Universal Second Factor authentication
or why 2FA today is
wubalubadubdub
Yuriy Ackermann
Sr. Certification Engineer @FIDOAlliance
twitter/github: @herrjemand


































Today we will learn
- Why passwords not enough
- Why 2FA has not succeeded
- Introduction to U2F
- DEMO
- Q&A

Why not just passwords?
Weak
Phishing
Reuse


Typical passwords life cycle
SOLUTION!
Two Factor Authentication - aka 2FA


pwned
haveibeenpwned.com
What is 2FA?
Passwords verify
2FA authenticate

Do you use 2FA?

What does 2FA looks like?
Three main types
Apps
Tokens
SMS
(TOTP and HOTP)
(PKI and OTP)





So we solved it?
Right?

Why 2FA has not succeeded?
Apps
Tokens
SMS
- Phishing!!
- UX
- Shared key
- Synced time
- Cost
- DRIVERS
- Phishing
- UX
- Centralised
- Fragile
- Still phishable
- UX
- Privacy
- Security
- SIM reissue
- SIM spoof
- Coverage
- NIST Ban








Current state of 2FA
I am in the deep pain,
please help!
So how do we solve it?
We need:
-
Easy to use
-
Open
-
Secure
-
Standardized
protocol.

Introducing
Universal Second Factor
aka FIDO U2F

How does U2F works?



User layer


Browser layer

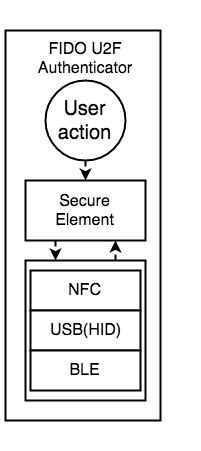
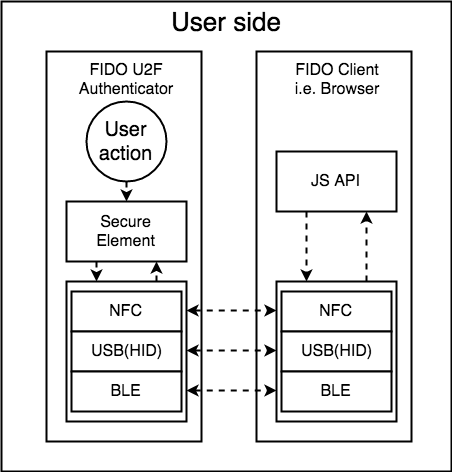
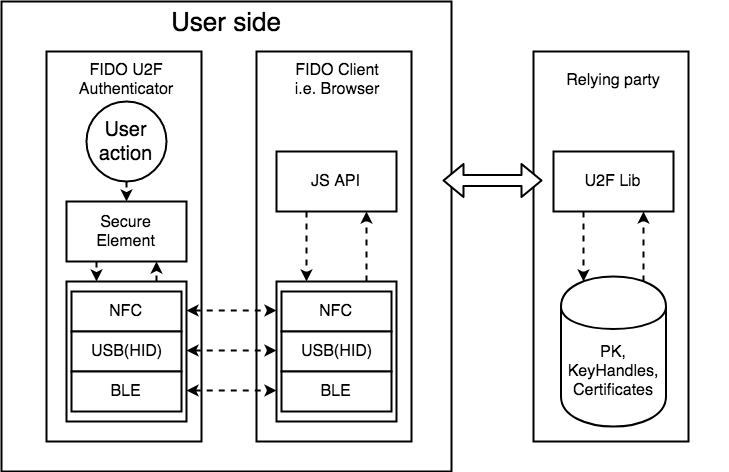
Protocol Layer


Step one: Challenge-Response


Step two: Phishing protection


Step three: Application-specific key-pair


Relying
Party
To Wrap, or not to Wrap?


Step four: Replay Attack Protection


Step five: Device attestation

Metadata service

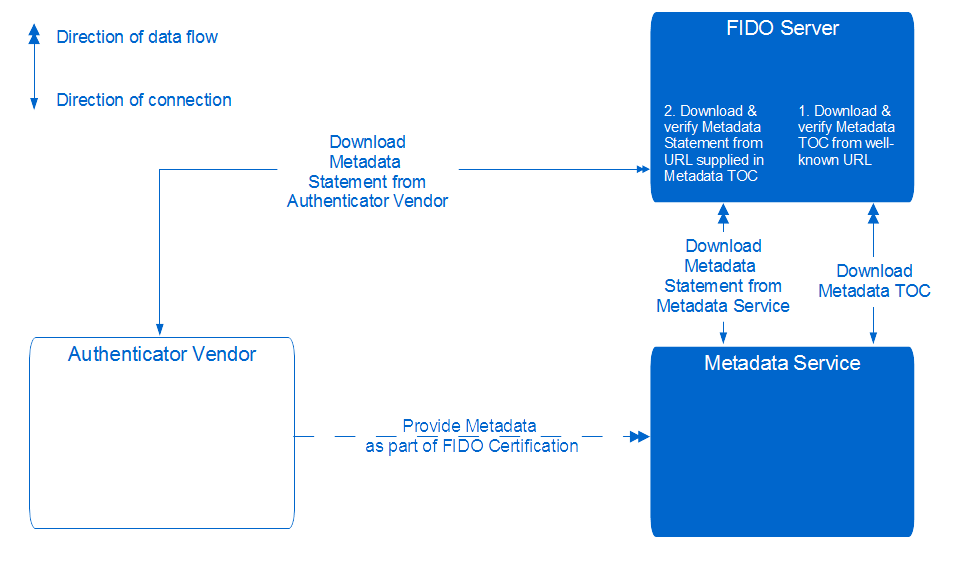
Step five and a half: Key exercise protection
User must confirm their decision to perform 2FA, by performing user gesture

e.g.
Fingerprint
Retina scan
Pincode
Remembering your wife's birthday.
Solving Rubikscube
...anything you want.
Pressing button

Multiple identifiers



Web
Android
iOS
How do we deal with it?
mail.google.com
apk-key-hash:FD18FA
com.google.SecurityKey.dogfood
GMail

Application Facets
{
"trustedFacets": [{
"version": { "major": 1, "minor" : 0 },
"ids": [
"https://accounts.google.com",
"https://myaccount.google.com",
"https://security.google.com",
"android:apk-key-hash:FD18FA800DD00C0D9D7724328B6D...",
"android:apk-key-hash:/Rj6gA3QDA2ddyQyi21JXly6gw9D...",
"ios:bundle-id:com.google.SecurityKey.dogfood"
]
}]
}MUST be served over VALID HTTPS!
...no self signed certs.

Implementations











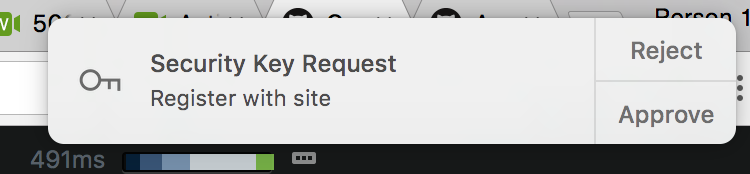


Current users






dongleauth.info

Browser support


Yes
Yes*
(Nightly)
No*
(Soon...)

Maybe?

Yes
WebAuthN
A W3C standard for PublicKey credential authentication
https://www.w3.org/Webauthn/

Today we learned
- Passwords are hard
- 2FA is wubalubadubdub, and we need to do something about it.
-
FIDO U2F is sweet.
- Protocol is cute
- You can have multiple identities
- There are existing solutions...
- ...and people do use it

DEMO
- You must use HTTPS
- Start using TLS Channel ID's
- U2F is just 2FA. Don't use as primary factor.
Security considerations

- https://github.com/Yubico/pam-u2f
- https://github.com/Yubico/python-u2flib-server
- https://github.com/Yubico/python-u2flib-host
- https://github.com/herrjemand/flask-fido-u2f
- https://github.com/gavinwahl/django-u2f
- https://github.com/google/u2f-ref-code
- https://github.com/conorpp/u2f-zero
- https://developers.yubico.com/U2F/
- https://fidoalliance.org/specifications/download/
- https://github.com/LedgerHQ <- JavaCard
- FIDO Dev (fido-dev) mailing list
Specs and data
Things to play with

What's next?
WE NEED










Questions?
twitter/github: @herrjemand

Quick thanks to
Feitian and Yubico
for swag!



Thank you OWASP!

Universal Second Factor authentication, or why 2FA today is wubalubadubdub? - OWASP LONDON FEB 2018
By FIDO Alliance
Universal Second Factor authentication, or why 2FA today is wubalubadubdub? - OWASP LONDON FEB 2018
OWASP London presentation on FIDO Universal Second Factor Authentication.
- 4,311

