How journalists can defend themselves from surveillance?
Jorge Luis Sierra
@latinointx
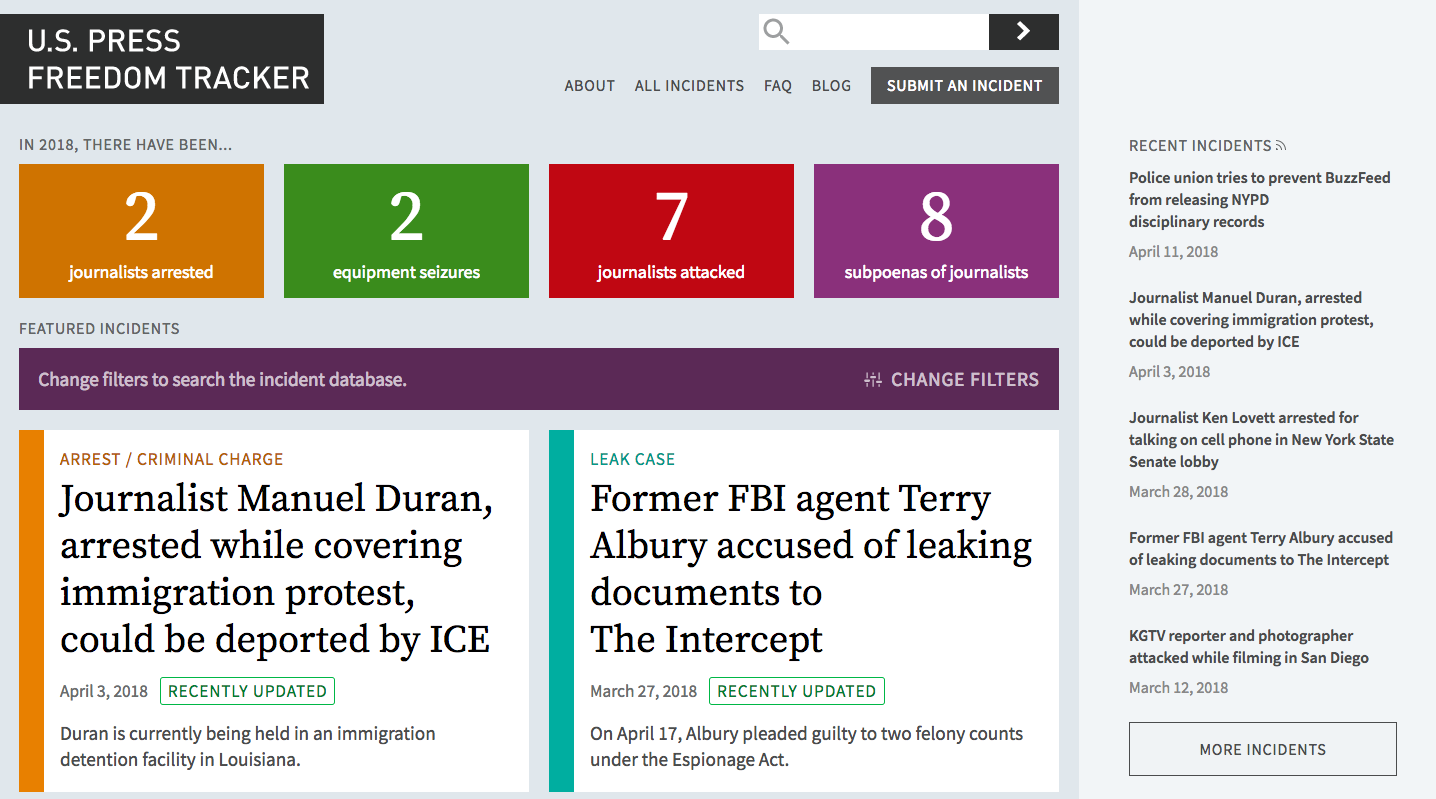
In 2017, the Press Freedom Tracker documented:
· 34 arrests
· 15 equipment seizures
· 44 physical attacks
· 5 border stops
· 5 subpoenas
Targeted surveillance?

Don Bolles, investigative reporter, IRE member, assassinated June 2, 1976, in Phoenix Arizona. Screenshot: IRE.org.
Don Bolles, investigative reporter, IRE member, assassinated June 2, 1976, in Phoenix Arizona. Screenshot: IRE.org.
Javier Valdez Cardenas, investigative reporter, assassinated May 15, 2017, in Culiacán, Sinaloa. Screenshot: Google search.
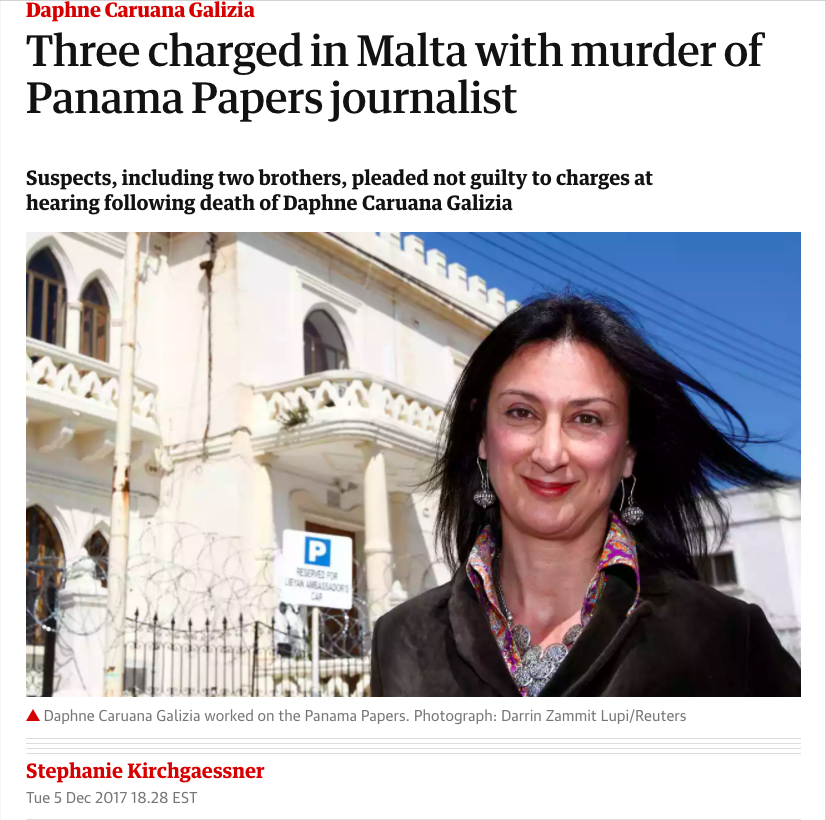
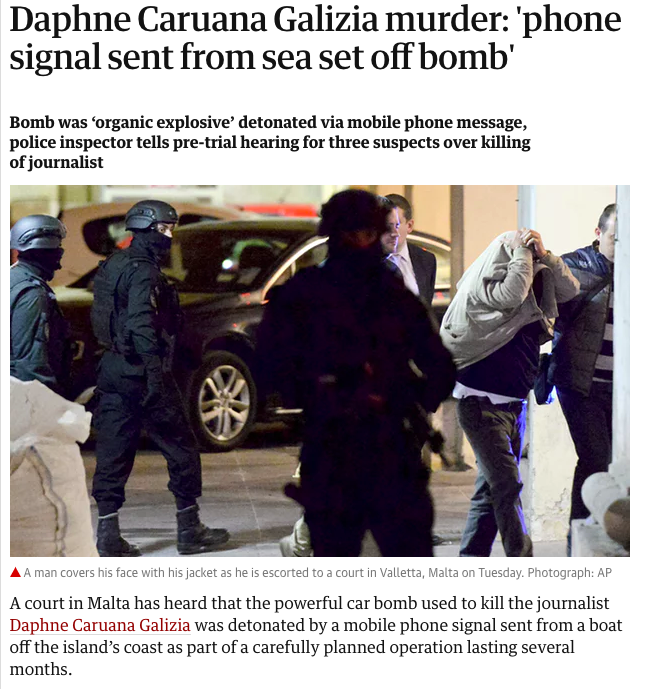
Daphne Caruana Galizia, investigative reporter, ICIJ member, assassinated October 16, 2017. Screenshot: The Guardian website.
Daphne Caruana Galizia, investigative reporter, ICIJ member, assassinated October 16, 2017. Screenshot: The Guardian website.
Daphne Caruana Galizia, investigative reporter, ICIJ member, assassinated October 16, 2017. Screenshot: The Guardian website.
Physical and electronic surveillance are combined
How to reduce risks when we are under physical surveillance?
Text
-
Are there unusual or suspicious vehicles parked near your office or home? -
Are people walking around your house? -
Have you seen the same people more than once? -
Are you being followed by a vehicle? -
Pay attention to groups of two or more males. -
Source: Clandestine Reporters Working Group
Text
-
If you are in a hotel, don’t answer phone calls and don’t allow visits in your room. -
Blend in with others. Try to mirror their clothing, behaviour, speed, eye contact and body language. -
Source: Clandestine Reporters Working Group
Text
-
Be aware of metadata retention. Telecommunications companies are allowed to keep your metadata and geolocation for years. See the case of Malte Splitz in 2009 as an example of the risks posed by metadata retention.. -
Source: Salama Project
Text
Be aware of surveillance devices.
- Stingrays tracking devices: According to the American Civil Liberties Union, this devices mimic cell towers to trick cell phones to transmit their locations and personal identification data. See this ACLU map about who have those devices in the US.
-
Source: ACLU
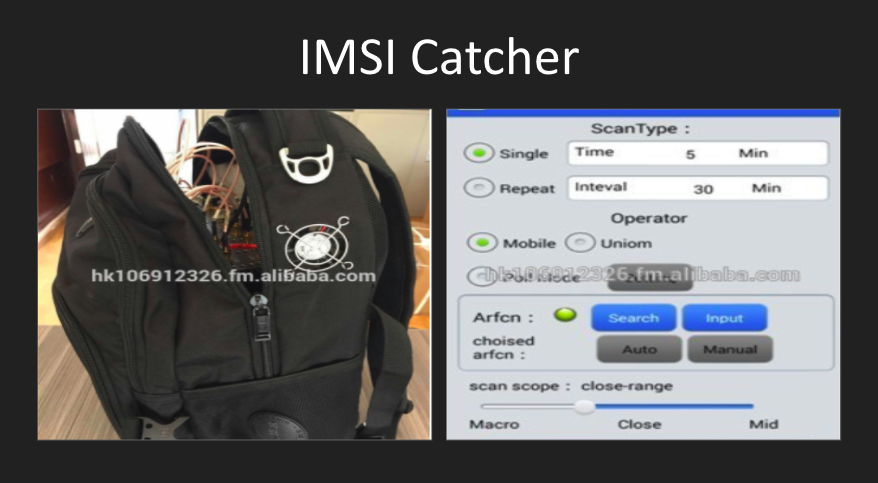
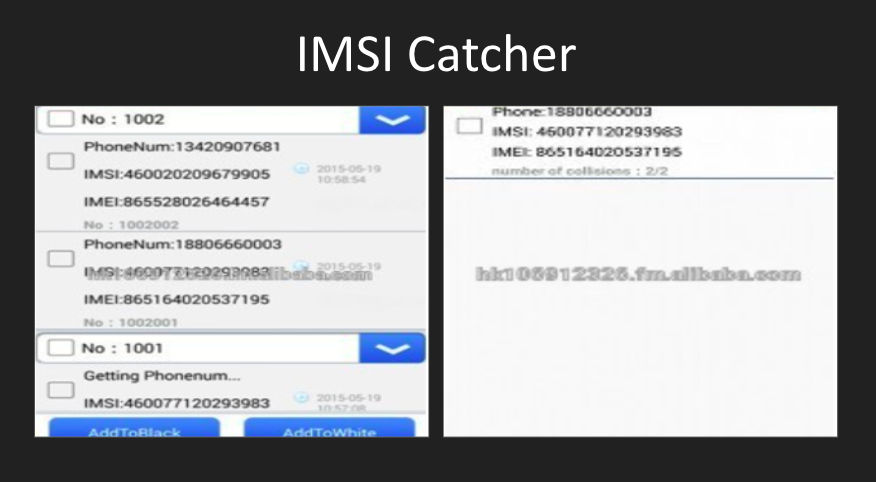
How to reduce risks when we are under electronic surveillance?
Protect your devices
- You should also make sure that every app and all the software used on your devices is kept up-to-date.
Avast
Avira
AVG
Protect your devices
- These two steps are going to be your first line of defense. You can find a more detailed list of information security tools that you can install on your devices here.
Follow good security practices.
The most common way for private companies, abusive governments, and criminal groups to conduct electronic surveillance is to infect devices via spear-phishing.
These are electronic messages that arrive via email, text or instant messaging, inviting the target to open a link or file containing surveillance software. Don’t click on them.
Monitor your devices
Data
Battery perfomance
Device's temperature
Protect your accounts:
- Use the Diceware to create a strong passphrase of six words or more.
Protect your accounts:
- Use the 2-F authentication. It works with a password that you know and an application that you have. Here is a Google tutorial.
- If you are under severe risk, you may use the Google Advance Protection Program, which is basically the use of a passphrase and two physical security keys to access a Google account.
Protect your communications:
Open PGP
Mailvelope
Signal
Meet Jitsi
Thank you
@latinointx
How journalists can d
By Jorge Luis Sierra
How journalists can d
- 468