Basic Local Security Principles
Shivani Bhardwaj
ILUG-D and LinuxChix India | Dec 3, 2016
User accounts
- Only authenticated users can access files and applications
- Commands: useradd and userdel
- /etc/passwd file
Security checks
- Linux distinguishes between several account types in order to isolate processes and workloads.
- Grant the minimum privileges possible and necessary to accounts, and remove inactive accounts.
- Commands: last and lastb
Root
What is root?
- Most privileged account
- No security restrictions imposed
- The shell prompt displays '#'
Picture by: The Linux Foundation
Do you always have to be root?
- SUID (Set owner User ID upon execution—similar to the Windows "run as" feature)
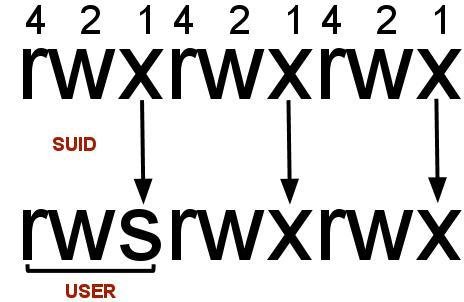
Are system upgrades really needed?
- Bug fixes and performance improvements
- Most of successful attacks come from exploiting security holes for which fixes are already known but not universally deployed.
The mighty thing called sudo.
su
- the root password
- user can do anything that the root user can
sudo
- the user’s password
- what the user is allowed to do can be precisely controlled and limited.
Why sudo is awesome?
- sudo has the ability to keep track of unsuccessful attempts at gaining root access.
- When trying to execute sudo bash without successfully authenticating the user, error is logged.
- Configuration information stored in the /etc/sudoers file and in the /etc/sudoers.d directory.
- Edit the sudoers file by using visudo
Linux is secure.
Process isolation
- Processes are naturally isolated from each other.
- Linux thus makes it difficult (though certainly not impossible) for viruses and security exploits to access and attack random resources on a system.
Playing with Passwords
Storage of passwords
- /etc/passwd
- /etc/shadow
Algorithm
- SHA-512
- sha512sum
Good practices
- Password aging
- Pluggable Authentication Modules (PAM)
- Use password cracking tools to determine if your password is weak
Securing boot process (GRUB 2)
- To prevent someone from bypassing the user authentication step.
- grub-mkpasswd-pbkdf2
- sudo vim /etc/grub.d/40_custom
set superusers=”username”
password_pbkdf2 username password_String_generated- sudo update-grub
That's all folks!
Local Security Principles
By Shivani Bhardwaj
Local Security Principles
Basic security principles in Linux | LinuxChix India + ILUG-D meetup Dec 3, 2016
- 726



