Security Risks

Agenda
- Introduction
- What is a data breach?
- Upcoming legislation
- Options for Protection

What is sensitive data?
- Personal Identifying information
- Credit cards/Bank Accounts
- Credit reporting information
- Credit eligibility information
- SSN/Tax File No

What is a data breach?
- Access by unauthorised users
- Unauthorised disclosure
- Accidental disclosure

Where are the risks?
- Admin staff with elevated access rights
- Unknown sensitive data
- Ex-staff with active accounts
- Unencrypted data
- Unencrypted documents, exports, reports
- Unpatched OS/database
- Default passwords
- Non-supported product versions

Kinds of attack
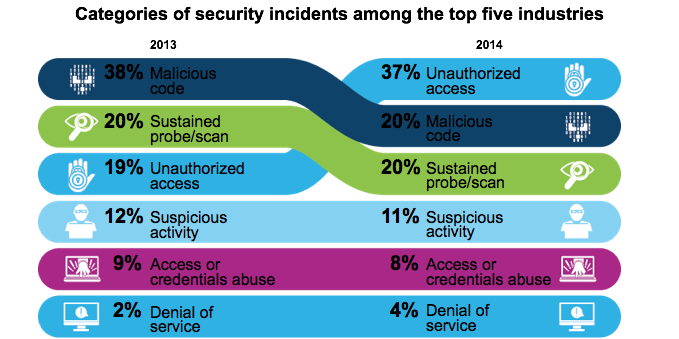
Source: IBM
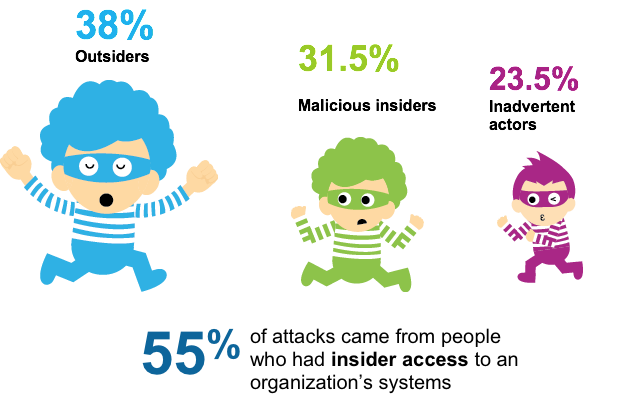
Who are they?
Time to discovery
Intrusion time is short
Detection time is long (weeks/months)
Mandatory Disclosure
- Disclosure is required if you have "reasonable grounds" to believe that a "serious data breach" has occurred.
- Serious = capable of harm (physical/financial/psychological)
- Up to 30 days to investigate
- Affects Federal Agencies, companies >$3M

Pending Legislation
- Existing 2008 Voluntary Privacy guidelines
- Proposed legislation - comments closed (Mar 2016)
- later 2016 before Parliament, will include:
- Mandatory disclosure
- Policy statement
- Response Plan
- Notify AIC (Australian Information Commissioner)
- Notify individual(s)

Protection options
- Do nothing (we're fine)
- Prepare for the worst (Policy & Response Plan)
- Investigate
- Identify critical risks
- Take action to protect
- Repeat regularly

Investigate

- Vulnerability Assessment
- Database identification
- Database access
- Discover sensitive data
- Access rights
- Assessment scorecard
- Vulnerability Reporting
- Recommendations
- Exception management (workflow)
Identify critical risks
- Review report
- Review recommendations
- Identify critical risks
- Create hardening action plan

Harden
- Implement action plan
- Re-run Vulnerability Assessment
- Compare Score card
Monitor
- Database access monitoring
- Configuration Access Monitoring
- File Access Monitoring
- Data Masking
- Alerts
- Workflow (integrate with ticketing system)
- Fully automated
- Reduced compliance costs

References - Upcoming legislation
https://www.oaic.gov.au/agencies-and-organisations/guides/data-breach-notification-a-guide-to-handling-personal-information-security-breaches
http://globalcompliancenews.com/consultation-opens-on-serious-data-breach-notification-bill-20151228/
http://www.claytonutz.com/publications/news/201512/04/serious_data_breach_notification_bill-exposure_draft_released_for_consultation.page
Security Assessment
By Mike King
Security Assessment
- 205



