Semi-Automated and Easily Interpretable
Side-Channel Analysis for Modern JavaScript
Cryptology and Network Security 2024, Cambridge
Iliana FAYOLLE †, Jan WICHELMANN ‡, Anja KÖHL ‡,
Walter RUDAMETKIN *, Thomas EISENBARTH ‡, Clémentine MAURICE †
† Univ. Lille, CNRS, Inria, France
‡ University of Lübeck, Germany
* Univ. Rennes, CNRS, Inria, France







FACT
More and more developers are turning to web technologies to build their applications.
Application
Side-channel
Secret Data
non-secured

Side-channel leakage
Side-channel leakage in software

- Control flow
- Memory usage / allocation

Application
Secret Data

Constant-time

secured
Side-channel
Constant-time implementations
A countermeasure?
No branching depending on a secret.
1.
No memory access or allocation depending on a secret.
2.
Do we have tools for this?

CacheAudit
Binsec/Rel
ctgrind
CacheQL
DiffFuzz
ct-fuzz
Microwalk
YES! A LOT!
BUT ... No one uses them.
BUT ... No one uses them.


- Poor usability,
- not well documented,
- compatibility problems,
- not integrated into development processes.
Microwalk-CI (CCS'22)

Statistical methods.
Practical leakage detection framework:
Great!
How do I use it?
:)
Dynamic analysis approach.
- Combines:
- Quickly locates and quantifies leakages.
- Analyses during Continuous Integration (CI).
- Is cross platform (Binary, C, JavaScript).
Microwalk-CI (CCS'22) tutorial
- Choose an analysis template.
Copy the template into the root of your library repository.
Merge or adjust the CI configuration and package files.
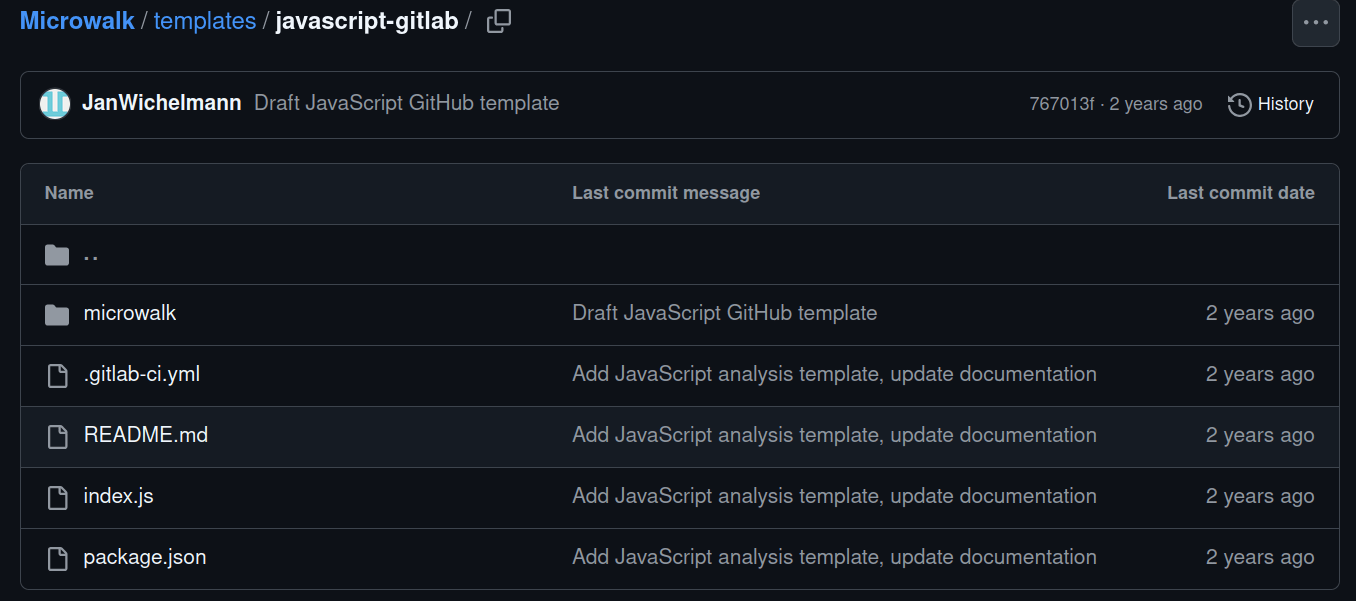
Microwalk-CI (CCS'22) tutorial
-
Choose an analysis template.
Copy the template into the root of your library repository.
Merge or adjust the CI configuration and package files.
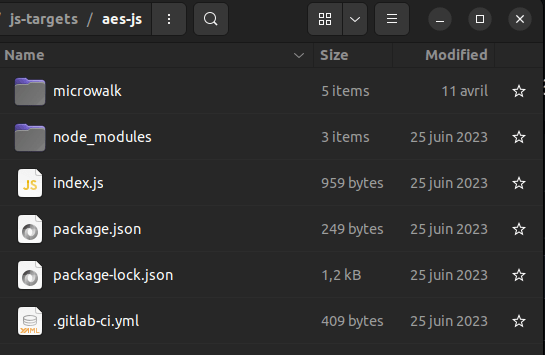
Microwalk-CI (CCS'22) tutorial
-
Choose an analysis template.
Copy the template into the root of your library repository.
Merge or adjust the CI configuration and package files.
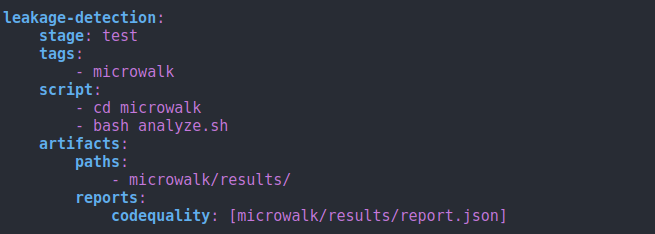
Microwalk-CI (CCS'22) tutorial
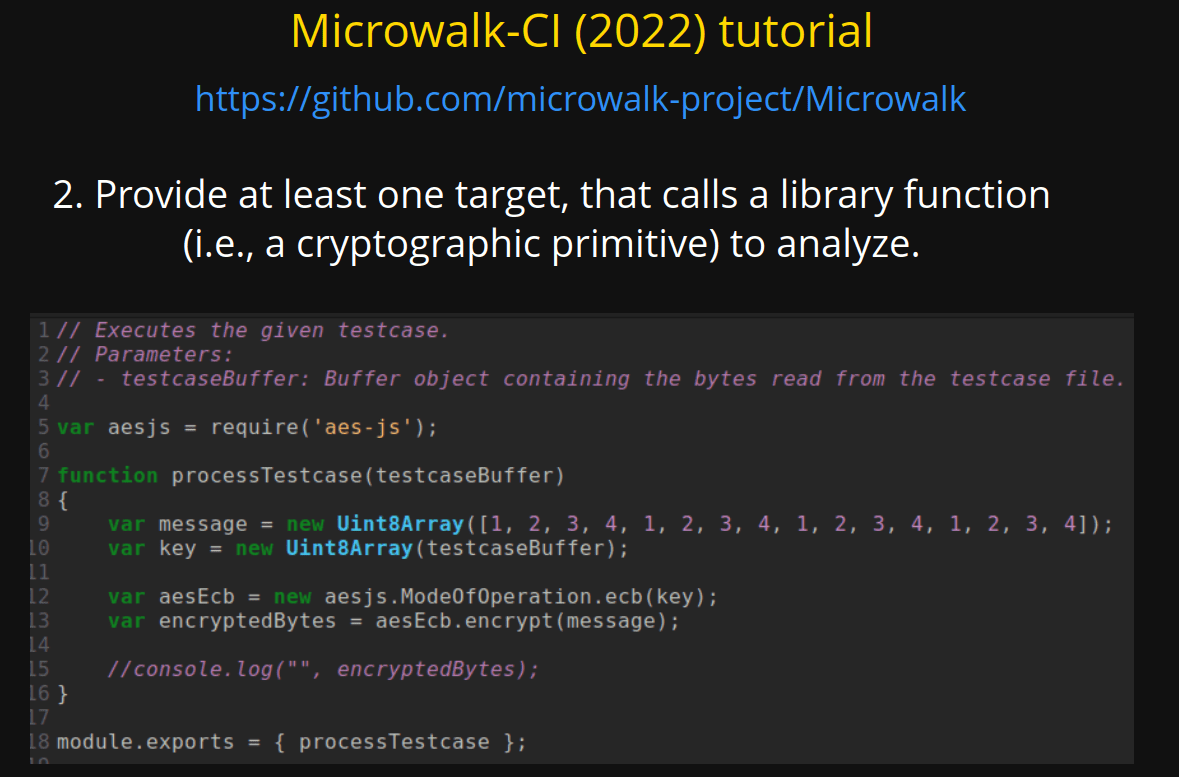
2. Provide at least one target, that calls a library function
(i.e., a cryptographic primitive) to analyze.
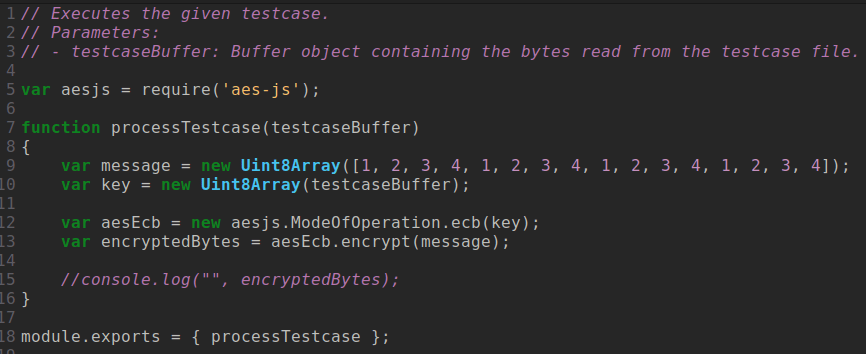
Microwalk-CI (CCS'22) tutorial
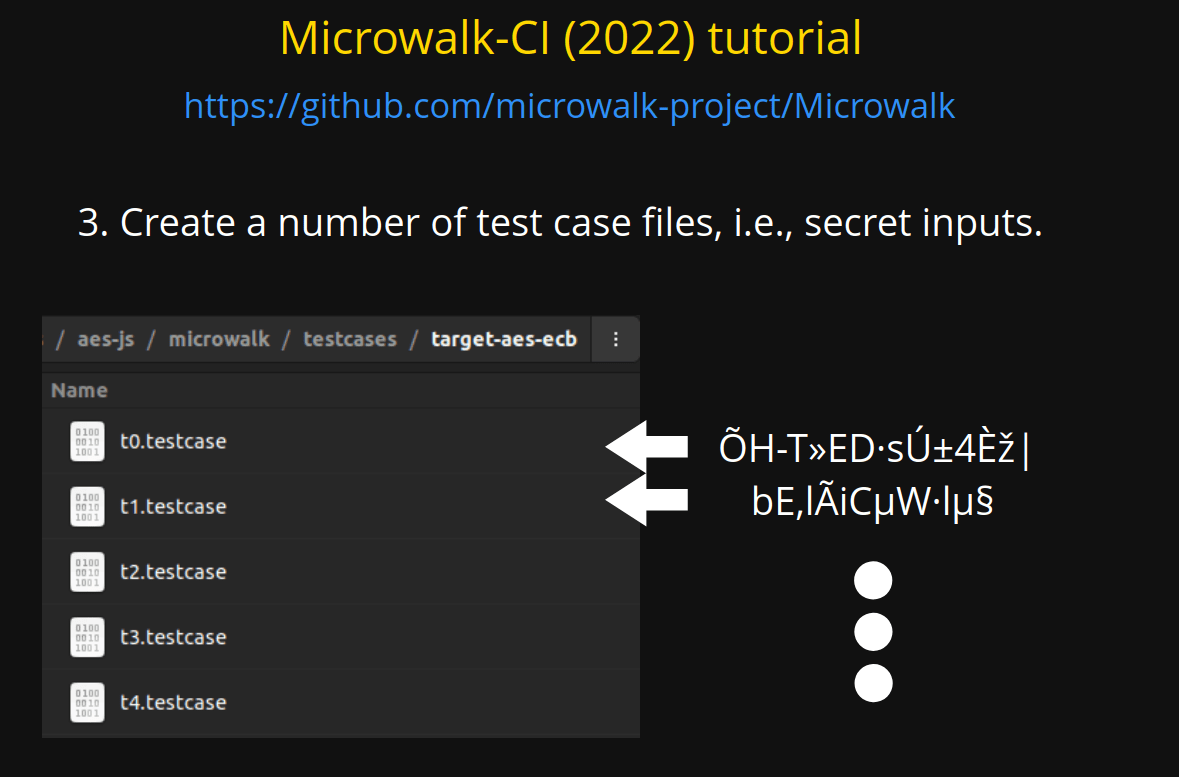
3. Create a number of test case files, i.e., secret inputs.
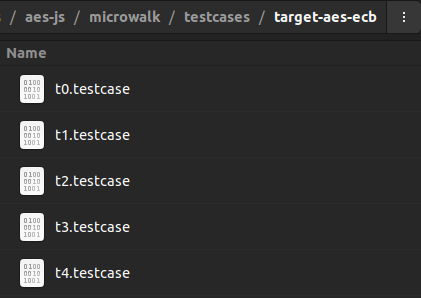
ÕH-T»ED·sÚ±4Èž|
bE,lÃiCµW·lµ§
Microwalk-CI (CCS'22) tutorial
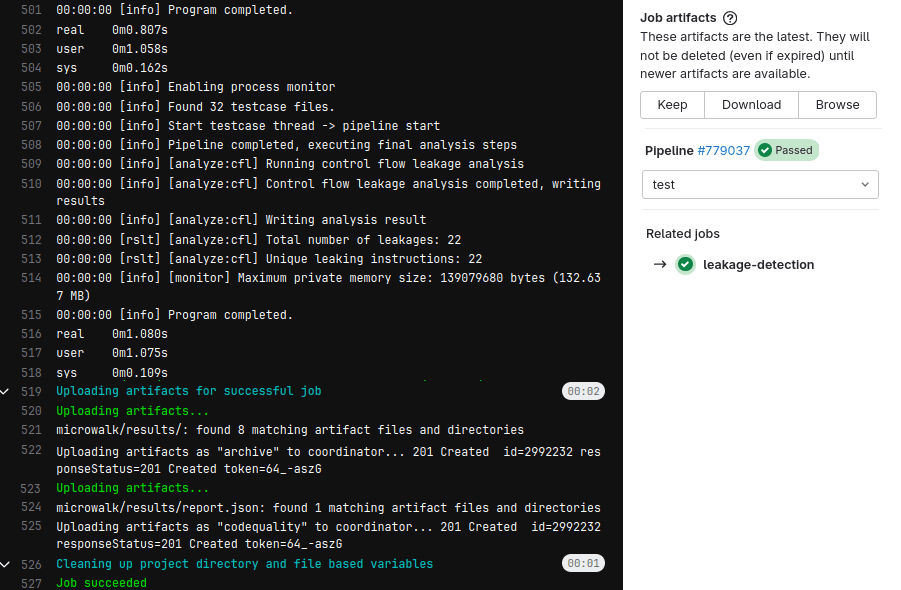
4. Push a new commit (that triggers the CI workflow).
Download the artifacts.
Microwalk-CI (CCS'22) tutorial
4. Push a new commit (that triggers the CI workflow).
Download the artifacts.
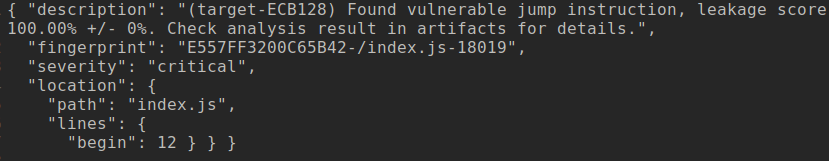
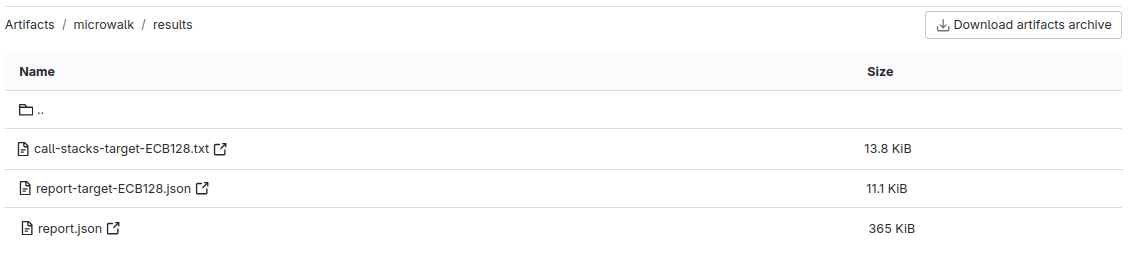
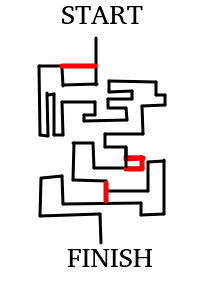
But how does Microwalk detect leakages?
Remember those two?
Will their execution paths be different?

Will their execution paths be different?
IF
ELSE
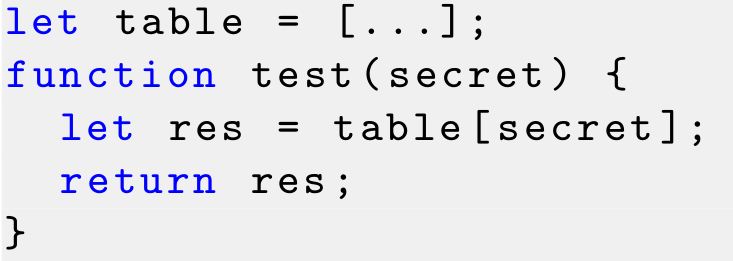
Table[key1]
Table[key2]
testcase 0
testcase 1
testcase 0
testcase 1

Will their execution paths be different?
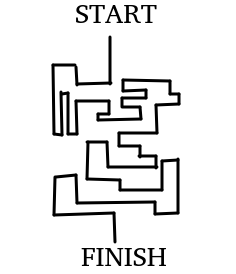
Will their execution paths be different?
2 possibilities:
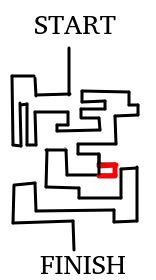
No differences between traces.
No leakage found.
At least 1 difference between traces.
A leakage is found.
testcase 0
testcase 1
Will their execution paths be different?


testcase 0
testcase 1
Will their execution paths be different?

+
testcase 2

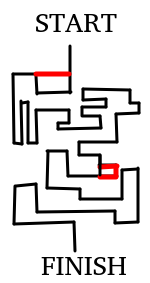
merged traces for testcases 0
; 1
Will their execution paths be different?
; 2
; 3; 4
3 leakages
What are the limits of Microwalk-CI?
Modern JavaScript libraries cannot be analyzed.
relies on
Jalangi2 framework
post-2015 versions of ECMAScript
classes
asynchronous programming
ES modules (ESM)
deferred execution
What are the limits of Microwalk-CI?
For each test ...
We are encouraged to write some testcases.
Writing tests is tedious and error-prone.
What are the limits of Microwalk-CI?

Its use requires some effort and time.
Are the tests sufficient to uncover all vulnerabilities?
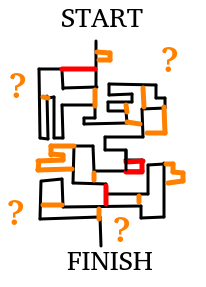
What are the limits of Microwalk-CI?
P1. Compatibility problem.
P2. Tedious test writing.
P3. Report interpretability.
Improve the compatibility of the trace generator.
Introduce semi-automation for (sub)target and test case generation.
Enhance the vulnerability report.
Contributions




AST-based Trace Generation
Semi-Automated Leakage Analysis
Evaluation
Leakage Report with Coverage
Why?
P1. Compatibility problem.
Improve the compatibility of the trace generator.
How?

AST-based Trace Generation
Transform the AST and enrich it with tracing code.
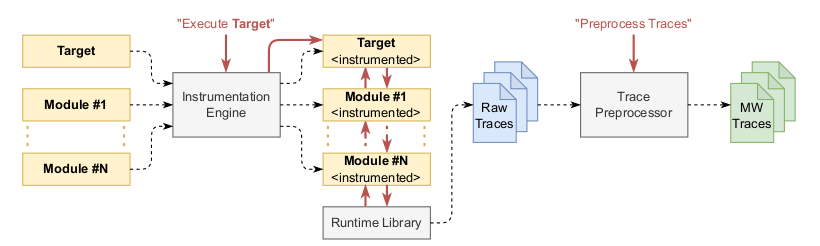
Modern JavaScript code
Converted code into a backwards compatible version of JavaScript.
Custom plugin for Babel
Represents a JavaScript program as an abstract syntax tree (AST).
How?
Result
The execution traces cover the analyzed library
modern JavaScript (ES2023)
classes
asynchronous programming
ES modules (ESM)
deferred execution
New tracer
package dependencies
written in older versions of JavaScript
no longer maintained
AND
its dependencies.

Semi-Automated Leakage Analysis
Why?
P2. Tedious test writing.
Introduce semi-automation for (sub)target and test case generation.
How?
How?
How?
How?
We designed a new generic analysis template.
Introduce Subtargets.
Automate test case generation.

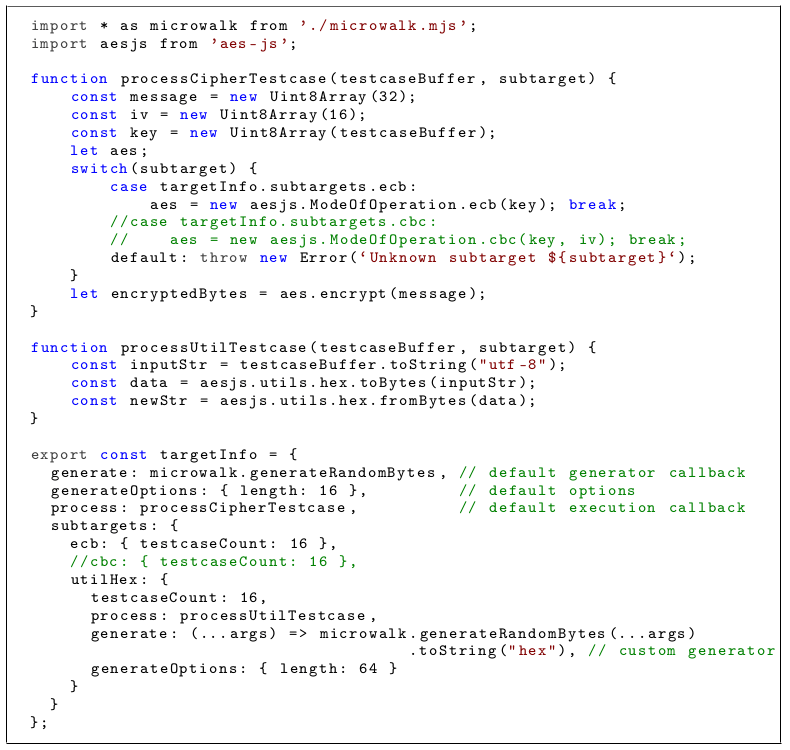
Result

Result
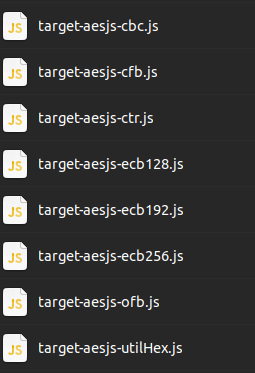
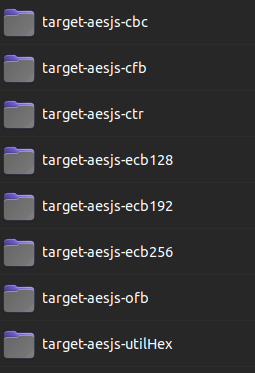
Mandatory lines for a 1st subtarget
(aes-ecb).
New lines to add another subtarget (aes-cbc).
New lines to add another target test (utilHex) with a custom test cases generator.

Leakage Report with Coverage
Why?
P3. Report interpretability.
Enhance the vulnerability report.
How?
How?


The library's code
The JSON report
The code coverage of the test suite
(with c8)
Result
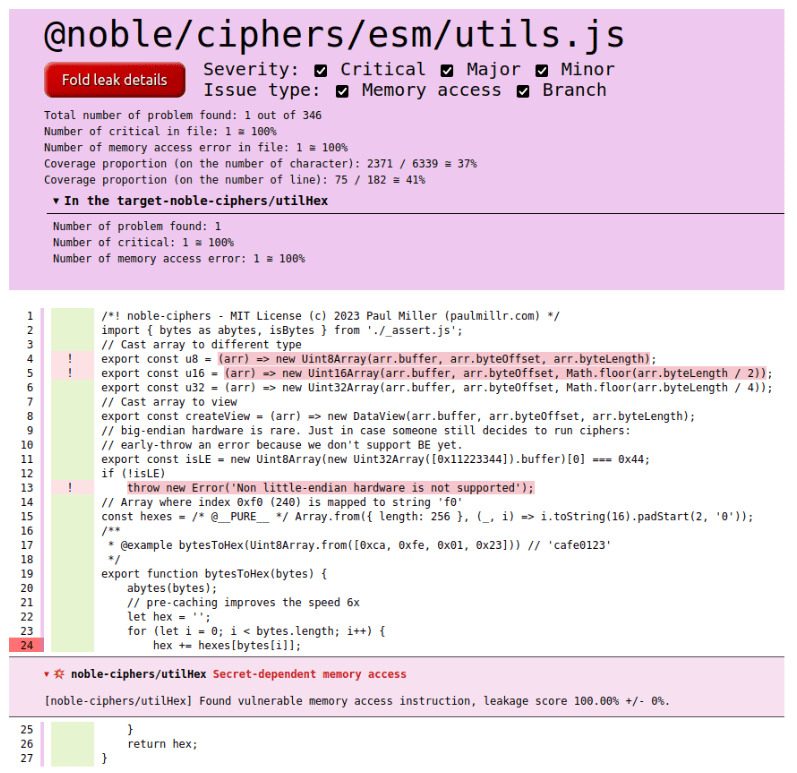
Result

Header with most important details.
Information box on the detected leak.
Code that was not executed during tests.

Evaluation
Why?
How do our enhancements allow a developer to fully analyze cryptographic libraries with minimal effort?
To sum up
- Performance:
New tracer:
- Development effort and coverage:
- Vulnerabilities:
- Need only one target file for each library.
- Findings from Wichelmann CCS'22 are validated.
Performs better.
Supports modern JavaScript.
- Maximize their coverage.
- More leakages are found.
- Previously missed code paths are identified.
135sec vs 73 sec ; < 2 GB
aes-js 80%; node-forge 45%; noble@ciphers 93%; noble@curves 72%
464 lines vs 206 lines
Conclusion
- Outperform the previous Jalangi2-based implementation.
- Uncover new vulnerabilities.
Find more vulnerabilities with less effort.

New
trace generator
New
test template
New
final report
Thank you!
(◠‿◕)

Our paper
Summary
The usability of side-channel leakage analysis tools can be further improved to aid their practical adoption.
- AST-based Trace Generation.
- Semi-Automated Leakage Analysis.
- Leakage Report with Coverage.
- Evaluation.
Our contributions:
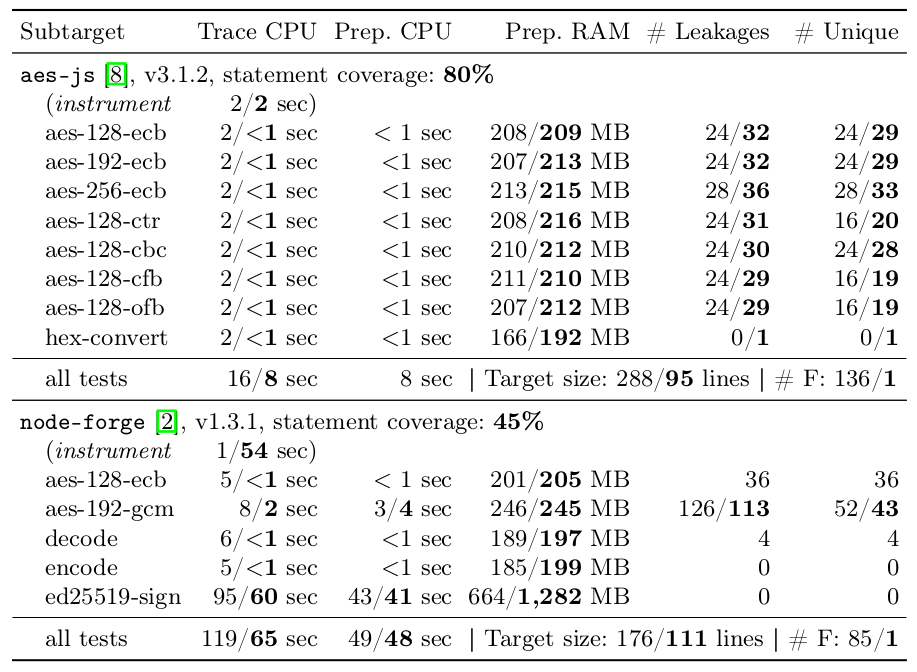
Comparison between Microwalk V3.2.0 and Microwalk using the enhanced analysis toolchain on aes-js and node-forge libraries.
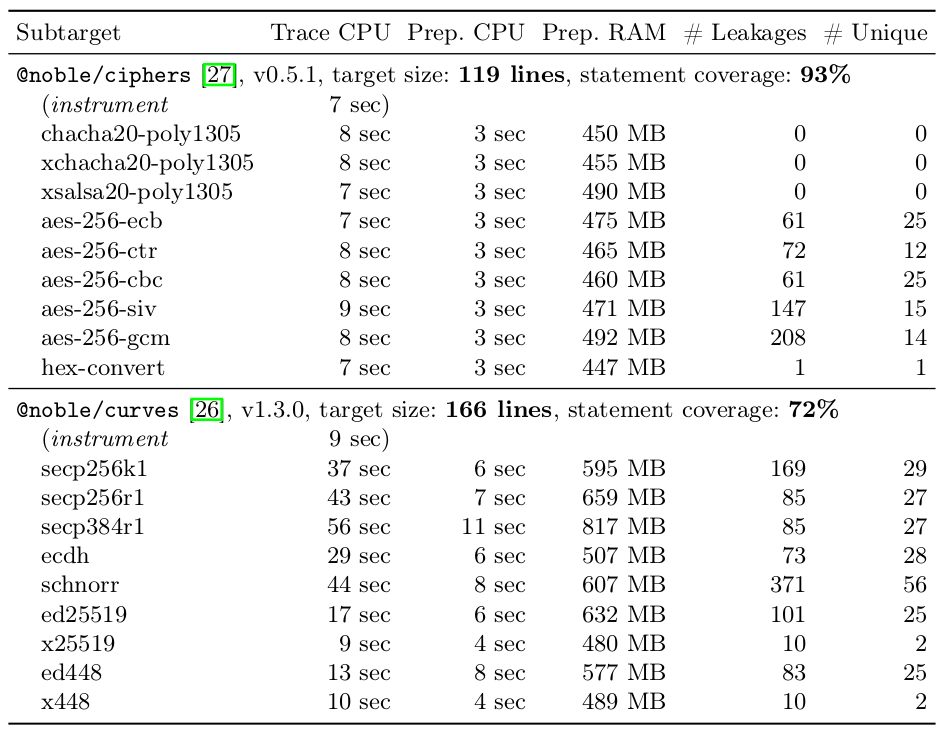
Results of using the enhanced analysis toolchain with 2 modern JavaScript cryptographic libraries: @noble/ciphers ; @noble/curves
Future Work
What about Just-in-time (JIT) compiled code?
To develop a JIT mode that does not insert new side channels.
Could the combined coverage/leakage reports be further integrated into developer workflows?
Yes!
What about randomized implementations?
To provide a randomization-capable analysis module.
Could our approach be applied to other programming languages?
Yes!
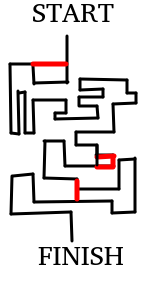
testcase 0
; 1
Will their execution paths be different?
+
testcase 2
testcase 3

testcase 0
; 1
Will their execution paths be different?
+
; 2
testcase 3
testcase 4


Side-channel
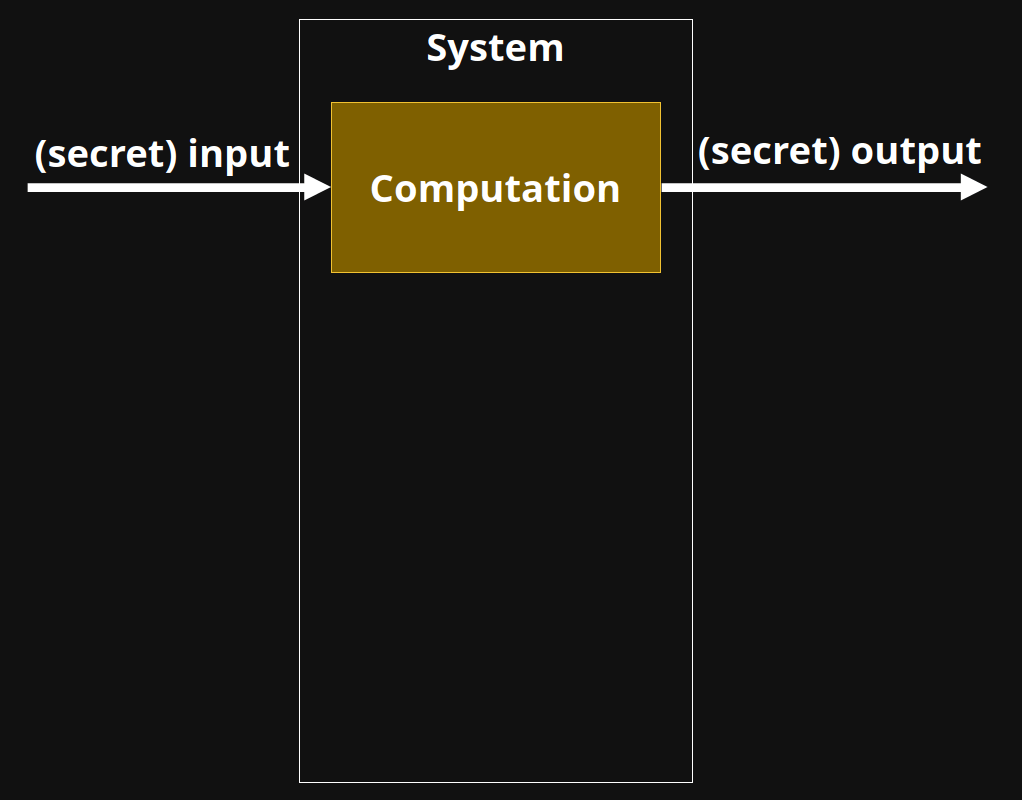
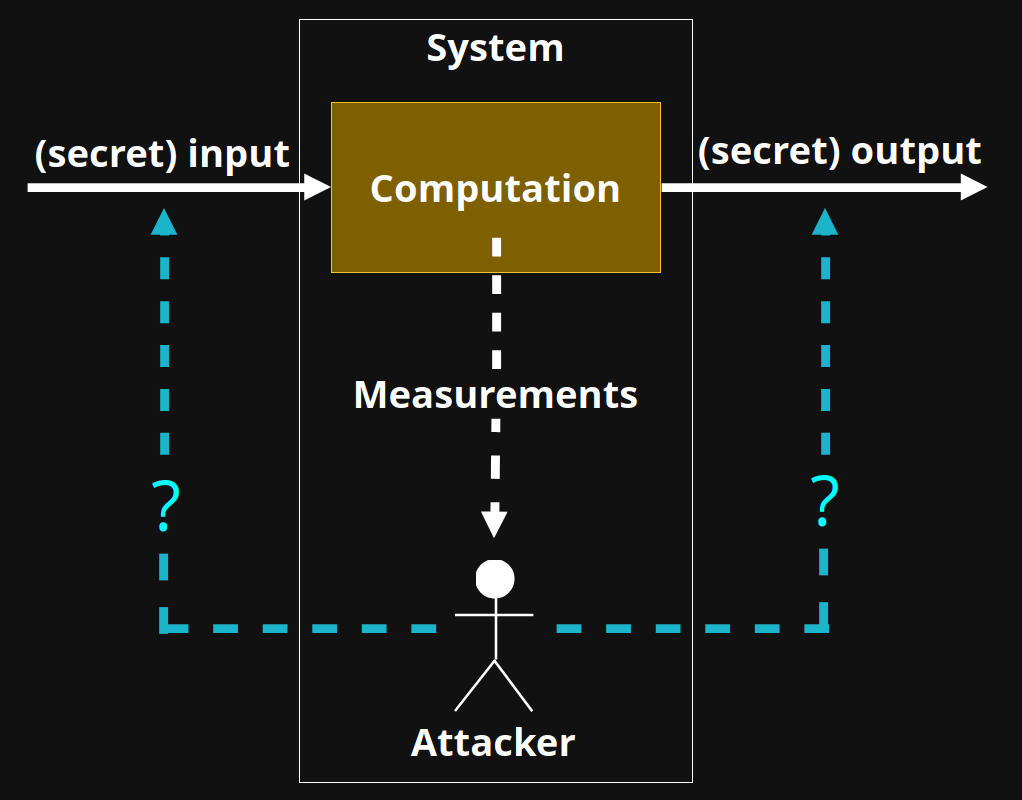
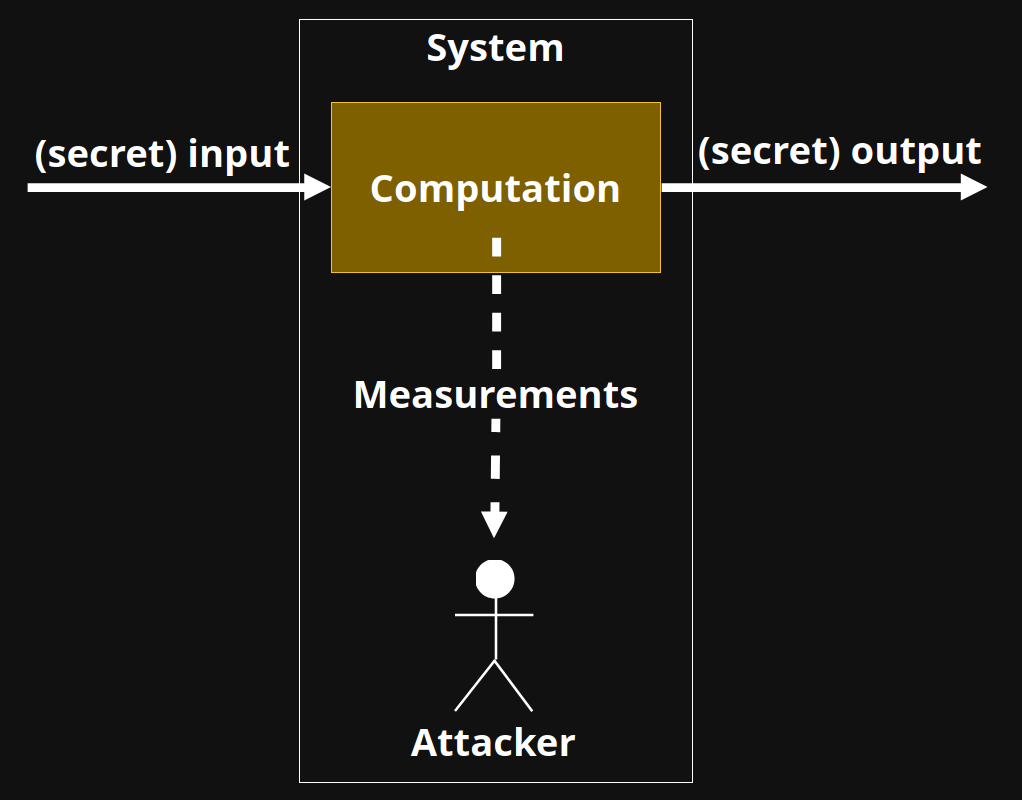
System
Computation
Measurements
Attacker
(secret) input
(secret) output
?
?
Microwalk-CI (CCS2022)

It combines a dynamic analysis approach and statistical methods to quickly locate and quantify side-channel leaks.
This tool automates side-channel analyses during Continuous Integration (CI).
It can be used on:
- Binary software,
- C,
- JavaScript libraries.
Great!
How do I use it?
:)
What are the limits of Microwalk-CI?
P1. Compatibility problem.
P2. Tedious test writing.
P3. Report interpretability.
Improve the compatibility of the trace generator by designing a new one.
Introduce semi-automation for (sub)target and test case generation.
Enhance the interpretability of the vulnerability report.
To sum up:
- Performance:
Our new tracer performs better than the legacy backend in most aspects, while supporting modern JavaScript.
- Development effort and coverage:
- Vulnerabilities:
We wrote a single target for each library, aiming for conciseness and maintainability, while maximizing their coverage.
We validate the findings from prior work and find more leakages.
Also, coverage helps to identify previoulsy missed code paths.
BUT nothing is perfect...
CANS24
By Iliana Fayolle
CANS24
- 105



