Martin Flores
Research Software Developer
iRODS Consortium

Authenticating to iRODS
via OpenID Connect (OIDC)
November 12-17, 2023
Supercomputing 2023
Denver, CO
Overview
- Current State of Authentication in iRODS
- OAuth 2.0 Flows
- Demo Setup & Demo
- Future Considerations

Current State of Authentication

Authentication in iRODS
- Plugins
- Native
- Username & Password
- PAM
- GSI
- Kerberos
- Native
- OAuth in Plugins is awkward to use...

iRODS HTTP API
- Ease of Use in Any Language
- Improved OAuth integration
- Possible support of multiple grant types

Overview of OAuth 2.0 and OpenID Connect

What is OAuth 2.0?
- Enables limited client access to an HTTP service
- At choice of resource owner
- Allows for finer, revocable control of resource owner data
- Avoids sharing password credentials
- Authorization focused

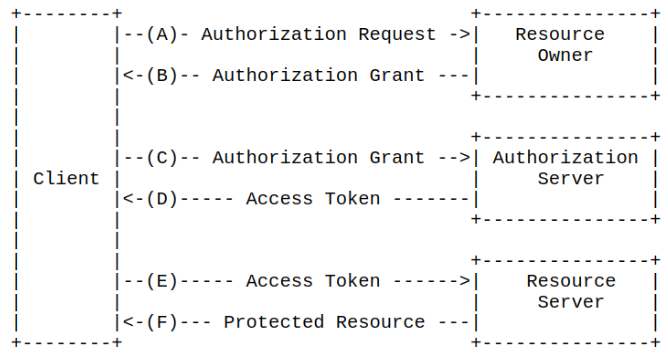
What is OpenID Connect?
- Provides an identity layer
- Enables clients to verify End-User
- Provides basic profile information
- Authentication Focused

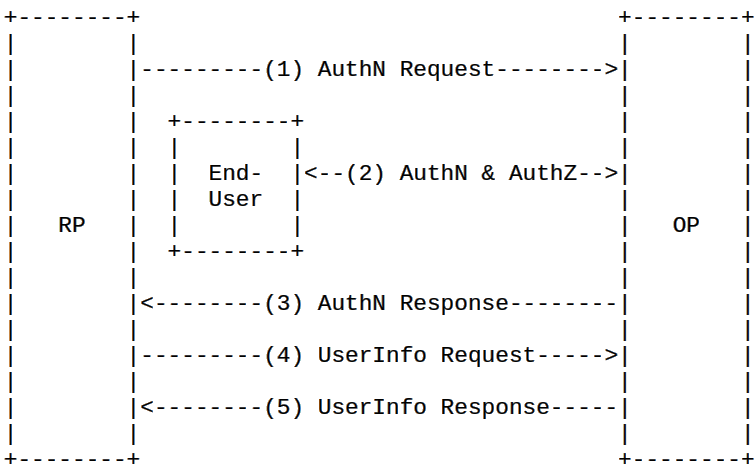
How do they work together?
- OIDC is an identity layer on top of OAuth 2.0
- OIDC
- Authentication
- OAuth
- Authorization

OAuth 2.0 Flows

OAuth 2.0 Grant Flows
- Implicit Grant ***
- Client Credentials Grant
- Authorization Code Grant
- Resource Owner Password Credential Grant ***

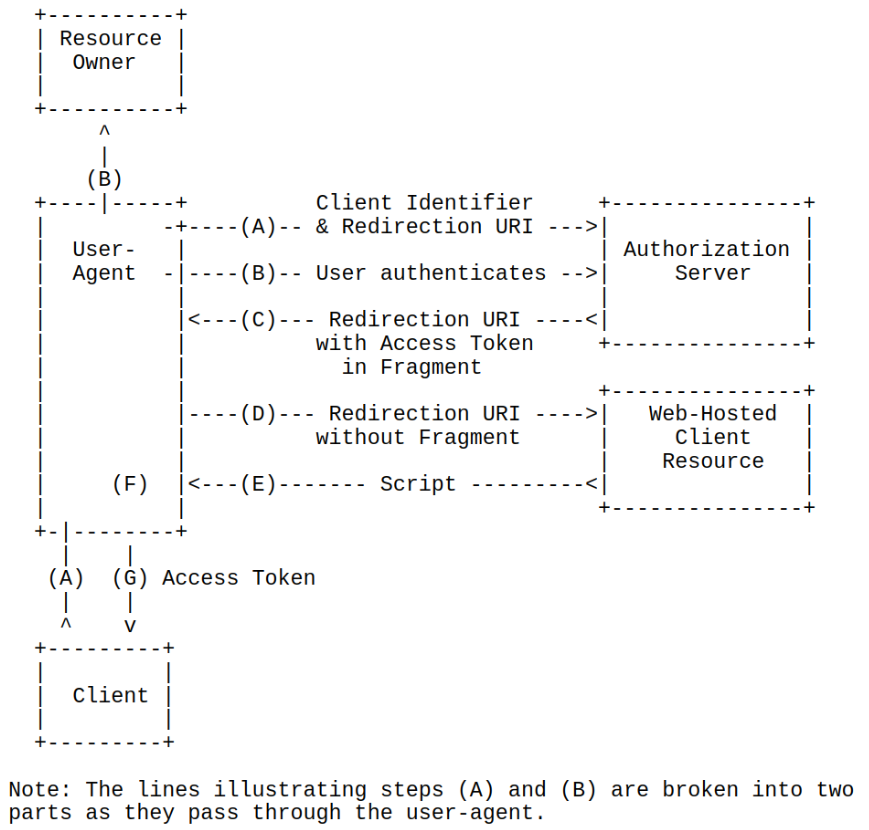
Implicit Grant
- Optimized for Public Clients
- Well-known redirection URI
- Typically implemented in the Browser

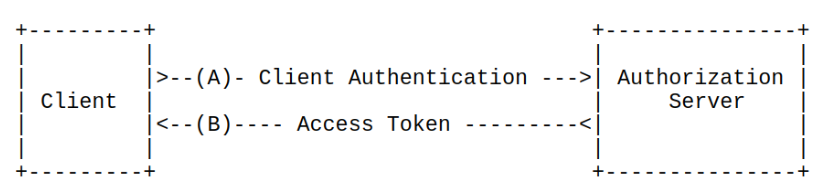
Client Credentials Grant
- Only for use with confidential clients
- Used in prearranged agreements

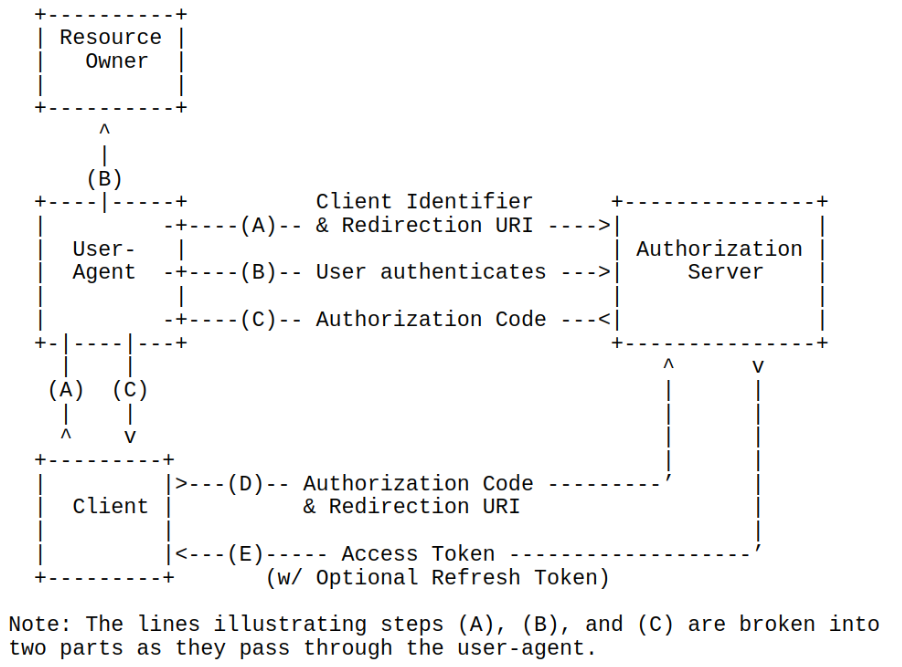
Authorization Code Grant
Of particular use for Confidential Clients

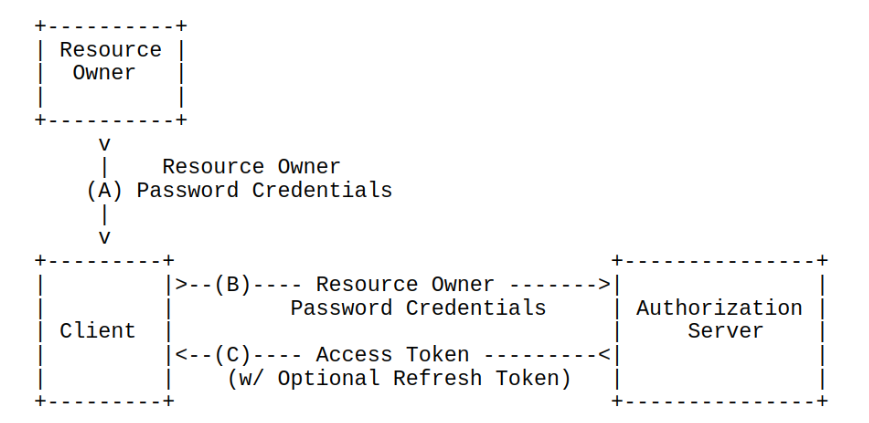
Resource Owner Password Credentials Grant
- Requires high trust between Client & Resource Owner
- Ideally used when alternatives flows are not viable, or migrating authentication schemes

Demo

Demo Setup
- iRODS 4.3.1
- Dockerized HTTP API 0.1.0
- OpenID Provider (OP)
- Keycloak

OpenID Provider Configuration
- Create a new scope
- Add claims to ID token
- Custom attribute
- Mapping to iRODS user (e.g., chuck)

HTTP API Configuration

...
"authentication": {
...
"oidc": {
"config_host": "127.0.0.1",
"port": 8080,
"uri": "/realms/test",
"client_id": "my_client_id",
"redirect_uri": "https://<domain>/irods-http/0.1.0/authenticate",
"state_timeout_in_seconds": 600
},
...
},
...Additional OIDC Configuration
HTTP API OAuth/OIDC Flow

POST /irods-http-api/0.1.0/authenticate HTTP/1.1
Host: ...
User-Agent: ...
Accept: */*
Authorization: iRODS bV9jaHVjazpmZWVsc3NvZ29vZA==POST /realms/test/protocol/openid-connect/token HTTP/1.1
Host: ...
User-Agent: ...
Accept: */*
Content-Length: 85
Content-Type: application/x-www-form-urlencoded
client_id=rods&grant_type=password&scope=openid&username=m_chuck&password=pass{
...
"id_token":"eyJhbGciOiJSUzI1Ni...",
...
}API Consumer Sends Authorization
HTTP API Forwards login to OP
OP Provides 'id_token'
HTTP API OAuth/OIDC Flow

{
"acr": "1",
"at_hash": "uVEs_Qa_PNiwjPI53B_xPw",
"aud": "rods",
"auth_time": 0,
"azp": "rods",
"email": "testmail@testing.test",
"email_verified": true,
"exp": 1685544256,
"family_name": "Mangione",
"given_name": "Chuck",
"iat": 1685543956,
"irods_username": "chuck",
"iss": "http://.../realms/test",
"jti": "b88e1681-b743-4e92-802e-cb7c74fb7739",
"name": "Chuck Mangione",
"preferred_username": "m_chuck",
"session_state": "6102608a-2e18-4d14-9273-344bde4851d2",
"sid": "6102608a-2e18-4d14-9273-344bde4851d2",
"sub": "8c7737cf-65fd-46a5-a54b-6ba45e574692",
"typ": "ID"
}'id_token' claims
Demo Time!

Logging in as [m_chuck] with a password of [feelssogood].
Base64 encoded as [bV9jaHVjazpmZWVsc3NvZ29vZA==].
Running the command [curl -s -X POST -H "Authorization: iRODS $user_and_pass" 127.0.0.1:9000/irods-http-api/0.1.0/authenticate -v].
* Trying 127.0.0.1:9000...
* Connected to 127.0.0.1 (127.0.0.1) port 9000 (#0)
> POST /irods-http-api/0.1.0/authenticate HTTP/1.1
> Host: 127.0.0.1:9000
> User-Agent: curl/8.1.1
> Accept: */*
> Authorization: iRODS bV9jaHVjazpmZWVsc3NvZ29vZA==
>
< HTTP/1.1 200 OK
< Server: Boost.Beast/322
< Content-Type: text/plain
< Content-Length: 36
<
{ [36 bytes data]
* Connection #0 to host 127.0.0.1 left intact
Received the following token: [95d56783-1f0b-4e7b-8ece-598fcb37eea5].Demo Time!

Looking at the collection [/tempZone/home/chuck].
Running the command [curl -s -G -H "authorization: Bearer $token" "127.0.0.1:9000/irods-http-api/0.1.0/collections" --data-urlencode "op=stat" --data-urlencode "lpath=$collection"].
Results:
{
"inheritance_enabled": false,
"irods_response": {
"error_code": 0
},
"modified_at": 1685554932,
"permissions": [
{
"name": "chuck",
"perm": "own",
"type": "rodsuser",
"zone": "tempZone"
}
],
"registered": true,
"type": "collection"
}
Demo Time!

Authorization Code Grant Demo Time!
Challenges
- OAuth 2.0 & OpenID Connect Definitions
- Determining Mapping Method
- Programmatically Determining OIDC Endpoints

Future Considerations

Considerations
- Alternative mapping mechanism for OAuth users to iRODS
- Using 'sub' OIDC attribute
- OAuth Credentials Handling
- Support More OpenID Features
- OpenID Provider Issuer Discovery
- Dynamic Client Registration
- Possible overlap between PAM Interactive auth plugin
- Investigate InCommon

Draft Specifications
- OAuth 2.0 Security Best Practices Draft (Work in Progress)
- Resource Owner Password Credentials MUST NOT be used
- OAuth 2.1 Draft (Work in Progress)
- Resource Owner Password Credentials Omitted
- Removal of Implicit Grant
- Resource Owner Password Credentials Omitted

References
- OAuth 2.0
- OpenID Connect Core
- OpenID Connect Client Discovery
- OAuth 2.1 Draft (Updated r9)
- OAuth 2.0 Security Best Current Practice Draft (Updated r24)

Thank you!

Copy of SC23 - Authenticating to iRODS via OpenID Connect (OIDC)
By Martin Flores Jr
Copy of SC23 - Authenticating to iRODS via OpenID Connect (OIDC)
- 497


