You found an XSS? Alright! But, what's next?
Kévin (Mizu)

CVSS
The Common Vulnerability Scoring System (CVSS) is a method used to supply a qualitative measure of severity. CVSS is not a measure of risk. CVSS consists of three metric groups: Base, Temporal, and Environmental.
Source: nvd.nist.gov
Vector String
CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H
How to score an XSS?
Average score
Web application only! Would be different for a static website!
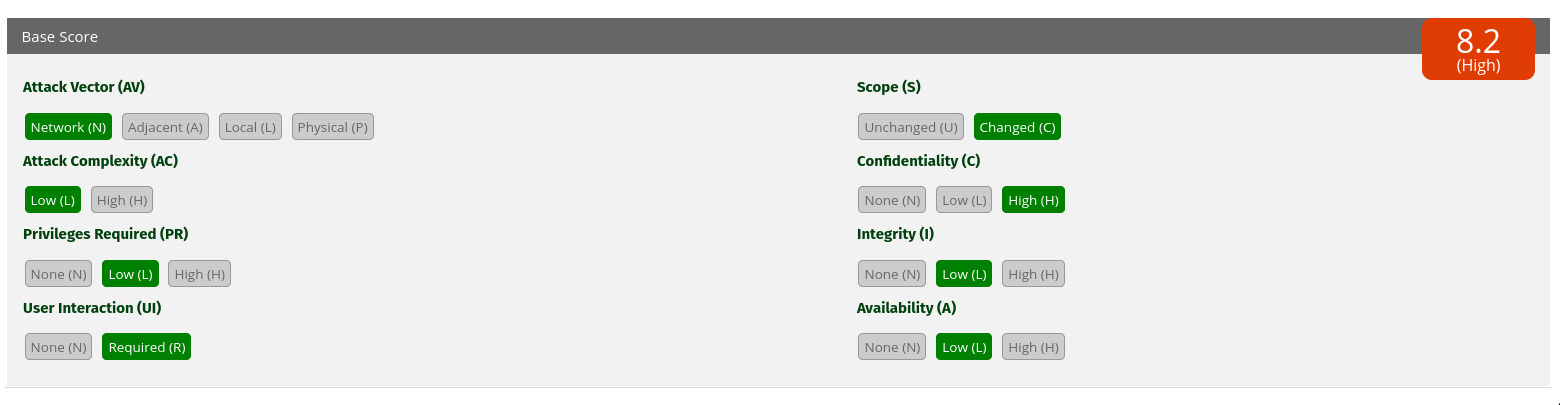
CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:H/I:L/A:L
Attack Complexity (AC)

https://www.first.org/cvss/specification-document#2-1-2-Attack-Complexity-AC
Default: Low (L)
User Interaction (UI)
https://www.first.org/cvss/specification-document#2-1-4-User-Interaction-UI

Victim need at least to click on a link :(
Default: Required (R)
Scope (S)
https://www.first.org/cvss/specification-document#2-2-Scope-S
Default: Change (C)

XSS → vulnerability on the website, but execution in the browser
= scope change :)
Privilege Required (PR)
| Value | Conditions |
|---|---|
| None (N) | :( |
| Low (L) | Victim user need to be authenticated as a normal user |
| High (H) | Victim user need to have admin privileges |
If it impact normal and admin users → Low
Web application only! Would be different for a static website!
Availability
Cookie Bomb → Low (L)
const value = "a".repeat(4080);
document.cookie = "";
for (let i = 0; i < 100; i++) {
let name = "a" + i;
document.cookie = `${name}=${value}; path=/; domain=.example.com`;
}Cookies!!!!






















Cookie scope

scope → mizu.re
https://mizu.re
https://sub.mizu.re
https://sub.mizu.fr
https://sub.sub.mizu.re
Default Cookie flags
| Flag | Value |
|---|---|
| HttpOnly | False |
| Secure | False |
| SameSite | None → 2 minutes Lax * |
* Firefox → None, but will change soon!
Cookie flags | SameSite
| Origin A | Origin B | SameSite? |
|---|---|---|
| https://mizu.re | http://mizu.re | Noo, scheme matter |
| https://sub1.mizu.re | https://sub2.mizu.re | Yes, subdomains don't matter |
| https://mizu.re | https://rhackgondins.com | Noo, different eTLD+1 |
Determining if an URL is considered as SameSite (OWASP)
Cookie flags | SameSite
| Value | Description |
|---|---|
| None | Always send the cookie |
| Lax | GET requests |
| Strict | Never |
Exploit time!
HO=?; SS=? | ?
HttpOnly
SameSite
Contexte
HO=F; SS=* | *

HO=T; SS=* | Basic Gadgets
- Password update
- Mail update → forgot password
- Phone update
- Increase user's privilege
- API Tokens
- Credentials auto-fill abuse
- Log page → PHP info, TRACE...
- ...
HO=*; SS=Lax | PreAuth XSS
Attacker's website
Can also be done using a POST form.

Victim's website
Not Auth
➀ Iframe

HO=*; SS=Lax | PreAuth XSS
Attacker's website
Can also be done using a POST form.

Victim's website

Victim's website
Not Auth
Auth
➀ Iframe
② Open

HO=*; SS=Lax | PreAuth XSS
Attacker's website
Can also be done using a POST form.

Victim's website

Victim's website
Not Auth
Auth
➀ Iframe
③ Exploit
② Open

HO=T; SS=* | OAuth Gadgets
- Frans Rosén : https://labs.detectify.com/2022/07/06/account-hijacking-using-dirty-dancing-in-sign-in-oauth-flows/#gadget-2-xss-on-sandbox-third-party-domain-that-gets-the-url
- @_lauritz_ : https://security.lauritz-holtmann.de/post/xss-ato-gadgets/
HO=T; SS=* | OAuth Gadgets
Authority Server

➀ Ask for bob data token
This is a simplified version of the OAuth implicit flow, check spec for details explanation.

Victim's Server
HO=T; SS=* | OAuth Gadgets

Authority Server

➀ Ask for bob data token
This is a simplified version of the OAuth implicit flow, check spec for details explanation.
② Ask bob's creds

Bob
Victim's Server
HO=T; SS=* | OAuth Gadgets

Authority Server

➀ Ask for bob data token
This is a simplified version of the OAuth implicit flow, check spec for details explanation.
② Ask bob's creds
③ Send them back

Bob
Victim's Server
HO=T; SS=* | OAuth Gadgets

Authority Server

Victim's Server
➀ Ask for bob data token
This is a simplified version of the OAuth implicit flow, check spec for details explanation.
② Ask bob's creds
③ Send them back
④ Data access token

Bob
HO=T; SS=* | OAuth Gadgets

Authority Server

➀ Ask for bob data token
This is a simplified version of the OAuth implicit flow, check spec for details explanation.
② Ask bob's creds
③ Send them back
④ Data access token

⑤ Read bob's data
Bob

Victim's Server
HO=T; SS=* | OAuth Gadgets

Authority Server

➀ Ask for bob data token
This is a simplified version of the OAuth implicit flow, check spec for details explanation.
② Ask bob's creds
③ Send them back
④ Data access token

⑤ Read bob's data
⑥ "
Bob

Victim's Server

Authority Server

➀ Ask for bob data token
This is a simplified version of the OAuth implicit flow, check spec for details explanation.
② Ask bob's creds
③ Send them back
④ Data access token

Steal it here!
⑤ Read bob's data
⑥ "
HO=T; SS=* | OAuth Gadgets
Bob

Victim's Server
HO=*; SS=* | Self XSS + Subdomain XSS


.

Victim's subdomain
Victim's main application
➀ Set cookie for self XSS page
HO=*; SS=* | Self XSS + Subdomain XSS


.

Victim's subdomain
➀ Set cookie for self XSS page

② Trigger self XSS
Victim's main application
HO=*; SS=* | Self XSS + Subdomain XSS


.

Victim's subdomain
Victim's main application
➀ Set cookie for self XSS page

② Trigger self XSS
③ Connected as user on other path
HO=*; SS=Lax | XSS Worm

Bob 1
Hacker
















Poison
Data :p
Data :p
HO=*; SS=* | XSS to RCE

Admin user

Victim's website
➀ Upload plugin
HO=*; SS=* | XSS to RCE

Admin user

Victim's website
➀ Upload plugin

Hacker
② Access plugin
HO=*; SS=* | XSS to RCE

Admin user

Victim's website
➀ Upload plugin

Hacker
② Access plugin
③ RCE
More techniques?
- Relative Path Overwrite (50 pts)
- Self XSS - DOM Secrets (55 pts)
- Self XSS - Race Condition (60 pts)
- Browser - bfcache / disk cache (65 pts)
- Same Origin Method Execution (90 pts)

The end

Rhackgondins team ❤

Leverage XSS criticity - RootMe 2023
By Kévin (Mizu)
Leverage XSS criticity - RootMe 2023
- 377



