
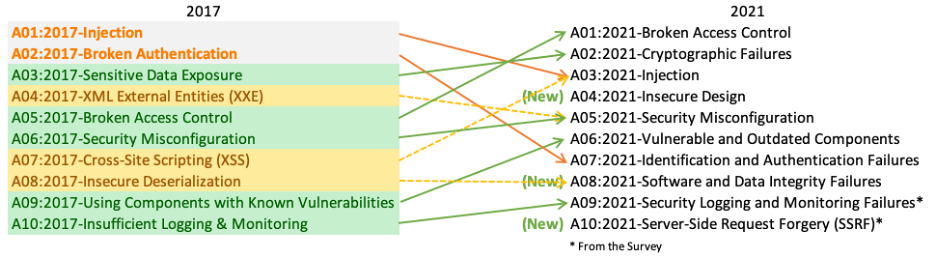
A01: 2021
Broken Access Control
Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or users, but is available to anyone.
A01: 2021
Broken Access Control
A01: 2021
Broken Access Control
A01: 2021
Broken Access Control
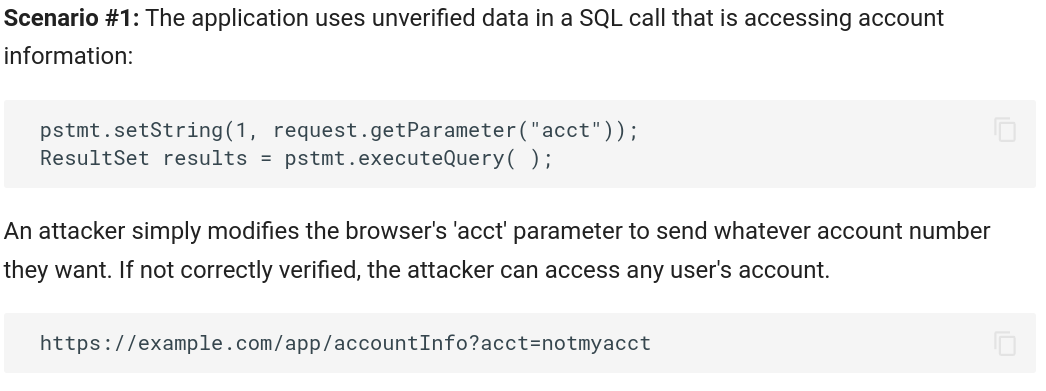
Bypassing access control checks by modifying the URL (parameter tampering or force browsing), internal application state, or the HTML page, or by using an attack tool modifying API requests.

A01: 2021
Broken Access Control
Permitting viewing or editing someone else's account, by providing its unique identifier (insecure direct object references)

A01: 2021
Broken Access Control
Accessing API with missing access controls for POST, PUT and DELETE.

A01: 2021
Broken Access Control
Elevation of privilege. Acting as a user without being logged in or acting as an admin when logged in as a user.

A01: 2021
Broken Access Control
Metadata manipulation, such as replaying or tampering with a JSON Web Token (JWT) access control token, or a cookie or hidden field manipulated to elevate privileges or abusing JWT invalidation.
A01: 2021
Broken Access Control
CORS misconfiguration allows API access from unauthorized/untrusted origins.

A01: 2021
Broken Access Control
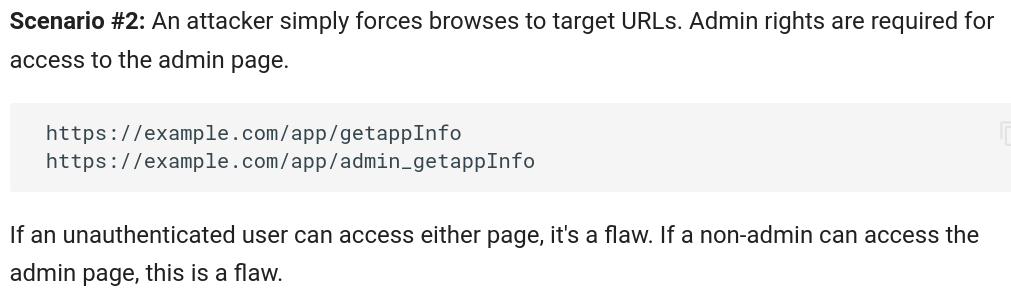
Force browsing to authenticated pages as an unauthenticated user or to privileged pages as a standard user.
How to prevent A01: 2021
Broken Access Control
Except for public resources, deny by default.

How to prevent A01: 2021
Broken Access Control
Implement access control mechanisms once and re-use them throughout the application, including minimizing Cross-Origin Resource Sharing (CORS) usage.

How to prevent A01: 2021
Broken Access Control
Model access controls should enforce record ownership rather than accepting that the user can create, read, update, or delete any record.
How to prevent A01: 2021
Broken Access Control
Unique application business limit requirements should be enforced by domain models.
How to prevent A01: 2021
Broken Access Control
Disable web server directory listing and ensure file metadata (e.g., .git) and backup files are not present within web roots.

How to prevent A01: 2021
Broken Access Control
Log access control failures, alert admins when appropriate (e.g., repeated failures).

How to prevent A01: 2021
Broken Access Control
Rate limit API and controller access to minimize the harm from automated attack tooling.

How to prevent A01: 2021
Broken Access Control
Stateful session identifiers should be invalidated on the server after logout. Stateless JWT tokens should rather be short-lived so that the window of opportunity for an attacker is minimized. For longer lived JWTs it's highy recommended to follow the OAuth standards to revoke access.

OWasp Top 10
By Johann-Peter Hartmann
OWasp Top 10
- 645



