Access Control
for the
Swarm

Geovane Fedrecheski
Advisor: Marcelo Zuffo
Nov 2016


Contents
-
Swarm?
-
Access Control?
-
Swarm Broker & Access Control
-
Prototype
-
Conclusion & Next steps
The Swarm
First, the IoT

Good
- Automation
- Pervasive
- Remote access
Bad
- Interoperability
- Scalability
- Security


Lee, Edward A., et al. "The Swarm at the Edge of the Cloud." IEEE Design & Test 31.3 (2014): 8-20.
Challenges
Distributed
Scale
Dynamic
Adaptative
Heterogeneous
Safe
Secure
Security
Key Management
Attacks
Energy Consumption
Authentication
Access Control
Access Control
NIST IR 7316 2006
Access control is concerned with providing users with selective access to resources.
NIST SP 800-162 2014
The Purpose of Logical Access Control is to protect objects from unauthorized operations.
Access Control System


3 Abstractions:

¬(p ∧ q)
Policies
Mechanism
Model
Types of
Access Control Systems
Access Control List (ACL)
Role-based Access Control (RBAC)
Attribute-based Access Control (ABAC)
Access Control List (ACL)
resource user:op ------------------ /tmp pablo:rw file.txt pablo:r / root:rwx
Role-based (RBAC)
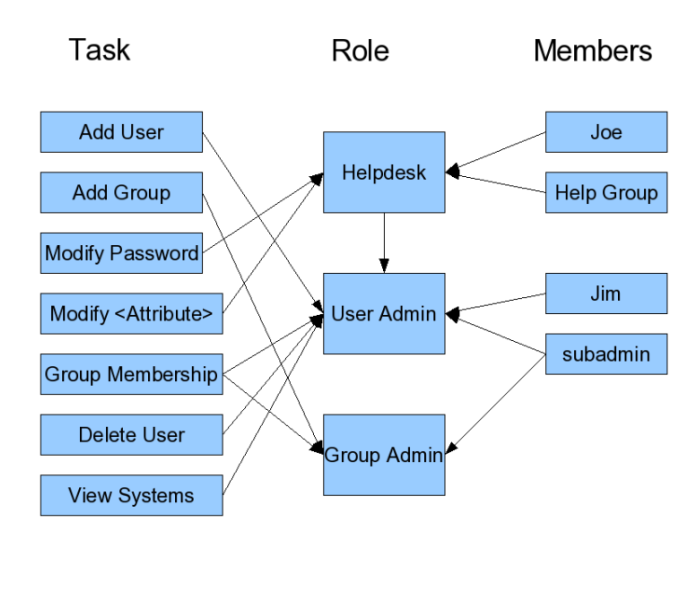
Attribute-based (ABAC)

Attribute-based (ABAC)

Swarm Broker
&
Access Control
The Swarm at the Edge of the Cloud
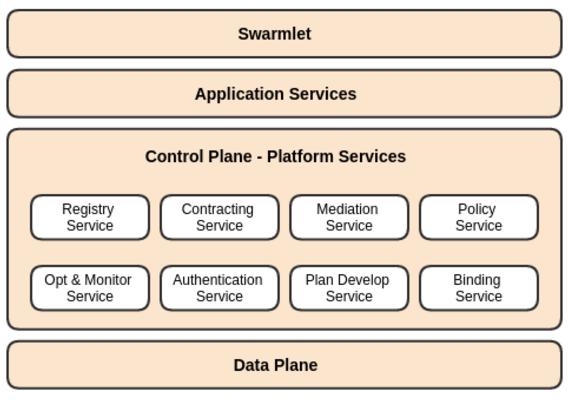

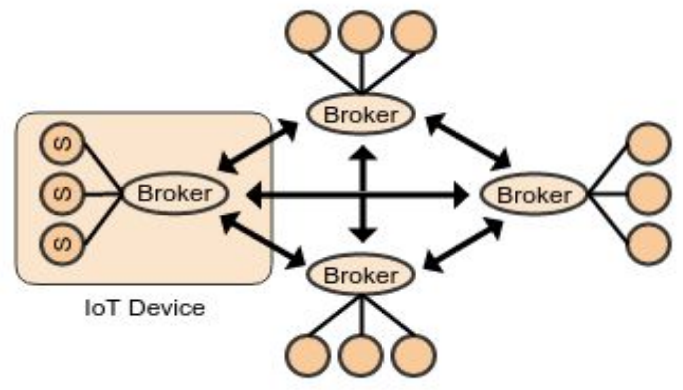
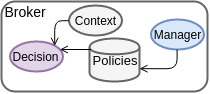
Swarm Broker
The Swarm Broker
Swarm Access Control
-
Attribute-based (ABAC)
-
Initially based on oneM2M specs
-
Very similar to XACML
Swarm Access Control


¬(p ∧ q)
Policies
Mechanism
Model

Policies
{
"id": "1",
"name": "policy 1",
"privileges": [
{
"originators": [
"john",
"rick"
],
"operations": 4,
"contexts": [
{"time_window": ["* * 6-22 * * *"]}
],
"targets": [
"indoorsensor/*",
"indoorsensor/*",
"outdoorsensor/temperature"
]
}
]
}
Mechanism
Policy Enforcement
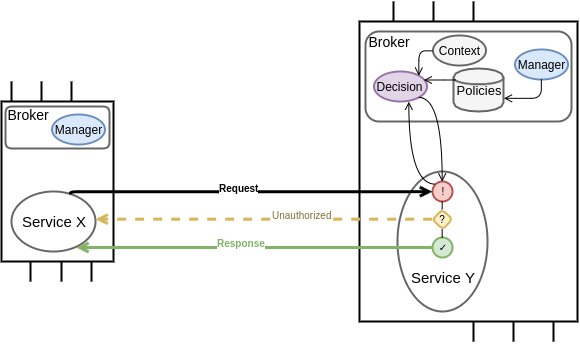
{from=X
op=read
to=Y/value}
GET /value origin: X
originators: ["Z", "X"], operations: 0x02 targets: ["Y/*"]

Mechanism
(ABAC terminology)
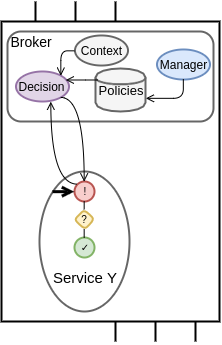
Policy Enforcement Point
(PEP)
Policy Decision Point
(PDP)
Policy Information Point
(PIP)
Policy
Administration
Point
(PAP)

Mechanism
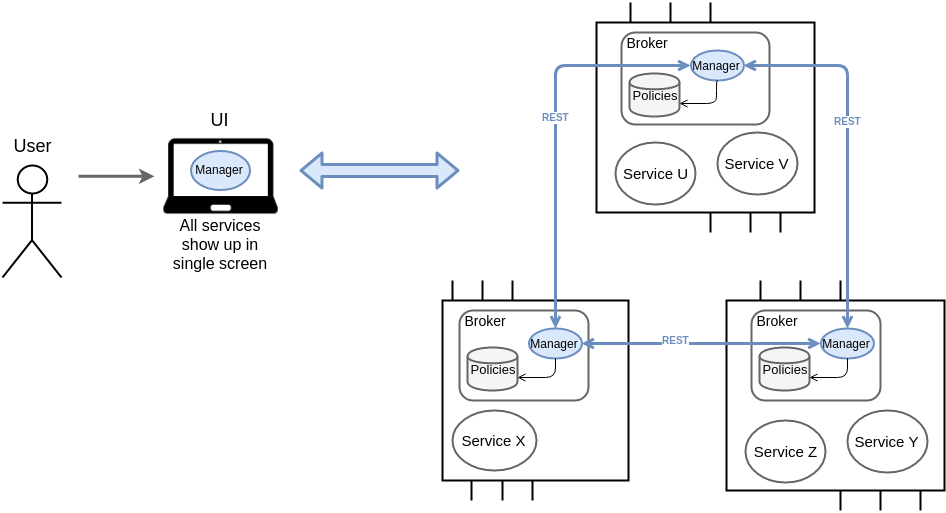
Policy Management

Prototype
Goal:
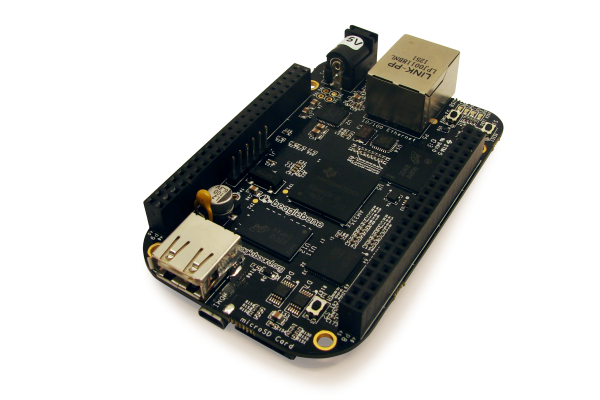
Single Board Computers
Development & Testing:
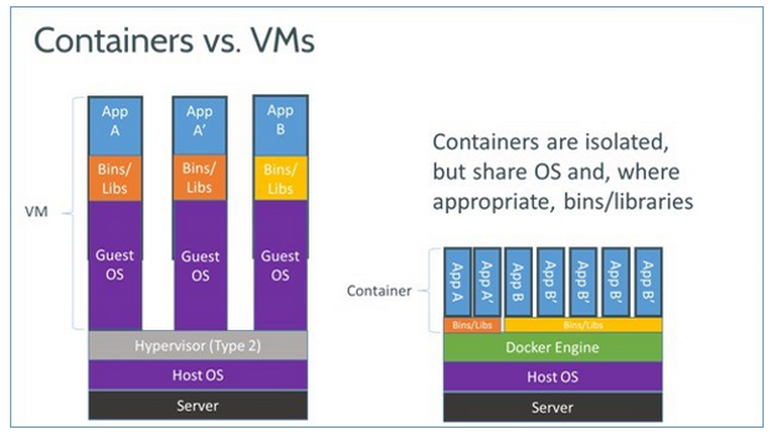
Linux Containers
Platform

Communication
-
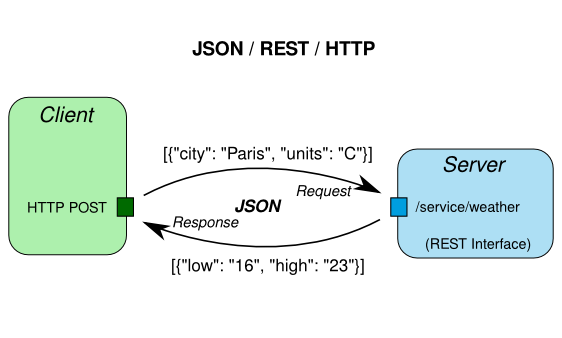
TCP/HTTP
-
REST architecture
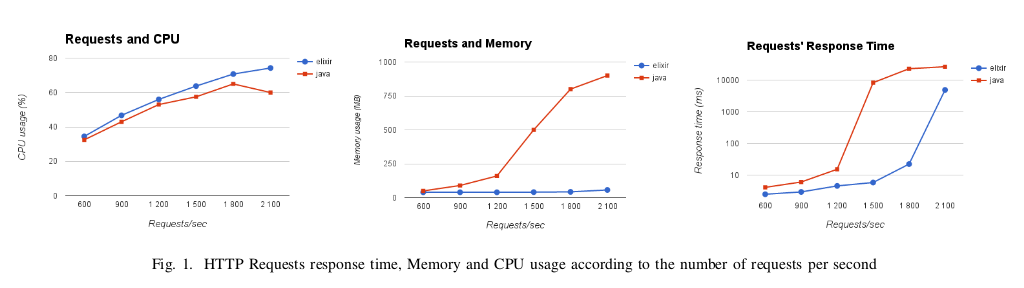
Language:
both Java and Elixir



Elixir libraries


Cowboy webserver

defmodule Sensor.Router do
use Plug.Router
plug :match
plug Plug.Parsers, parsers: [:json], json_decoder: Poison
plug :fetch_sd_params
plug BrokerHTTPClient, :authorize
plug :dispatch
get "/temperature-sensor/value" do
value = Handler.read |> Float.round(1)
resp =
%{"value" => value, "unit" => "celsius"}
|> Poison.encode!
send_resp(conn, 200, resp)
end
enddefmodule BrokerHTTPClient do
def authorize(conn, _opts) do
params = fetch_authz_params(conn)
Logger.info "Called PEP with #{inspect params}"
broker_access_control =
conn.assigns[:broker_url] <> @authorize_path
resp = HTTPoison.get(broker_access_control, [], params: params)
if allowed?(resp) do
conn
else
send_resp(conn, 401, "") |> halt
end
end
end


defmodule BrokerHTTP.Router do
use BrokerHTTP.Web, :router
pipeline :api do
plug :accepts, ["json"]
end
scope "/broker", BrokerHTTP do
pipe_through :api
resources "/registry", RegistryController, only: [:index, :create, :show]
resources "/locate-requests", LocateController, only: [:create] do
resources "/candidates", CandidateController, only: [:index, :create, :show]
end
get "/security/authorize-request", AccessControlController, :index
resources "/security/policies", PolicyController
end
enddefmodule BrokerHTTP.AccessControlController do
use BrokerHTTP.Web, :controller
alias Plug.Conn.Status
def index(conn, %{"fr" => from, "to" => to, "op" => op}) do
req = %Request{from: from, to: to, op: String.to_integer(op), id: nil}
status = if Broker.AccessControl.authorize(req) do
Status.code(:ok)
else
Status.code(:unauthorized)
end
send_resp conn, status, ""
end
enddefmodule Broker.AccessControl.PDP do
def authorize(request) do
acp_rules = PRP.get_applicable_acp request
decision = Enum.reduce(acp_rules, false, fn(rule, acc) ->
acc || match(rule, request)
end)
Logger.info "Authorizing request #{inspect request} resulted in #{decision}"
decision
end
def match(rule, %Request{} = request) do
match_origs(rule, request)
&& match_ops(rule, request)
&& match_targets(rule, request)
&& match_ctxs(rule, PIP.fetch_context(request))
end
end
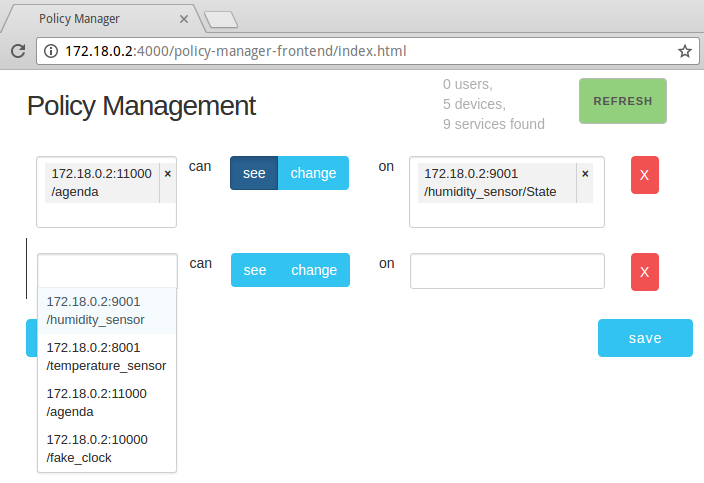
Policy Manager


defmodule BrokerHTTP.Router do
use BrokerHTTP.Web, :router
pipeline :api do
plug :accepts, ["json"]
end
scope "/broker", BrokerHTTP do
pipe_through :api
resources "/registry", RegistryController, only: [:index, :create, :show]
resources "/locate-requests", LocateController, only: [:create] do
resources "/candidates", CandidateController, only: [:index, :create, :show]
end
get "/security/authorize-request", AccessControlController, :index
resources "/security/policies",
PolicyController,
only: [:index, :create, :show, :update, :delete]
end
endPolicy Manager
Demo
Conclusion
Goal: a secure Swarm
Access Control
prototype
Policy Manager
prototype
+


Next steps
Goal: a secure Swarm
-
Authentication
-
Improve Policy Manager & UI
-
Next Generation Access Control (NGAC)

Obrigado!
Geovane Fedrecheski
geonnave@gmail.com
Advisor: Marcelo Zuffo
Nov 2016


Access Control
for the
Swarm
Access Control for the Swarm
By Geovane Fedrecheski
Access Control for the Swarm
- 790



