Kali Linux
Basic Commands
Eun Joo Lee
August 28th, 2018
Agenda
- What is Kali Linux
- Knowing Your System
- Permissions
- Searching Made Simpler
- Networking
- Tips & Tricks
What is Kali Linux
- Released March 13th, 2013 (formerly BackTrack Linux)
- Debian-based Linux distribution
- Penetration testing and security audit
- Contains several hundred tools
- Open source
- Multi language support
Knowing Your System
root@kali-Linux:~# ls
Desktop helloworld.py snort_rules.py write.py
Documents Music snort_rules.txt
Downloads Pictures Templates
hello.py Public Videos
root@kali-Linux:~# cd Downloads
root@kali-Linux:~/Downloads# ls
ls - list
cd - change directory
Oh no!
Wrong directory
root@kali-Linux:~/Downloads# cd ..
root@kali-Linux:~# pwd
/root
root@kali-Linux:~# ls
Desktop helloworld.py snort_rules.py write.py
Documents Music snort_rules.txt
Downloads Pictures Templates
hello.py Public Videos
root@kali-Linux:~# cd Desktop
root@kali-Linux:~/Desktop# ls
Python VBoxLinuxAdditions.run
root@kali-Linux:~/Desktop# ls -la
total 7164
drwxr-xr-x 2 root root 4096 Aug 28 13:13 .
drwxr-xr-x 16 root root 4096 Aug 28 12:38 ..
-rw-r--r-- 1 root root 175 Aug 27 19:01 Python
-rwxr-xr-x 1 root root 7321035 Aug 4 13:11 VBoxLinuxAdditions.run
cd - change directory
pwd - print working directory
ls - list
ls -la - list all files
Permissions
chmod
change file mode permissions
Read (r)=4
Write(w)=2
Execute(x)=1
sudo
Root Permission
- Change command to become root user and issue passwd:
sudo -i
passwd - OR set a password for root user in one command line:
sudo passwd root - Test it to make sure your password has changed:
su -
Searching Made Simpler
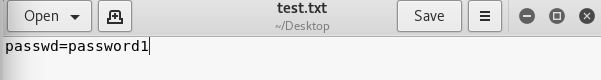
root@kali-Linux:~/Desktop# grep -i "passwd" test.txt
passwd=password1
grep
The grep filter searches a file for a particular pattern of characters, and displays all lines that contain that pattern.
Pipe
To send the output of one program to another program which allows for further processing
root@kali-Linux:~/Desktop# ls -la /etc
total 1564
drwxr-xr-x 188 root root 12288 Aug 28 12:37 .
drwxr-xr-x 24 root root 4096 Aug 28 12:54 ..
-rw-r--r-- 1 root root 2981 Apr 12 03:37 adduser.conf
-rw-r--r-- 1 root root 44 Jul 23 20:24 adjtime
-rw-r--r-- 1 root root 185 Apr 12 03:42 aliases
drwxr-xr-x 2 root root 20480 Aug 4 11:24 alternatives
drwxr-xr-x 2 root root 4096 Jul 23 19:50 amap
-rw-r--r-- 1 root root 401 May 29 2017 anacrontab
drwxr-xr-x 8 root root 4096 Jul 23 19:50 apache2
-rw-r--r-- 1 root root 433 Oct 1 2017 apg.conf
drwxr-xr-x 3 root root 4096 Jul 23 19:50 apm
drwxr-xr-x 3 root root 4096 Aug 4 11:16 apparmor
drwxr-xr-x 8 root root 4096 Aug 4 11:24 apparmor.d
-rw-r--r-- 1 root root 769 Jan 22 2018 appstream.conf
drwxr-xr-x 6 root root 4096 Jul 23 20:24 apt
drwxr-xr-x 2 root root 4096 Jul 23 19:50 arpwatch
drwxr-xr-x 3 root root 4096 Aug 4 11:21 avahi
-rw-r--r-- 1 root root 1994 Feb 13 2018 bash.bashrc
-rw-r--r-- 1 root root 45 Feb 12 2018 bash_completion
drwxr-xr-x 2 root root 4096 Aug 4 13:00 bash_completion.d
drwxr-xr-x 2 root root 4096 Jul 23 19:50 bdfproxy
drwxr-xr-x 2 root root 4096 Jul 23 19:50 beef-xss
-rw-r--r-- 1 root root 367 Mar 2 13:03 bindresvport.blacklist
drwxr-xr-x 2 root root 4096 Apr 1 04:02 binfmt.d
drwxr-xr-x 2 root root 4096 Aug 4 10:16 bluetooth
-rw-r--r-- 1 root root 860 Feb 20 2018 btscanner.dtdtotal 1564
drwxr-xr-x 188 root root 12288 Aug 28 12:37 .
drwxr-xr-x 24 root root 4096 Aug 28 12:54 ..
-rw-r--r-- 1 root root 2981 Apr 12 03:37 adduser.conf
-rw-r--r-- 1 root root 44 Jul 23 20:24 adjtime
-rw-r--r-- 1 root root 185 Apr 12 03:42 aliases
drwxr-xr-x 2 root root 20480 Aug 4 11:24 alternatives
drwxr-xr-x 2 root root 4096 Jul 23 19:50 amap
-rw-r--r-- 1 root root 401 May 29 2017 anacrontab
drwxr-xr-x 8 root root 4096 Jul 23 19:50 apache2
-rw-r--r-- 1 root root 433 Oct 1 2017 apg.conf
drwxr-xr-x 3 root root 4096 Jul 23 19:50 apm
drwxr-xr-x 3 root root 4096 Aug 4 11:16 apparmor
drwxr-xr-x 8 root root 4096 Aug 4 11:24 apparmor.d
-rw-r--r-- 1 root root 769 Jan 22 2018 appstream.conf
drwxr-xr-x 6 root root 4096 Jul 23 20:24 apt
drwxr-xr-x 2 root root 4096 Jul 23 19:50 arpwatch
drwxr-xr-x 3 root root 4096 Aug 4 11:21 avahi
:
The pipe operator gets the stdout of a command and make the stdin to another process
ls -ls /etc | less
root@kali-Linux:~/Desktop# ls | tee sample.txt
Python
Python.txt
sample
sample.txt
test_directory
test.txt
VBoxLinuxAdditions.run
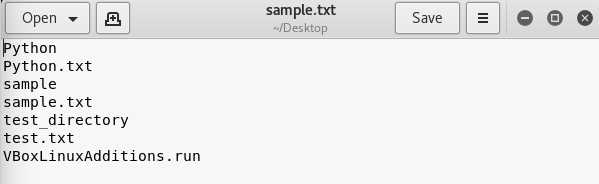
You should see the output of ls on your screen and if you open up the sample.txt file you should see the same information!
What if I wanted to write the output of the command to two different streams?
Networking
ifconfig
List your internal IP address
root@kali-Linux:~/Desktop# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.0.2.15 netmask 255.255.255.0 broadcast 10.0.2.255
inet6 fe80::a00:27ff:fee3:b633 prefixlen 64 scopeid 0x20<link>
ether 08:00:27:e3:b6:33 txqueuelen 1000 (Ethernet)
RX packets 15 bytes 1932 (1.8 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 35 bytes 3037 (2.9 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 28 bytes 1596 (1.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 28 bytes 1596 (1.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
nmap (network mapping)
Helps determine if ports are open or closed
root@kali-Linux:~/Desktop# nmap
Nmap 7.70 ( https://nmap.org )
Usage: nmap [Scan Type(s)] [Options] {target specification}
TARGET SPECIFICATION:
Can pass hostnames, IP addresses, networks, etc.
Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254
-iL <inputfilename>: Input from list of hosts/networks
-iR <num hosts>: Choose random targets
--exclude <host1[,host2][,host3],...>: Exclude hosts/networks
--excludefile <exclude_file>: Exclude list from file
HOST DISCOVERY:
-sL: List Scan - simply list targets to scan
-sn: Ping Scan - disable port scan
-Pn: Treat all hosts as online -- skip host discovery
-PS/PA/PU/PY[portlist]: TCP SYN/ACK, UDP or SCTP discovery to given ports
-PE/PP/PM: ICMP echo, timestamp, and netmask request discovery probes
-PO[protocol list]: IP Protocol Ping
root@kali-Linux:~/Desktop# ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_seq=1 ttl=63 time=30.9 ms
64 bytes from 8.8.8.8: icmp_seq=2 ttl=63 time=47.7 ms
64 bytes from 8.8.8.8: icmp_seq=3 ttl=63 time=29.4 ms
64 bytes from 8.8.8.8: icmp_seq=4 ttl=63 time=25.9 ms
64 bytes from 8.8.8.8: icmp_seq=5 ttl=63 time=30.7 ms
ping
Test for network connection
traceroute
trace route to host
uses ICMP packets to map the route
root@kali-Linux:~/Desktop# traceroute
Usage:
traceroute [ -46dFITnreAUDV ] [ -f first_ttl ] [ -g gate,... ] [ -i device ] [ -m max_ttl ] [ -N squeries ] [ -p port ] [ -t tos ] [ -l flow_label ] [ -w MAX,HERE,NEAR ] [ -q nqueries ] [ -s src_addr ] [ -z sendwait ] [ --fwmark=num ] host [ packetlen ]
Options:
-4 Use IPv4
-6 Use IPv6
-d --debug Enable socket level debugging
-F --dont-fragment Do not fragment packets
-f first_ttl --first=first_ttl
Start from the first_ttl hop (instead from 1)
-g gate,... --gateway=gate,...
Route packets through the specified gateway
(maximum 8 for IPv4 and 127 for IPv6)
-I --icmp Use ICMP ECHO for tracerouting
-T --tcp Use TCP SYN for tracerouting (default port is 80)
-i device --interface=device
Specify a network interface to operate with
Tips & Tricks
Tips & Tricks
up arrow (locate most recent searches)
clear (clear your terminal)
ctrl + z (stop processing)
tab (when locating files)
Thank You!
Kali Linux Basic Commands
By eunjoolee787
Kali Linux Basic Commands
Eun Joo Lee August 28th, 2018
- 605



