Week 9
Please sit on the right half of the room
--->
Cryptography
What is cryptography?
Cryptography: Using codes or ciphers to protect information from unauthorized access
- Modern cryptographic algorithms are based on computational hardness assumptions, and have a variety of use cases, for example
- Encrypting Web Traffic: Ensuring in-transit data can't be read by unauthorized users
- Ensuring Data Integrity: Verifying data hasn't been modified or corrupted
- Obfuscation: Malware might encrypt portions of its data to hide from analysis
Review: Hashing
Hashes are one-way functions
- Most common hash functions take an input of arbitrary size and produce an output of a fixed length
- It's meant to be hard/impossible to derive the input data from the hash
- Common algorithms: SHA256, MD5
- What are some potential use cases?
- Verifying data integrity
- Password hashing
Simple XOR
# Example: XOR Encryption and Decryption with a Single Byte Key
# Original data block (plaintext)
data_block = bytearray("Hello, World!", "utf-8")
# Single byte key for XOR encryption/decryption
key = 0x5A # Example key byte
# Encrypt the data block by XORing each byte with the key
encrypted_data = bytearray()
for byte in data_block:
encrypted_byte = byte ^ key
encrypted_data.append(encrypted_byte)
print("Encrypted Data:", encrypted_data)
# Decrypt the data block by XORing each byte with the same key
decrypted_data = bytearray()
for byte in encrypted_data:
decrypted_byte = byte ^ key
decrypted_data.append(decrypted_byte)
print("Decrypted Data:", decrypted_data.decode("utf-8"))
Candidate use cases
- Hide strings from exespy?
- Hide strings from x64dbg?
- Hide strings from Ghidra?
- Encrypt data on-disk?
- Encrypt web traffic?
Some Math
-
Given, key ^ plaintext = ciphertext- I want to derive the equation that gets me the key
-
Therefore, plaintext ^ cyphertext = key - So we can recover the key by xoring the encrypted data with some plaintext that we know
Known Plaintext Attack
00000000: 7f45 4c46 0201 0100 .ELF....
00000008: 0000 0000 0000 0000 ........
00000010: 0300 3e00 0100 0000 ..>.....
00000018: 104f 0000 0000 0000 .O......
00000020: 4000 0000 0000 0000 @.......
00000028: 78f3 0100 0000 0000 x.......
00000030: 0000 0000 4000 3800 ....@.8.
00000038: 0d00 4000 1e00 1d00 ..@.....
00000040: 0600 0000 0400 0000 ........
00000048: 4000 0000 0000 0000 @.......Since a symmetrical XOR is used for both encryption and decryption, we can recover the key by xoring the encrypted data and plaintext
00000000: 25 1F 16 1C 58 5B 5B 5A |.%..X[[Z|
00000008: 5A 5A 5A 5A 5A 5A 5A 5A |ZZZZZZZZ|
00000010: 5D 5A 1C 5A 5B 5A 5A 5A |]Z.Z[ZZZ|
00000018: 4A 17 5A 5A 5A 5A 5A 5A |J.ZZZZZZ|
00000020: 1A 5A 5A 5A 5A 5A 5A 5A |.ZZZZZZZ|
00000028: 22 B1 5B 5A 5A 5A 5A 5A |".[ZZZZ|
00000030: 5A 5A 5A 5A 1A 5A 62 5A |ZZZZ.ZbZ|
00000038: 4F 5A 1A 5A 44 5A 47 5A |OZ.ZDZGZ|
00000040: 5E 5A 5A 5A 5E 5A 5A 5A |^ZZZ^ZZZ|
00000048: 1A 5A 5A 5A 5A 5A 5A 5A |.ZZZZZZZ|
Encrypted ELF
Decrypted ELF
Will making the key longer solve this problem?
Solution: One Time Pad
One Time Pad: XOR operation where the key length is equal to the message length
- Again, let's consider some candidate use cases:
- Hide strings from exespy?
- Hide strings from x64dbg?
- Hide strings from ghidra?
- Encrypt data on disk?
- Encrypt web traffic?
Other Weakness: Key size must match the total data length, which might be quite large
Symmetric-Key Algorithms
Symmetric Key Encryption Algorithms are those where the encryption and decryption key are the same. Similar uses as one-time pads but solve the key-length problem.
- Here are some common examples
- AES: Key size of 128/192/256 bits, block of 128 bits
- DES: Key size of 56 bits, block size of 64 bits
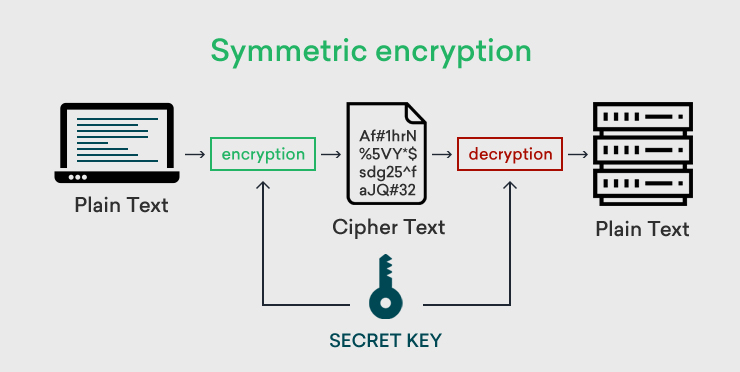
Problem: Does this help us secure web traffic?
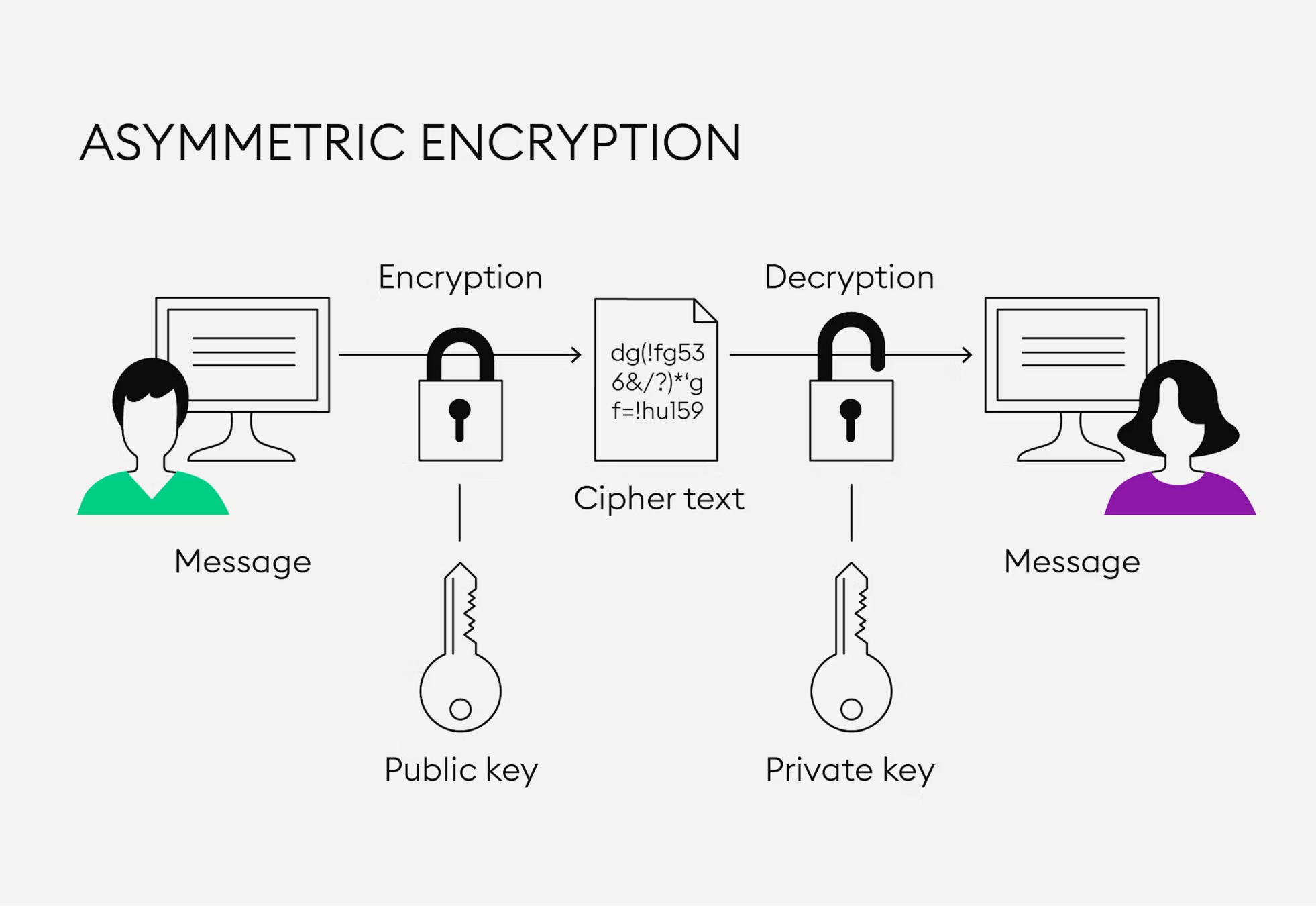
Asymmetric-Key Algorithms
Asymmetric Key Encryption Algorithms are those where the encryption and decryption key are different. E.g RSA.
- For example, consider secure data transmission:
- Receiver generates a private key used for decryption, and derives a public key used for encryption
- Anyone can encrypt data with the public key, but only the receiver can decrypt it with the private key
- Assumes the hardness of deriving the private key from the public key
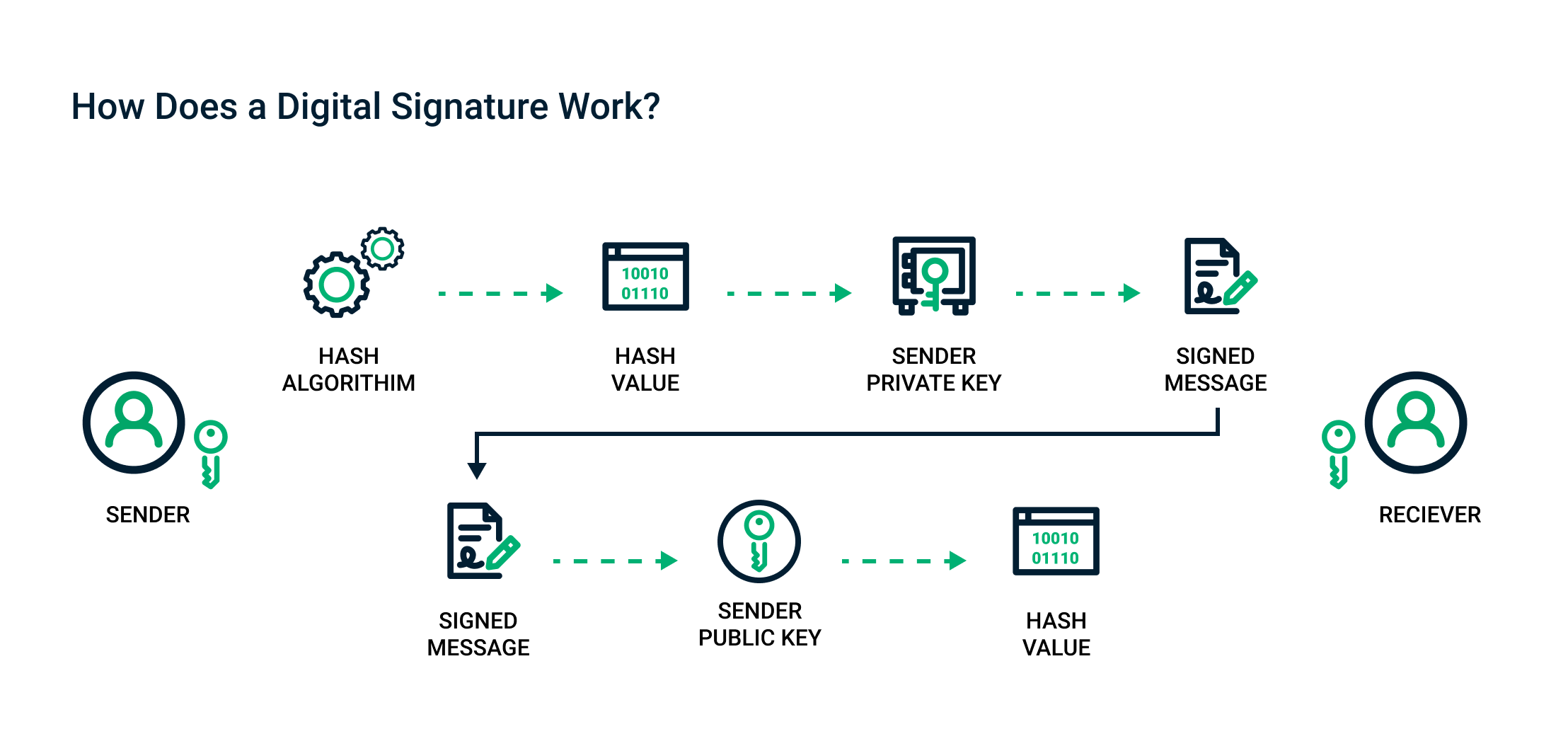
Digital Signatures
Use to verify the data comes from an authorized sender
- For signatures, the decryption key is shared publicly
- The sender uses the private key to encrypt a hash of the data they send
- The receiver uses the public encryption key to decrypt the hash
- If it matches, the message came from the same person that originally broadcast the public key
Questions?
Case Study: HTTPS/TLS
SSL/TLS
SSL/TLS: Stands for Secure Socket Layer/Transport Layer Security. Mostly used for securing web traffic. It combines all the concepts we've previously covered.
- Consists of three protocols:
- Handshake Protocol: Uses RSA/ECC to exchange a symmetric key and sign messages
- Record Protocol: Uses AES (or 3DS) to efficiently encrypt the transmitted data
- Alert Protocol: Use to transmit errors/warnings, usually within the record protocol encryption
Lab 1
SSL/TLS
Week 9
By Chase Kanipe
Week 9
- 219



