Introducción al Hacking: Introducción, e historias sobre los Juegos CTF.

Pregunta #1
"hack the _________"
DGROMOV --- ST4R-L0RD







Av3ng3rs 1n1t14t1v3

https://ctftime.org/stats/2017/CO
eL ULTIMO JUEGO EN CIENCIAS COMPUTACIONALES
¿Como preparase para defender?
¿Existe una sola clase que cubra todo?
Creando hackers
¿Que es un hacker?

¿Como educar/entrenar hackers?
COMPETENCIAS EN DESAROLLO
- Criptografía
- Esteganografía
- Forense
- Ingeniería inversa
- Explotación
Enter defcon
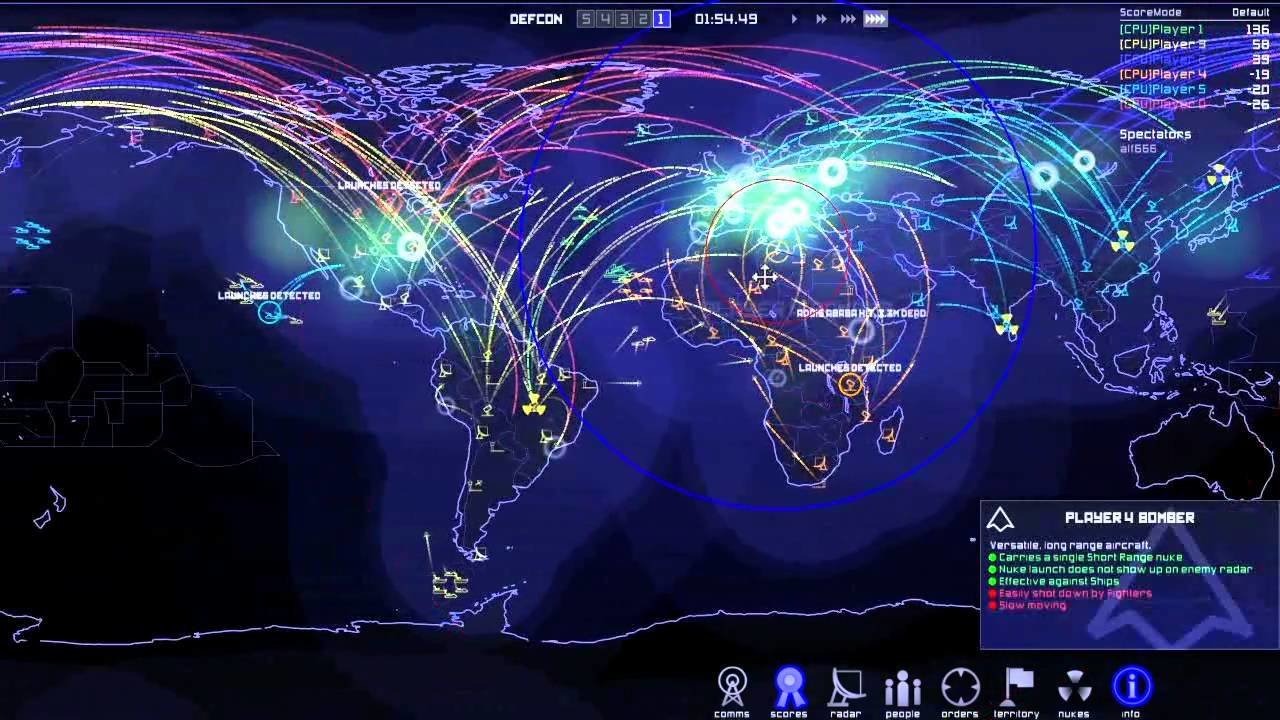
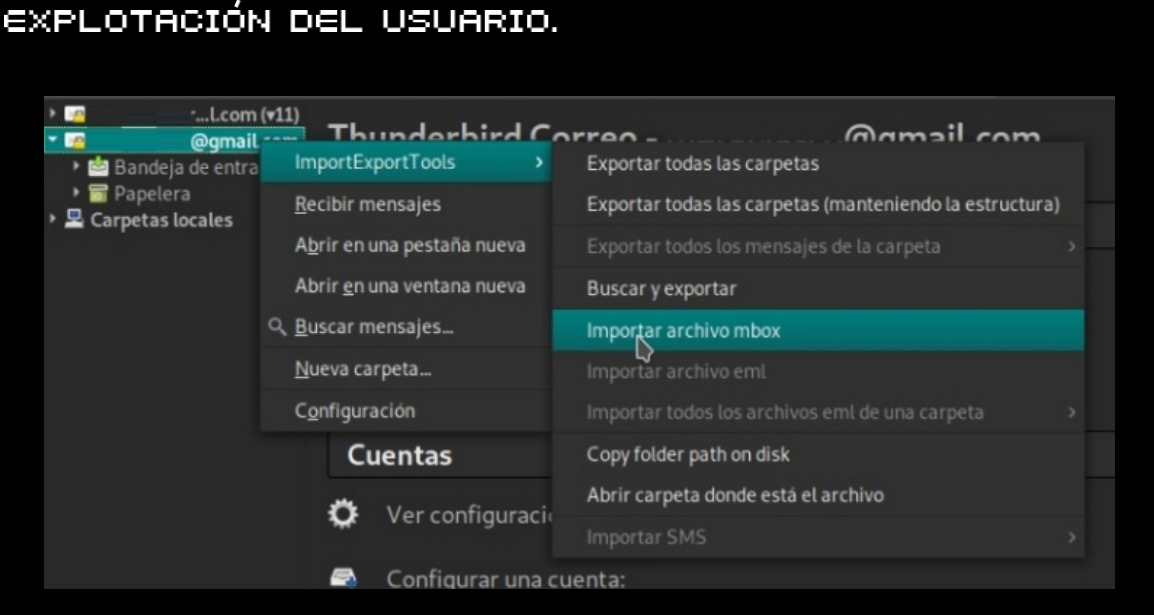
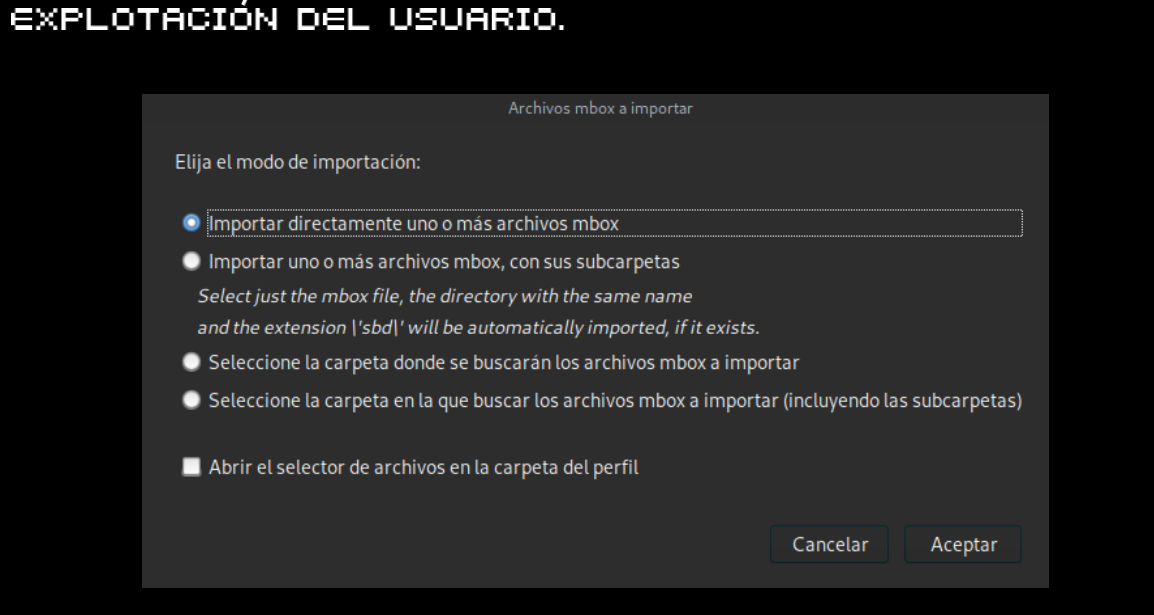
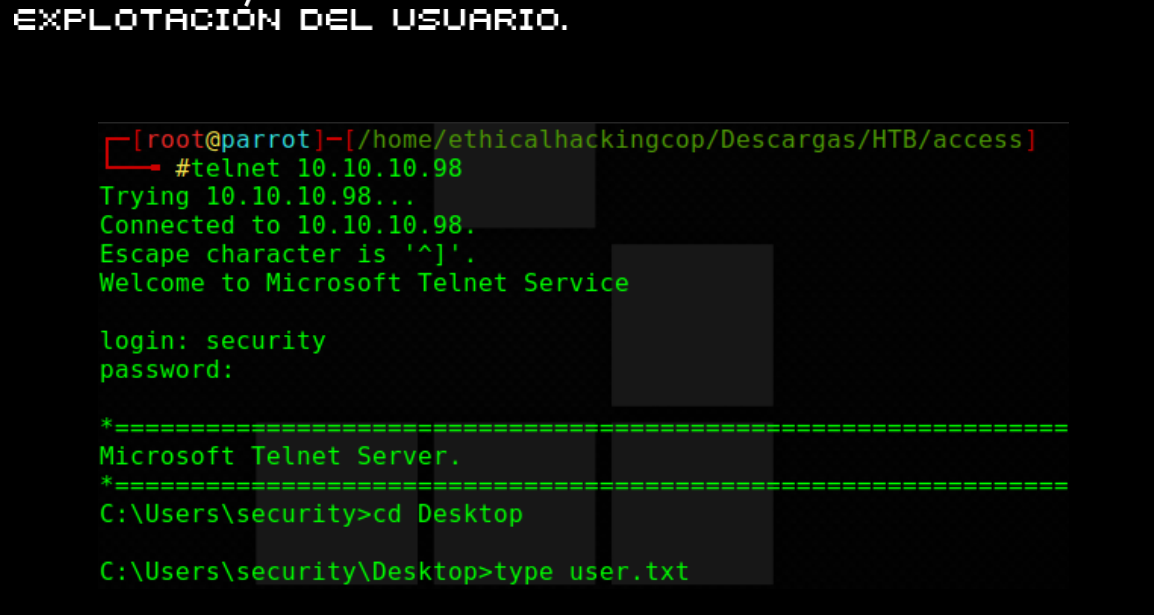
HACK THE BOX

pHILOSOPHER
Cripto


Tradución
Carta 1 = 365C997610306888C3CB07B26C7ED39325E4AD1BDC87255B8F5E54B66E253759B306A9BAA01B7D4A
Carta 2 = 5A04DC351E3D7B9CC3CE1DFF5142B08B3AFCA60B9484336B961F54A67319304E8845ABA9B60C734A
Rompiendo one time pad

Rompiendo one time pad


Rompiendo one time pad




Totalmente seguro
Rompiendo one time pad


¿Totalmente seguro?
Rompiendo one time pad


¿Totalmente seguro?
ONE TIME PAD BREAKING
./xorstrings.py 365C997610306888C3CB07B26C7ED39325E4AD1BDC87255B8F5E54B66E253759B306A9BAA01B7D4A 5A04DC351E3D7B9CC3CE1DFF5142B08B3AFCA60B9484336B961F54A67319304E8845ABA9B60C734A
=> 6c5845430e0d131400051a4d3d3c63181f180b1048031630194100101d3c07173b43021316170e00./cribdrag.py 6c5845430e0d131400051a4d3d3c63181f180b1048031630194100101d3c07173b43021316170e00
Your message is currently:
0 ________________________________________
Your key is currently:
0 ________________________________________
Please enter your crib: punched cards
0: "�-+ fhw4cdh)N"
1: "(0-mevp f{?YO"
2: "56`n{qd%y,OX�"
3: "3{cp|ea:.\Nk"
...
26: "pes_or_cards}"
27: "`hRd�^'"pwejs"
Enter the correct position, 'none' for no match, or 'end' to quit: 26
Is this crib part of the message or key? Please enter 'message' or 'key': message
Your message is currently:
0 __________________________punched cards_
Your key is currently:
0 __________________________pes_or_cards}_ONE TIME PAD BREAKING
thcon{punched_tapes_or_cards}
BROKENhash
El reto nos dirige hacia una página web. Esta nos dirige a subir dos archivos
touch t.txt
touch t2.txtif sha1[0] == sha1[1] and md5[0] != md5[1]: get flag # ;)El sitio web nos da una alerta
BROKENhash
Subimos los dos pdf con el mismo sha1 hechos por Google
El sitio web devuelve => Too Easy.BROKENhash
Utilizamos un sitio web para realizar dos archivos con el mismo sha
sha1sum a.pdf
9895a12be3429d4ca69835aad36527664ed952e5 a.pdf
sha1sum b.pdf
9895a12be3429d4ca69835aad36527664ed952e5 b.pdfBROKENhash
Utilizamos un sitio web para realizar dos archivos con el mismo sha
THCon{ST0P_US1nG_Th0S3_l4m3_H4SH_FuNCTIONz}AlexCTF 2017 – SC1: Math bot
It is well known that computers can do tedious math faster than human.
nc 195.154.53.62 1337
Creacion de script -- python to the rescue
!/usr/bin/env python
import socket, sys
server ="195.154.53.62"
port = 1337
botMath = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
print "connecting to:"+server
botMath.connect((server, port))
text = botMath.recv(2040)
print text
while 1:
while(text =='\n'):
text = botMath.recv(2040)
print(text)
texte = text.split('\n')
for te in texte:
if("=" in te):
nbre1= te.split(" ")[0]
opera= te.split(" ")[1]
nbre2= te.split(" ")[2]
if(opera == "+"):
reponse = int(nbre1) + int(nbre2)
elif(opera == "-"):
reponse = int(nbre1) - int(nbre2)
elif(opera == "/"):
reponse = int(nbre1) / int(nbre2)
elif(opera =="%"):
reponse = int(nbre1) % int(nbre2)
else:
reponse = int(nbre1) * int(nbre2)
botMath.send(str(reponse)+"\n")
print(reponse)
text='\n'Fore3: USB probing (150)
One of our agents managed to sniff important piece of data transferred transmitted via USB, he told us that this pcap file contains all what we need to recover the data can you find it ? fore2.pcap
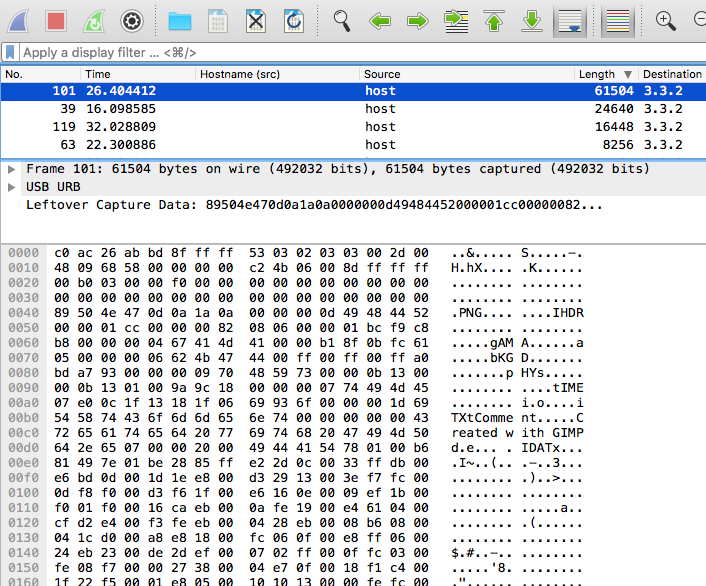
"Leftover Capture Data" > "Copy" > "...as Hex Dump"
Lanzamos esto a vim y borrando la primera columna,
despues %s/ //g; %s/\n//g tenemos un string hexcat ./raw | xargs python -c 'import sys; print sys.argv[1].decode("hex")' > out1.png$ file out1.png
out1.png: PNG image data, 460 x 130, 8-bit/color RGBA, interlaced
$ exiftool out1.png
ExifTool Version Number : 10.08
File Name : out1.png
Directory : .
File Size : 60 kB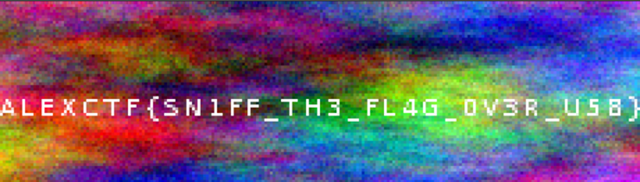
Pregunta #2 Trivia
It lead to memory leakage between servers and clients rending large number of private keys accessible. (one word)
Heartbleed
"The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. This weakness allows stealing the information protected, under normal conditions, by the SSL/TLS encryption used to secure the Internet."
ingeniería inversa
file gifted
$file gifted
gifted; ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked
(uses shared libs), for GNU/Linux 2.6.32, strippedHora de IDA!!
.text:08048562 push dword ptr [ebp-0Ch]
.text:08048565 push offset aS ; "%s"
.text:0804856A call ___isoc99_scanf
.text:0804856F add esp, 10h
.text:08048572 sub esp, 8
.text:08048575 push dword ptr [ebp-0Ch]
.text:08048578 push offset aAlexctfY0u_h4v ;
.text:0804857D call _strcmp
.text:08048582 add esp, 10h
.text:08048585 test eax, eax
.text:08048587 jnz short loc_80485A3
.text:08048589 sub esp, 0Ch
.text:0804858C push offset aYouGotItRightD
.text:08048591 call _putsGuarda flag en [ebp -0Ch] y la comparamos con aAlexctfY0u_h4v
aAlexctfY0u_h4v = AlexCTF{Y0u_h4v3_45t0n15h1ng_futur3_1n_r3v3r5ing}Mucho mas simple
$ strings gifted
/lib/ld-linux.so.2
libc.so.6
_IO_stdin_used
exit
...
[^_]
AlexCTF{Y0u_h4v3_45t0n15h1ng_futur3_1n_r3v3r5ing}
Enter the flag:
You got it right dude!
Try harder!
;*2$"
...
The flag is quickly found as a plaintext string in the binary.
For further investigation, I disassembled the binary in radare2.
The flag is being pushed as a string onto the stack just before
the call to strcmp.unvm me
If I tell you what version of python I used .. where is the fun in that?
unvm_me.pyc
Buscamos un decompilador de python- https://github.com/gstarnberger/uncompyle
mkdir unvm
$ virtualenv unvm
$ source ./unvm/bin/activate
$ pip install uncompyle2
$ ./unvm/bin/uncompyle6 ./unvm_me.pyc > unvms.py$ cat unvms.py
import md5
md5s = [174282896860968005525213562254350376167L, 137092044126081477479435678296496849608L,
126300127609096051658061491018211963916L, 314989972419727999226545215739316729360L, 256525866025901597224592941642385934114L, 115141138810151571209618282728408211053L,
8705973470942652577929336993839061582L, 256697681645515528548061291580728800189L,
39818552652170274340851144295913091599L, 65313561977812018046200997898904313350L,
230909080238053318105407334248228870753L, 196125799557195268866757688147870815374L,
74874145132345503095307276614727915885L]
print 'Can you turn me back to python ? ...'
flag = raw_input('well as you wish.. what is the flag: ')
if len(flag) > 69:
print 'nice try'
exit()
if len(flag) % 5 != 0:
print 'nice try'
exit()
for i in range(0, len(flag), 5):
s = flag[i:i + 5]
if int('0x' + md5.new(s).hexdigest(), 16) != md5s[i / 5]:
print 'nice try'
exit()
print 'Congratz now you have the flag'vamos a romper md5
Añadimos para obtener los md5
for x in md5s: print '{0:032x}'.format(x)831daa3c843ba8b087c895f0ed305ce7
6722f7a07246c6af20662b855846c2c8
5f04850fec81a27ab5fc98befa4eb40c
ecf8dcac7503e63a6a3667c5fb94f610
c0fd15ae2c3931bc1e140523ae934722
569f606fd6da5d612f10cfb95c0bde6d
068cb5a1cf54c078bf0e7e89584c1a4e
c11e2cd82d1f9fbd7e4d6ee9581ff3bd
1df4c637d625313720f45706a48ff20f
3122ef3a001aaecdb8dd9d843c029e06
adb778a0f729293e7e0b19b96a4c5a61
938c747c6a051b3e163eb802a325148e
38543c5e820dd9403b57beff6020596djohn the ripper to the rescue
$ john --incremental=LowerNum hashes --format=raw-md5831daa3c843ba8b087c895f0ed305ce7: ALEXC
6722f7a07246c6af20662b855846c2c8: TF{dv
5f04850fec81a27ab5fc98befa4eb40c: 5d4s2
ecf8dcac7503e63a6a3667c5fb94f610: vj8nk
c0fd15ae2c3931bc1e140523ae934722: 43s8d
569f606fd6da5d612f10cfb95c0bde6d: 8l6m1
068cb5a1cf54c078bf0e7e89584c1a4e: n5l67
c11e2cd82d1f9fbd7e4d6ee9581ff3bd: ds9v4
1df4c637d625313720f45706a48ff20f: 1n52n
3122ef3a001aaecdb8dd9d843c029e06: v37j4
adb778a0f729293e7e0b19b96a4c5a61: 81h3d
938c747c6a051b3e163eb802a325148e: 28n4b
38543c5e820dd9403b57beff6020596d: 6v3k}$ cat solution | sed 's/.*://g' | tr -d '\n '; echo
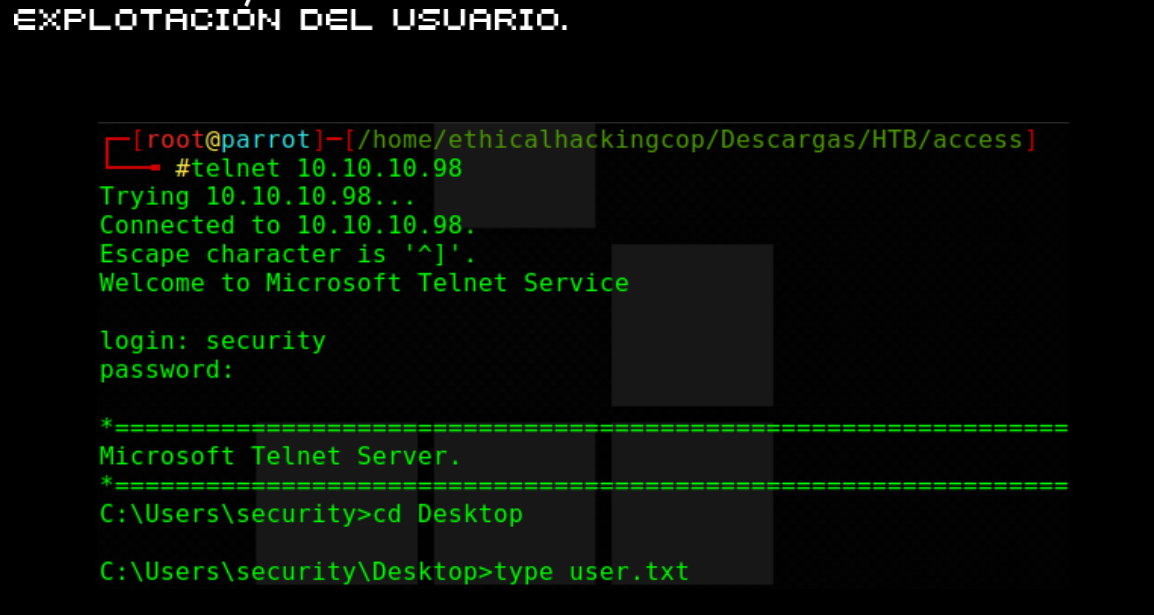
ALEXCTF{dv5d4s2vj8nk43s8d8l6m1ds9v41n52nv37j481h3d28n4b6v3k}eNTER THE HACKBOX
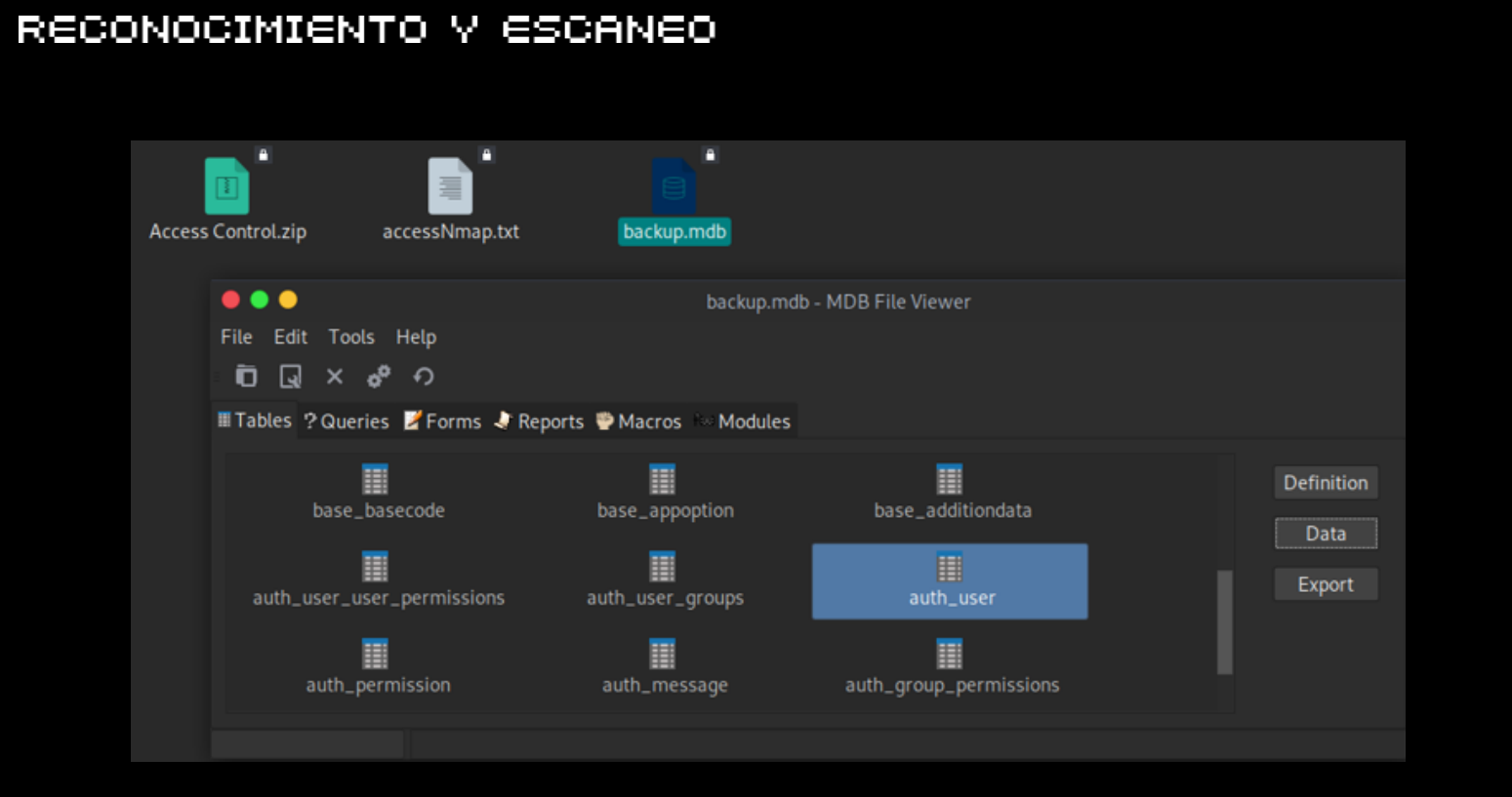
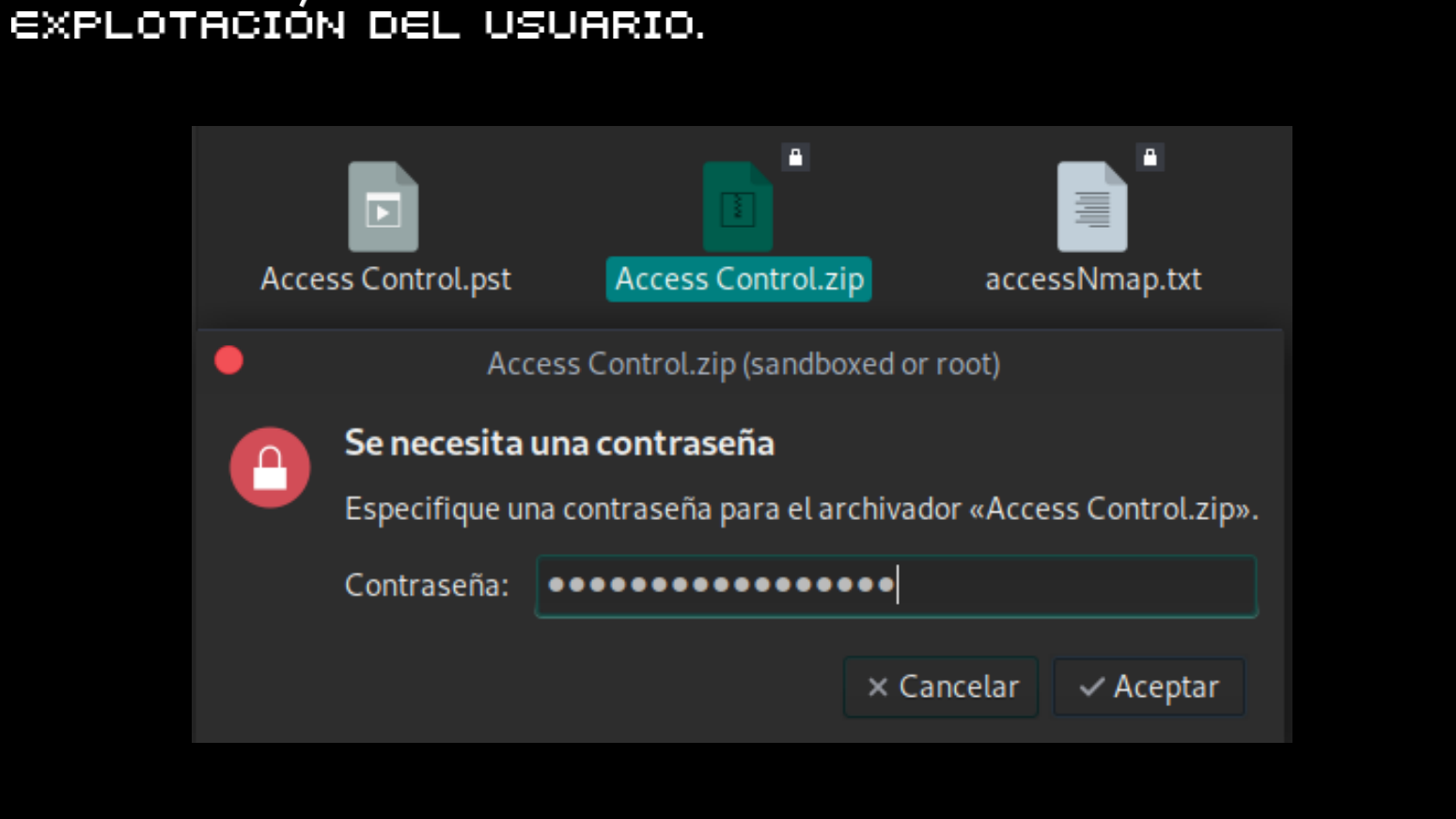
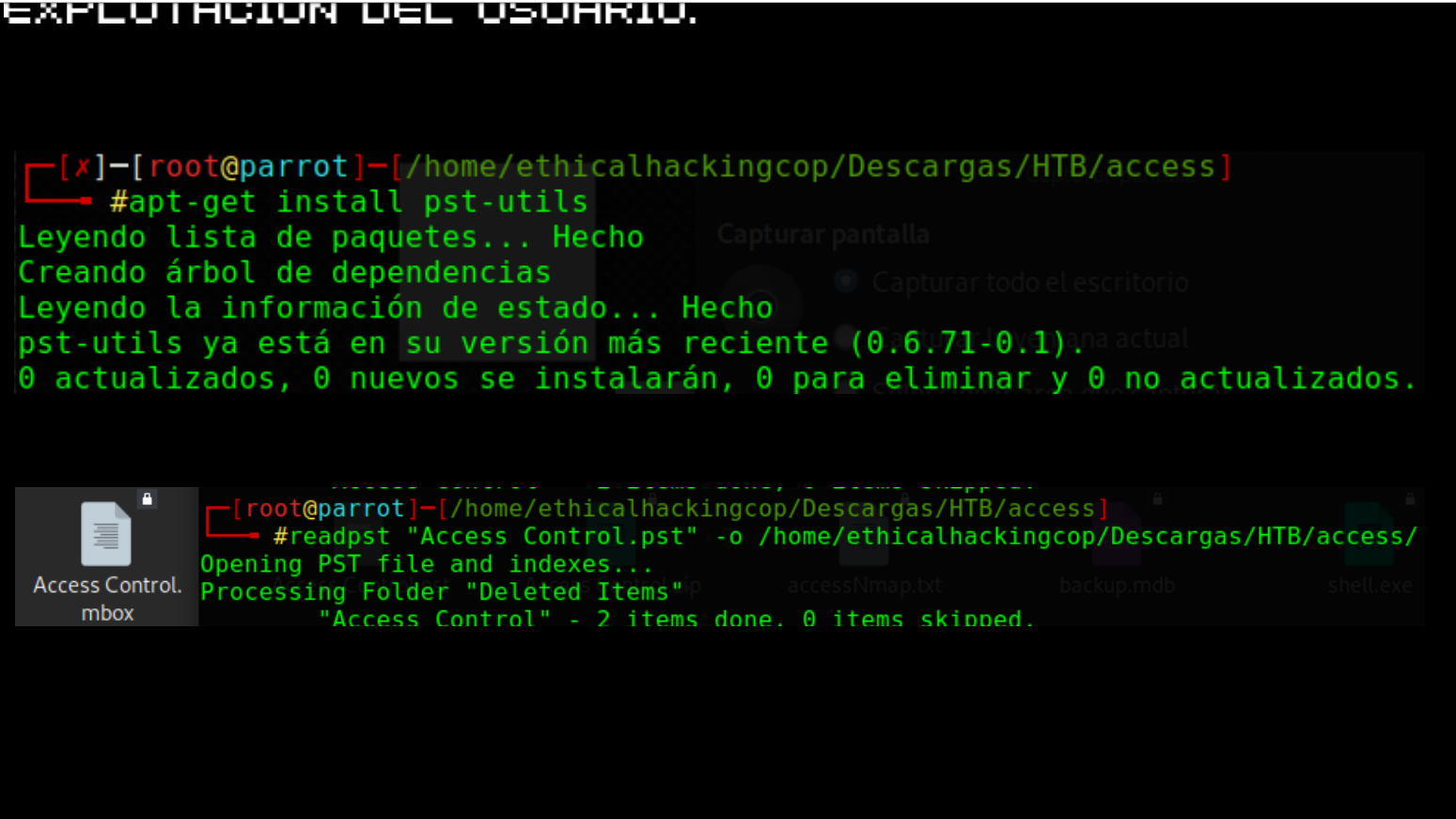
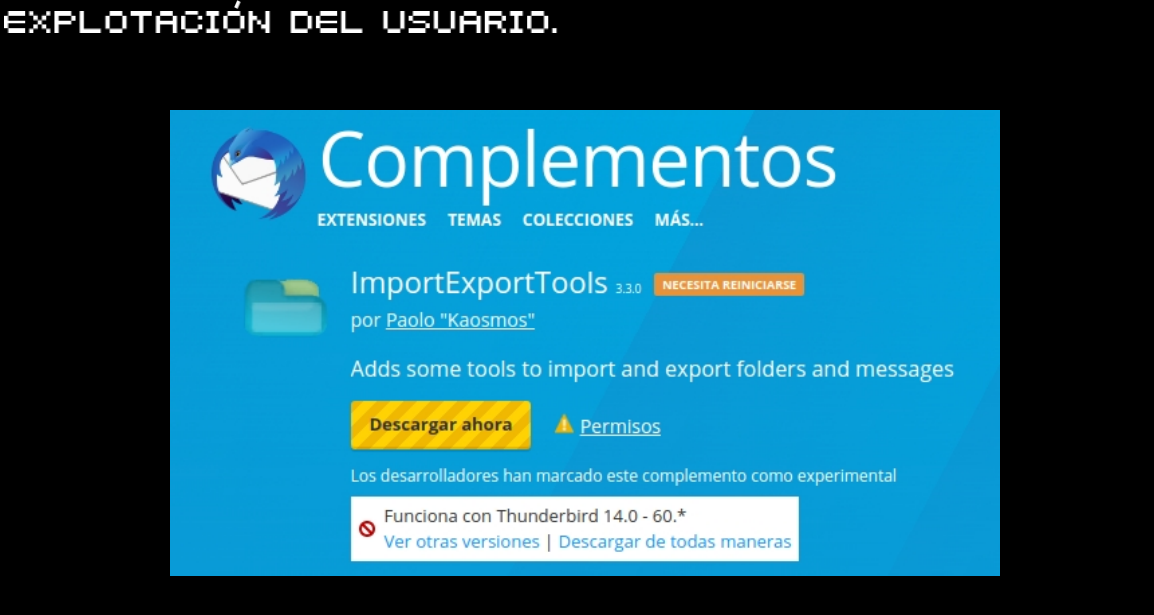
RECONOCIMIENTO Y ESCANEO
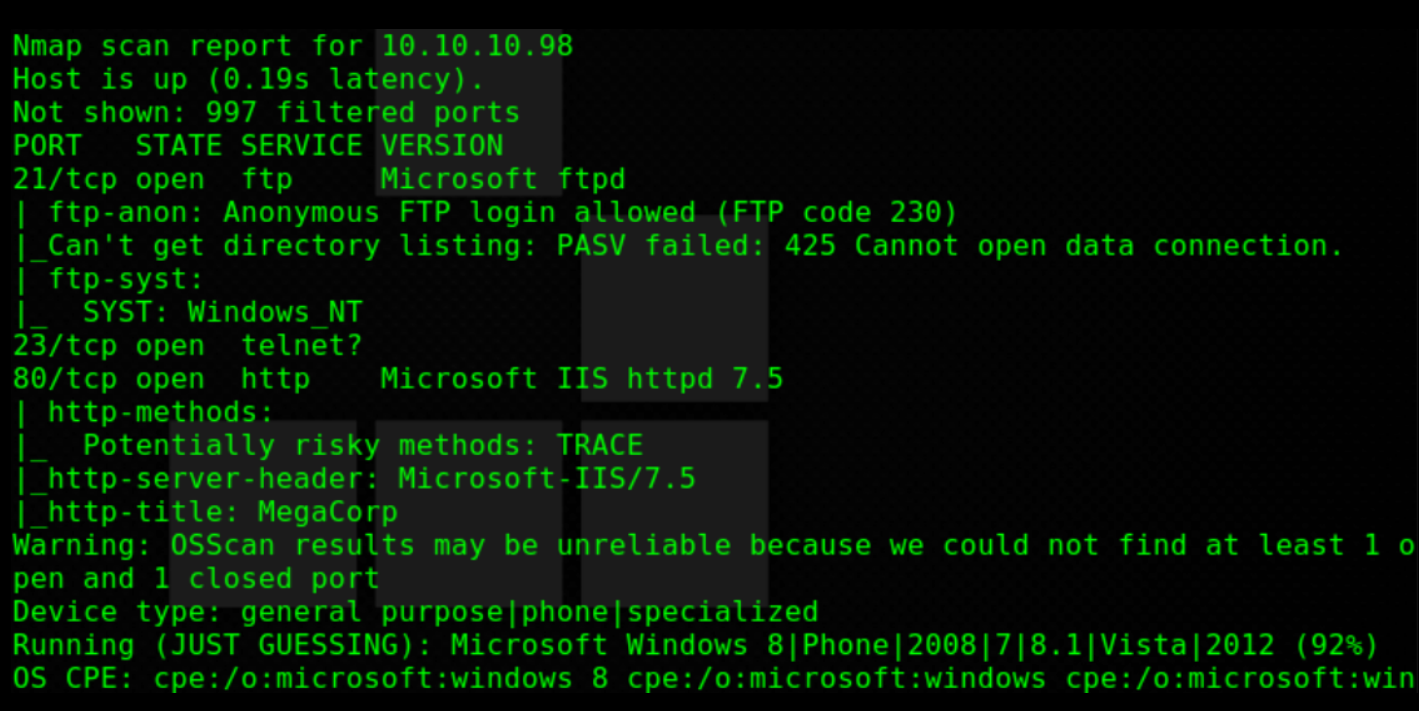
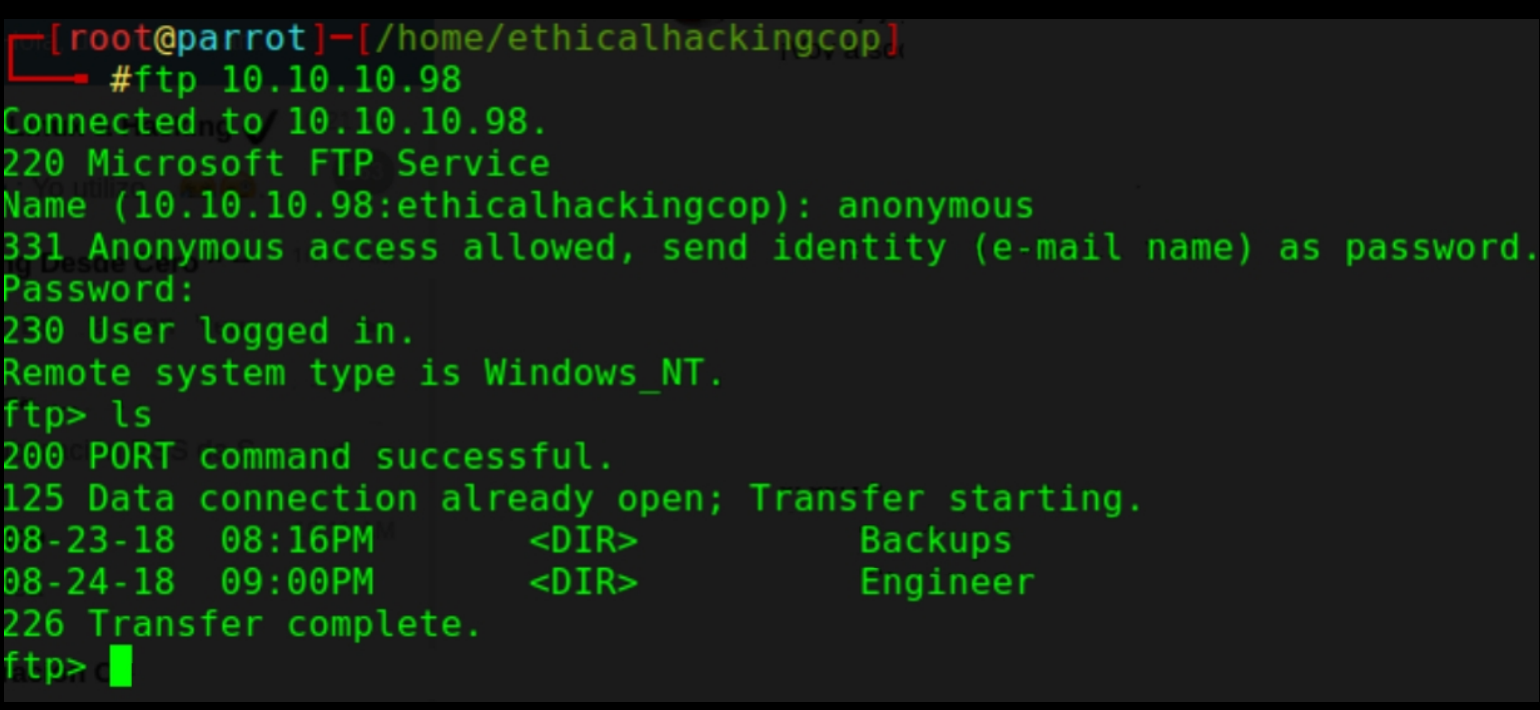
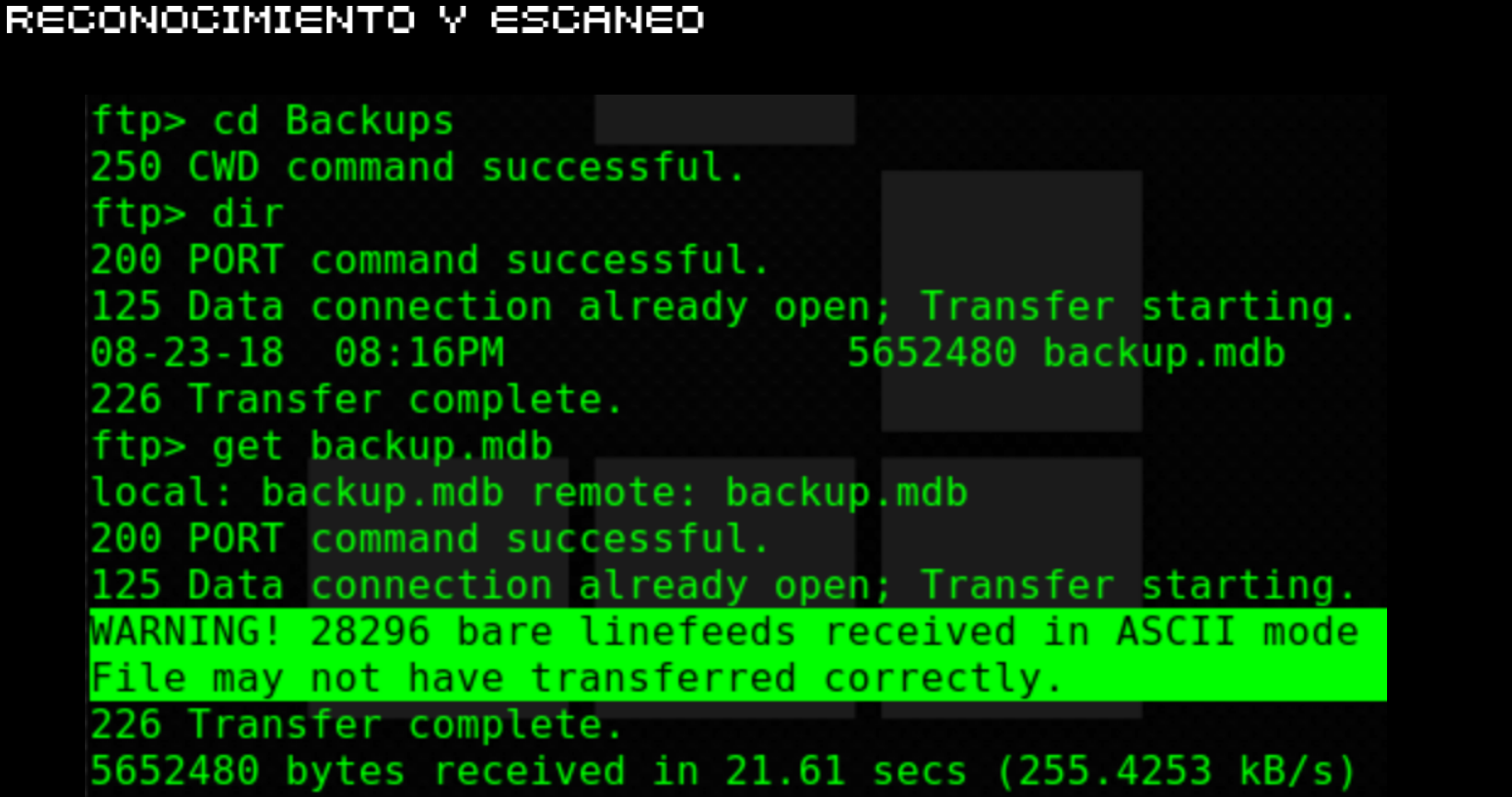
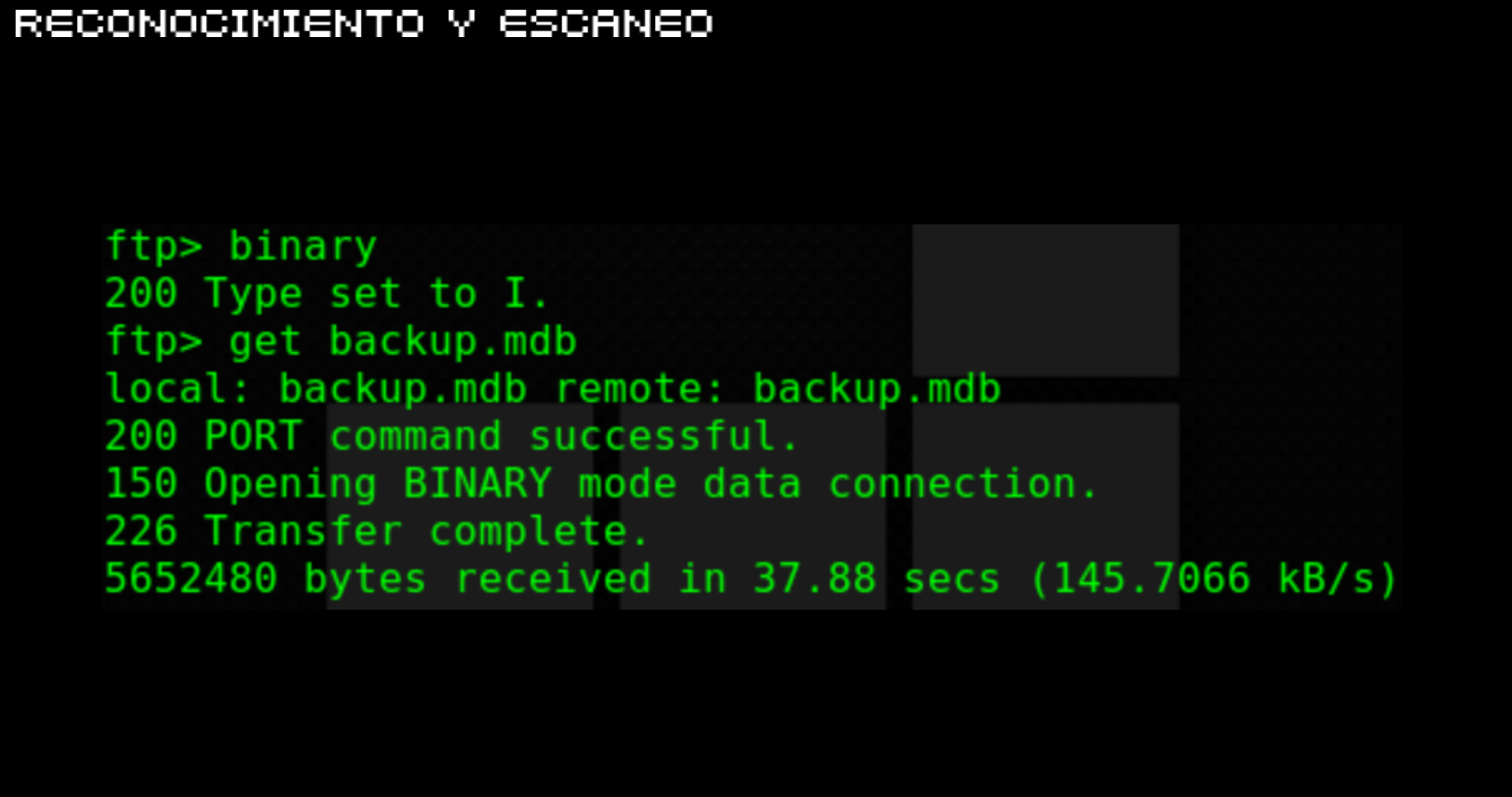
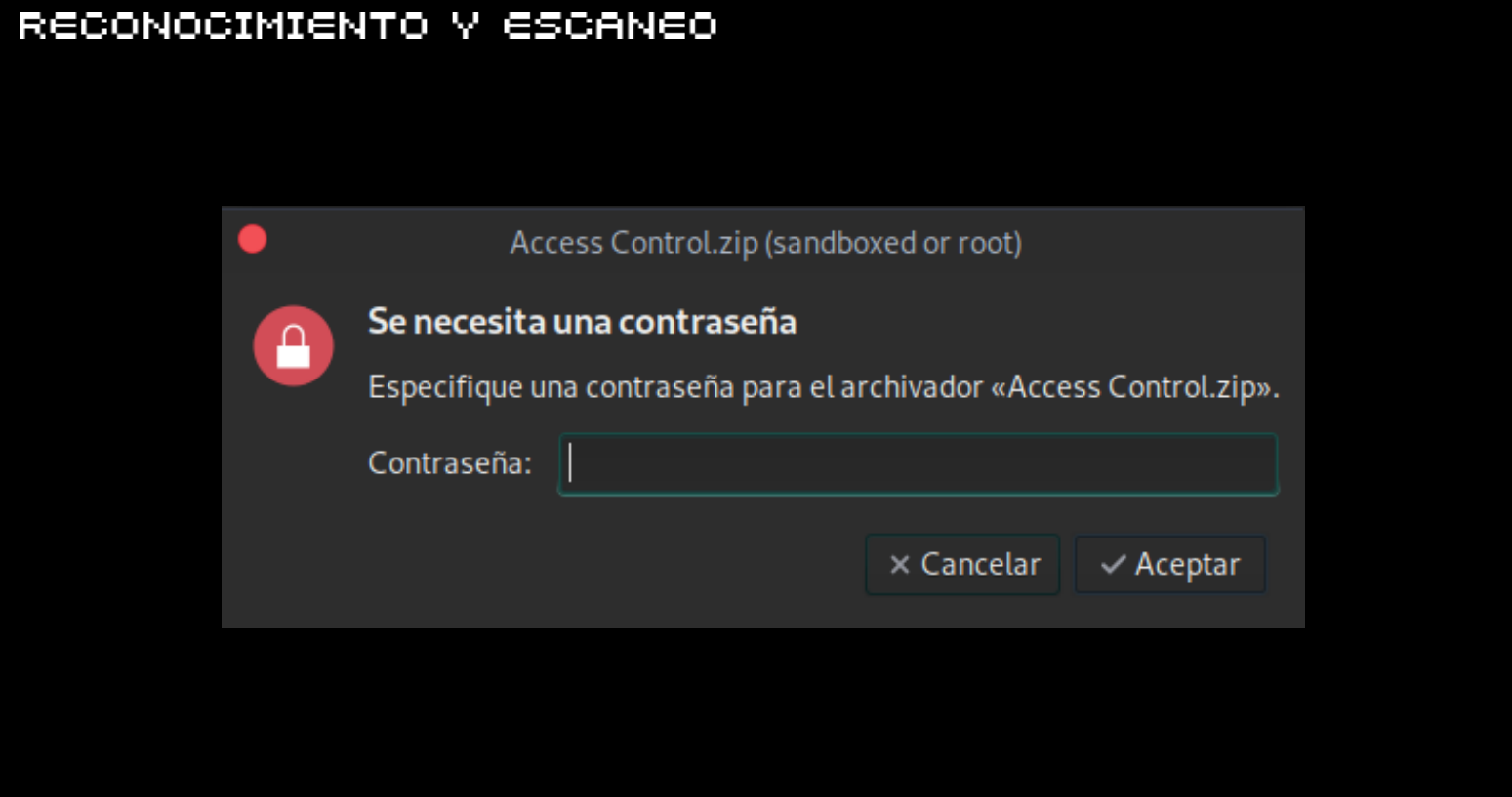
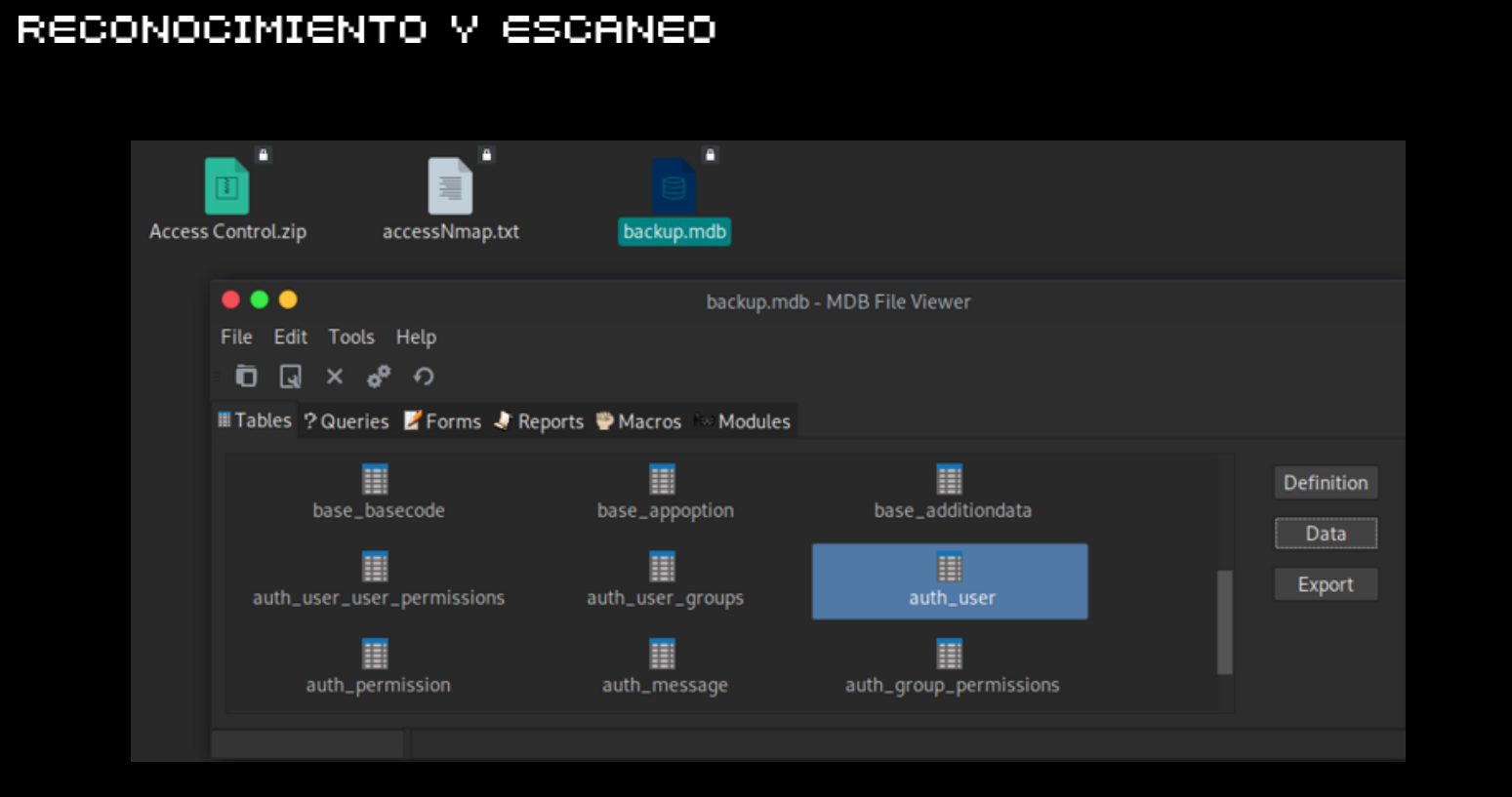
CTF-Historias
By David Cardozo
CTF-Historias
- 993



