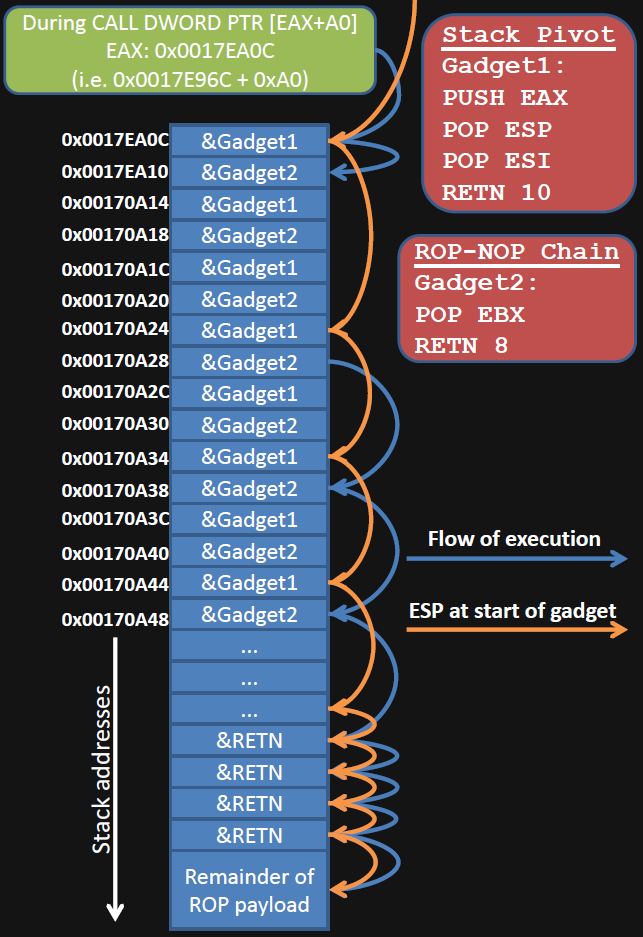
All about ROP Chain
What is ROP?
- Return Oriented Programming
- Allows us to call other functions through buffer overflows
What is ROP Chain?
- Bunching together multiple snippets of assembly code to perform desired behavior
- Usually called chaining
- Snippets often called gadgets, generally used for setting parameters to functions
Return to Libc
- Extremely common ROP Chain
- Takes advantage of GOT to call function from libc
- Click here to learn about GOT
- ASLR does not randomize GOT entries (but PIE does).
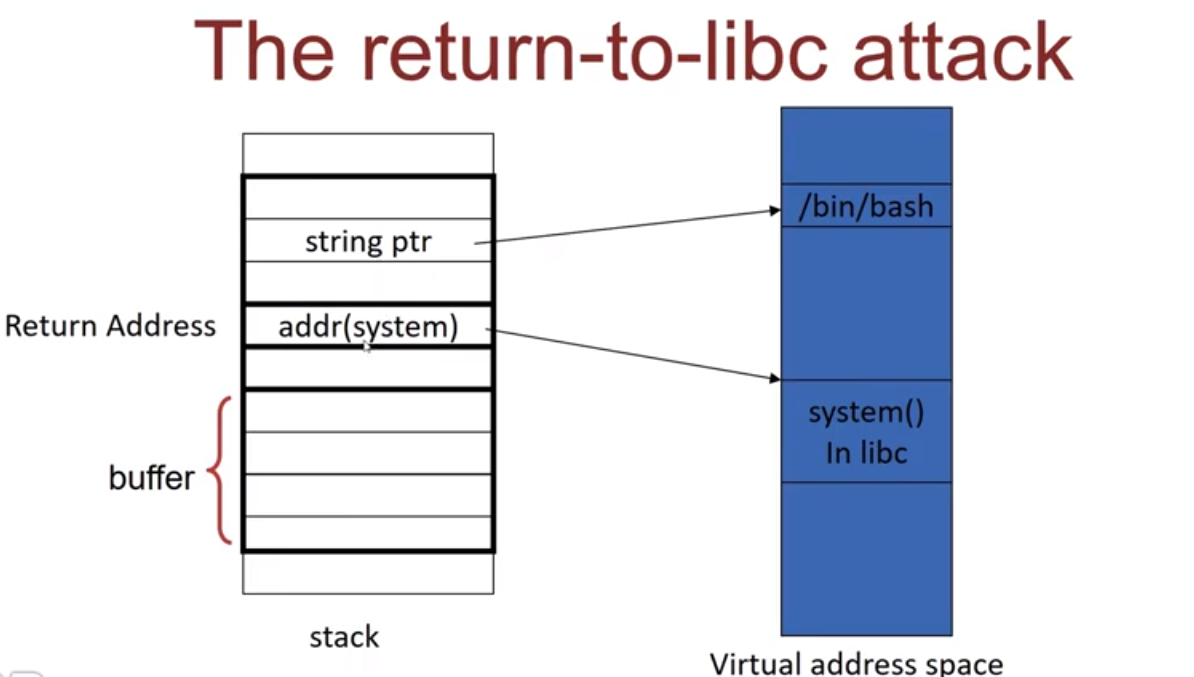
End Result: We can call functions to get a shell or read from memory/disk!
What to Look For?
We'll be working with return-to-what from downunderctf - Download PWNTOOLS
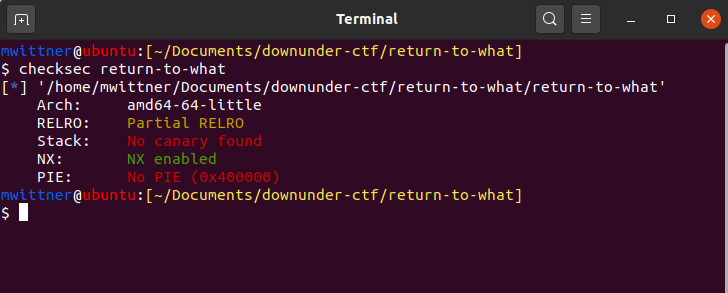
Clear indication that ROP of some kind works
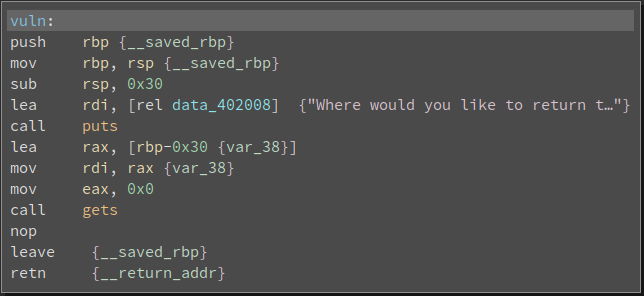
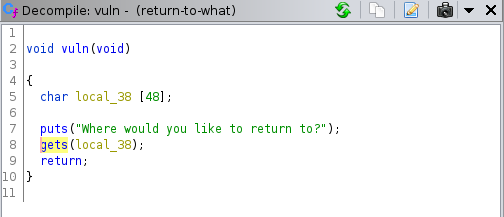
Further Analysis
We'll be working with return-to-what from downunderctf - Download PWNTOOLS
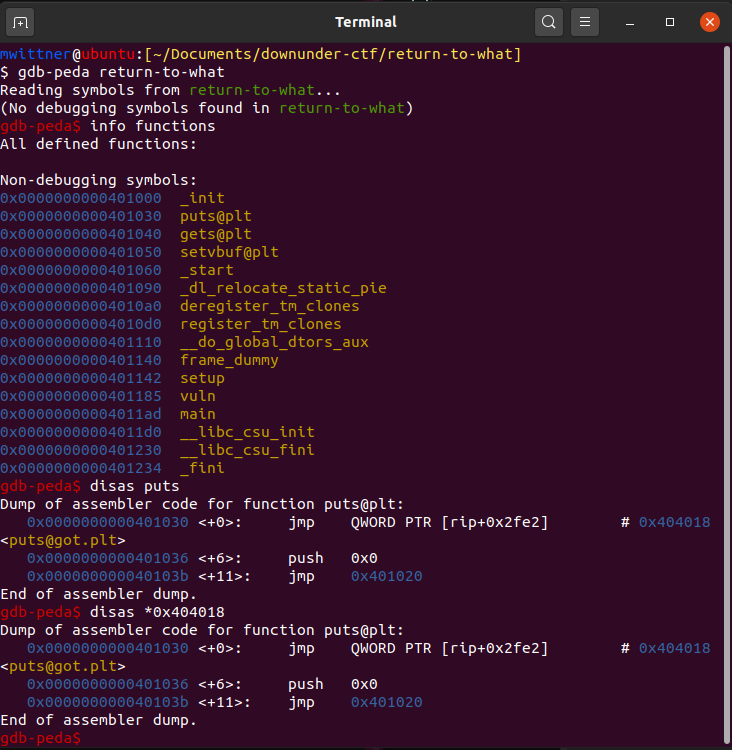
Exploit Concept
We'll be working with return-to-what from downunderctf - Download PWNTOOLS
- Overwrite up until RET
- Leak the address of PUTS through the GOT Table
- Given the offset of system, calculate where system is in LIBC
- Find where bin/sh is in libc
- Construct ROP attack
- Returning to System, with param "/bin/sh"
- Jump to vuln and execute buffer overflow with ROP attack.
Finally...Exploiting!
We'll be working with return-to-what from downunderctf - Download PWNTOOLS
- Overwrite up until RET
- Leak the address of PUTS through the GOT Table
- Given the offset of system, calculate where system is in LIBC
- Find where bin/sh is in libc
- Construct ROP attack
- Returning to System, with param "/bin/sh"
- Jump to vuln and execute buffer overflow with ROP attack.
Finally...Exploiting!
We'll be working with return-to-what from downunderctf - Download PWNTOOLS
pwn template --host=<enter address> --port=<port> return-to-what > return-to-what.pyROP ROP ROPPITY
By Ragnar Security
ROP ROP ROPPITY
All about rop chain exploits.
- 371



