Attacking the enterprise security.
A guide for office managers and sales people
What security is not...
1
A theater
2
A firewall, antivirus, IDS/IPS

3
A gun or knife in your pocket
4
Security is a process
5
Security is a chain, it is as strong as it's weakest link
6
Security is a compromise

7
Information security...
... protects the confidentiality, integrity, and availability of information on the devices that store, manipulate, and transmit the information through products, people, procedures
8
CIA triad
9
Security layers
Products. People. Procedures.
10
How can the confidential data get compromised?
11
- Social Engineering
- Phishing
- USB key malware
- Scanning from the Internet
- Guessing/brute-forcing passwords
- WiFi
- Stolen credentials
- Using password recovery functionality
- Insider information
- And many more...
12
Exploiting trust
13
In technology...
Core Internet protocols (ARP, SMTP, FTP, DNS)
14
In humans...
Social Engineering, phishing, etc
15
Spot the attacker

16
Common scenario
17
- Reconnaissance
- Scanning and enumeration
- Gaining access
- Escalation of privilege
- Maintaining access
- Covering tracks and placing backdoors
18
Facebook, LinkedIn, Google
19

A story of Adam Penenberg hack
http://www.pcworld.com/article/2070671/anatomy-of-a-hack-team-meets-a-professors-challenge.html
20
Sucking data out of corporate network without wireless device
Johnny Long
21
22
23
24



25
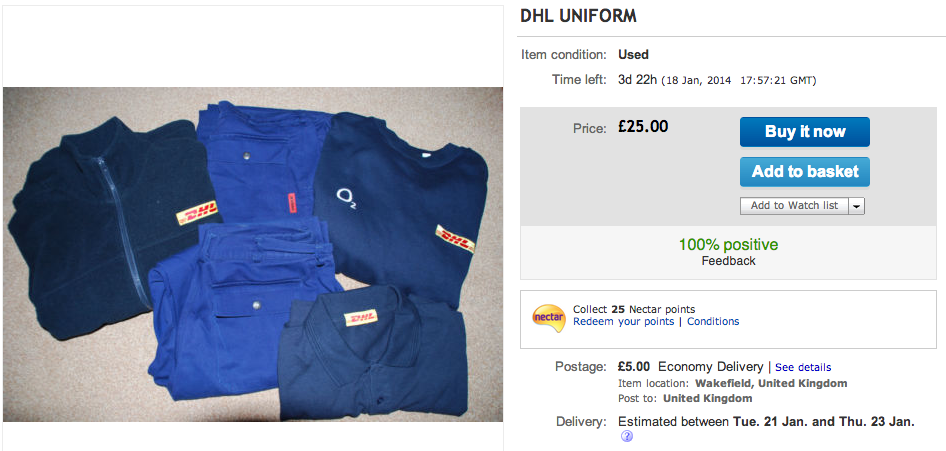
26
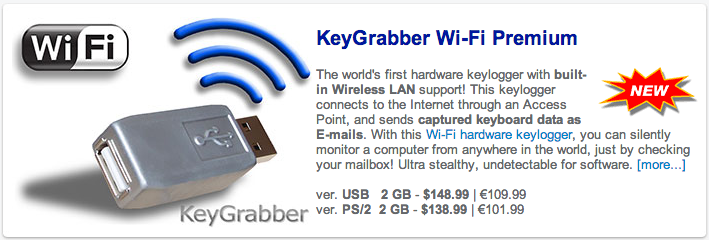
27
How can you protect the data?
28
- Layering - multiple layers to get to info
- Limiting - permissions, tech (AV, firewall)
- Diversity - different layers, app/db on different hosts
- Obscurity - hiding the information (eg apache banner)
- Simplicity - KISS
Intro to security
By artjom
Intro to security
- 1,297