Password-Free Authentication


@jochen_christ
Dev && Consultant
Quiz
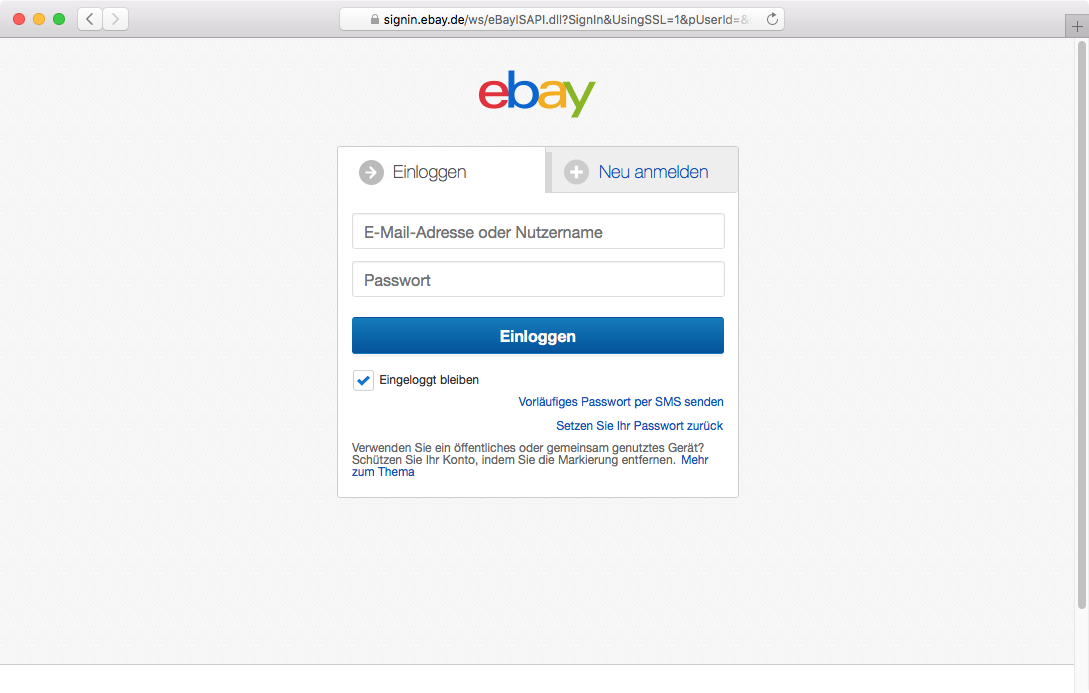


All major Websites use Passwords
10/10 of Top Sites by Alexa Page Rank as of August 1, 2017 and
10/10 of Most Downloaded iOS Apps in 2016 use password credentials or federated logins with passwords credentials
The Problem with Passwords
Problem #1
Passwords
are stolen
All previous sites reported data breaches
https://en.wikipedia.org/wiki/List_of_data_breaches
Problem #2
Passwords
are weak
| Username | Salt value | String to be hashed | Hashed value = SHA256 (Password + Salt value) |
|---|---|---|---|
| user1 | E1F53135E559C253 | password123+E1F53135E559C253 | 72AE25495A7981C40622D49F9A52E4F1565C90F048F59027BD9C8C8900D5C3D8 |
| user2 | 84B03D034B409D4E | password123+84B03D034B409D4E | B4B6603ABC670967E99C7E7F1389E40CD16E78AD38EB1468EC2AA1E62B8BED3A |
Best Practice: Salting
https://en.wikipedia.org/wiki/Salt_(cryptography)
GPU Brute-Force








| Chars | Length | Example | Days |
|---|---|---|---|
| 94 | 6 | 8(Ve>r | 0 |
| 62 | 8 | 4C4dkD5p | 0 |
| 94 | 8 | F,nB4r=$ | 0,1 |
| 94 | 10 | X9Zq-Sz,zQ | 1385 |
| 62 | 20 | 5UiqgFLmlL8KlnTqm580 | 1E19 |
MD5 (Unix, Postgres)
Time to brute force all hashes on 1 AWS p3.16xlarge with hashcat 4
https://hashcat.net/forum/thread-6972.html
SHA512 (Ubuntu)
Time to brute force all hashes on 1 AWS p3.16xlarge with hashcat 4
https://hashcat.net/forum/thread-6972.html
| Chars | Length | Example | Days |
|---|---|---|---|
| 94 | 6 | 8(Ve>r | 0 |
| 62 | 8 | 4C4dkD5p | 0,1 |
| 94 | 8 | F,nB4r=$ | 4 |
| 94 | 10 | X9Zq-Sz,zQ | 36.076 |
| 62 | 20 | 5UiqgFLmlL8KlnTqm580 | 4E20 |
BCrypt
Time to brute force all hashes on 1 AWS p3.16xlarge with hashcat 4
https://hashcat.net/forum/thread-6972.html
| Chars | Length | Example | Days |
|---|---|---|---|
| 94 | 6 | 8(Ve>r | 18 |
| 62 | 8 | 4C4dkD5p | 5822 |
| 94 | 8 | F,nB4r=$ | 162.562 |
| 94 | 10 | X9Zq-Sz,zQ | 1E9 |
| 62 | 20 | 5UiqgFLmlL8KlnTqm580 | 1E25 |
PBKDF2 (OSX 10.8+)
Time to brute force all hashes on 1 AWS p3.16xlarge with hashcat 4
https://hashcat.net/forum/thread-6972.html
| Chars | Length | Example | Days |
|---|---|---|---|
| 94 | 6 | 8(Ve>r | 41 |
| 62 | 8 | 4C4dkD5p | 13.000 |
| 94 | 8 | F,nB4r=$ | 365.000 |
| 94 | 10 | X9Zq-Sz,zQ | 3E9 |
| 62 | 20 | 5UiqgFLmlL8KlnTqm580 | 4E25 |
Office 2013
Time to brute force all hashes on 1 AWS p3.16xlarge with hashcat 4
https://hashcat.net/forum/thread-6972.html
| Chars | Length | Example | Days |
|---|---|---|---|
| 94 | 6 | 8(Ve>r | 48 |
| 62 | 8 | 4C4dkD5p | 15.500 |
| 94 | 8 | F,nB4r=$ | 432.000 |
| 94 | 10 | X9Zq-Sz,zQ | 3E9 |
| 62 | 20 | 5UiqgFLmlL8KlnTqm580 | 5E25 |
Android PIN
Time to brute force all hashes on 1 AWS p3.16xlarge with hashcat 4
https://hashcat.net/forum/thread-6972.html
| Chars | Length | Example | Days |
|---|---|---|---|
| 94 | 6 | 8(Ve>r | 0 |
| 62 | 8 | 4C4dkD5p | 27 |
| 94 | 8 | F,nB4r=$ | 757 |
| 94 | 10 | X9Zq-Sz,zQ | 6.696.000 |
| 62 | 20 | 5UiqgFLmlL8KlnTqm580 | 8E22 |
1Password
Time to brute force all hashes on 1 AWS p3.16xlarge with hashcat 4
https://hashcat.net/forum/thread-6972.html
| Chars | Length | Example | Days |
|---|---|---|---|
| 94 | 6 | 8(Ve>r | 0 |
| 62 | 8 | 4C4dkD5p | 49 |
| 94 | 8 | F,nB4r=$ | 1371 |
| 94 | 10 | X9Zq-Sz,zQ | 12.120.331 |
| 62 | 20 | 5UiqgFLmlL8KlnTqm580 | 1E23 |
How to crack Linux Passwords
adduser jochen
tail /etc/shadow
jochen:$6$BCdbmeYs$7nTt9u6RDDbaHF5r59AP9DpVmy33Vx7AUFGtL64fUUrFlR5haXPUBJK3RZ8/QM1sQn0ljTGzUHD.q22UYryID0:17499:0:99999:7:::
apt-get install hashcat
hashcat -m 1800 -a 3 '$6$BCdbmeYs$7nTt9u6RDDbaHF5r59AP9DpVmy33Vx7AUFGtL64fUUrFlR5haXPUBJK3RZ8/QM1sQn0ljTGzUHD.q22UYryID0' ?l?l?l?l?l?l
Problem #3
Passwords
are reused
87%
reuse passwords on multiple sites
https://keepersecurity.com/assets/pdf/Keeper-Mobile-Survey-Infographic.pdf
Problem #4
Difficult to create
Typical Password Policy
- Min 8 characters
- Uppercase
- Lowercase
- Digits
- Special Charachters
- No Dictionary Word
Study:
83% need 4 attempts (avg) for a valid string
https://www.nist.gov/publications/passwords-and-people-measuring-effect-password-composition-policies
😡
25% completely failed
Problem #5
Hard to remember
Experiment:
Remember that password
bT,t1K=+lf
Now, write down that password
Problem #6
Inconvenient to enter
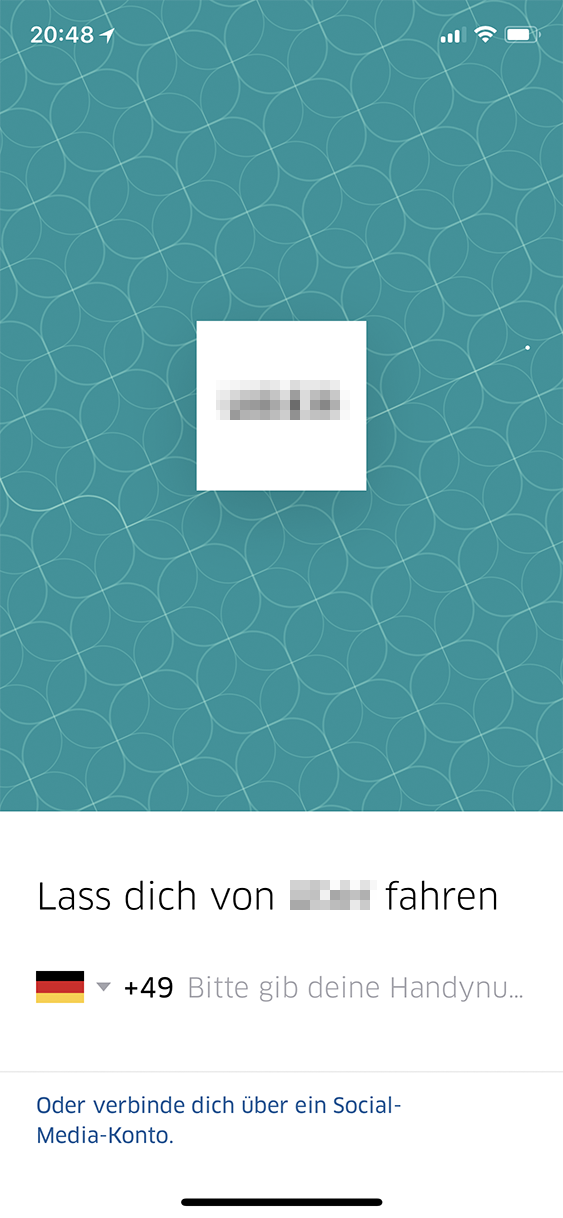
Passwords are omnipresent,
yet insecure and inconvenient.
Yes,
there are alternatives
Authentication Factors
KNOWLEDGE
Something only the user knows

PINs
Passwords
Security Questions
Gestures
Private URLs
Current Account Balance
Place of a hidden item
POSSESSION
Something only the user has
Smartcard
USB-Token
TAN-List
Mobile Phone
Key
INHERENCE
Something only the user is
Fingerprint
Voice
Iris
Face
Skin Color
Birthmark
Tattoo
Key strike sequences

TIME
A time only the user can be at
LOCATION
A place where only the user can be
ABILITY
Something only the user can do
Password-Free Authentication Methods
SSH Private Key
# Generate a private and public keys
ssh-keygen -t rsa
# Save the public key on the target host
cat ~/.ssh/id_rsa.pub | ssh user@hostname 'cat >> .ssh/authorized_keys'
# Now you can login without password
ssh user@hostname
#
git clone https://github.com/dev-night/talks.gitUSB Dongle
YubiKey

Magic Link

Authentication Factor
Knowledge / Federated
Magic Link
Strengths
Einfach
Komplett ohne Passwort
Weaknesses
Abhängigkeit zu E-Mail
Dauer, Spam-Gefahr
Usability
Applicability
einfach zu verstehen /
aber E-Mail nicht immer parat
✓ Custom Websites
✓ Custom Apps
Integration
Fertige Library
Magic Link
- Relies on Mail System
- Access Token/Link in Mail Body
- Simple to Use
- No registration required
- Convenient for infrequent Logins
- Mails are unencrypted
- Same security as Password Reset feature
One Time Code
over SMS
Windows Hello
Face Recognition
Authentication Factor
Inherence / Face
Windows Hello
Strengths
Einfach, ziemlich Fälschungssicher
Weaknesses
Entführungsgefahr, Unzuverlässigkeit, kann nicht weitergegeben werden, Registrierung notwendig, Datenschutzbedenken
Usability
Applicability
Einfach, wenn verfügbar
✘ Custom Websites
? Custom Apps
Integration
Hardware notwendig
Google Hands-Free
Authentication Factor
...
Google Hands-Free
Strengths
...
Weaknesses
...
Usability
Applicability
...
✓/ ✘ Custom Websites
✓/ ✘ Custom Apps
Integration
...
Social Login
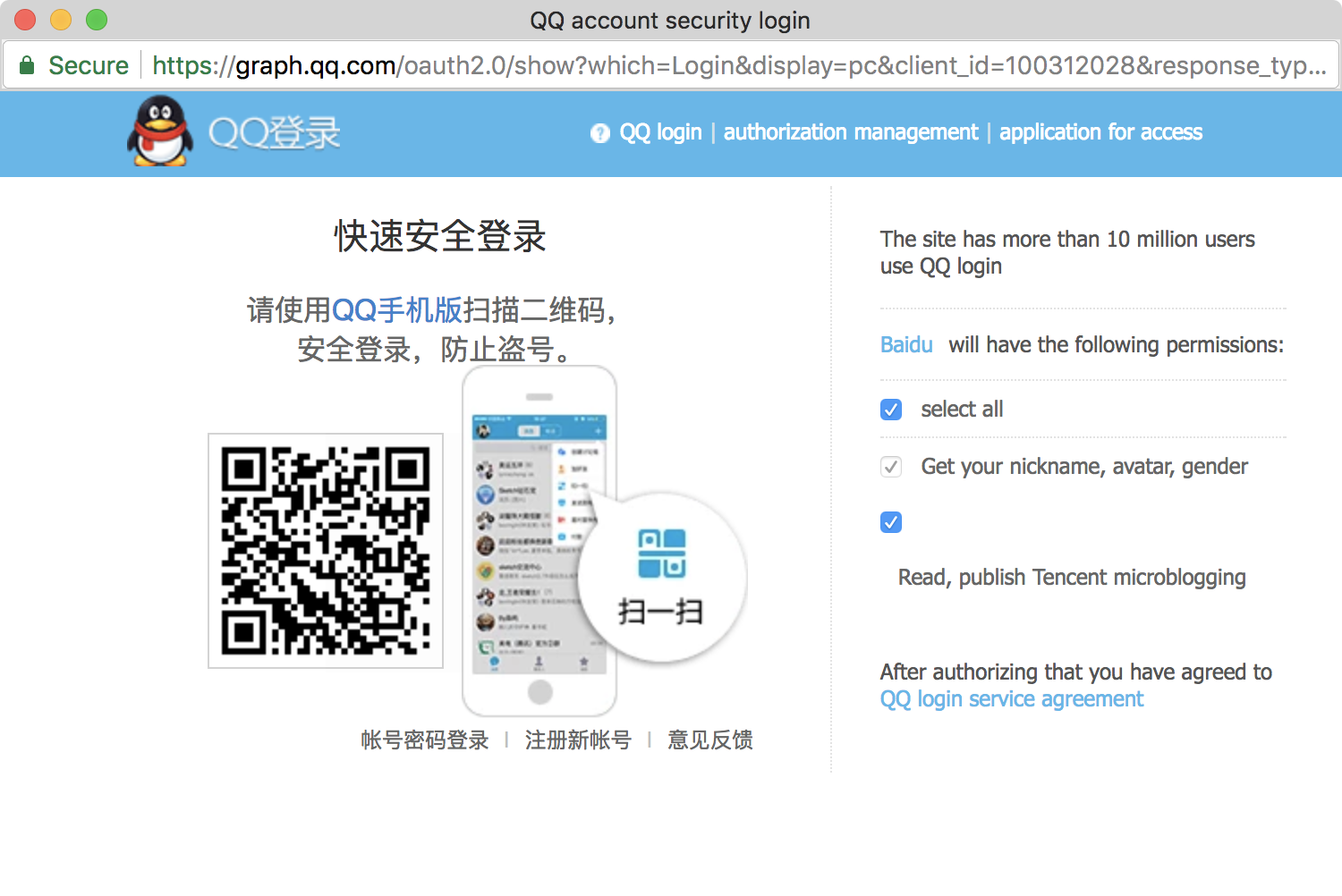
Authentication Factor
...
Social Login
Strengths
...
Weaknesses
...
Usability
Applicability
...
✓/ ✘ Custom Websites
✓/ ✘ Custom Apps
Integration
...
Authentication App
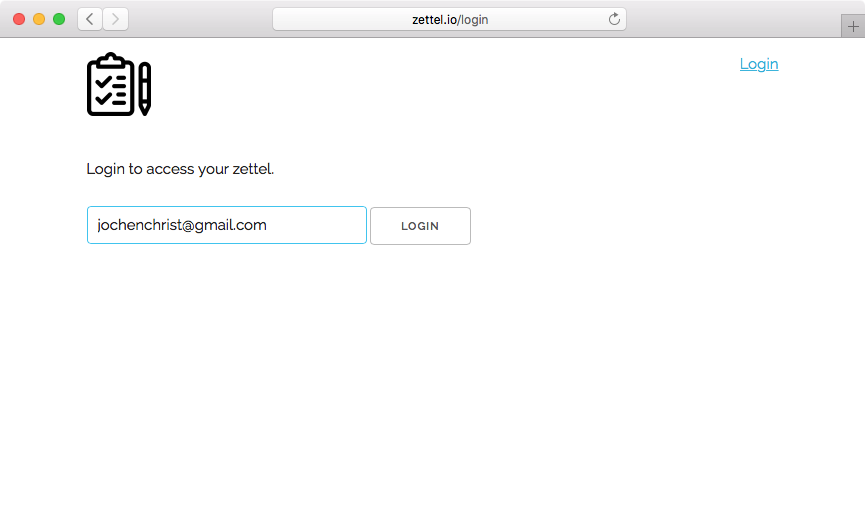
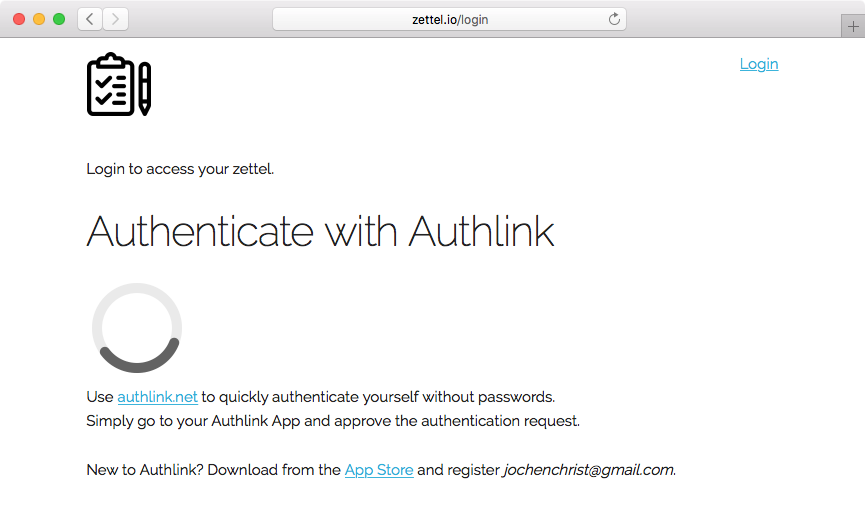

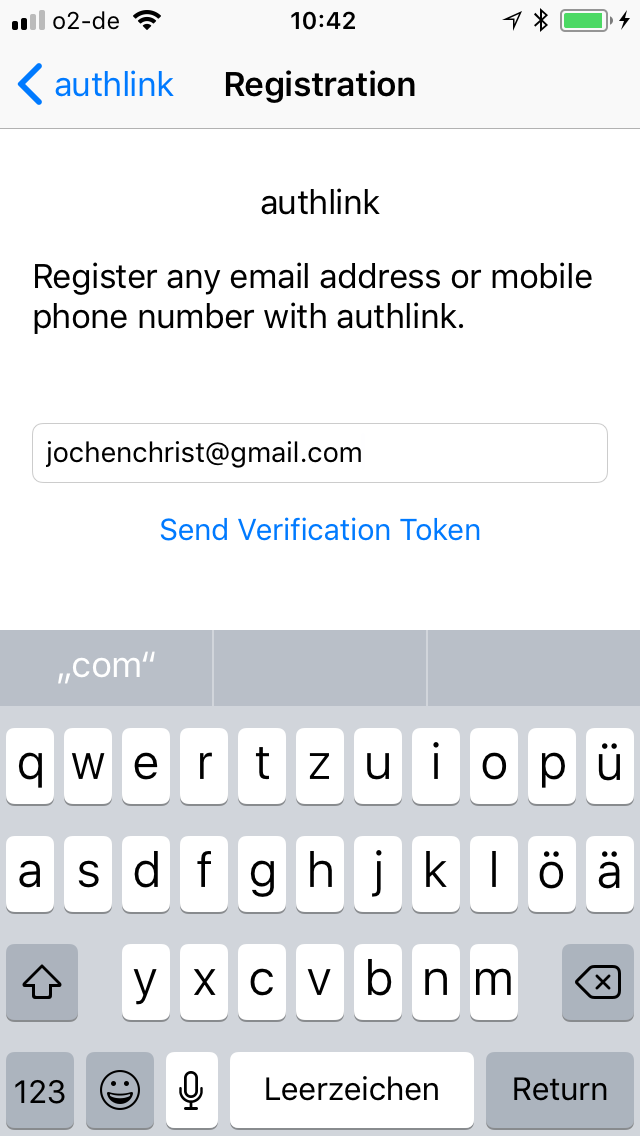
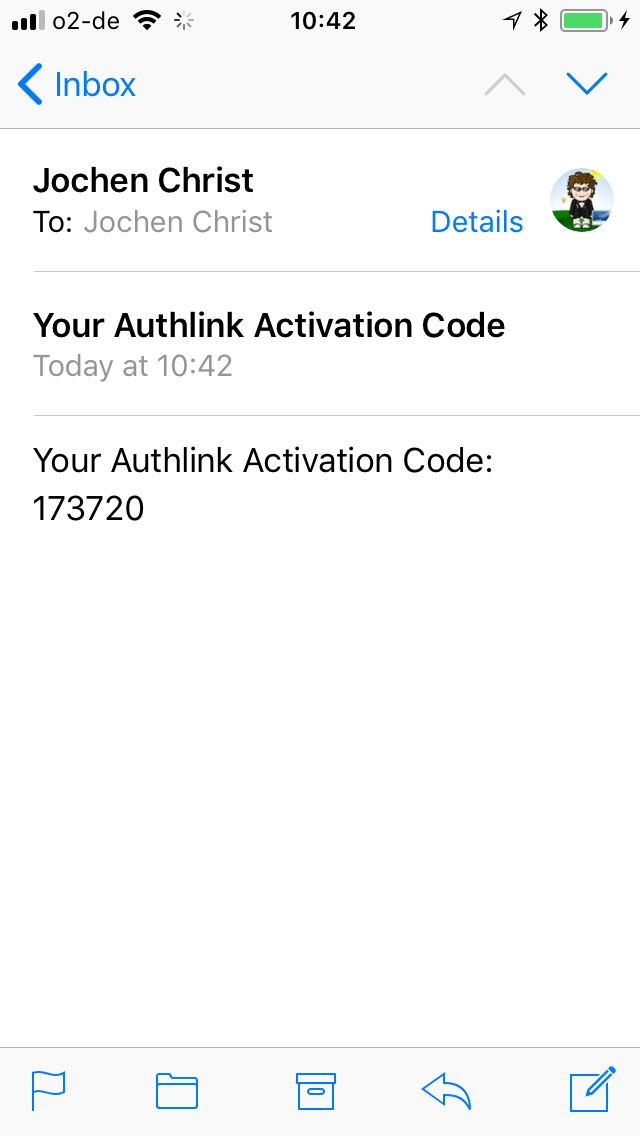
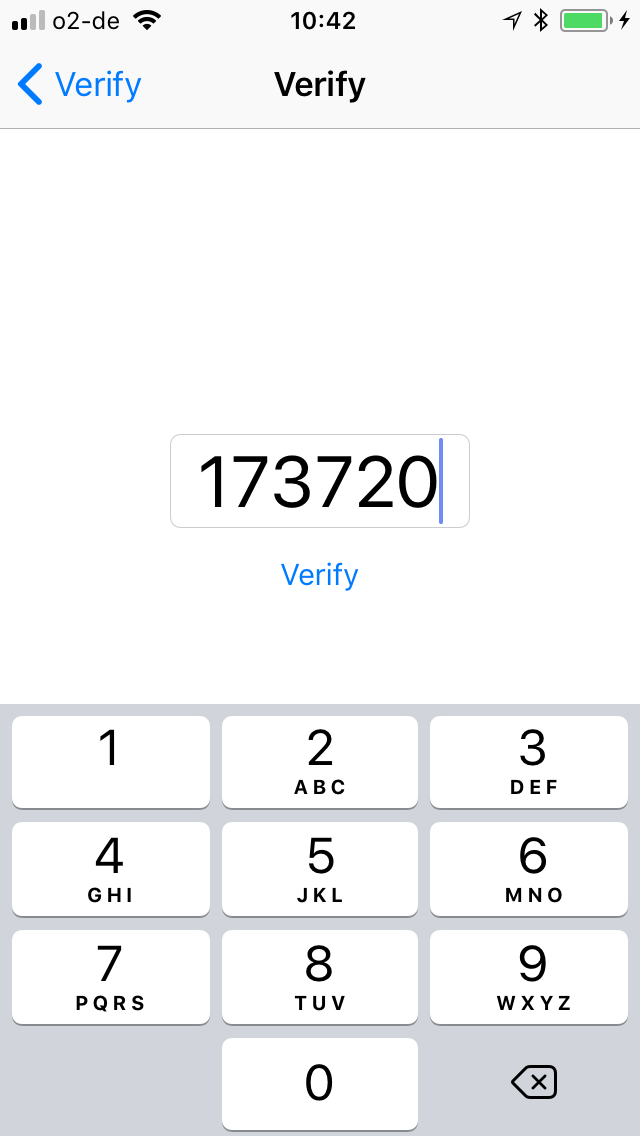
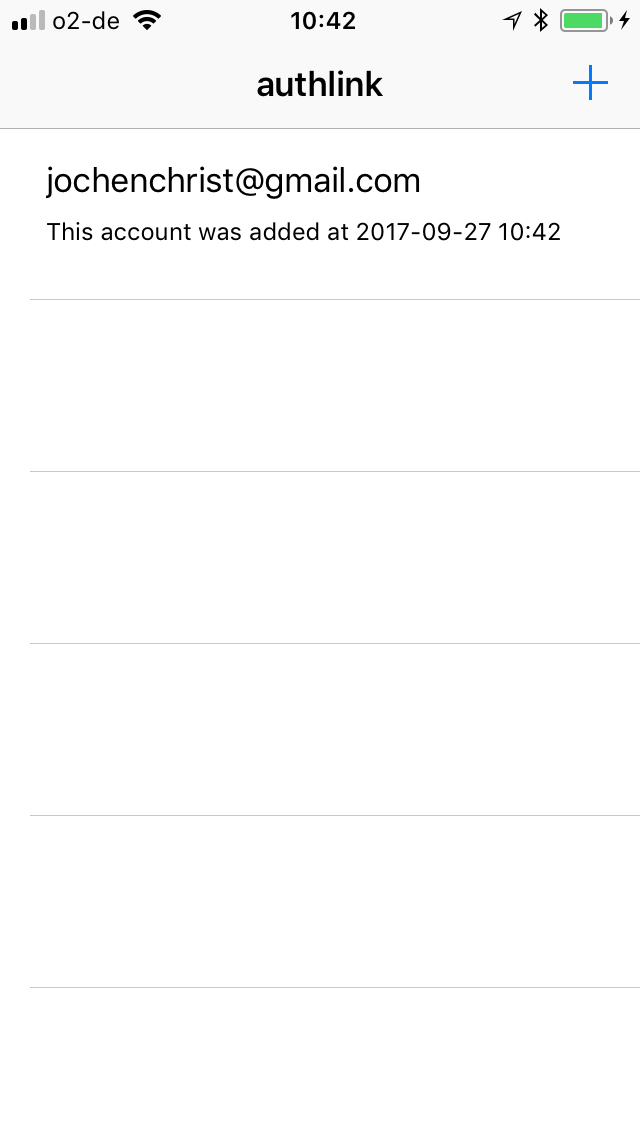
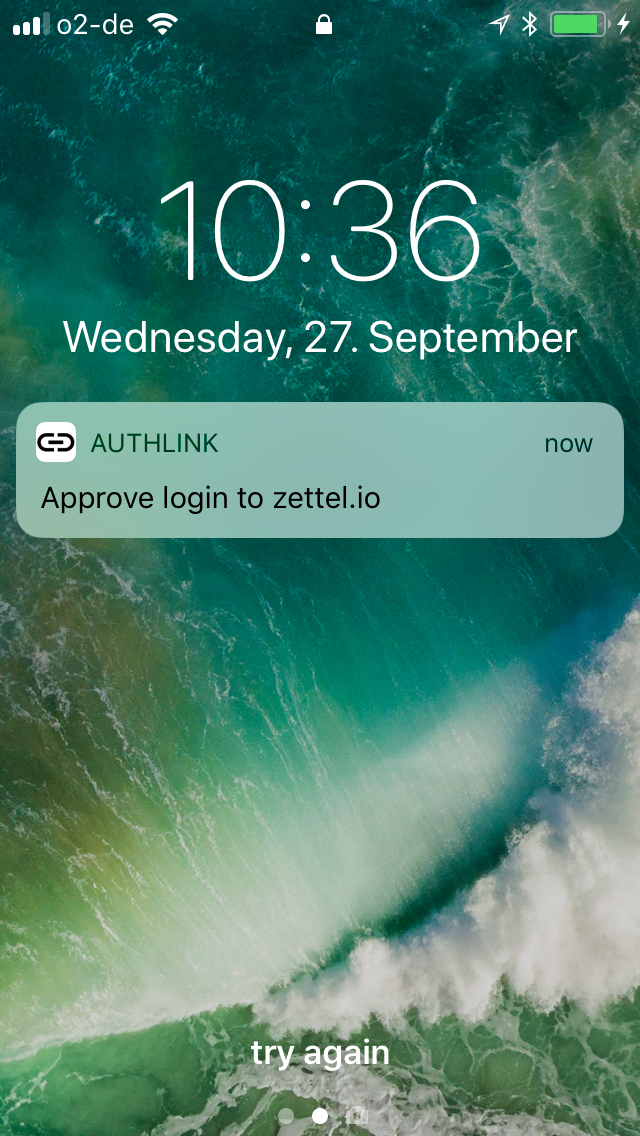
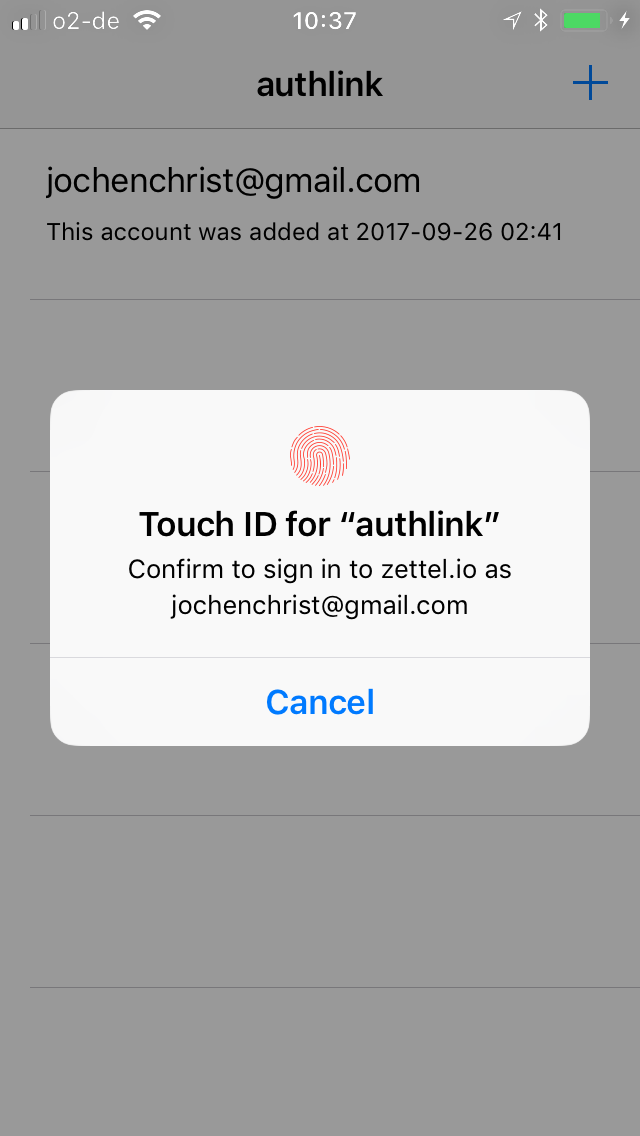
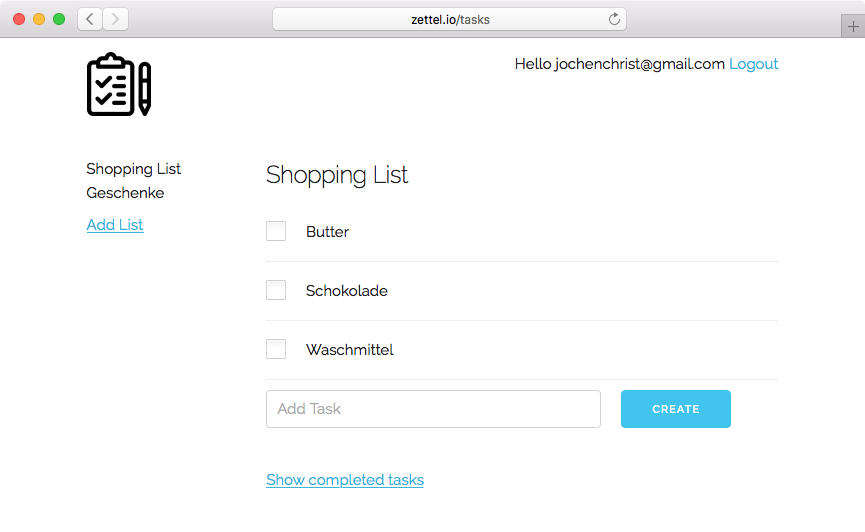
POST https://api.authlink.net/authentications
{
"client" : "zettel.io",
"user" : "jochenchrist@gmail.com"
}
HTTP/1.1 201 Created
{
"status" : "PENDING",
"_links" : {
"token" : {
"href" :
"https://api.authlink.net/authentications/35547ba8-1903-4355-97a4-d3e9b3ace25e/token"
}
}
}
GET https://api.authlink.net/authentications/35547ba8-1903-4355-97a4-d3e9b3ace25e/tokenHTTP/1.1 200 OK
{
"status" : "VERIFIED",
"accessToken" : "eyJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJqb[truncated...]"
}
Authentication Factor
...
Authentication App
Strengths
...
Weaknesses
...
Usability
Applicability
...
✓/ ✘ Custom Websites
✓/ ✘ Custom Apps
Integration
...
Upcoming Specs:
FIDO UAF /
W3C Webauthn
https://www.slideshare.net/FIDOAlliance/fido-uaf-10-specs-overview-and-insights-60000803
My Recommendations for Users
- Accept the fact that services are or will be hacked
- Use 20 char random passwords
- Use password managers (with strong password)
- It's OK to use social logins
- Enable 2FA for work or real sensitive accounts
My Recommendations for
Product Owners and Devs
- Accept the fact that services are or will be hacked
- Provide alternatives to password logins
- Magic-Links
- Social Logins
- Allow passwords > 20 chars
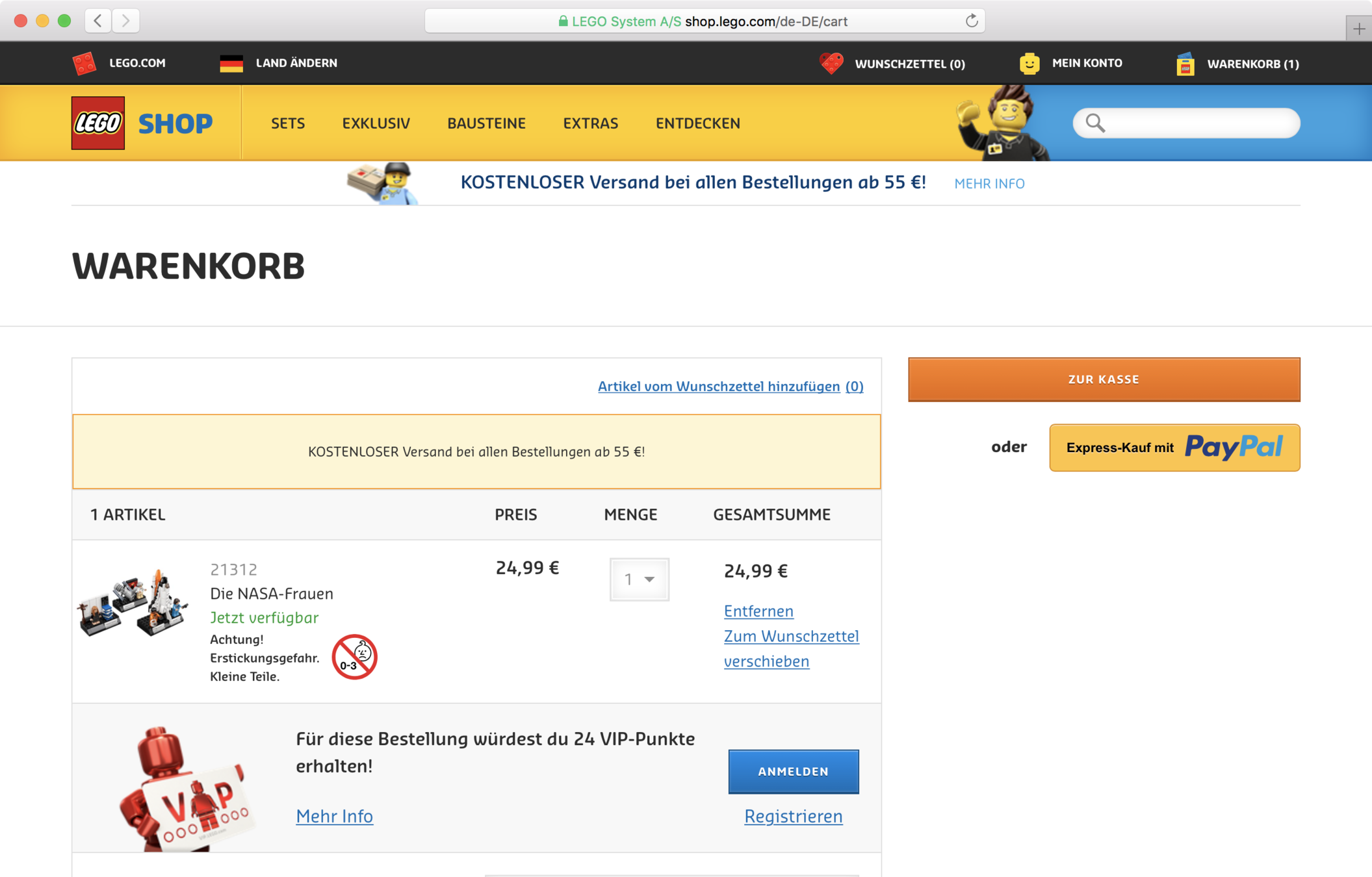
- Webshops: Allow Guest Check-Out
- Check your Hash-Algorithm:
Use BCrypt or a HSM to hash passwords - Lock account after 5 failed login attempts
- Block IP after ~50 failed login attempts
USABILITY > SECURITY
Final Thoughts
Backup
- https://medium.com/@iraklis/running-hashcat-v4-0-0-in-amazons-aws-new-p3-16xlarge-instance-e8fab4541e9b
- https://crackstation.net/buy-crackstation-wordlist-password-cracking-dictionary.htm
Password-Free Authentication (/dev/night)
By jochenchrist
Password-Free Authentication (/dev/night)
- 377

