SSL ≈ Plaintext
The End of Security Iconography
Zachary Lym & Jeremy Rand
Namecoin Research
Security Icons == Encryption
Research History
- Eye tracking: users looked at icon when present but ignored icon's absence (Whalen & Inkpen, 2005)
- Behavioral: users logged in with their own account information (Schechter, et al 2007)
- "Malicous" Tor exit node that removed SSL from connections.
- Users are above-average in technical skills and paranoia.
- 300 logins
- 117 email accounts.
- 16 credit card numbers.
-
7 paypal logins.
-
100% Success Rate.
Present Study: Focus on EV
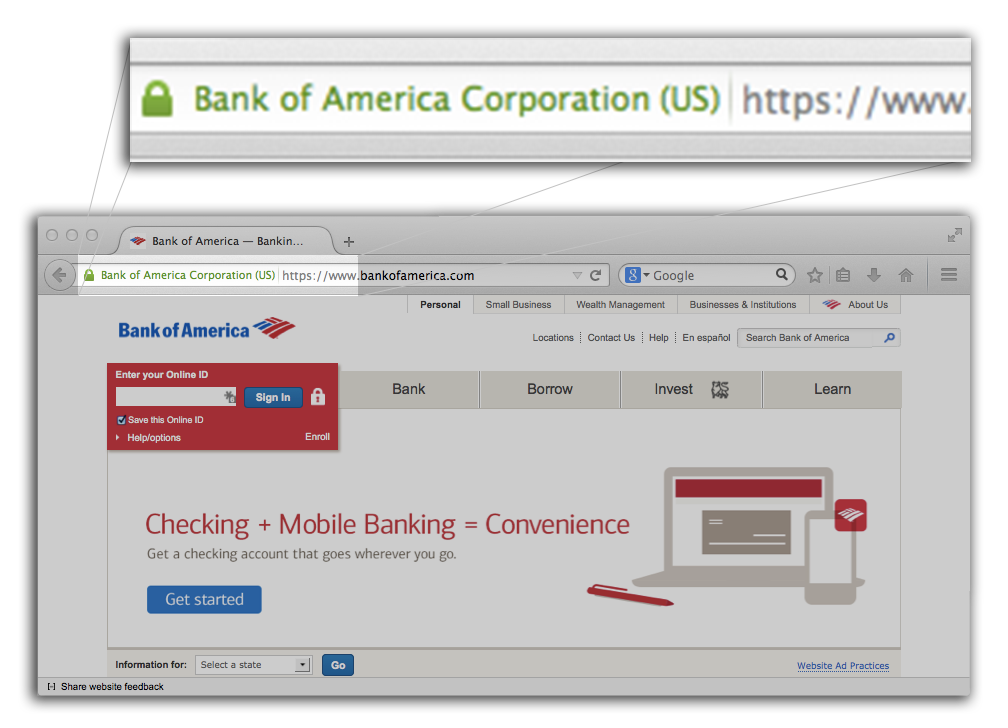
Details
- Between Subjects Design
- Participants asked to login to social media (Twitter), email (Outlook), and their bank account.
- Control: no changes.
- Manipulation: regular SSL, no EV indicators.
- Randomly approached 20 strangers and offered $5.
- Sketchy as hell: in university library, zero officialdom.
- Dependent Variables:
- Logins
- Questions about login process:
- Did you notice anything odd?
- Did you notice lack of EV cert?
- Did you avoid logging into an account?
Findings
- No statistical differences between groups.
- 2 out of 3 participants who claimed to notice a lack of EV iconography logged into their account anyway.
- CS major was the only participant who refused to login.
- Replicated existing studies with larger user counts.
∴ Not secure!
Difference
Couple results with theory to:
- prove that the security model itself is unfixable;
- redefine into two problems: fraud detection + encryption;
- push for incremental improvements;
- jump start research to solve new problems.
It Can't Be Fixed
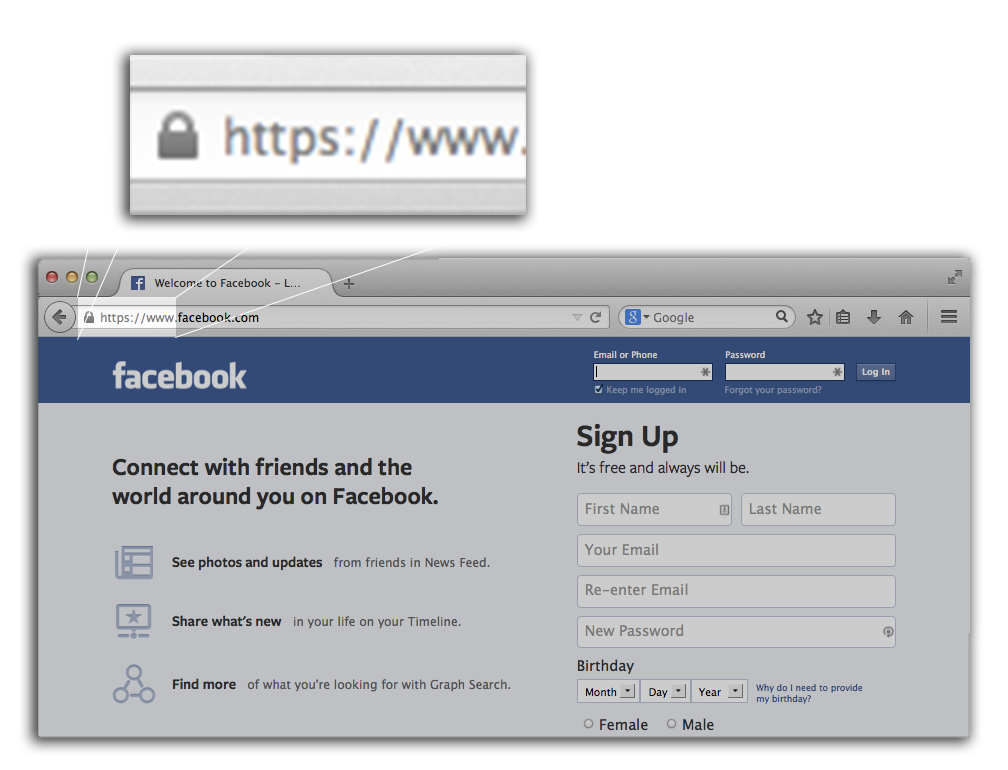
- HTTPS (lock icon bottom of page)
- Lock + HTTPS ~2004
- Extended Validation ~2008

Research
"[We] found no evidence that security was checked at all ... we were unsuccessful in reproducing normal browsing behavior during our study. ...Despite being asked to treat the [dummy] data as if it was their own, most participants were completely unmotivated to take any precautions." (Whalen & Inkpen, 2005)
WRONG:
- Present study
- Marlinspike 2009
- Schechter, et al 2007
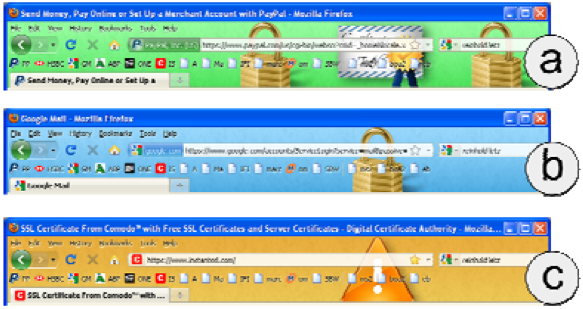
Limits of Security Iconography
Limits of Security Iconography
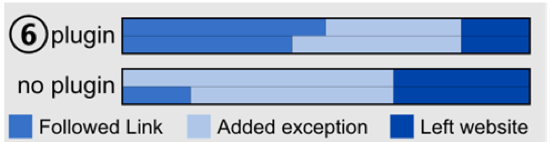
H3: The absence of the (trusted) Persona on non-encrypted websites will reduce their trustworthiness.
"... we expected ... the plugin group (trust ratings) to drop due to a missing positive feedback. This did not happen. The study duration was much too short for people to get used to the plugin and expecting the green Persona to show up." (Maurer, et al 2011)
Industry
- Response to research from friend, security researcher, & smartest person in the room, "Use 3 certificate authorities...."
- Everyone is trying to solve the wrong problem.
- Chrome dev discussing drawbacks of DANE (Adam Langley, 2011)
-
In theory, it should be hard to get a CA certificate for, say, paypa1.com....
-
... if you want a certificate that identifies a legal entity, rather than a domain name, then you want EV certs.
-
... if DNSSEC stapled certificates end up being predominantly used for abuse then I'll probably kill them.
-
DANE support was pulled a year later due to lack of use.
-
∴ Belief in broken model is blocking progress.
Logical Fallacies
- Users check or even understand URLs.
- bankofamerica.securelogin.com
- Users understand encryption certificates.
- Attackers will use SSL.
- Users become more alert over time.
- Statistically significant improvement!!!! (see below)
Lesson 1
SECURITY ICONOGRAPHY MODEL CANNOT BE FIXED!
Cognitive Spotlight
Psych 101
- Limited processing power. (Simons & Chabris, 1999)
- Tasks that are repetitive become habituated, leave the cognitive spotlight. (Raskin, 2000)
- Human factors researchers: moderate improvement with novel icons are due to novelty! Stimulus/response ... extinction. (Sokolov, 1960)
Lesson 1.5
Usability Bugs are as Severe
as Programming Bugs
... and this security bug is deterministic!
When the algorithms are broken: MASS PANIC!
- Four-day lag between disclosure and fix of GOTO Fail.
- Research showing security icons are broken: 1 decade.
Usability vs Security- Usability == Security
Fraud Detection & Encryption
Related Yet Distinct Problems
- Current web security model inappropriately ties these two issues together.
- Incremental improvements blocked because proposed solutions do not solve both problems.
- Proposed solutions that solve both problems fail because they were not incremental.
Ancient History
-
Web security model (certificate authorities) was one of a series of 4 AM decisions @ Netscape (Marlinspike, 2011).
-
Encryption overhead was non-trivial, especially on the server.
-
Early web was publisher centric, 2-way communications were reserved for mail, usenet, etc.
- Websites needing encryption might be in the dozens.
- Certificate authority would vet identity of website.
- Users would check on the sites that they visited.
- Certs cost $$$!
- 650 "trusted" organizations.
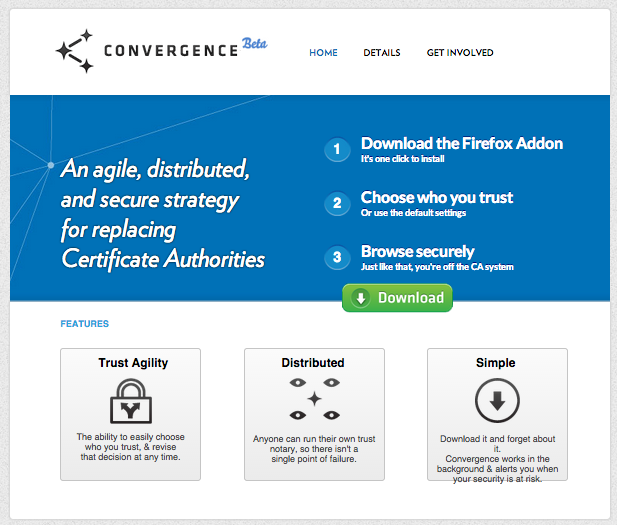
Convergence
- Marlinspike's attempt at replacing cert auths.
- Client choose notaries who track TLS info.
- n-of-m agreement on correct TLS cert.
- Triangulation is similar to Perspectives and MonkeySphere.
- Marlinspike abandoned the project after one year.
Information Theory
{sender, receiver, information} == Web == Email == SSH
Fraud detection
- Web sucks at this.
- SSH is okay.
- Email is pretty good.
- Spear Phishing : (
Encryption
- Web sucks at this.
- SSH is good.
- Email is okay, getting better.
- Needs transport and E2E encryption.
Lesson 2
Change is Always Incremental
Fraud Detection & Authenticity
AKA: Needs More Research
Email Fraud Detection
- Primarily statistical analysis
- Sender/Receiver
- Content
- Catches vast majority of non-targeted attacks.
- Some people will always fall for a sc.
- Spear Phishing sucks!
- Real authenticity checking would help.
-
High-level targets and locked down systems (iOS, Android) require 0-days.
- Browser and OS deserve some blame here.
Web Fraud Detection
... What Fraud Detection?
- Less fraud than email due to one-way nature of web.
- Abdicate responsibility to Certificate Authorities.
- We can do better than the PhishTank!
Web Fraud Detection
Correlate user input types and sites!
- We already track usernames, passwords, addresses.
- We can detect credit card numbers, SSN, etc.
- Users log into ~25 sites & appear to use different passwords for financial sites (Florêncio & Herley 2007).
- ML visual matching (Afroz & Greenstadt, 2011).
- Detect visually similar sites, prevent sending bank account credentials?
- Enable more advanced users (Snowden) to turn on warnings for visually similar sites?
Web Fraud Detection
Other cool stuff
- HSTS prevents downgrade attacks after first visit.
- Can be hard coded into browser.
- Supported by 2/3 major browsers, coming to IE 12.
- Nine of top 10 banks don't have it enabled.
- Should be done in DNS, wouldn't require initial visit.
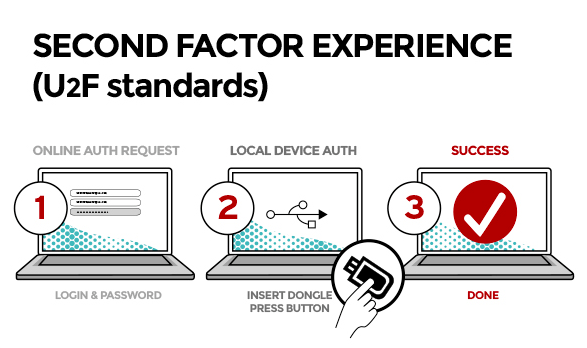
- FIDO/U2F is great.
- Public key crypto, not just passwords.
- Hardware based.
Web Authenticity
Triangulation of TLS information.
- Do we really need 3 operators tracking TLS information?
- Qualys was the only serious Convergence notary.
- This is what "Let's Encrypt" should have been.
- Could have 3 entities signing a single feed....
- Could count DNS information (via DANE) as an information source.
- Browser could (optionally) cache parent private key as an independent source of information (akin to SSH).
- Attacker would have to trick client on first connect.
- Only for places like Google, Apple, etc.
Kickstarting Progress
Competition and Money
- No one asked for Convergence, NIH syndrome.
- Competition made browsers much faster.
- We could create a feature list and collect real-world metrics.
- Opening for IE and Opera.
- Microsoft has the infrastructure and R&D.
- Opera could easily enable DANE (implementation exists for Chrome).
- Qualys is still publishing Convervence notary feed...
A Future for Certificate Auths
Certificate Authorities Have Power
- Printing money using encryption long before Bitcoin.
- Their people are in standards committees.
- ... but they want to provide real value!
Insurance Brokers
- Browsers track number of users and types of information, Cert Auths certify insurance.
- Cost (somewhat) scales with risk.
- Different rates for sites taking credit cards vs bank account information vs SSNs.
-
Riskier customers pay more.
- Not very granular, but better than nothing.
What This Gets Us
Fraud Detection & Authenticity
- Stop abdicating to cert auths, start using statistics.
- As good as email, which catches 99% of non-targeted attacks.
- It's possible to get better than email and catch targeted attacks.
- Convergence style notary + DANE + caching = 2.5 independent sources of information.
- Certificate Authorities certify fraud insurance.
- Offers real value.
- Cost (somewhat) scales with risk.
- Monetary incentives for better security.
Somewhat incremental, requires research.
Web Encryption
The fix is incremental!
- Embrace Self-Signed Certs
- Embrace DANE
- Reject Unencrypted
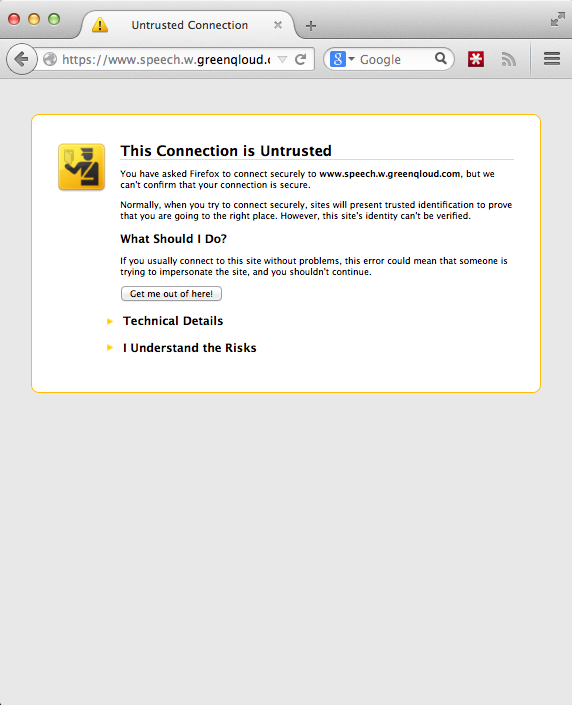
Self-Signed Certs Browser Vendors
- Just remove the warning.
- 0 reasons for this behavior.
- For the diehards: do not show lock icon.
- 4 vendors, 95% of market.
- Auto updates = rapid uptake.
- Would remove code from browsers.
Self-Signed Certs Server Vendors
- TLS by default.
- 3 vendors, 90% of the market (Netcraft).
- Minor tweak!



- DANE is not perfect, but it's better!
- Publicly auditable security process.
- Increases cost of attack.
- Cracking .com TLD vs 1 of 650 CAs....
-
Incremental improvement.
- Existing standard.
- Information channel available to all browsers.
- Does not require browser vendors to build more infrastructure.
- Progressive enhancements over self-signed.
- Require DANE for password input?
- Requires tracking passwords.
- Require DANE for password input?
- Opens door for innovation from .bit and .p2p.
DANE: TLS fingerprints in DNS
What This Gets Us
Encryption
- Backports universal encryption to HTTP 1.1!
- Shuts down large swaths of the NSA's opportunistic surveillance.
- Makes censorship (China's Great Firewall) less effective, more expensive.
- Opening for innovation from Namecoin and BitShares.
100% Incremental!!!
What's At Stake
The Open Web
Review
- Web crypto is broken and the attack is ~deterministic.
- Self Signed Certs + DANE = Universal SSL.
- Support research but don't block improvements.
Questions?
SSL ≈ Plaintext
By Zach Lym
SSL ≈ Plaintext
- 1,171



