Javascript Security
"an insecure mess"
High level overview

High level overview

Introducing

JSprime is a light-weight source code scanner for identifying security issues (DOM XSS) using static analysis
It is written in JavaScript to analyze JavaScript

How it works ?
-
It pushes the code to Esprima, to generate AST
-
Parse the JSON AST, to locate all sources and keeping track of their scopes.
-
Parse the AST, to locate sinks and sink aliases keeping trak of the scope they are in.
-
Parse AST to locate functions which are fed with sources as arguments.

How it works ?
-
Once all the sources are collected it will remove the sources which won't pass a set of predefined filters.
-
Remaining sources are tracked for assignments or pass as argument operation to the collected sinks.
-
After that a report is generated with different color coding.

Demo time.

What it can't do?
-
It can't detect 100% of the issues.
-
It can't learn sources and sinks automaticaly.
-
It can't handle obfuscated JavaScript.
-
It can't analyze dynamically generated JavaScript using 'eval' or similar methods.
What about the rest of the code ?
Introducing Retire.js
"What you require you must also retire."
Can scan a web application or node app for use of vulnerable JavaScript libraries and Node modules.
Retire.js
It can be run in multiple ways:
-
Command line scanner
-
Grunt/Glup plugin/task
-
Chrome and Firefox extension
How it works ?
Retire.js
How it works ?
(focus on command line)
Running "retire" in cmd on the root of the application.
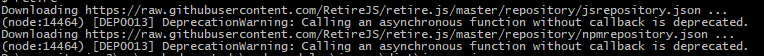
After that the tool will check the libraries dependencies used in the project and compare them to the ones listed in the 2 files.
Retire.js
How it works ?
(focus on command line)
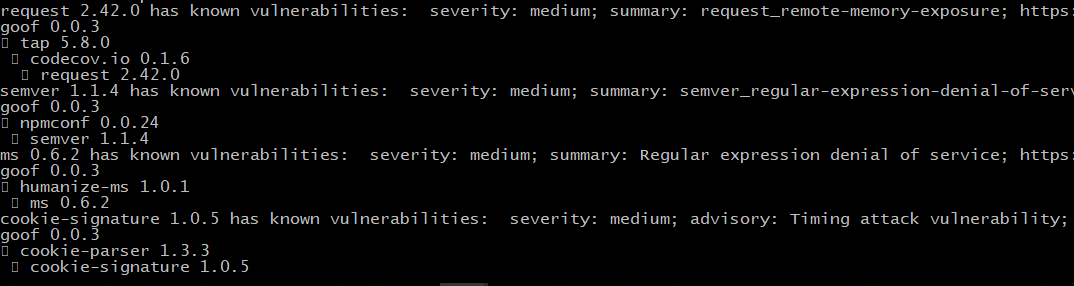
ReDOS
The Regular expression Denial of Service (ReDoS) is a Denial of Service attack, that exploits the fact that most Regular Expression implementations may reach extreme situations that cause them to work very slowly (exponentially related to input size)
XSS
Cross-site scripting is a type of computer security vulnerability typically found in web applications. XSS enables attackers to inject client-side scripts into web pages viewed by other users
Directory traversal
Directory traversal is an HTTP exploit which allows attackers to access restricted directories and execute commands outside of the web server's root directory. Web servers provide two main levels of security mechanisms. Access Control Lists (ACLs) Root directory.
Remote Memory Exposure
~ no formal definition found ~
As an example if we initialize a Buffer with a fix size the buffer should hold a space of data that is empty - if this dose not happen (and a 3d party can get a reference to the newly created Buffer) then we can say we have a remote memory exposure
Timing attack vulnerability
&
Heap spraying
Couldn't find any way of showcasing this...
Javascript Security
By Stefan Hagiu
Javascript Security
- 580



