SecQAtion
Security Testing Automation
About Me!
Riddhi Shree
Security Analyst Consultant | Arogya.ai
Trainer | SCADEMY - Secure Coding Academy
Community Volunteer | winja.nullcon.net
Conference Speaker | BSides, c0c0n, Nullcon, ISC2, Hack-In-The-Box, TexasCyber, Wicked6
GitHub: riddhi-shree Linkedin: riddhi-shree-001
Twitter: @_riddhishree
About This Talk!
When conducting security assessments:
- Tools are important
- Numerous tools exist
- Often, one tool isn't sufficient
Is it possible to build our own tool that can consume other tools, add its own steps, reduce the manual intervention, and generate a consolidated report? How hard could this be?
Let the robots do the grunt work.

Standard Security Testing Approach
- Browse
- Analyze
- Prepare
- Attack
- Confirm
- Report

Place of Security in SDLC
In traditional software development, security is a bottleneck
https://portswigger.net/solutions/devsecops/guide-to-devsecops


Robot Framework
- Open source automation framework
- For test automation
- For robotic process automation (RPA)
- Uses SeleniumLibrary and many other libraries
- Auto-generates test summary and test log
- Understands files with .robot extension
https://robotframework.org/
Basic Demo: Web Crawling
Basic Elements of Robot Framework
- Variables
- Keywords
- Test Cases
- Report and Log

VARIABLES:

KEYWORDS:

TEST CASES

TEST LOG:

Analyze the data captured by the robots as per your instructions.

TEST TEMPLATE:
Complex Project?
Maintain a folder structure

Power Features of Robot Framework
Python Libraries:
- Extend the capabilities of robot framework by writing custom keywords via Python scripts
- Include script results in final report auto-generated by robot framework
Test Template:
It is possible to repeat a set of test steps easily for an entirely different data set.
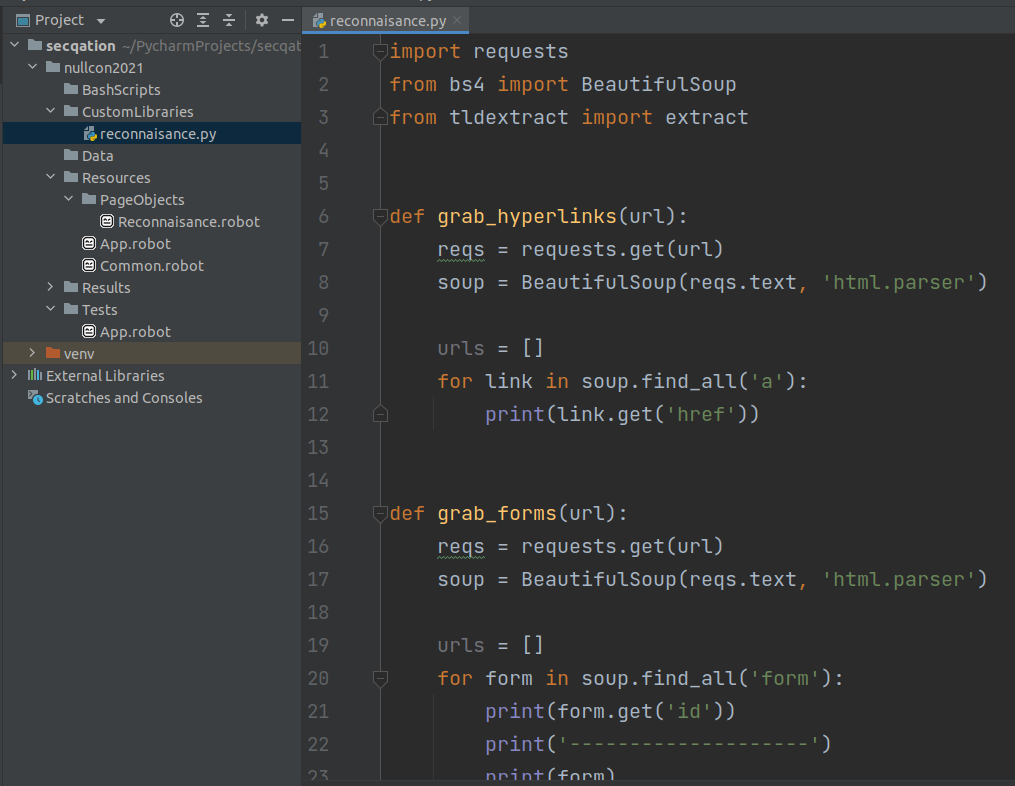
CUSTOM KEYWORDS:
mitmproxy
Intercepting API Requests & Responses

Title Text

While robots are busy exploring the web pages, mitmproxy intercepts and saves server requests and responses.

$ mitmweb -r traffic.mitm
Title Text
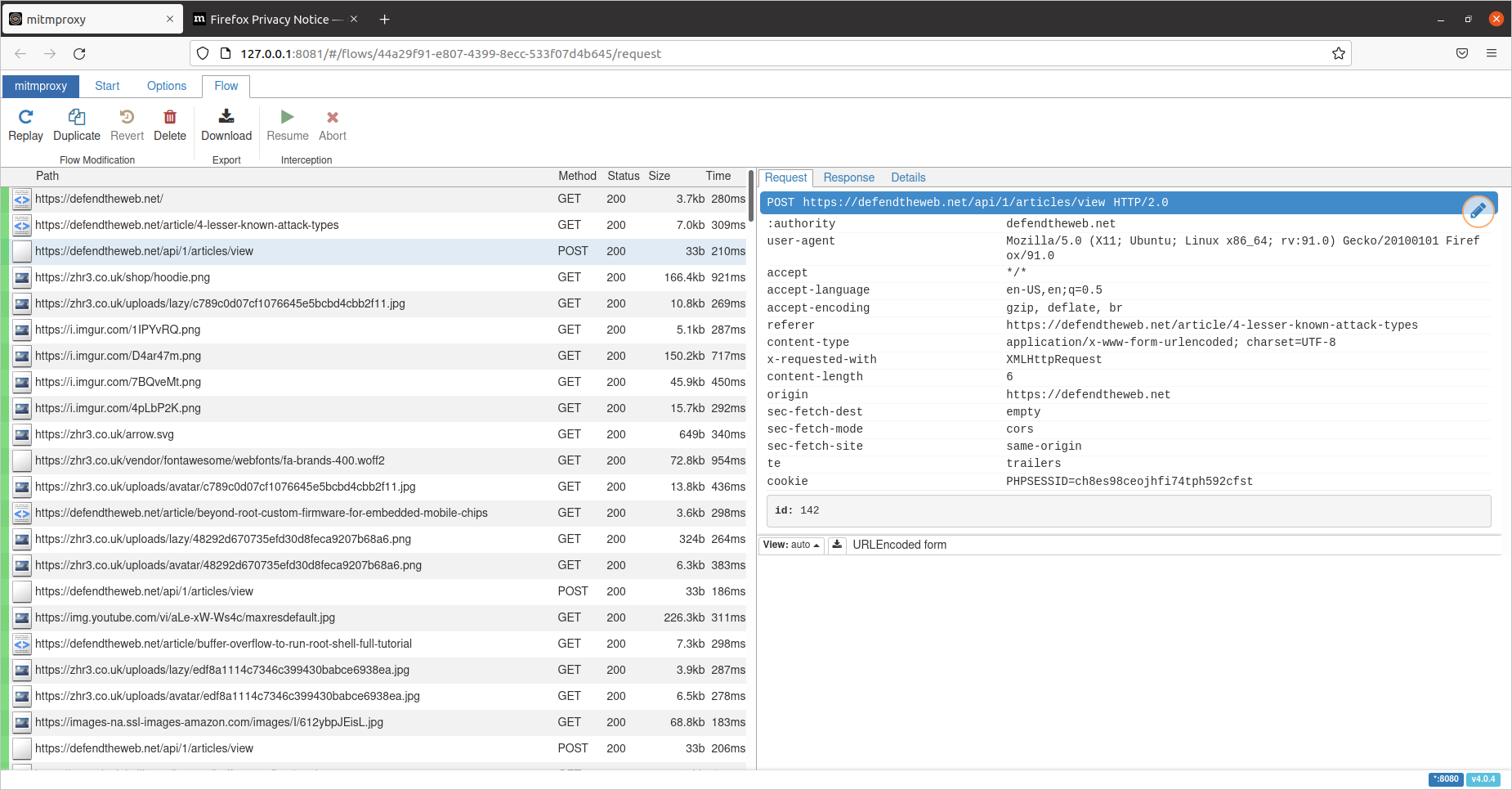
mitmweb can be used to further analyze the saved server requests and responses.
Apply Human Intelligence... Now!
-
While the robots were at work, it was a break for you. With a refreshed mind, now is the time to look at all the gathered data and identify potential attack vectors. You can get a good understanding about the target application.
-
If there's a need, the robot test cases can be enhanced further to automate the form filling process, or any other manual task, including reading emails from your email account or running commands in your bash shell, etc.
-
If you have clarity in your mind regarding the exact steps that you wish to perform, writing robot test cases is really a trivial process.
Pabot: Parallel Processing
- A parallel executor for Robot Framework tests
-
Split one execution into multiple and save test execution time


If same action needs to be performed on different URL's, then parallel processing can be applied

DevSecOps
It's easy to take our automation to the next level:
- Prepare automation test cases
- Build a Jenkins pipeline
- Every time code is pushed to GitHub, trigger a Jenkins build via webhook
- Jenkins will spin up docker containers and execute test cases
- Test report is pushed to S3 bucket
- The updated test report is served via CloudFront
Jenkinsfile: Stages

Handling Secrets


Jenkins
Jenkinsfile
Jenkinsfile: Post

ngrok

$ ngrok http 8080
Webhook

Git Push

Jenkins Pipeline

Console Output


https://github.com/aws-samples/amazon-cloudfront-secure-static-site#user-content-amazon-cloudfront-secure-static-website
Serving Test Report via S3 and CloudFront
Final Report

SecQAtion
By Riddhi Shree Chaurasia
SecQAtion
- 803



