Human Factors and the Web's Security Model
Zachary Lym
Web Encryption 1.0
- Browser trust notaries (aka Certificate Authorities).
- Notaries "verify" domain name owner.
- Web pages have their encryption signed by notary.
- Created when Yahoo!'s directory had 30 links.
A Long List of Fails
- Organized crime can purchase notary for $50K.
- Governments can infiltrate one of 650+ notaries.
- Lack of free encryption has enabled dragnet surveillance.
+ Prevents low level offenders
... right?
(Moxiespike, 2011)
Security Model
- A few dozen major websites would ever need encryption.
- One person would use encryption on two or three websites.
- User checks if encryption is enabled.
Previous Research
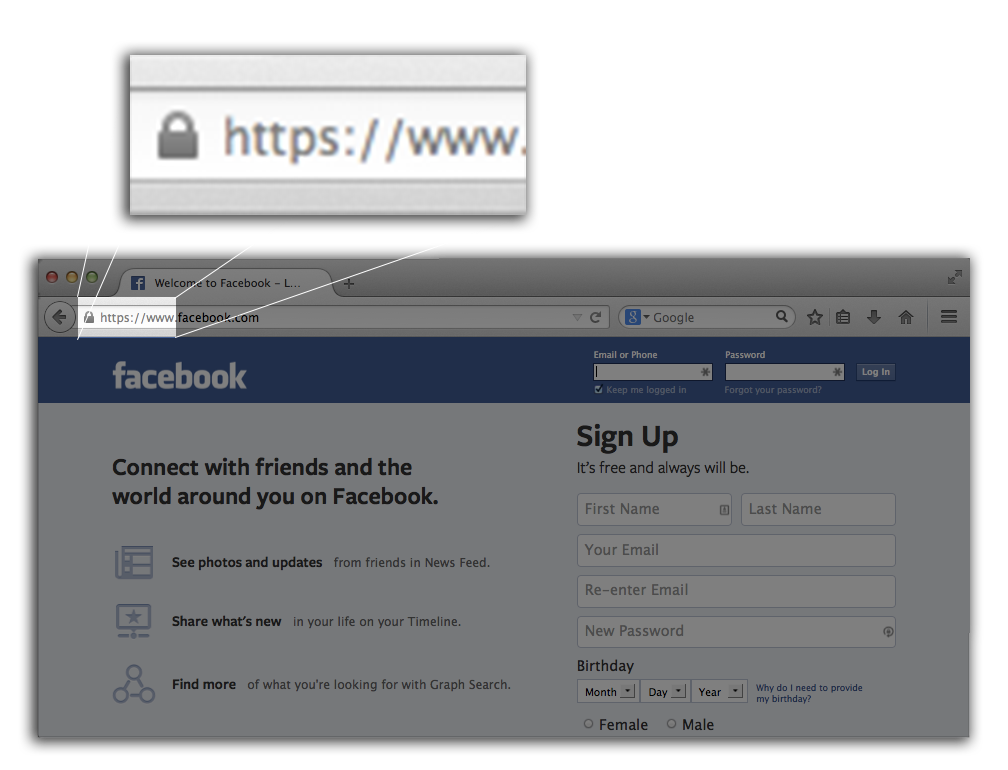
https vs http
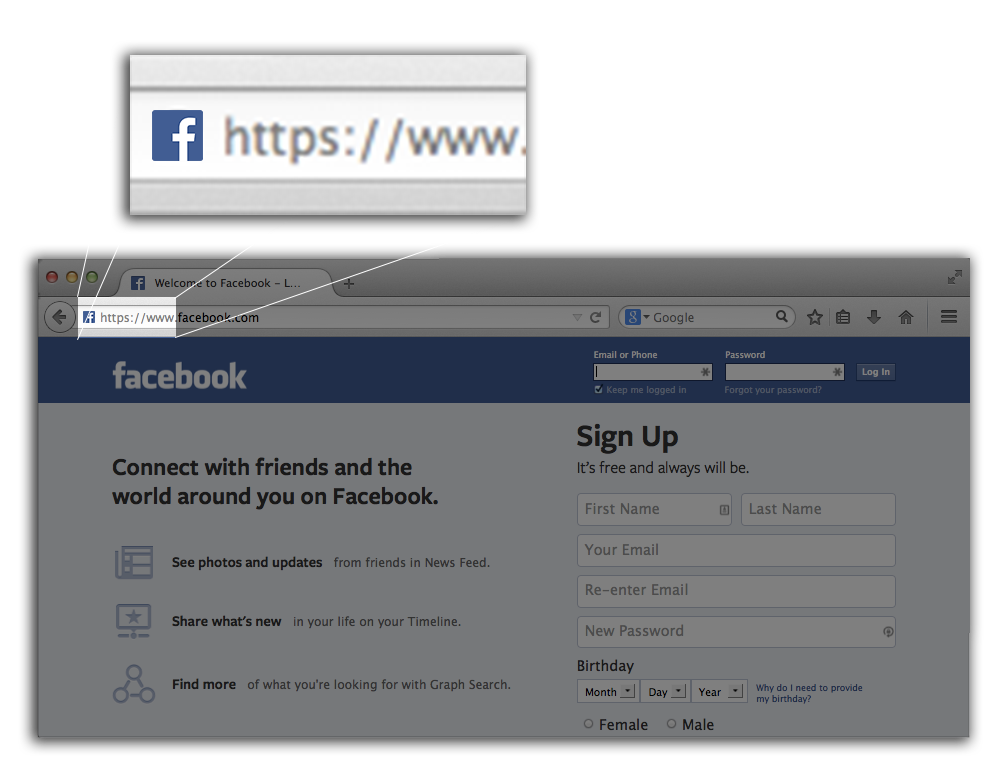
Lock Icon + https
Prior Research on 'https' + lock
- Many studies with various methodologies showing a lack of effectiveness
- Gathering evidence: use of visual security cues in web browsers (Whalen & Inkpen, 2005)
- Why phishing works. (Dhamija, Tygar, & Hearst, 2006)
- The emperor's new security indicators. (Schechter, Dhamija, Ozment, & Fischer, 2007)
"All 63 participants entered their passwords and completed this task, despite the absence of HTTPS indicators..." –Schechter et al. (2007)
"Extended Validation" + https...
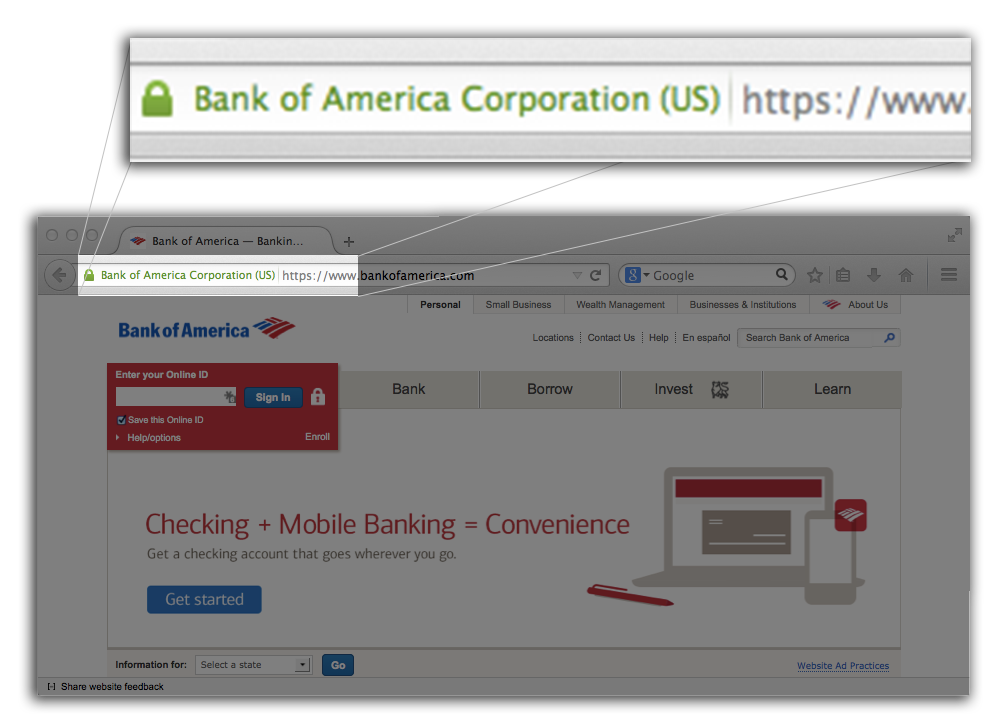
Prior Research on EV icons
- An evaluation of extended validation and picture-in-picture phishing attacks (Jackson, et. al 2007)
- Participants compared screenshots of phishing vs real websites, EV certs had no effect.
The Present Study
Do users notice and use "Extended Validation" iconography?
Method & Participants
- Twenty students were randomly approached in a university library and offered $5 to participate in an experiment.
- Half assigned to modified Firefox which disabled EV iconography, control group used unmodified Firefox.
- Asked to login to Outlook/Live/Hotmail, Twitter, and/or any financial account and perform filler tasks.
Results
-
Zero participants mentioned EV or other security indicators in the early free response questions.
- Three participants mentioned site being slow.
- Three participants claimed to notice lack of EV but appear to two logged in anyway(!)
- Two participants avoided logging into an account, one in the control and one in the manipulation group.
- One participant (a computer science student) noticed that EV was not working, did not mention it in his response.
- One participant noticed that the TLS cert was issued by "The Russian Mafia" (which is what we named our fake certificate authority).
Statistical Analysis
EV Login logging into any website using EV Fisher's p = 0.7
Bank Login logged into a financial site using EV Fisher's p = 0.657
Avoid Login avoided logging into a site Fisher's p = 0.669
Differences any perceivable changes Fisher's p = 0.218
•EV removal add-on made some browsing sluggish.
Conclusion: Extended Validation iconography had no statistically significant impact on end-user behavior.
Possible Confounds
- Software slowed down load-times.
- Many participants first started by checking on their phone.
- Browser history showed participants logged into email but only one every emailed us, probably an issue on our end.
- Only a few sites with extended validation and some subjects had banking sites without EV or that broke for some reason.
- Security conscious subjects may have simply not logged into because they were on a public computer.
- All but three participants logged into an account.
- Next time ask participants if they can identify phishing vs real site using screenshots.
- Ask participants if they know what the EV icon means.
Discussion
Imagine if a bug in a major crypto library enabled arbitrary MITM attacks...
- Apple's GoToFail and GnuTLS lib/x509/verify.c both allowed arbitrary MITM attacks.
- Everyone freaked out, fixed within a few days.
- We have known about this problem for a decade.
- Spooks (NSA, China, et al.), criminals, and Cert Authorities are the only people with anything to gain from the current system.
THIS IS EVERY BROWSER CONNECTION
Try Again?
- When https failed we grouped it with the lock icon.
- When the lock icon failed we tried EV.
- Research on new icons/imagery is always promising:
- Shining chrome: using web browser personas to enhance SSL certificate visualization (Maurer, Luca, & Stockinger, 2011).
- Changing the entire browser skin helps... kinda.
- Browser Interfaces and Extended Validation SSL Certificates
- New icons for EV marginally improve some metrics.
- etc.
- One thing that binds these studies together is the entrenched security model. One study blamed users carelessness with ids and passwords on 3rd variable effects (Whalen & Inkpen, 2005).
Security Model is Broken!
-
Change blindness.
- Habituation and the cognitive unconscious.
- ∴ Security indicators cannot work.
- ∴ Self-signed is the new default.
Cultural Failure
usability vs security
gravity vs flight
usability == security
- Any solution must protect the average user against an average attacker by default.
- Must also enable expert users to defend against global adversaries such as the NSA or the Chinese government.
Potential Solutions
-
Usable
- End dragnet surveillance
-
Robust against governments
-
Robust against organized crime
- Robust against script kiddies
Perspectives, MonkeySphere, and Convergence
-
Choose who you trust.
- Stalled out.
- Probably due to lack of incremental changes.
Step 1: Encryption Everywhere
-
Self-signed certs cause big, scary warnings.
-
Regular encryption is as worthless as no encryption.
- ∴ ZERO reason for these scary warnings.
Change in UX
- Unencrypted http connections (eventually) display big scary warning about being unencrypted.
Changes in Industry
-
Minor tweak to 4 browser vendors.
-
Add self-signed by default to 3 web servers.
- Add verified/signed but unencrypted transport for CDNs, caching, etc ?
What this gets us:
-
Usable √
-
End dragnet surveillance √
-
Robust against governments X
-
Robust against organized crime X
-
Robust against script kiddies X
Step 2: Behavioral Warnings
- Sites where user inputs data is relatively small.
- Sites where user inputs passwords is very small.
-
∴ Warn based on combination of behavioral data and external risk assessment á la Convergence.
- Sites where user inputs data is relatively small.
- Sites where user inputs passwords is very small.
- ∴ Warn based on combination of behavioral data and external risk assessment á la Convergence.
Change in UX
- None for all sites that don't have passwords.
- Use FIDO 2-factor auth for websites with passwords.
- Encryption still free & trustworthy for site admins.
- None for all sites that don't have passwords.
- Use FIDO 2-factor auth for websites with passwords.
- Encryption still free & trustworthy for site admins.
Changes in Industry
- CA Auth → Insurance Providers
- CA Auth → Insurance Providers
What this gets us:
- Usable √
- End dragnet surveillance √
- Robust against governments X
- Robust against organized crime √
- Robust against script kiddies √
- Usable √
- End dragnet surveillance √
- Robust against governments X
- Robust against organized crime √
- Robust against script kiddies √
Step 3: Trustless Clients
- New data structures and protocols (Namecoin specifically) allow us to build trust-less clients.
- We don't have to trust any third party, we can trust the data structures themselves.
-
∴ We need to move DNS to these data structures.
- New data structures and protocols (Namecoin specifically) allow us to build trust-less clients.
- We don't have to trust any third party, we can trust the data structures themselves.
- ∴ We need to move DNS to these data structures.
Changes in Industry
-
Revolution! Experimentation!
- Start small, IETF approval of experimental domains.
-
∴ Improve incrementally, scale what works.
- Revolution! Experimentation!
- Start small, IETF approval of experimental domains.
-
∴ Improve incrementally, scale what works.
What this gets us:
- Usable √
- End dragnet surveillance √
- Robust against governments √
- Robust against organized crime √
- Robust against script kiddies √
- Usable √
- End dragnet surveillance √
- Robust against governments √
- Robust against organized crime √
- Robust against script kiddies √
Closing
-
The web was built as a "series of 4 AM decisions."
- A lot of good came out of those early decisions.
- A lot of new crypto has come out since then.
-
∴ It's time that we make some new 4 AM decisions.
Thank You
Bibliography
- Biddle, van Oorschot, Patrick, Sobey, & Whalen, (2009). Browser interfaces and extended validation SSL certificates: an empirical study. In Proceedings of the 2009 ACM workshop on Cloud computing security (pp. 19–30). AC
- Gilovich, Medvec, & Savitsky, (2000). The spotlight effect in social judgment: an egocentric bias in estimates of the salience of one’s own actions and appearance. Journal of Personality and Social Psychology, 78(2), 211.
- Jackson, Simon, Tan, & Barth, (2007). An evaluation of extended validation and picture-in-picture phishing attacks. Financial Cryptography and Data Security, 281–293.
- Marlinspike, (2011, August). SSL and the Future of Authenticity. Presented at the Black Hat Security Conference, Las Vegas. Retrieved from http://blackhat.com/html/bh-us-11/bh-us-11-archives.html
- Rainie, Kiesler, Kang, & Madden, (2013, June). Anonymity, Privacy, and Security Online Omnibus DataSet. Pew Research Center’s Internet & American Life Project. Retrieved from http://www.pewinternet.org/2013/09/05/anonymity-privacy-and-security-online/
- Schechter, Dhamija, Ozment, & Fischer, (2007). The emperor’s new security indicators. In Security and Privacy, 2007. SP’07. IEEE Symposium on (pp. 51–65). IEE
- Simons, & Chabris, (1999). Gorillas in our midst: Sustained inattentional blindness for dynamic events. Perception-London, 28(9), 1059–1074.
- Whalen, & Inkpen, (2005). Gathering evidence: use of visual security cues in web browsers. In Proceedings of Graphics Interface 2005 (pp. 137–144). Canadian Human-Computer Communications Society.
Web Encryption 2.0
By Zach Lym
Web Encryption 2.0
- 1,335