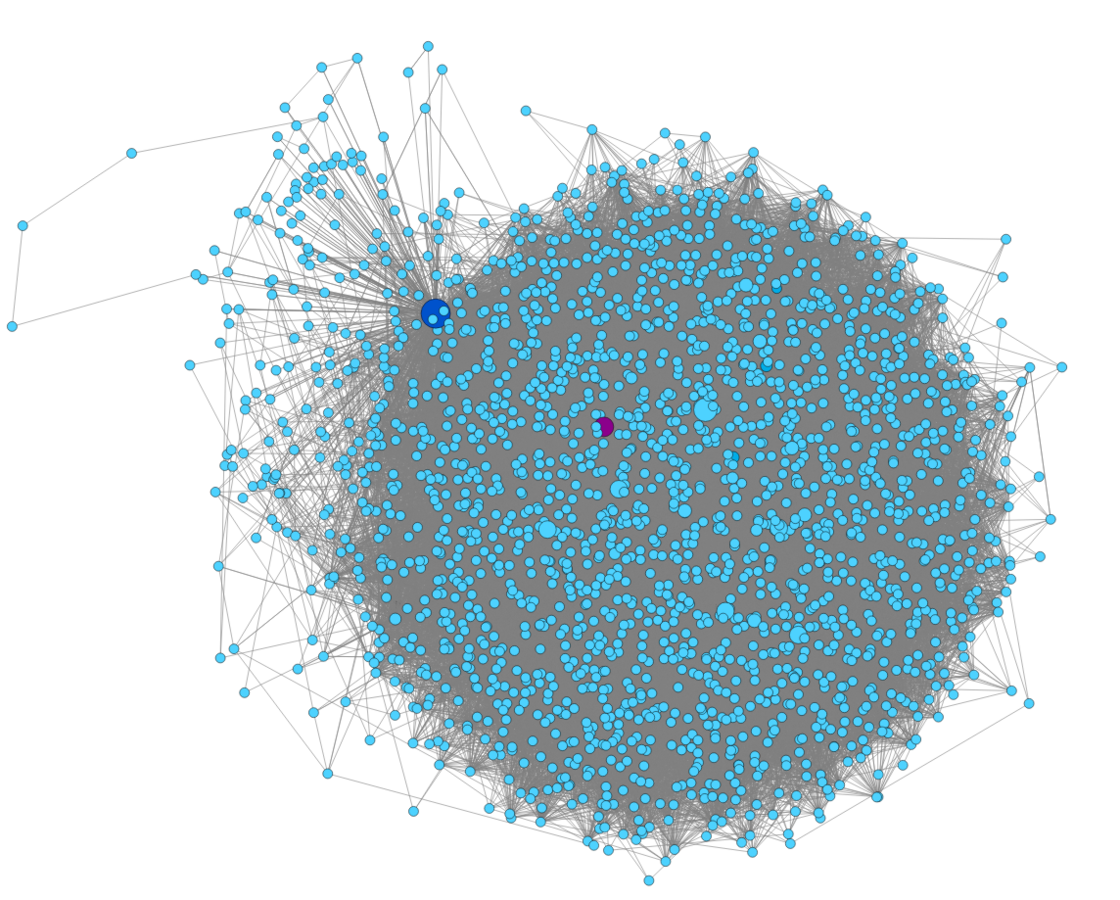
We still have problems to solve when it comes to detecting malware in the network. If the malware is new, there are not signatures, no IoCs, no threat information. If you have thousands of hosts you can not even analyze the payloads, or you don't have payloads and have to resort to NetFlows. In this limited context is where we developed a new idea to detect the behavioral patterns of how a computer works in the network by analyzing its communications as a cyclic graph. Our technique applies new concepts to reduce the information being analyzed while retaining and graphing the major features. We test our concept on dozens of Normal and Malware traffic, which gives significance to the work. The takeaway is: the way you use your computer leaves traces in the network, and those traces can be used to detect when you are infected.