Introduction
to InfoSec
Because all it takes is green text on a black background
What is InfoSec?

What InfoSec is NOT
InfoSec as a Career
$$$
Bug Bounties


Security Research


Why do security vulnerabilities exist?

But how do hackers work?

So what does InfoSecIITR do?
CTFs!

Organizing CTFs on Backdoor along with SDSLabs

Meetup every week to solve challenges together, and have discussions on everything related to security
We love Slack <3
Show up regularly for meetings, and you'll be added in :)
Win Contests!
Deloitte CCTC


Microsoft BTS Quals
Rank 1, 5, 8 in India

Microsoft BTS
(Finals)
Winners and First Runners Up


2nd, 13th, 14th rank in India (qualified for the finals to be held in November)

And many others....
CTF! WTF?
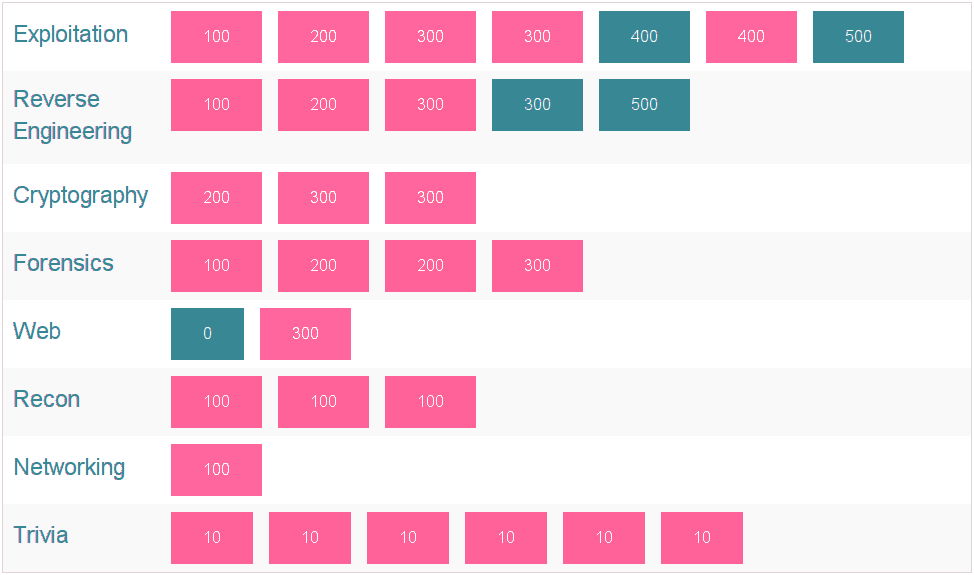
Categories
Crypto
- Ancient Crypto: ROT13, Cesar Cipher, Vignere Cipher etc.
- Modern Crypto: AES, DES, RSA etc.
Reverse Engineering
Web
- XSS
- SQLi
- Directory Traversal
- File include
- Code Injection
- ...
Forensics
- Analyzing Network Captures(Wireshark etc.)
- Steganography: concealing a file, message, image, or video within another file, message, image, or video.
- "Undeleting" files
- ...
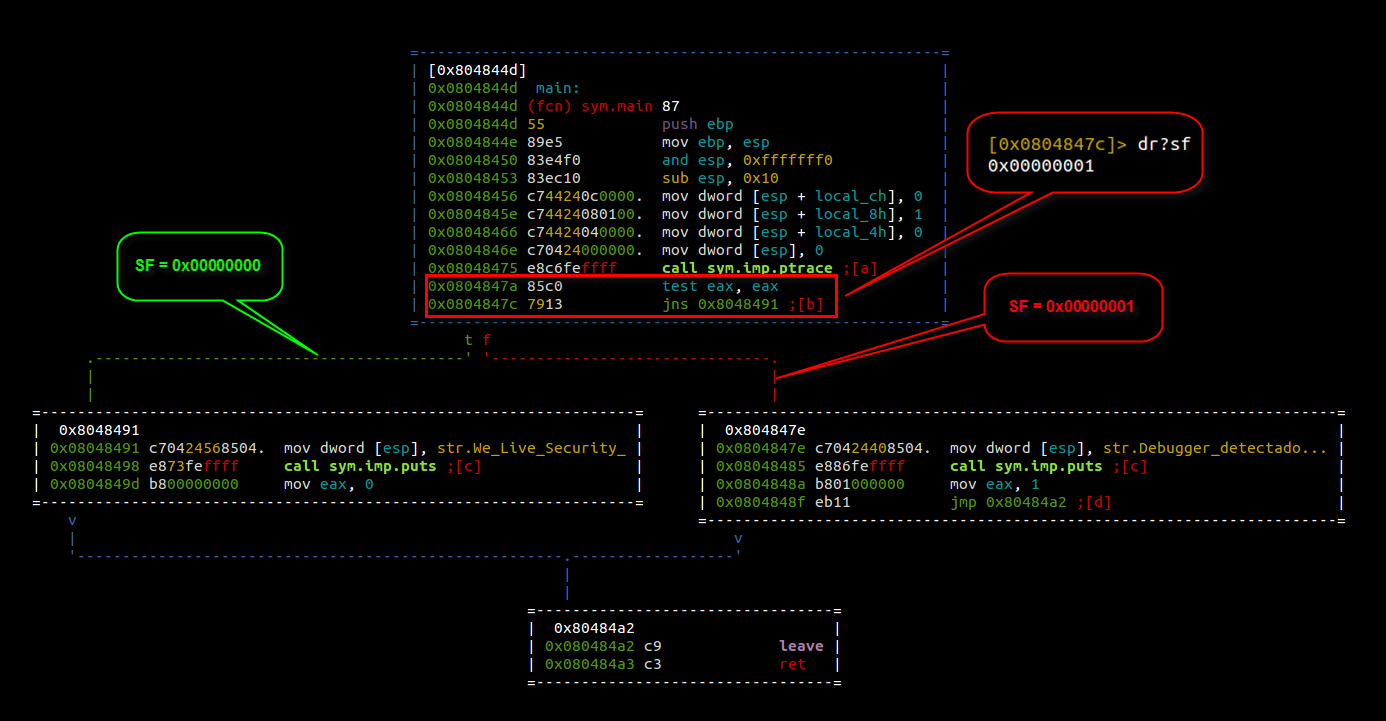
Binary Exploitation
Text
- Buffer overflows
- Return-oriented programming
- Format String vulnerability
- ...
Types
Jeopardy

Attack-Defence
Jeopardy
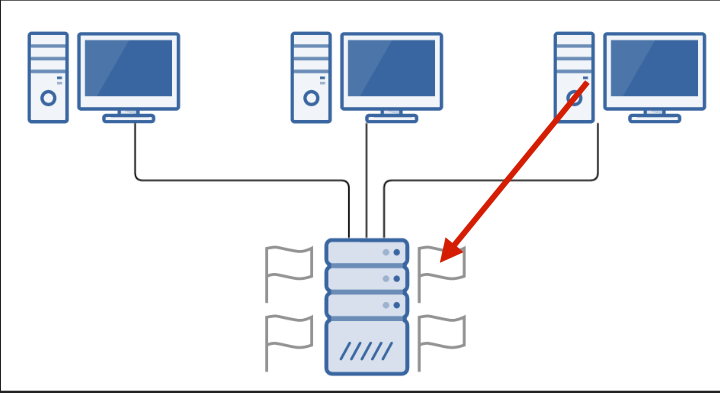
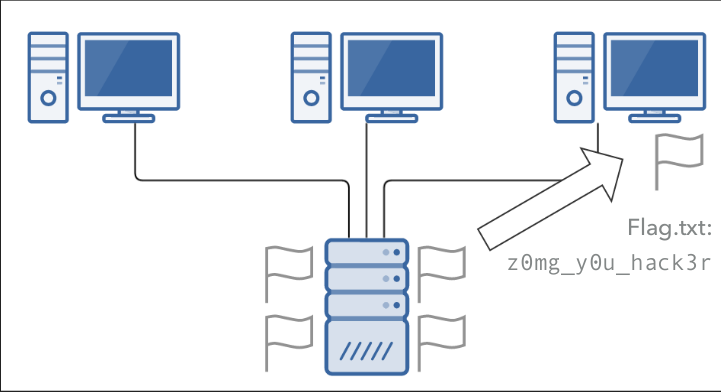
Attack Defence
Wargames
(Always online CTFs)
- backdoor.sdslabs.co
- picoctf.com
- pwnable.kr
- overthewire.org/wargames/
- io.netgarage
- gracker.org
- ...and many more
And
Now
This...
Demo time
Questions?
Meeting+Workshop at 8:30pm today
Bring your laptops along :)
deck
By jaybosamiya
deck
- 284
