Stratosphere Project
Malware Detection in the Network. Behavioral Analysis with Machine Learning
García Sebastián PhD.
sebastian.garcia@agents.fel.cvut.cz
Live Slides bit.ly/stratos1


Stratosphere Project
Free
Software

Machine
Learning
Behavioral
IPS
Protecting
NGOs
Stratosphere Technical Pillars
Less is More
Disassociate
Verify
Analyze the behavior of group of flows.
Representation of behaviour from detection.
With real and labeled datasets and networks
Behaviors
-
Your behavior is usually the same when connecting with the same service.
-
Group flows going to a specific service by ignoring the source port. We have our connection.
-
10.0.2.2-60.60.60.1-80-tcp
-
-
The connection, composed of several flows, now shows a behavior.
-
Using a service, you go from one state to the next state.
-
Each flow has its own state.
-
We model the states using four features.
-
Size of the flow.
-
Duration of the flow.
-
Periodicity of the flow.
-
Time between flows.
-
From Connections to States
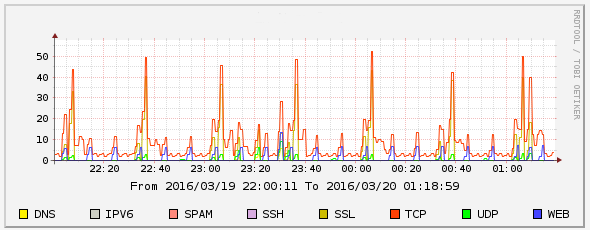
States as Letters

The Behavior of a Connection

10.0.2.111-217.23.10.139-80-tcp 55*V0v00v*E*v*v*v*v*E*v
1 flow -> 4 features -> 1 letter + 1 symbol
Stratosphere Behavior Demo
Stratosphere Testing Framework: Create and Analyze Behaviors
About the Behaviors
-
Malware mostly generate the same behavior.
-
Changing the behavior is costly for the attacker.
-
These behaviors do not expire quickly.
-
Infections go unnoticed for hours. There is time.
From the letters create a Markov Chains behavioral model
Detection with Markov Chains
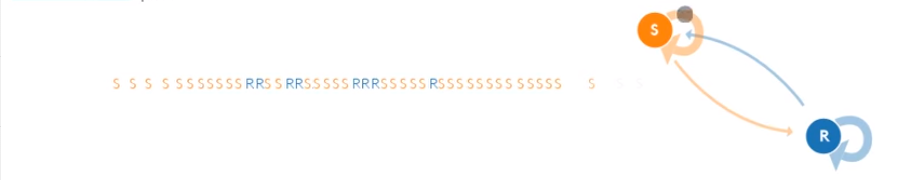
-
Train Markov Models with known Behaviors: Malware and Normal.
Detection with Markov Chains
-
Compare the unknown traffic of a network to each trained Markov Model.
Trained M1
Unknown Connection
87,a,a,b,B,i*i*i*i*i (?)
Trained M2
Trained M3
Stratosphere Detection Demo
-
Stratosphere Testing Framework
-
Stratosphere Linux IPS
Results
-
How to measure?
-
Packets/Flows/Connections/IPs?
-
Per minute? Per hour? Per day?
-
Who is putting the labels?
-
In Stratosphere it also depends on the models used.
-
-
Stratosphere Malware and Normal Dataset
-
https://stratosphereips.org/category/dataset.html
-
Results
-
In our datasets
-
96% TPR. Our own botnet traffic connections that are detected.
-
-
Real Traffic
-
~0.0002% FPR (30 FP in 132,000 connections/5min)
-
-
Novel Success cases: Linux Botnet, DDoS, etc.
-
Errors? For sure.
Stratosphere Data Analysis
-
Cloud-based Detection service for NGOs.
-
Add new algorithms continually.
-
Update the models.
-
Verify the detections if necessary.
-
NGOs can send the Flows or only the letters! Privacy matters.
Thanks!
Sebastian Garcia
sebastian.garcia@agents.fel.cvut.cz
@stratosphereips
https://stratosphereips.org
Malware Detection in the Network. Behavioral Analysis with Machine Learning
By eldraco
Malware Detection in the Network. Behavioral Analysis with Machine Learning
Stratosphere Project
- 1,784



