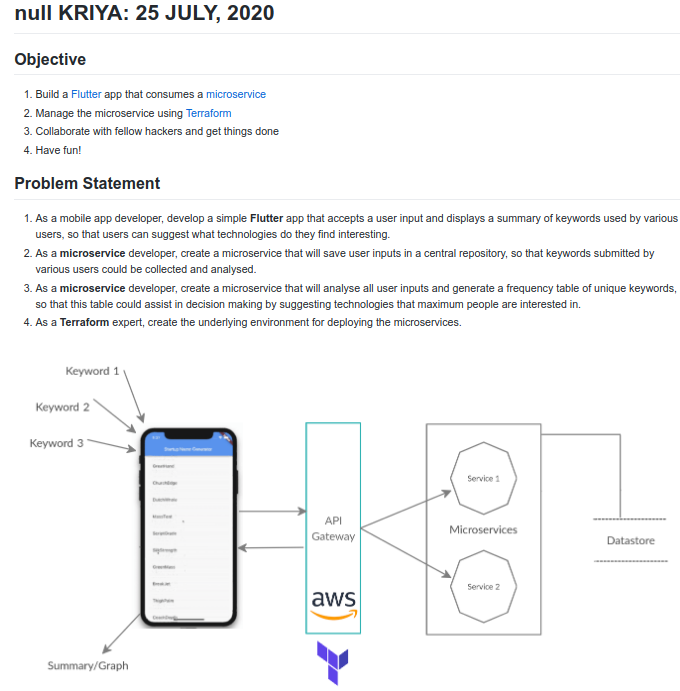
Build. Break. Learn.
Riddhi Shree
A beginner with 10+ years of Software Industry experience





I Take Pride In
Work I've done in my free time!
Enjoyed giving talks, workshops, training, tool demo at conferences
- Hack-In-The-Box (HITB), Abu Dhabi
- Nullcon, Goa
- c0c0n, Kochi
- BSides, Delhi
- ISC2, Bangalore
I Believe In
Dreaming big. Breaking rules. Creating awareness.


We're here for?
- Injection Attacks
- Cross-Site Scripting (XSS)
- XML External Entities (XXE)
- Broken Authentication & Authorization
- Insecure Deserialization
- Sensitive Data Exposure
- Security Misconfigurations
Let's get started..
Injection Attacks
- 1st Order SQL Injection
- 2nd Order SQL Injection
- OS Command Injection
- Template Injection
- CRLF Injection

Why does it work?
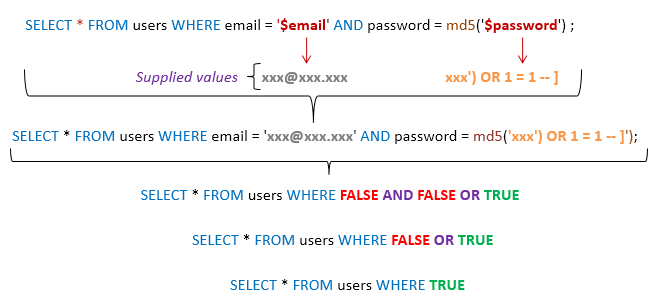
SQL Injection
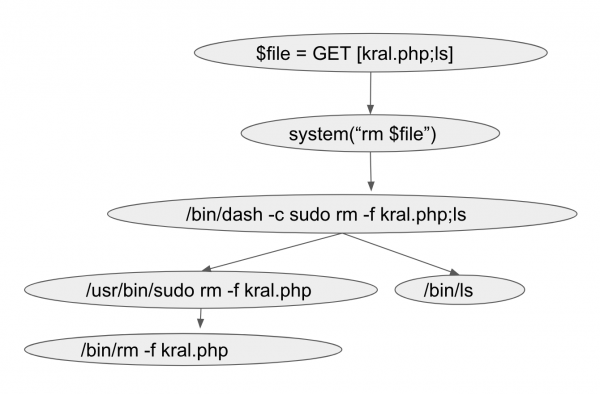
OS Command Injection
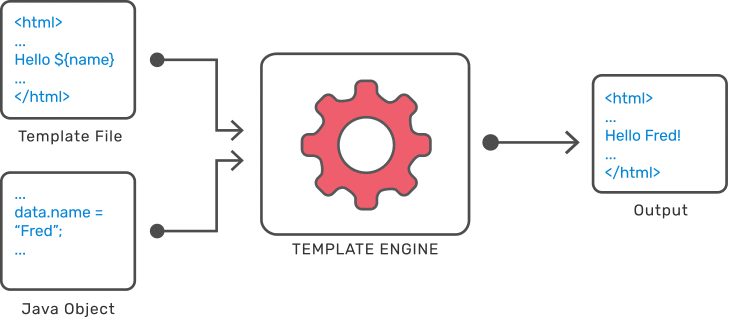
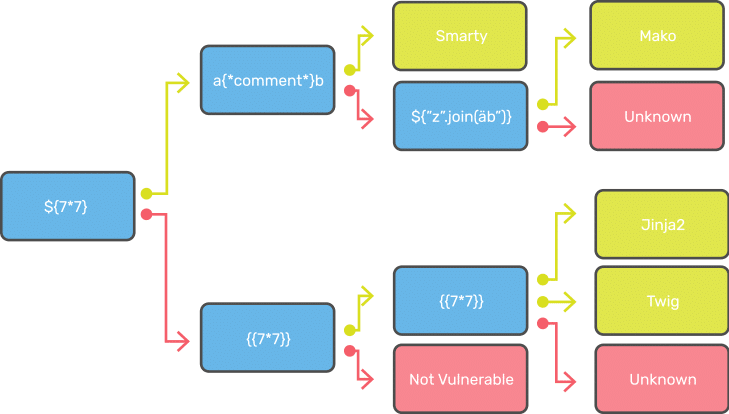
Template Injection
Template Injection
CRLF Injection
How to Protect?
- Proper usage of parameterised queries
- Server-side input validation
- Proper error handling
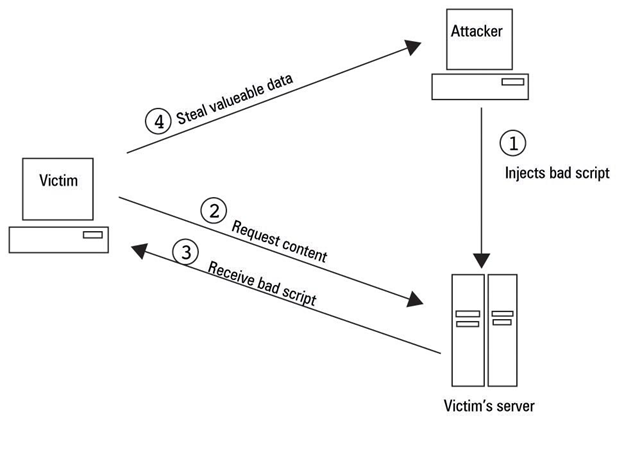
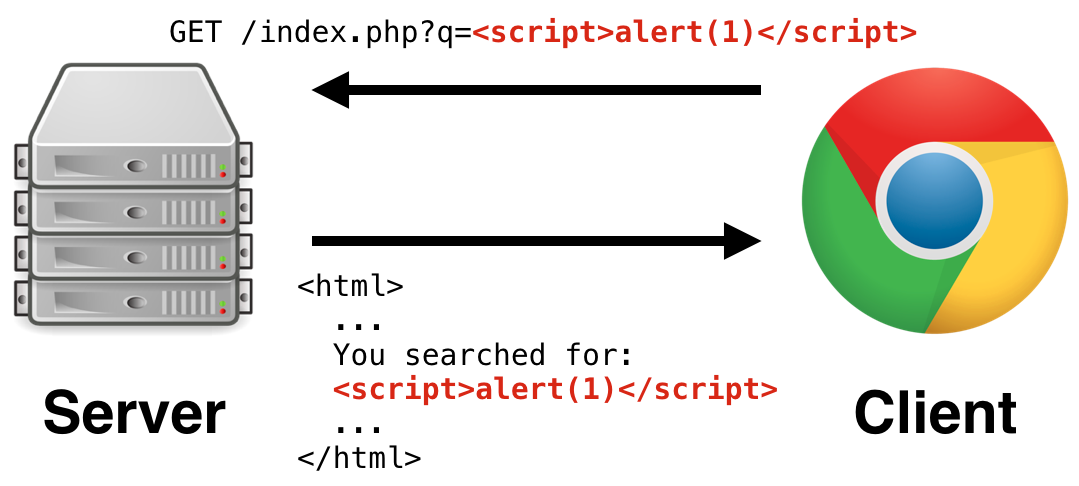
Cross Site Scripting (XSS)
- Reflected XSS
- Stored XSS
- DOM-based XSS

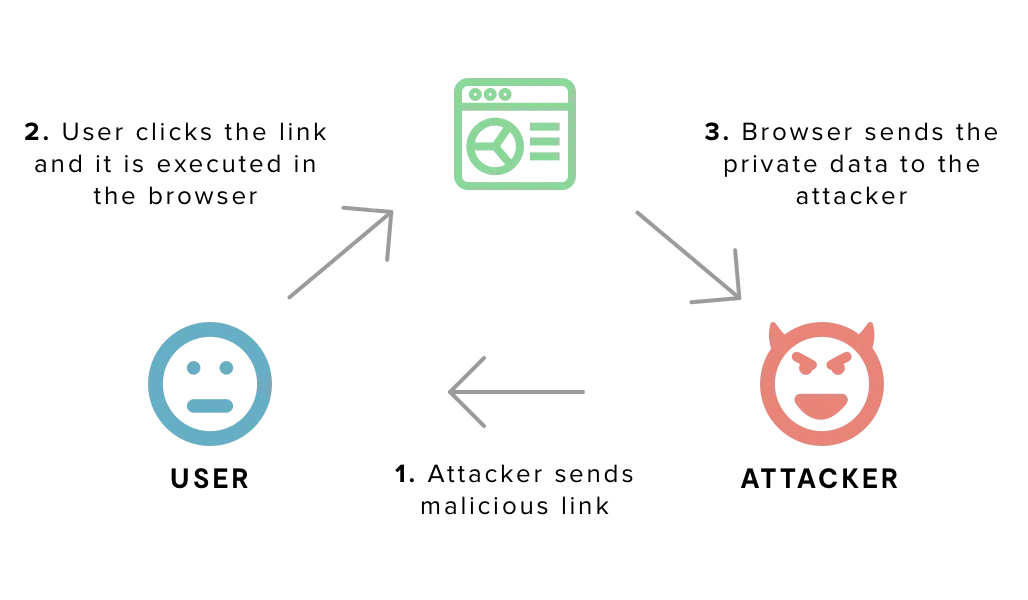
Reflected XSS
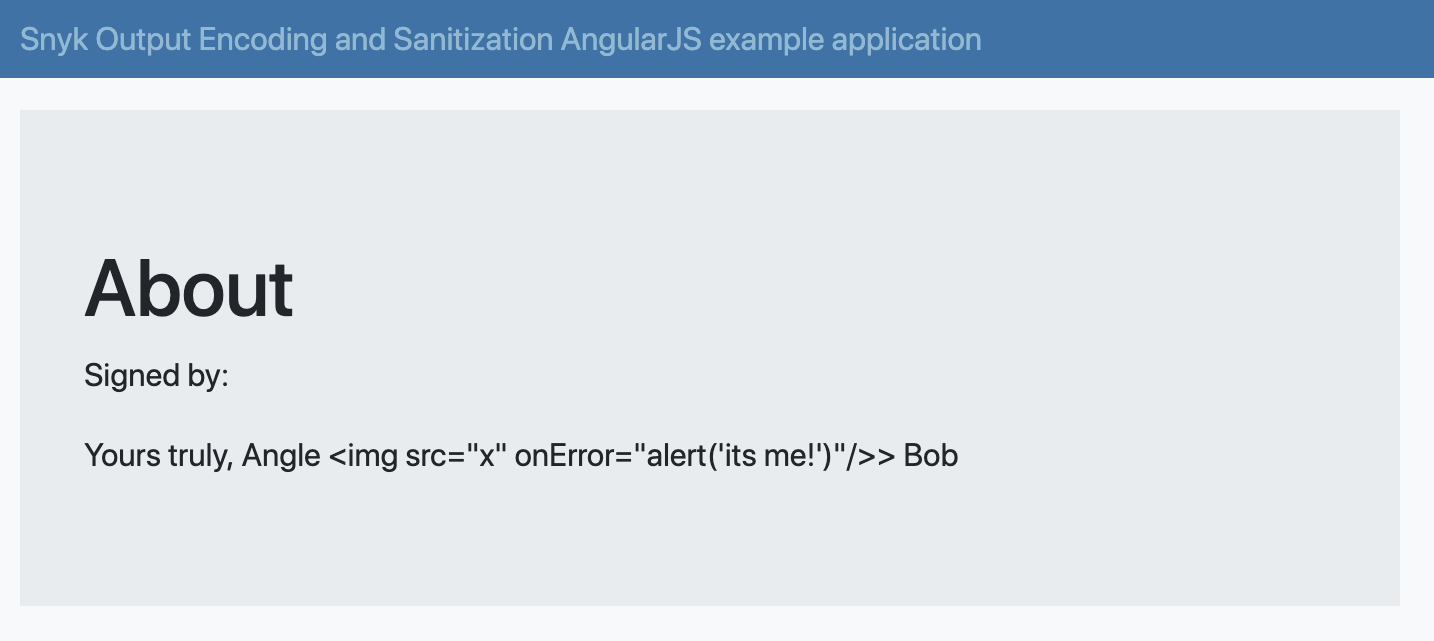
Stored XSS
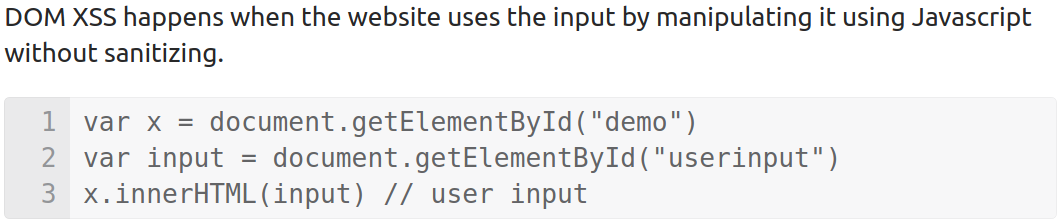
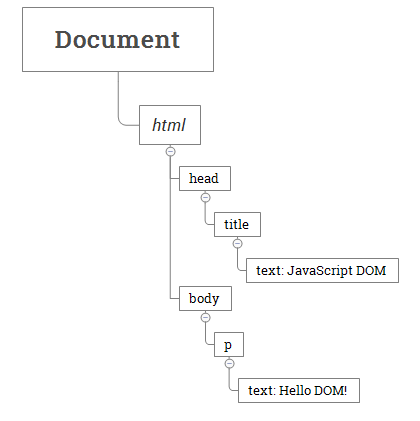
DOM Based XSS
How to protect?
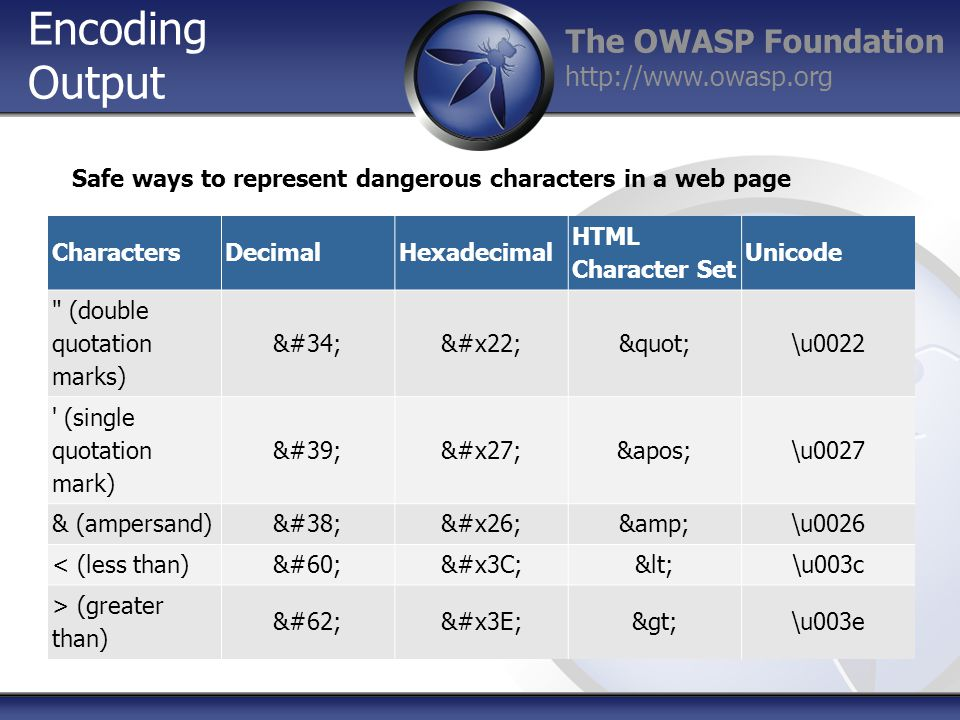
- Contextual output encoding
https://cheatsheetseries.owasp.org/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet.html
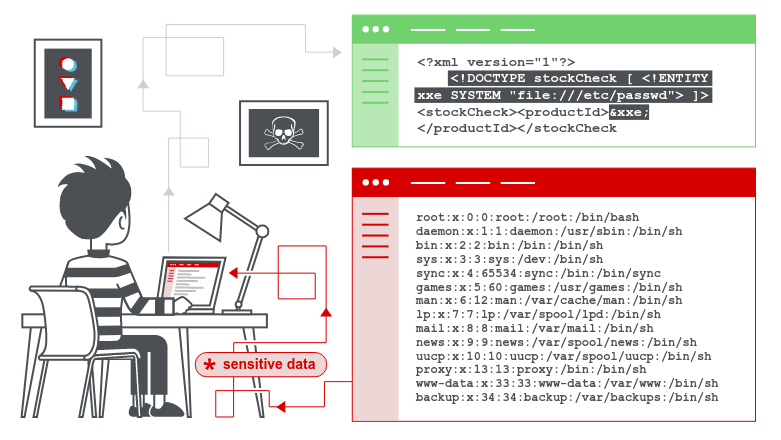
XML Eternal Entities (XXE)
-
File Inclusion
-
Server-Side Request Forgery (SSRF)
-
Data Exfiltration
-
Remote Code Execution (RCE)

Broken Authn and Authz
-
JWT Validation Bypass
-
OAuth 2.0 Security Misconfigurations
-
Session Fixation via HTTP Header Injection
-
Cross-Site Request Forgery (CSRF)
-
Insecure Direct Object Reference (IDOR)
-
Parameter Tampering

JWT Validation Bypass
- Brute-force JWT Secret
- The None Algorithm
- RS256 to HS256
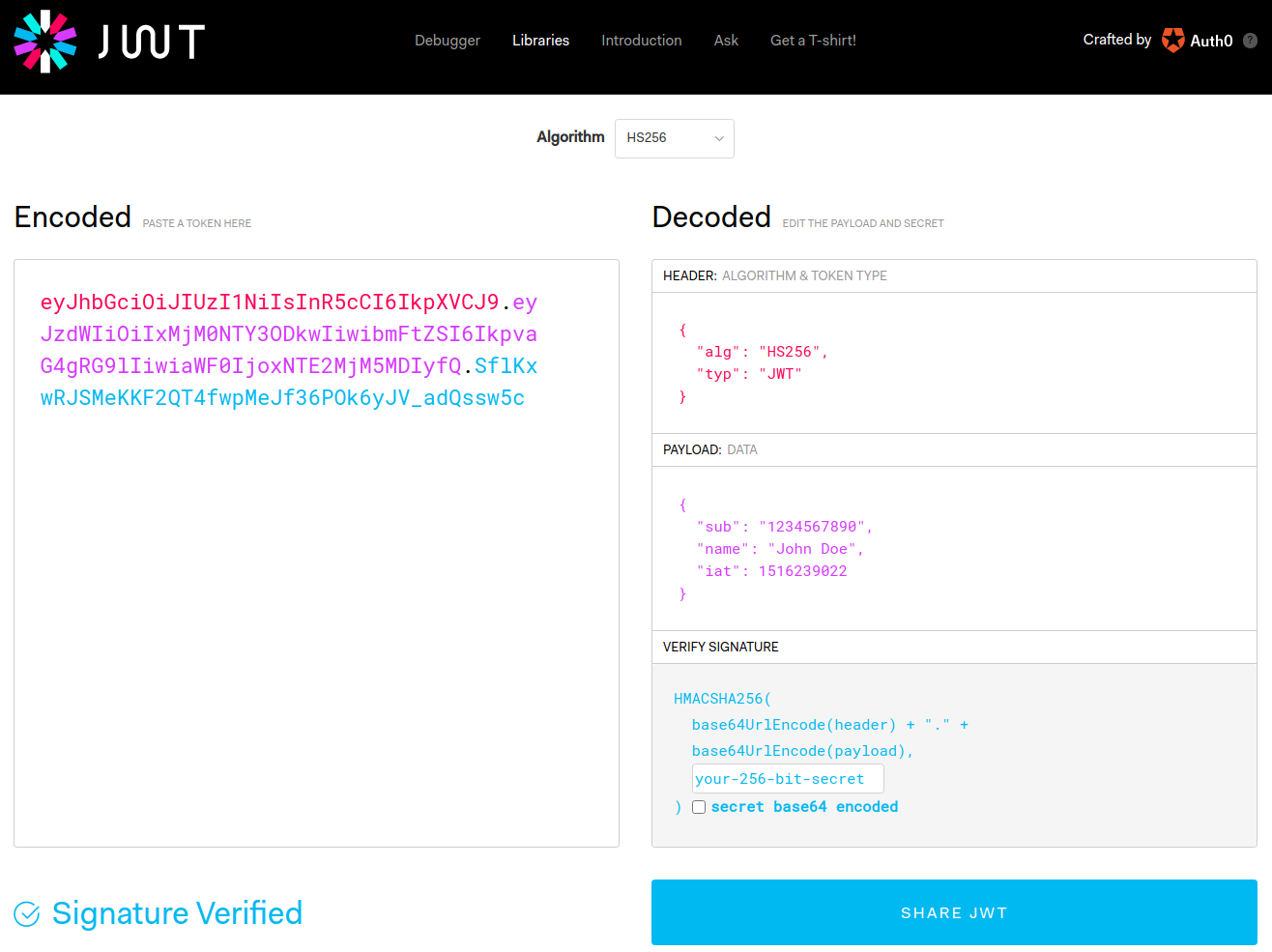
https://jwt.io/
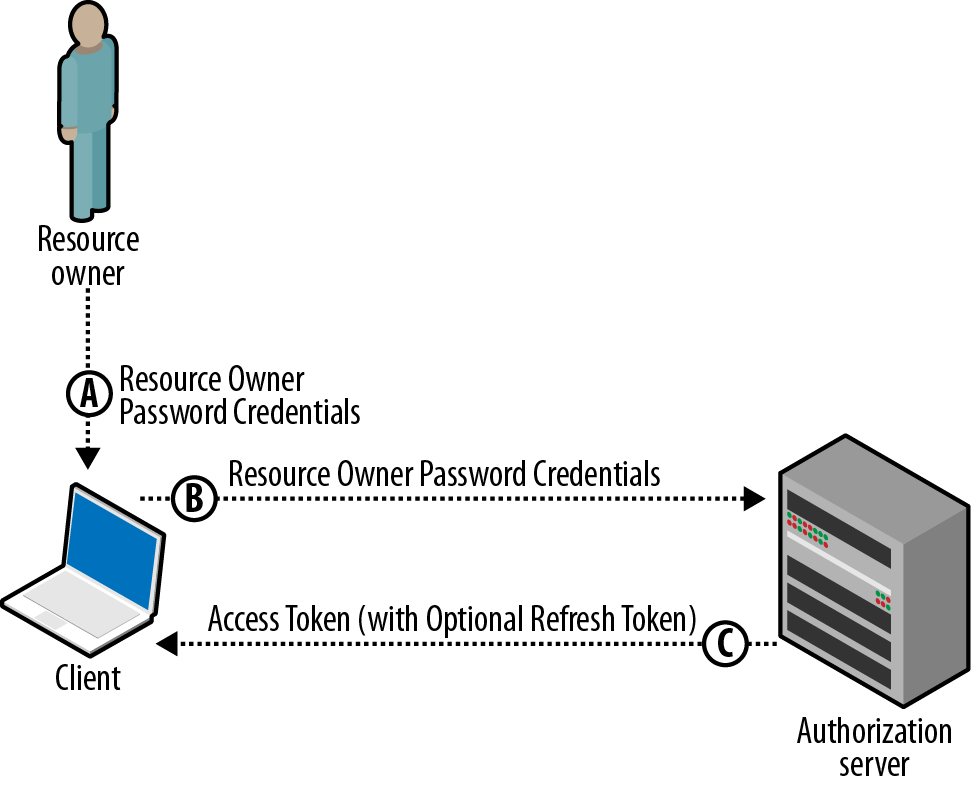
OAUTH 2.0 Authorization
- https://tools.ietf.org/html/rfc6749
Typical Client-Server Model
- Client authentication involves resource owner's credentials, i.e., resource owner's credentials are shared with third-party clients
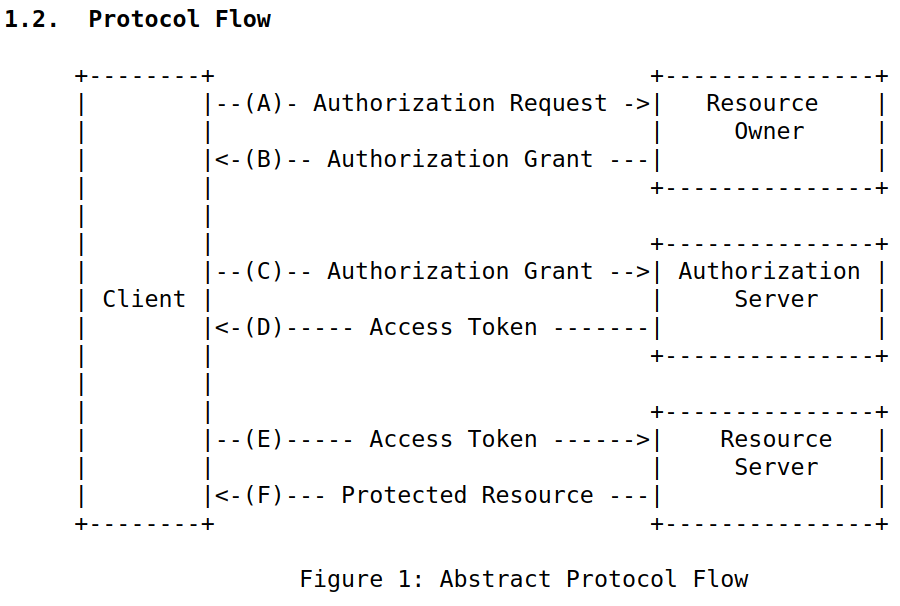
OAUTH 2.0 Security Considerations
- Unauthenticated Clients
- Client Impersonation
- Insecure Transmission of Access/Refresh Tokens
- Access/Refresh Token Expiry
- Open Redirection
- Failure to Detect Authorization Code Compromise
- Access Token's (Broad) Scope
- Sensitive Plaitext Information in "state" and "scope"
- Missing CSRF protection for redirection URI (via "state" parameter)
- Injection via "state" and "redirect_uri" parameters
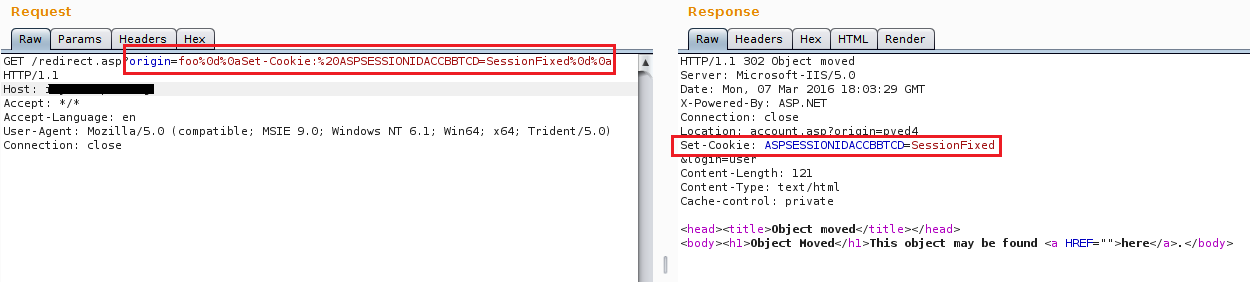
Session Fixation via HTTP
- https://unsecured.nwebsec.com/SessionFixationAttacker
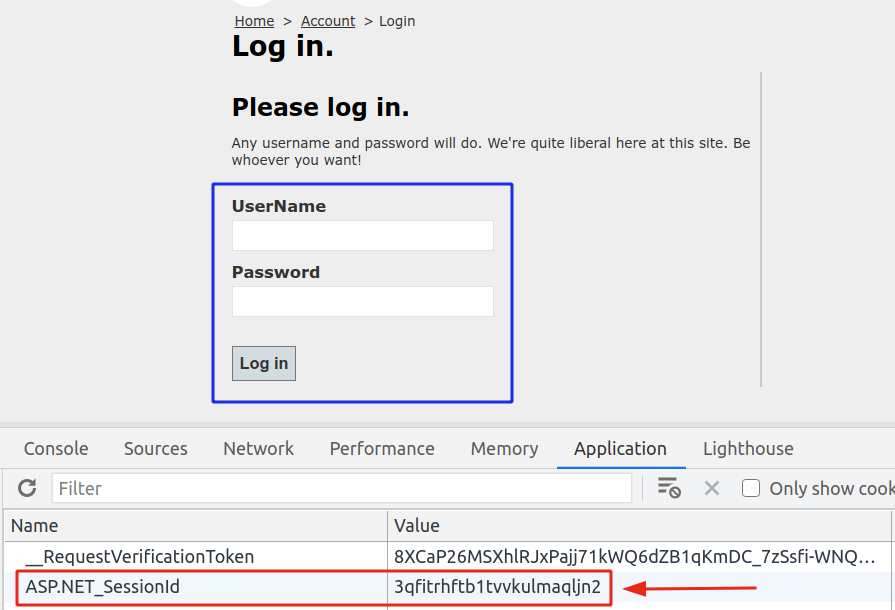
Cross-Site Request Forgery (CSRF)
Insecure Direct Object Reference (IDOR)
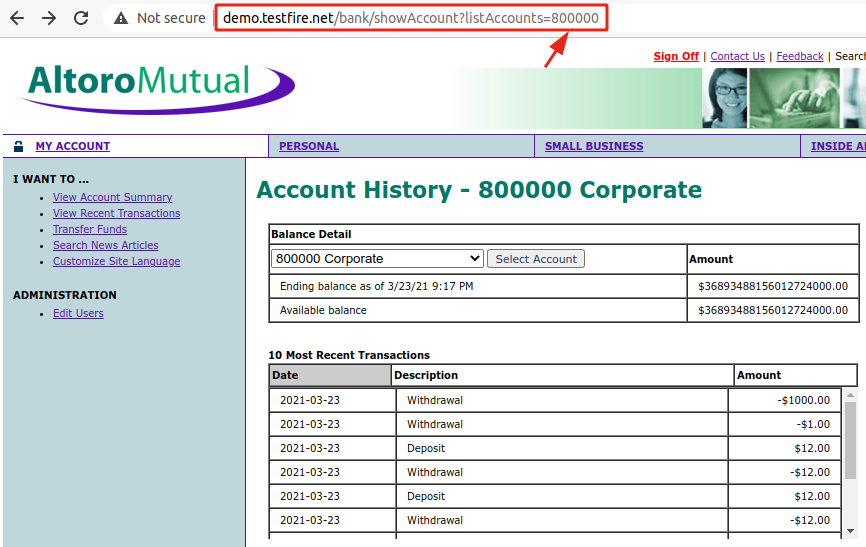
Parameter Tampering
- We have been doing this all along, through all our demos.
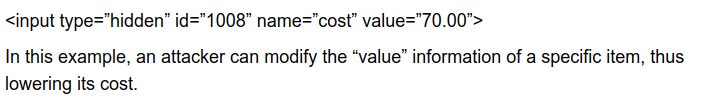
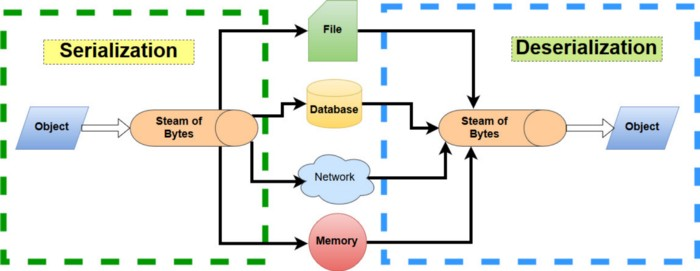
Insecure Deserialization
Of Untrusted User Input

Sensitive Data Exposure
-
Missing/Broken Cryptography
-
Hardcoded Secrets in JavaScript Files
-
Verbose Error Messages
-
Verbose Server Responses

Insufficient Cryptography
- Poor key management
- Use of custom encryption protocols
- Use of insecure algorithms
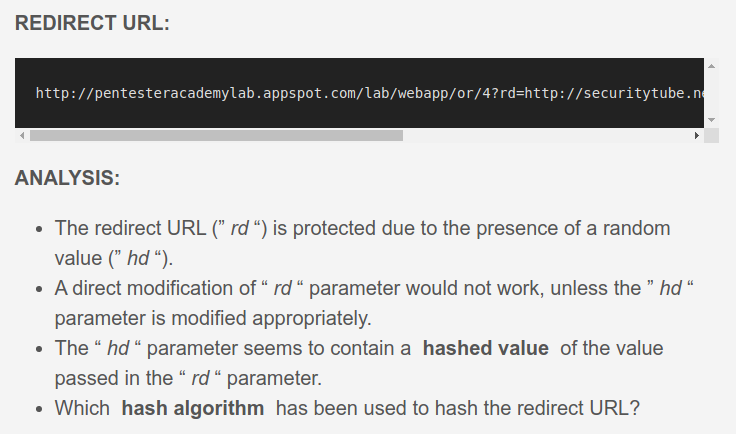
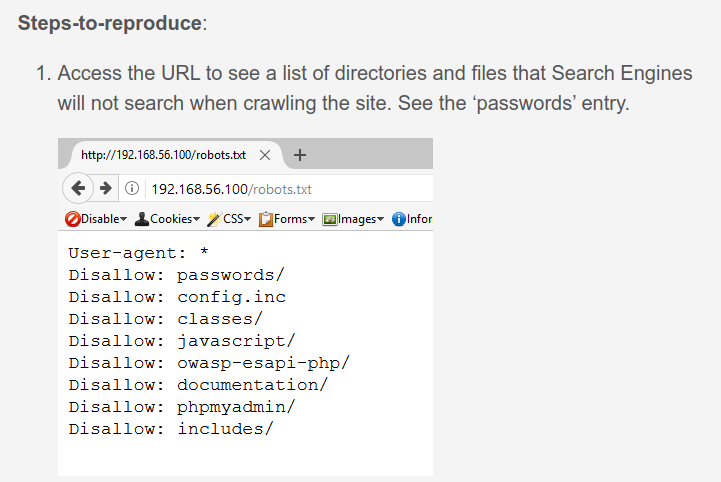
Security Misconfigurations
-
Missing Security Headers
-
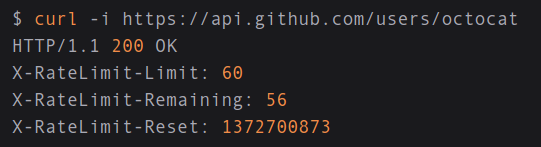
Missing Rate Limiting
-
Weak Password Policy
-
Use of Default Credentials
-
Missing Server Side Validations
-
Permission Issue
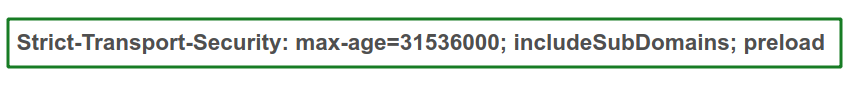
Enable HTTP Strict Transport Security (HSTS) Policy
- Prevent Cookie Hijacking
- Prevent SSL/TLS downgrade attacks
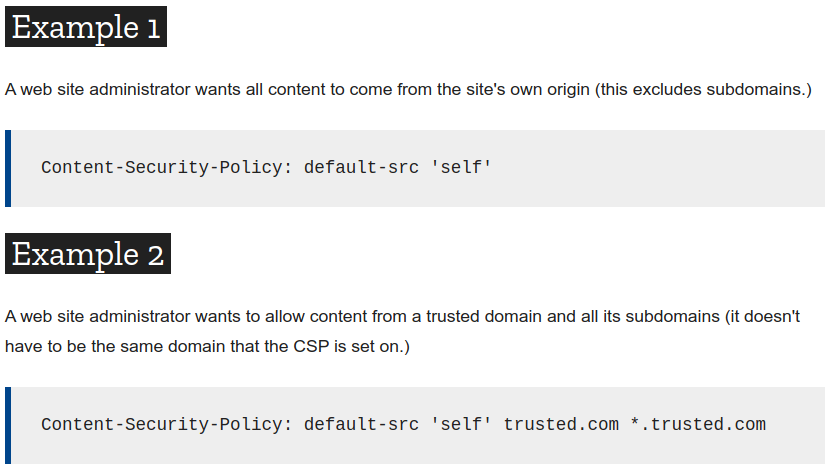
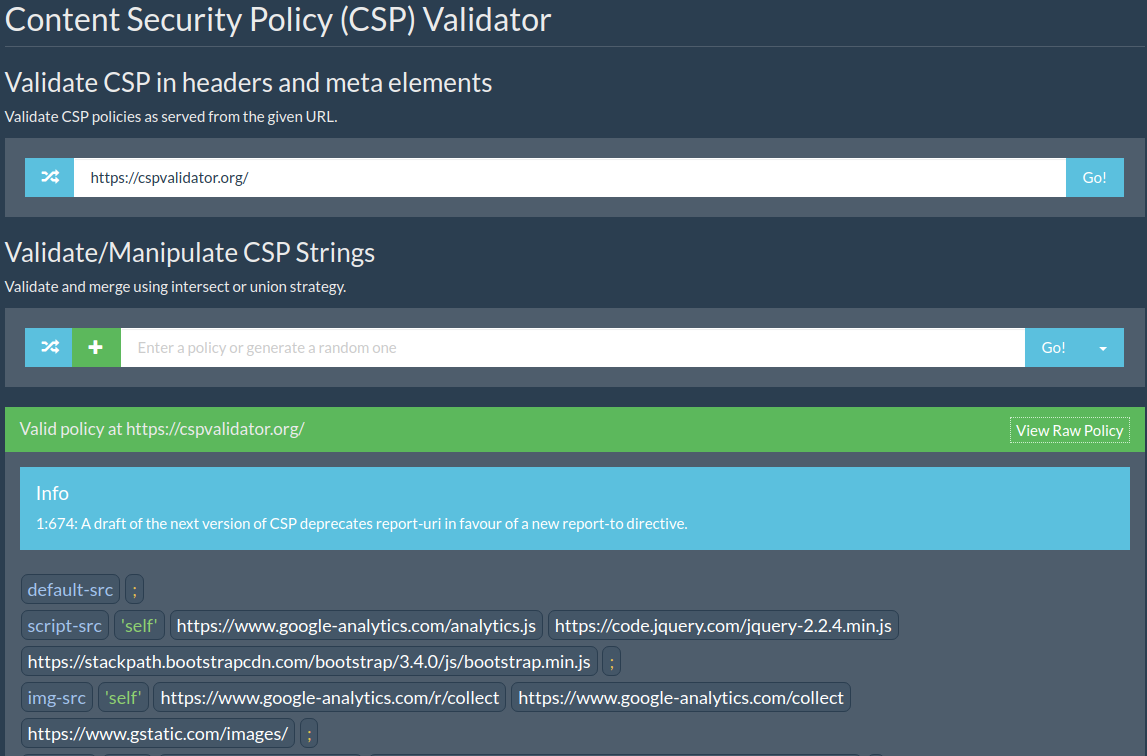
Content Security Policy (CSP)
Prevent Click-jacking
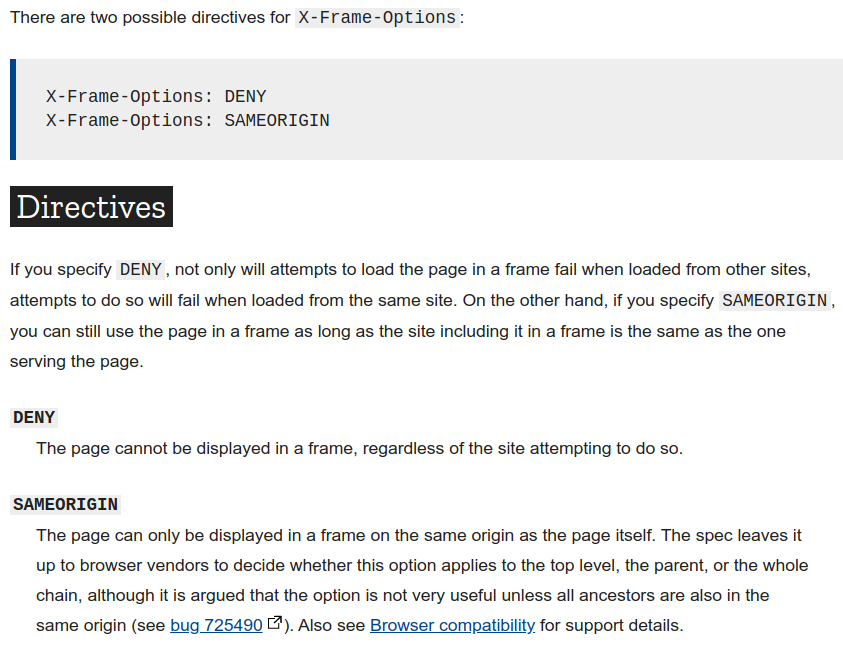
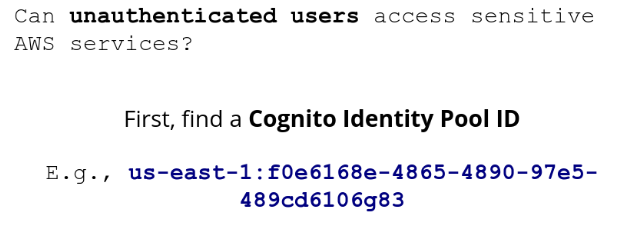
Amazon Cognito Misconfiguration
- https://slides.com/riddhishreechaurasia/null-bangalore-vyapi#/4/9
- https://github.com/riddhi-shree/knowledge-sharing/blob/master/Mobile/Android/amazon_cognito_authz_issue/README.md
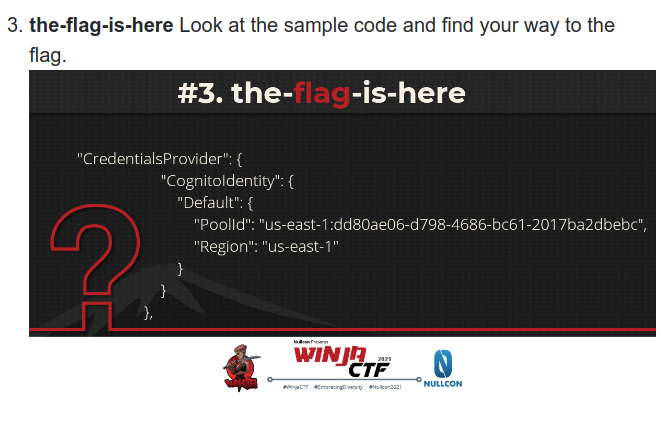
Test Your Skills
- docker run --rm -p 3000:3000 bkimminich/juice-shop
Further Reading
- https://github.com/riddhi-shree/knowledge-sharing/blob/master/Mobile/Android/amazon_cognito_authz_issue/README.md
- https://riddhi-shree.medium.com/security-shepherd-broken-auth-and-session-management-challenge-5-d3044e25a784
- https://www.youtube.com/watch?v=bRPpIdvSsJ4
- https://blog.appsecco.com/server-side-request-forgery-via-html-injection-in-pdf-download-90ee4053e911
- https://github.com/riddhi-shree/knowledge-sharing
- https://github.com/riddhi-shree/web-app-pentesting-using-burp-suite
- https://drive.google.com/file/d/1c92dHP_kbLlS53iRx_kLP7ht3Ayp7hZU/view?usp=sharing
Build. Break. Learn.
By Riddhi Shree Chaurasia
Build. Break. Learn.
- 1,006