Web System Security
Jamie Pate
- Sr Web Developer
- Fortinet
- Fortigate firewall appliance

Overview of basic aspects of Web System Security
- Web systems and their threats
- Systems serving web content (http)
- Site data protection (database server)
- Exploits that use the web browser
- Secure Communication
Disect root causes of recent high profile vulnerabilities
- Heartbleed CVE-2014-0160
- Shellshock CVE-2014-6271
- Aftershock CVE-2014-7169
Web Systems
what is a web system
The internet is a Series of tubes
- historically non-secure
- plain text -> https
- connecting (all) computers
- can't block everything
- providing a service
- increasingly complicated systems
- clients and servers

Ever present danger
- Continuous scanning by
- state sponsored organizations
- terrorist organizations
- criminals and criminal organizations
- Server software and OS are inherently insecure
- flaws discovered daily
- even the latest versions
- one weak link exposes the entire system
Links to exploit
- Transport and protocols
- plain text
- ssl/tls and https
- mitm
- Web Serving Software
- holes in Apache, IIS, Nginx etc
- configuration issues
- information disclosure
- xss reflection
CGI - Server programs
Custom code running on a web server
- Fewer eyeballs
- Naive implementations
- validation
- xss
- csrf
- Library imports
- unknown quality
- orphaned code
- ↱

Database
- Parameterized queries
- input sanitation
- whitelisting
or else:
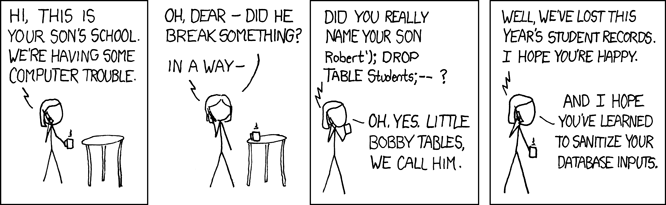
bobby-tables.com
Web Clients
- HTML5 feature explosion
- 19% decrease in 2013
- 47% increase since 2009
- Most browser vulnerabilities patched in less than 30 days.
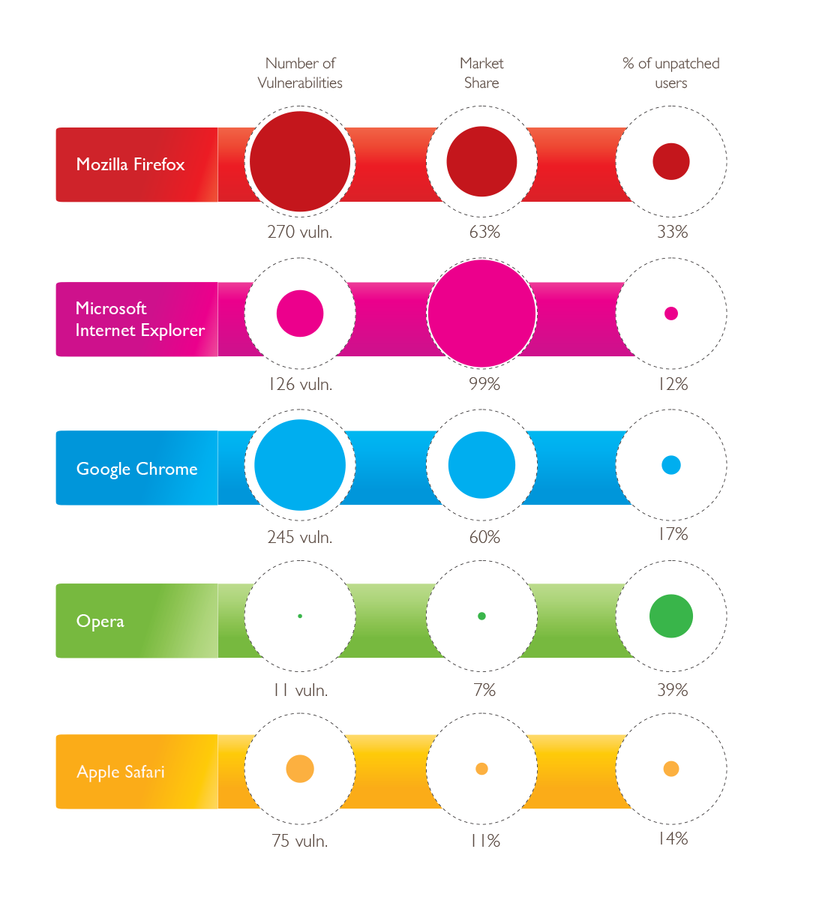
Statistics for 2013
Market share counts installations, not active users
Web Client
Attacks enabled by sites:
- XSS Cross Site Scripting
- Unsanitized user input presented as content
- xss-game.appspot.com
- CSRF Cross Site request forgery
- Trick users into posting to authenticated url
- Prevented with a session-unique CSRF form parameter
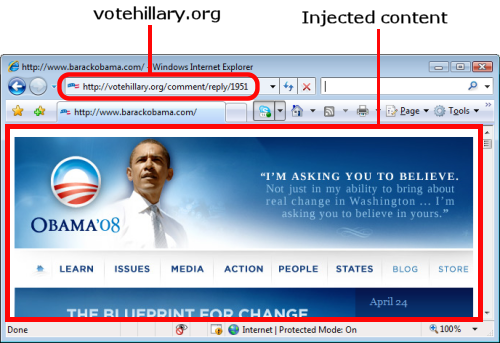
n0p.net 2006


Secure Transport

Transmit via HTTPS
OpenSSL
TLS Heartbeat
April 7th 2014:
A missing bounds check in the handling of the TLS heartbeat extension can be used to reveal up to 64kB of memory to a connected client or server
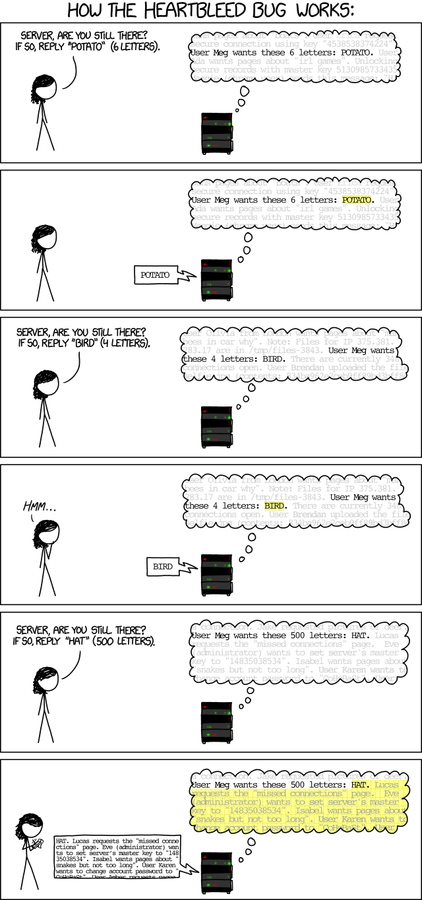
17% of secure web servers(0.5M)
TLS clients using affected OpenSSL instances are also vulnerable
"reverse heartbleed"
Affects products including IP phone systems and telepresence (video conferencing) systems

Root Cause
Buffer under-read:
unsigned int payload;
unsigned int padding = 16; /* Use minimum padding */
/* Read type and payload length first */
hbtype = *p++;
n2s(p, payload); //n2s macro copies 16 bits from p to payload (length) without validation!
pl = p;
if (s->msg_callback)
s->msg_callback(0, s->version, TLS1_RT_HEARTBEAT,
&s->s3->rrec.data[0], s->s3->rrec.length,
s, s->msg_callback_arg);
if (hbtype == TLS1_HB_REQUEST)
{
unsigned char *buffer, *bp;
int r;
/* Allocate memory for the response, size is 1 byte
* message type, plus 2 bytes payload length, plus
* payload, plus padding
*/
buffer = OPENSSL_malloc(1 + 2 + payload + padding); //magic numbers, \o/
bp = buffer;
/* Enter response type, length and copy payload */
//...
/* Random padding */
RAND_pseudo_bytes(bp, padding);
r = dtls1_write_bytes(s, TLS1_RT_HEARTBEAT, buffer, 3 + payload + padding);Resolution
unsigned int payload;
unsigned int padding = 16; /* Use minimum padding */
if (s->msg_callback)
s->msg_callback(0, s->version, TLS1_RT_HEARTBEAT,
&s->s3->rrec.data[0], s->s3->rrec.length,
s, s->msg_callback_arg);
+ /* Read type and payload length first */
+ if (1 + 2 + 16 > s->s3->rrec.length)
+ return 0; /* silently discard */
+ hbtype = *p++;
+ n2s(p, payload); //copy 16 bits from p as payload length
+ if (1 + 2 + payload + 16 > s->s3->rrec.length)
+ return 0; /* silently discard per RFC 6520 sec. 4 */
+ pl = p;
+
if (hbtype == TLS1_HB_REQUEST)
{
unsigned char *buffer, *bp;
+ unsigned int write_length = 1 /* heartbeat type */ +
+ 2 /* heartbeat length */ +
+ payload + padding;
int r;
+ if (write_length > SSL3_RT_MAX_PLAIN_LENGTH)
+ return 0;
+
/* Allocate memory for the response, size is 1 byte
* message type, plus 2 bytes payload length, plus
* payload, plus padding
*/
+ buffer = OPENSSL_malloc(write_length);
bp = buffer;
/* Enter response type, length and copy payload */
//...
/* Random padding */
RAND_pseudo_bytes(bp, padding);
+ r = dtls1_write_bytes(s, TLS1_RT_HEARTBEAT, buffer, write_length);
if (r >= 0 && s->msg_callback)
s->msg_callback(1, s->version, TLS1_RT_HEARTBEAT,
+ buffer, write_length,
s, s->msg_callback_arg);Social Root Causes
Implicit trust of open source
Nobody looked (or admitted to looking)
The code was too horrible
Hoped "upstream" could deal with it.
Perfect storm:
"Horrible code actively discourages outside involvement - the barrier to entry for other developers is too high. Everyone looks at it, and goes back to doing their own stuff, hoping like heck that the upstream maintainers know what they are doing and care"
Enter LibreSSL
Research prompted by heartbleed uncovered a custom malloc() replacement that:
- Never frees memory
- Uses LIFO recycling
Effective as an expoit mitigation countermeasure
- Dire consequences
- Prevents analysis tools like Valgrind and Coverity from detecting memory issues

Shell Shock

Bourne Again SHell
aka "bashdoor"
Environment Variable Expansion
1989-2014 (25 years)
In the beginning there was the command line.
env x = "() { :;}; echo 'u r pwned'| wall"
bash -c "echo am I pwned?"Innocent enough?
Who calls out to bash anyways?
Seriously, who does that anyways?
- Apache HTTP using mod_cgi or mod_cgid
- sshd (bypass ForceCommand)
- Git and Subversion deployments
- DHCPClient!
- Various Daemons and SUID programs
Coding like it's 1989:
+ #define SEVAL_FUNCDEF 0x080 /* only allow function definitions */
+ #define SEVAL_ONECMD 0x100 /* only allow a single command */Opaque state machines!
strcpy (temp_string + char_index + 1, string);
- if (posixly_correct == 0 || legal_identifier (name))
- parse_and_execute (temp_string, name, SEVAL_NONINT|SEVAL_NOHIST);
-
- /* Ancient backwards compatibility. Old versions of bash exported
- functions like name()=() {...} */
- if (name[char_index - 1] == ')' && name[char_index - 2] == '(')
- name[char_index - 2] = '\0';
+ /* Don't import function names that are invalid identifiers from the
+ environment, though we still allow them to be defined as shell
+ variables. */
+ if (legal_identifier (name))
+ parse_and_execute (temp_string, name, SEVAL_NONINT|SEVAL_NOHIST|SEVAL_FUNCDEF|SEVAL_ONECMD);
if (temp_var = find_function (name))'Old' versions of bash...
report_error (_("error importing function definition for `%s'"), name);
}
-
- /* ( */
- if (name[char_index - 1] == ')' && name[char_index - 2] == '\0')
- name[char_index - 2] = '('; /* ) */
}
#if defined (ARRAY_VARS) dispose_fd_bitmap (bitmap);
discard_unwind_frame ("pe_dispose");
+
+ if (flags & SEVAL_ONECMD)
+ break;
}
}Only evaluate one.
struct fd_bitmap *bitmap;
+ if ((flags & SEVAL_FUNCDEF) && command->type != cm_function_def)
+ {
+ internal_warning ("%s: ignoring function definition attempt", from_file);
+ should_jump_to_top_level = 0;
+ last_result = last_command_exit_value = EX_BADUSAGE;
+ break;
+ }
+
bitmap = new_fd_bitmap (FD_BITMAP_SIZE);
begin_unwind_frame ("pe_dispose");Only allow function definitions (don't call them!)
Social Cause
- The flaws in Bash were in a quite obscure feature that was rarely used.
- Most of Bash was written in 1989. C code style has come a long way
- Code appears to have grown organically, liberal use of global variables
goto return0;
}
- else if (var = find_variable_last_nameref (temp1))
+ else if (var && (invisible_p (var) || var_isset (var) == 0))
+ temp = (char *)NULL;
+ else if ((var = find_variable_last_nameref (temp1)) && var_isset (var) &&
+ invisible_p (var) == 0)
{
temp = nameref_cell (var);I don't even.... invisible_p? (global!)
- Scrutiny caused by shellshock revealed that the fix was incomplete.
- At least 5 more vulnerabilities
- privilege escalation
- DOS
- memory corruption, and possible arbitrary code execution
- Generally not as ... shocking

Web System Security
Web security has many layers
- Http daemon
- Database
- Browser/client
- Network
All the moving pieces must be secured individually and as a whole system

Many eyes do help, they must be active
Top 10 Intrusions
- Bash.Function.Definitions.Remote.Code.Execution
- OpenSSL.ChangeCipherSpec.Injection
- PHP.CGI.Argument.Injection
- OpenSSL.TLS.Heartbeat.Information.Disclosure
- HTTP.URI.SQL.Injection
- Joomla.JCE.Extension.Remote.File.Upload
- HTTP.XXE
- OpenSSL.Heartbleed.Attack
- Open.Flash.Chart.PHP.File.Upload
- Adobe.Flash.Player.Argument.Index.Memory.Corruption
http://www.fortiguard.com/fortiguard_labs/threat_monitor
Wouldn't You Prefer A Nice Game Of Chess?
eece412 web security
By Jamie Pate
eece412 web security
- 2,583



