SECURING DATA
AND COMMUNICATIONS
These are the topics I would like to cover in this presentation:
-- How to protect data stored in devices (desktop and laptop computers, mobile phones an tablets.
-- How to protect data in process (applications and software security).
-- How to protect data in transit (applications and software to protect communications)
Example of encryption. Click on this link.
YOUR SOURCES HAVE ZERO DIGITAL SECURITY CAPACITIES. HOW DO YOU COMMUNICATE SECURELY WITH THEM?
SOURCES REFUSE TO PASS TIPS TO JOURNALISTS WHO LACK DIGITAL SECURITY CAPACITIES. WHAT CAN YOU DO?
YOU ARE CROSSING A BORDER. WHAT CAN YOU DO IF A CUSTOM OFFICER ASK YOU TO RENDER YOUR PASSWORDS?
YOU HAVE ONE TERABYTE OF STORED DATA. HOW DO YOU PROTECT IT?
JOURNALISM ISSUES IN THE DIGITAL ERA
NORTH
SOUTH
Technology
Adoption
Adoption
Strategies
NORTH
SOUTH
Mapping risks
Threat
models
Threats for journalists
- Malicious software
- Unauthorized access
- System failure
- Social engineering
Threats for online media
- Injection
- Broken authentication and session management
- Broken access control
- Security misconfiguration
- Sensitive data exposure
- Insufficient attack protection
- Cross-site request forgery
- Using components with known vulnerabilities
- Underprotected APIs
Vulnerabilities
- Weak passwords
- Plain text communication
- Poor practices
- Lack of technology
- Hacked credentials
- Digital footprint in social media
- Metadata retention
- Mixing personal and profesional information
Capacities
- Strong passwords or passphrases
- Encrypted communication
- Good practices
- Adoption of technology
- Professional use of social media
Risks
- Extreme
- High
- Moderate
- Low
Reduce vulnerabilities
Increase capacities
Reduce risk
Set up goals
SOURCES
Sharp digital skills
Use strong passwords
Do not re-use passwords
Encrypt devices
Encrypt communications
JOURNALISTS
Lack digital security skills
Use weak passwords
Re-use passwords
Use non-encrypted devices
Use non-encrypted comms
Journalists
Sources
Can you remind me how to use my PGP keys?
Protect
authentication
Create strong passwords
- More than 25 characters
- At least one capital letter
- At least one one number
- At least one one punctuation sign
- Use one password per account
- Do not share your password
Create strong passphrases
- Use the diceware method
- At least six words
- Hands-on:
- Roll the virtual dice (5 virtual dice, six times)
- Find the words
The diceware method




reich
hood
mush
anvil

amigo
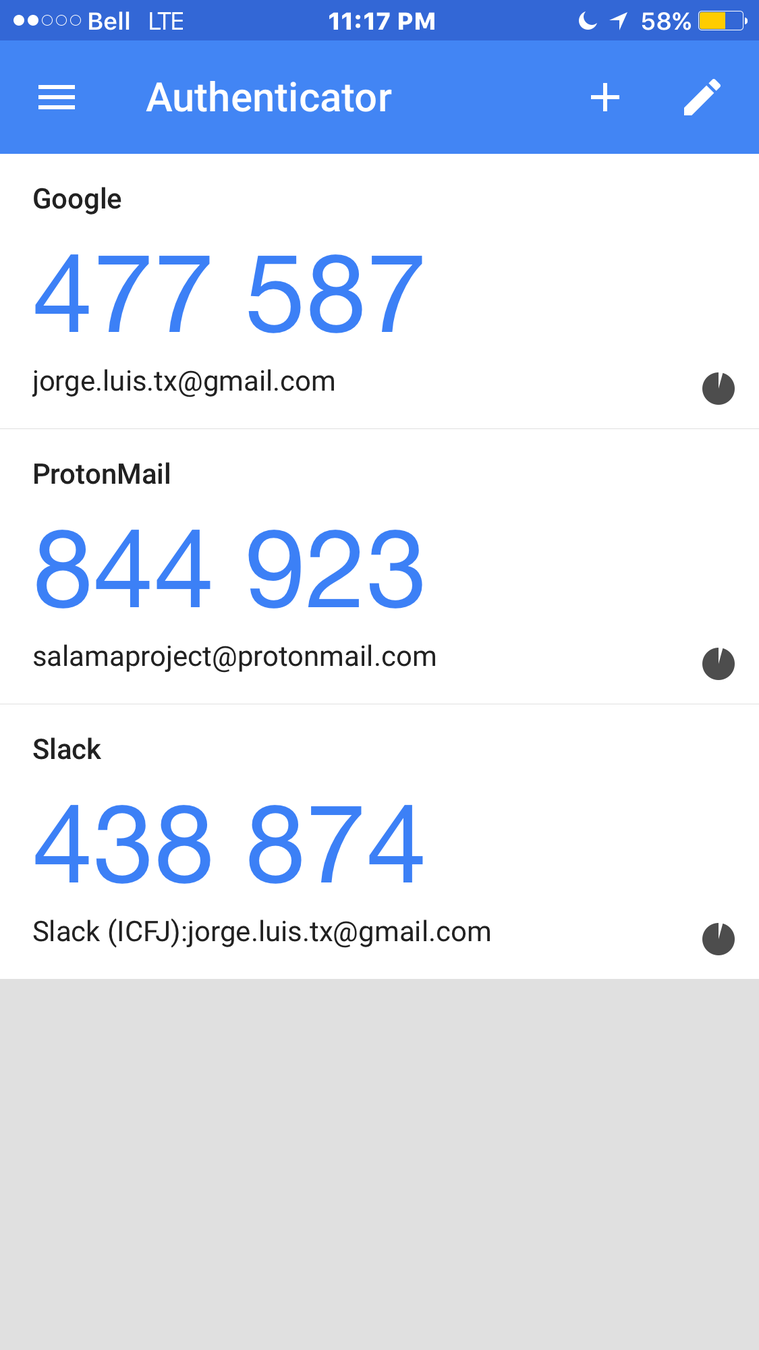
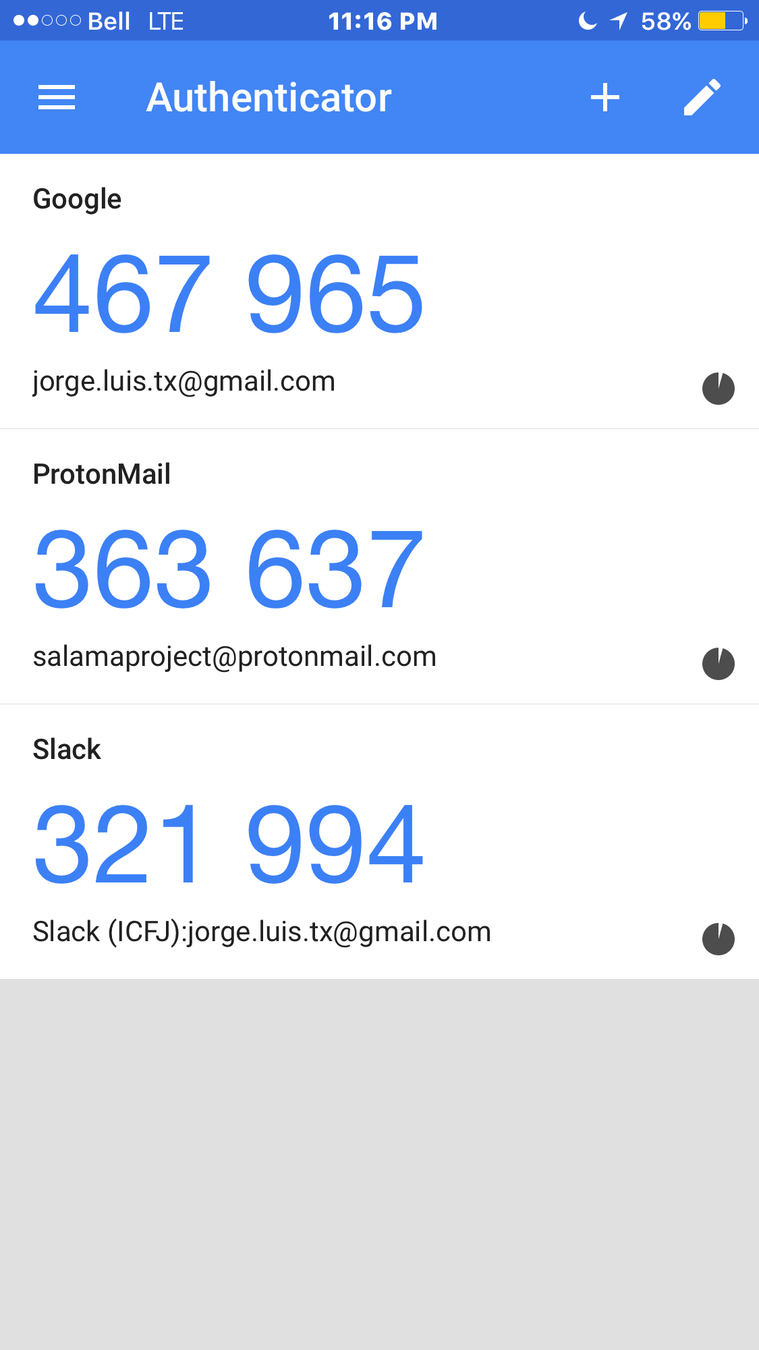
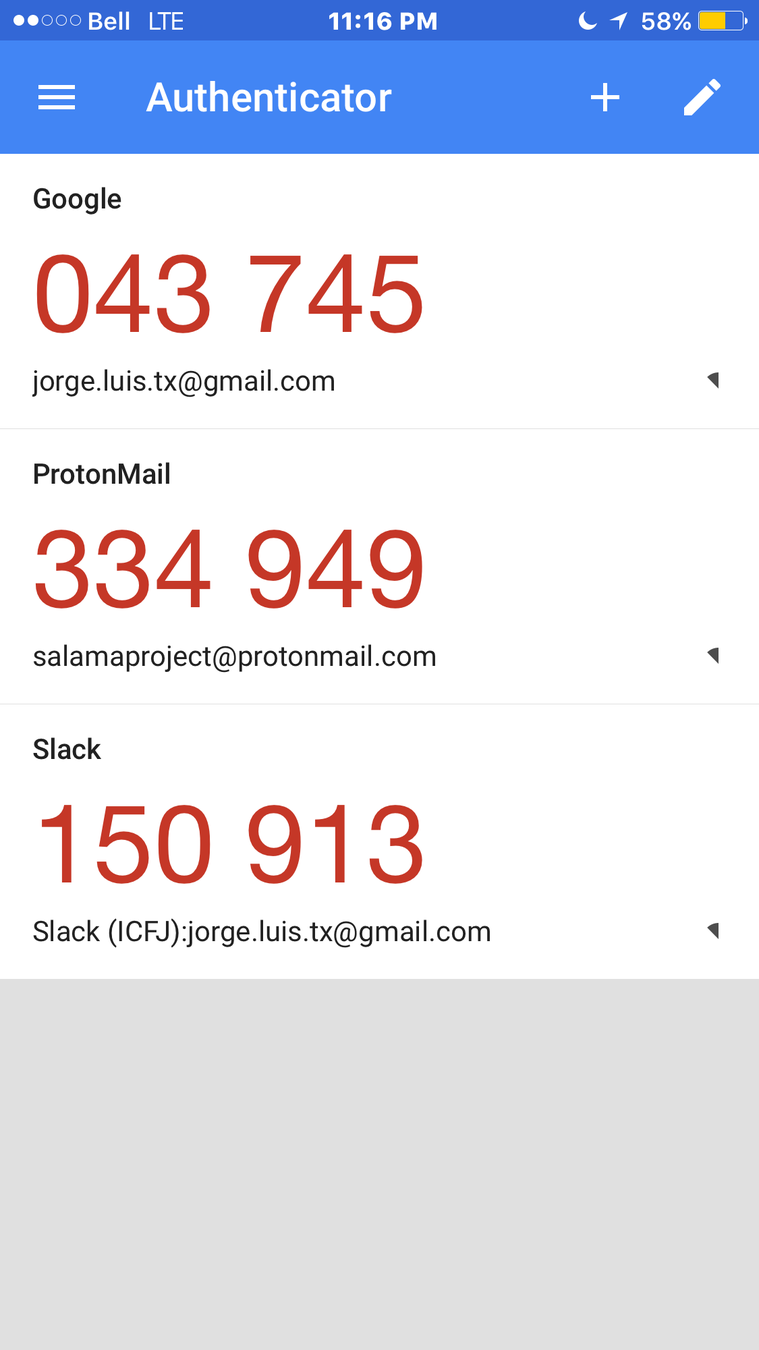
Use 2FA
Data Encryption
Encrypt hard drives
- Filevault for Macs
- Bitlocker for Windows
- Veracrypt for both
Use antivirus
- Avast
- Avira
- AVG
Protect your devices
Use antivirus
Update operating systems
Update all applications
Prevent phishing attacks
Encrypt word documents
Encrypt
communications
Some apps to your toolbox
- WhatsApp
- Signal
- Peerio
- Jitsi
End-to-end encryption
Data storage
Metadata storage
Non encrypted database
Retention of contacts list

Signal
End-to-end encryption
No data storage
No metadata storage
Encrypted database
No retention of contacts list
Disappearing messages
Peerio
End-to-end encryption
Encrypted storage
File destruction
PGP Keys
Ghost messages

Jitsi
End-to-end encryption
Encrypted chat
Encrypted voice
Encrypted video
Password
Encrypt
emails
Create PGP keys
Mailvelope
Mailvelope
- Get the Mailvelope Chrome extension
- Install the extension
- Get your pair of keys
- Use a passphrase!
- Share your public key
- Encrypt emails
- Encrypt files
Jorge Luis Sierra
- @latinointx
- salamaproject@protonmail.com
- Public key
- Key ID: 0AB9B78C
- Fingerprint: 8724 D62C 2DD7 2EDD 5206 C308 4C2B 17E2 0AB9 B78C
Thank you!
Securing data and communications
By Jorge Luis Sierra
Securing data and communications
A mini-toolkit for investigative journalists [and their sources]
- 1,025