Web security:
CSRF attacks
Human Talks
Grenoble 10/06/2014
Fabio Lombardi
About me
- 2013 - ongoing:
Research & Development Engineer @ Bonitasoft
- Past:
1 year and an half as Web Intrusion Tester Consultant
Promo Ensimag and Polytechnic of Turin 2012
Master in IT Security and dev
Web security: owasp top 10
Open Web Application Security Project: https://www.owasp.org/index.php/Top_10_2013-Top_10

CSRF
Cross Site Request Forgery

attacker page
- It could be a popular web site clone ( phishing tools ) + hidden iframe or img:
<iframe src=./attack_payload.html width=0 height=0> </iframe>
- attack_payload.html:

- action="http://my-site.com/..." works using the session cookie obtained from my-site.com page.
Why It works?
It's a browser feature which is also used in good ways:
e.g. Facebook like or Google + buttons in third parties websites.
The session is kept alive for multiple tabs
impacts
- Malicious money transfers
- User creation
- Privilege escalation
- Compromise end-user data
- If the victim is an admin => the entire web application can be compromised
- Examples (today fixed): ING direct, youtube, new york times
Limitations
The attacker cannot:
-
read the session cookie
- read the HTTP response
Based on this, the solution is to generate and exchange an X-API-Token ( unique and random ) shared between server and client
Solution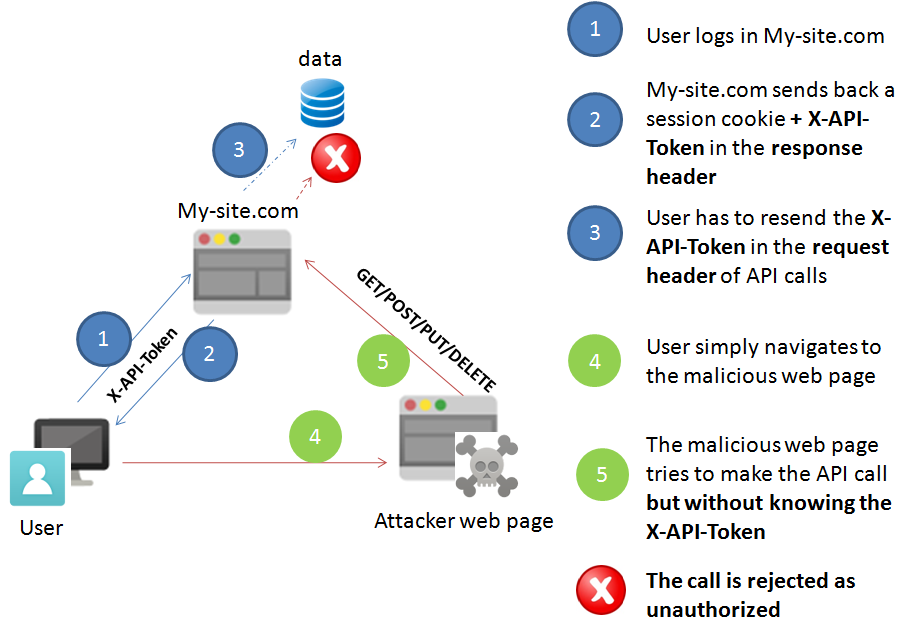
server example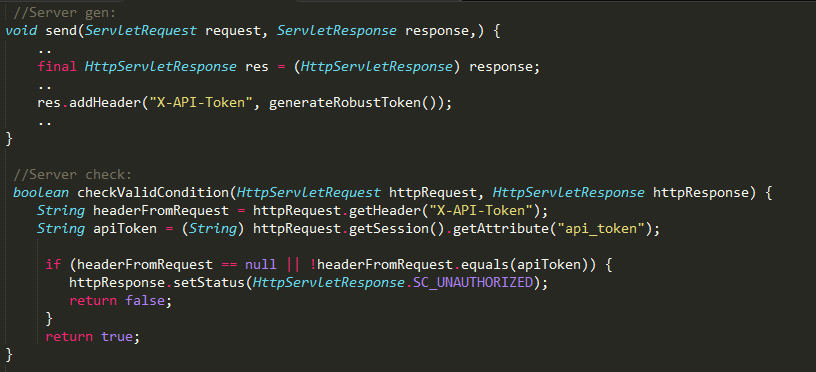
client example

thank you
QUESTIONS ?
CSRF Attacks
By Fabio Lombardi
CSRF Attacks
- 1,473