How to Design IAM
ISDA - 9/7 - Minimum
-
Experiences
-
Cloud Architect (2018+)
-
OOBOX Group (2017+)
-
ISDA (2016+)
-
DevOps Engineer / SRE (2015+)
-
Software Engineer (2011+)
-
-
Abilities
-
Python
-
Container
-
Cloud Services
-
CI / CD / CM
-
Who Am I?
+ Cloud Architect
+ System Architect
+ Database Administrator
+ Backend Engineer
+ DevOps Engineer
+ QA Engineer
+ Project Manager
+ Technical Leader
Current Job
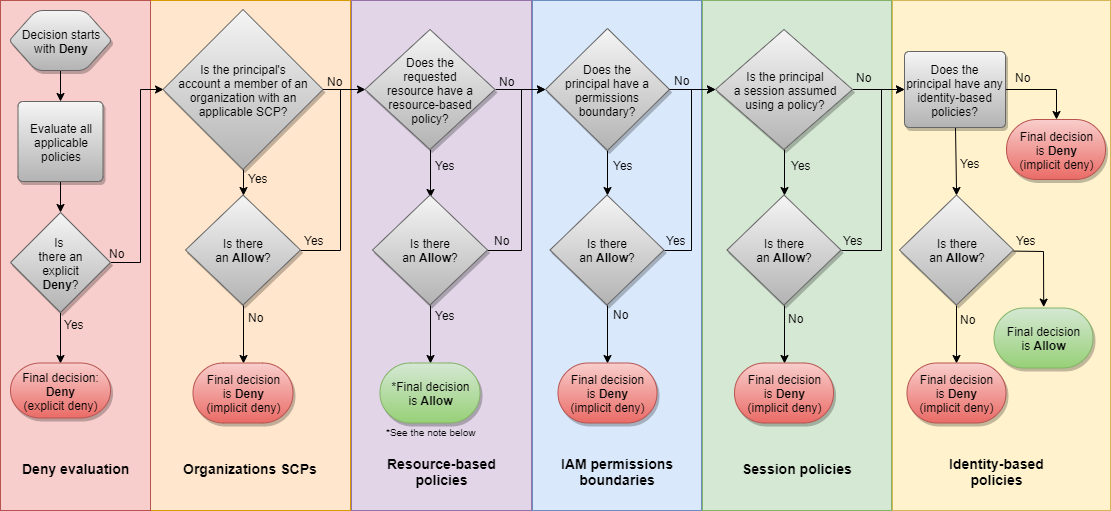
AWS Policy Logic
AWS IAM Policy
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowServices",
"Effect": "Allow",
"Action": [
"s3:*",
"cloudwatch:*",
"ec2:*"
],
"Resource": "*"
},
{
"Sid": "AllowManageOwnPasswordAndAccessKeys",
"Effect": "Allow",
"Action": [
"iam:*AccessKey*",
"iam:ChangePassword",
"iam:GetUser",
"iam:*LoginProfile*"
],
"Resource": ["arn:aws:iam::*:user/${aws:username}"]
}
]
}
AWS S3 Policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListAllMyBuckets",
"s3:GetBucketLocation"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::bucket-name",
"Condition": {
"StringLike": {
"s3:prefix": [
"",
"home/",
"home/${aws:username}/*"
]
}
}
}
]
}
GCP IAM Policy

image from https://cloud.google.com/iam/docs/overview
GCP IAM Role

image from https://cloud.google.com/iam/docs/overview
Too hard!!!
😱
We Just Need
Casbin
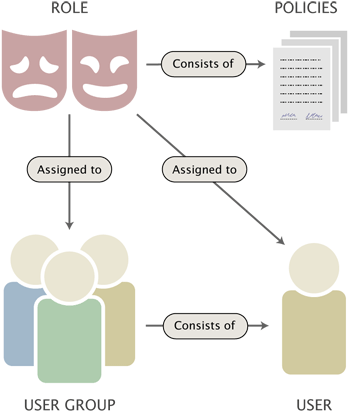
Golang

Role-Based Access Control

Casbin Policy
Subject
Action
Object
Policy Type
Casbin Model
[request_definition]
r = sub, obj, act
[policy_definition]
p = sub, obj, act
[role_definition]
g = _, _
[policy_effect]
e = some(where (p.eft == allow))
[matchers]
m = g(r.sub, p.sub) && r.obj == p.obj && r.act == p.act
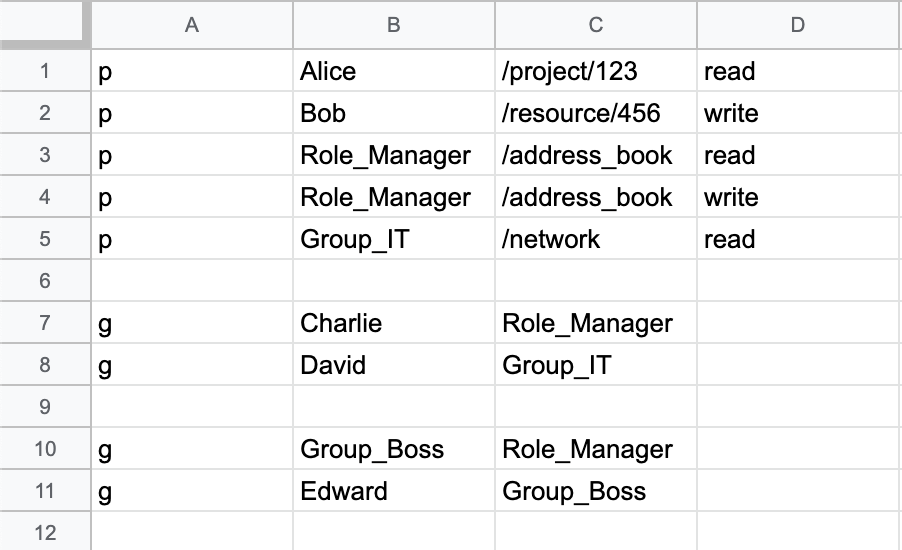
PyCasbin Example
import casbin
# New an enforcer instance
e = casbin.Enforcer(
model='/path/to/rbac_model.conf',
adapter='/path/to/rbac_policy.csv'
)
# decides whether a "subject" can access a "object" with the operation "action"
assert True == e.enforce('Alice', '/project/123', 'read')
assert True == e.enforce('Bob', '/resource/456', 'write')
assert True == e.enforce('Charlie', '/address_book', 'read')
assert False == e.enforce('David', '/project/123', 'read')
Casbin Server

API
Casbin
DB
1. request
2. valid permission
3. allow / deny
4. query
5. result
6. response
IAM
By Jung-Lun Hsu
IAM
RBAC
- 707



