Securing Linux services
Kushal Das
@kushaldas
DeiC konference 2022
CC-BY-SA 4.0
CC-BY-SA 4.0
@kushaldas
@kushaldas



@kushaldas

@kushaldas


@kushaldas
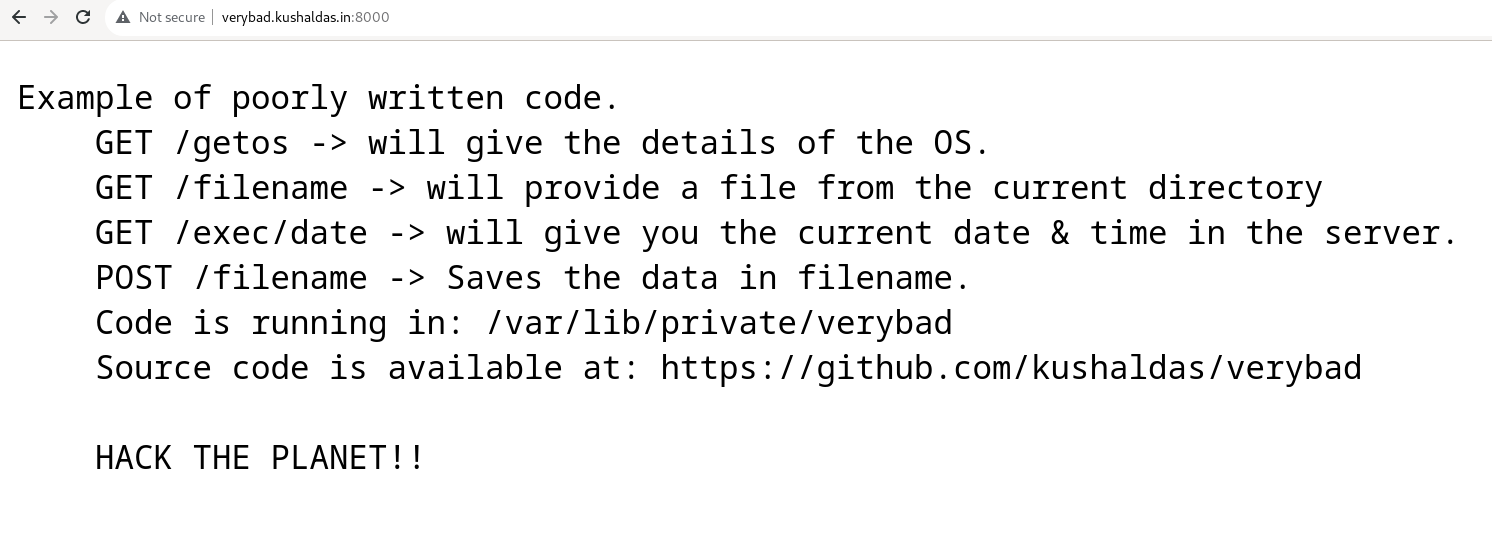
http://verybad.kushaldas.in:8000/
@kushaldas

@kushaldas
man systemd.exec
@kushaldas
PrivateTmp=
@kushaldas
@kushaldas
ProtectHome=
@kushaldas
@kushaldas
ProtectProc=
But not for root user
@kushaldas
TemporaryFileSystem=
TemporaryFileSystem=/var:ro
BindReadOnlyPaths=/var/lib/systemd@kushaldas
@kushaldas
PrivateDevices=
Adds API pseudo devices, /dev/zero, /dev/null
@kushaldas
@kushaldas
ProtectKernelModules=
Loading/unloading kernel modules are not allowed.
@kushaldas
RestrictFileSystems=
RestrictFileSystems=ext4 tmpfs@kushaldas
@kushaldas
[Service]
Type=simple
ExecStart=/usr/sbin/verybad
Restart=always
DynamicUser=yes
StateDirectory=verybad
WorkingDirectory=/var/lib/verybad
PrivateDevices=yes
NoExecPaths=/
ExecPaths=/usr/sbin/verybad /usr/lib/systemd/systemd /lib64/ld-linux-x86-64.so.2 /lib64/libgcc_s.so.1 /lib64/libm.so.6 /lib64/libc.so.6 /usr/bin/date
Environment="ROCKET_ADDRESS=0.0.0.0"
TemporaryFileSystem=/etc:ro
BindReadOnlyPaths=/etc/os-release /etc/localtime /var/lib/verybad/Rocket.toml
InaccessiblePaths=/dev/full /dev/zero
PrivateDevices=yes
ProtectProc=invisible
@kushaldas
https://kushaldas.in
Thank you :)
DeiC konference 2022
By dascommunity
DeiC konference 2022
- 646



