Blockchain Technolgy & Decentralized Finance Part 3
Instructors: Andreas Park & Zissis Poulos
Rotman – MBA


Cryptography
Cyrptographic Hashing
- What is hashing?
- Why do we use it?
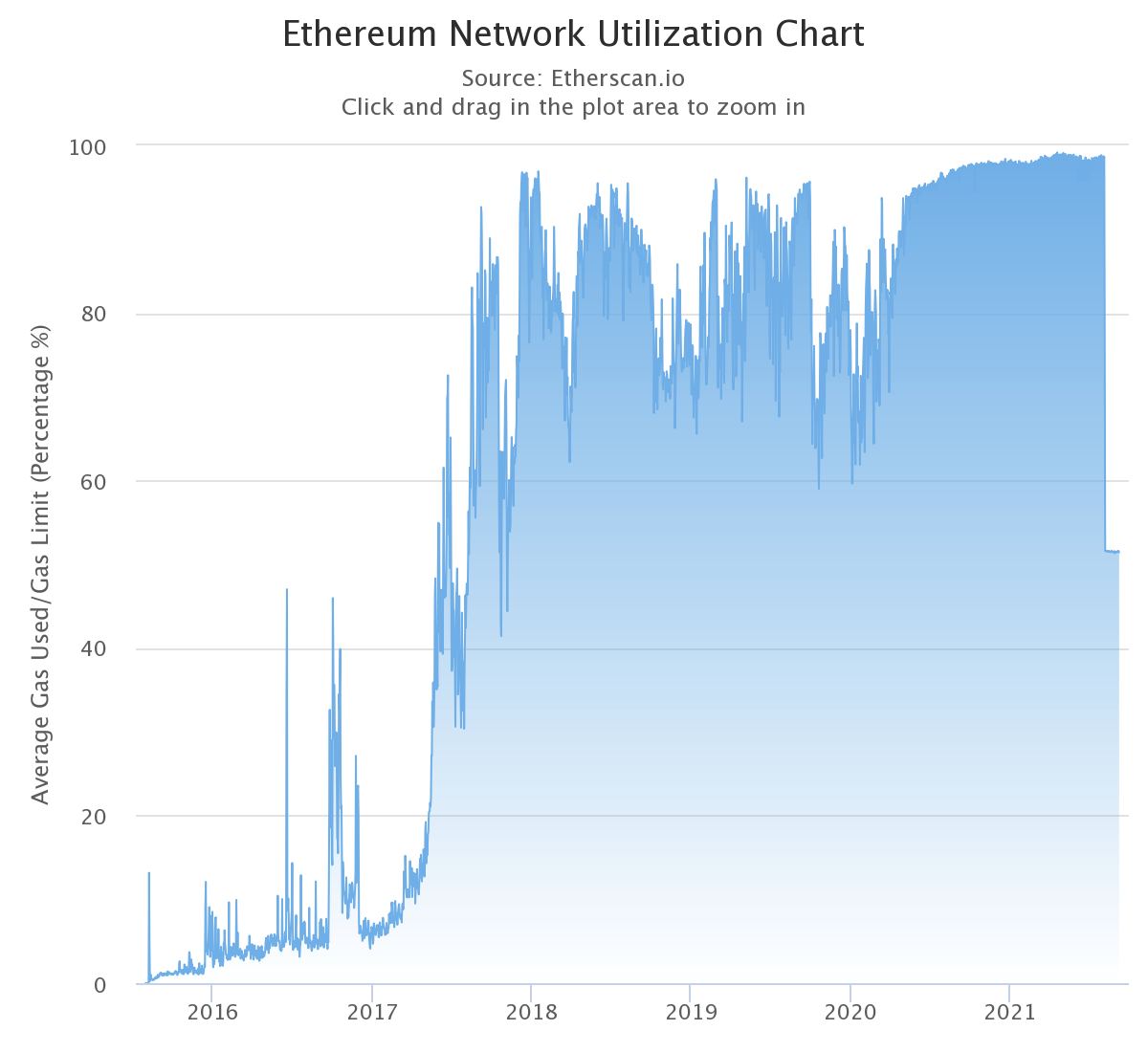
Ethereum is full and using it is expensive
Definition
Takes a message/text of arbitrary length and generates a fixed length output or "digest"
Properties
- Deterministic (i.e., not random)
- the same message always generates the same digest
- Fast
- you don't need much time/many computing cycles to compute a hash
- "unpredictable"
- if two messages are similar, their digests should look very different
- not invertible
- there is no inverse function, i.e., you cannot analytically infer the message from the digest, nor can an attacker find the message from the digest efficiently by searching (it's VERY hard).
-
Collision resistant
- an attacker cannot find two messages that have the same digest in "normal" time.
Simple Application
- Databases should not store user passwords and usernames in plain text
- => attacker could immediately impersonate every user
- Store as a hash: attacker cannot easily invert the username & password
What hashing functions are there
- Many!
- MD5
- SHA1 (better than MD5)
-
SHA256 (better than MD5)
- output of 256 bits; 4 bit= 1 characters => 64 characters (hexadecimals)
- developed by the NSA
- Code, e.g., https://www.movable-type.co.uk/scripts/sha256.html
- SHA512
- RIPEMD-160 (for 160 bit output)
Demo time!
https://andersbrownworth.com/blockchain/
Why are hashing functions used in blockchain?
- efficient way to represent data
- always same-length output
- => good convention
- small changes to data trigger large changes in hash
- (recall the demonstration)
- => easy to check consistency
- they work as "pointers"
- each block contains a hash of the past block
- this hash is a pointer
- pointers make searches easy
- Hashes of hashes are used to simplify data storage
- the process of hashing hashes repeatedly creates the "Merkle Tree"
Encryption
- Problem: send message M that you want no-one to be able to read
- Basic idea:
- should be easy to decrypt with the right tool
- hard to decrypt without it
Alice wants to send Bob money without Charles seeing it
SYMMETRIC: Alice and Bob use the same key to
encrypt and decrypt a message
Public key = Private key
ASYMMETRIC: Bob has a public and a private key
Public
Private
Digital Signatures
- Problem: send message and ensure that the other side believes that you sent this particular message
- worry about manipulation
- other side may worry about proving what you did, etc.
- => want to digitally sign the message
- As with encryption:
- should be easy to prove that you signed
- hard to forge your signature
Alice's private
Alice wants to send Bob message and provide proof that it's her
Alice's public
Uses
- Transaction authorization
- Governance votes
- Consensus protocol votes
Types
- RSA (Rivest-Shamir-Adleman)
- old school, fast to verify, long keys
- not used in blockchain
- Elliptic curve
- shorter keys for same level of security as RSA
- Ethereum, Bitcoin
- BLS (Boneh–Lynn–Shacham)
- mutliple pub keys and messages into one signature!
- Ethereum 2.0
Uses
- Transaction authorization
- Governance votes
- Consensus protocol votes
Types
- RSA (Rivest, Shamir, Adleman)
- old school, fast to verify, long keys
- not used in blockchain
- Elliptic curve
- shorter keys for same level of security as RSA
- Ethereum, Bitcoin
- BLS
- mutliple pub keys and messages into one signature!
Quantum-resistant signatures???
Summary
The main cryptographic primitives
- Collision-resistant hash functions
- Digital signatures
But it doesn't end here...
zk-SNARKS
- Used for privacy and to some extent for scaling
- Covered later in the course
Proof-of-Stake
Proof of X
Proof of Stake (PoS) - What is the goal?
- Energy efficiency
- No need to commit extreme compute power to solve puzzles for leader election (PoW)
- Centralization Risk
- Can validate using simpler hardware -> more nodes can participate to validate network
- Economic cost of attacks
- Explicit penalties for misbehaviour (vs. PoW)
Validation and leader election
random
32 ETH
Validation and leader election
random
random
random
Committee 1
Committee 2
random
Block formation
Committee 1
Committee 2
...
Committee 32
attest
attest
Slot 1
Slot 2
Slot 32
...
12 seconds
Finality!
...
checkpoint
...
vote
vote
When final?
2/3 of stake has voted
Security
What do we need from validators?
- Participation
- Honesty
if "lazy"

misses out on rewards
if dishonest
Security
What is dishonest?
- Propose multiple blocks for single slot
- Contradictory attestations
TLDR
Performing a 51% attack still possible but "almost equivalent to having your entire mining farm burn down while you are doing it" -Zamfir
Other malicious behaviour
- Long-range attack
- Short range reorgs (can be bad for DeFi)
- etc.
What about forks??
Still possible
- Need agreement on what the canonical chain is
- Longest-chain rule not ideal. Why?
B3
B1
B2
B4
Protocol Rule
"The canonical chain is the one with greatest weight of attestations in its history"
PoS vs PoW
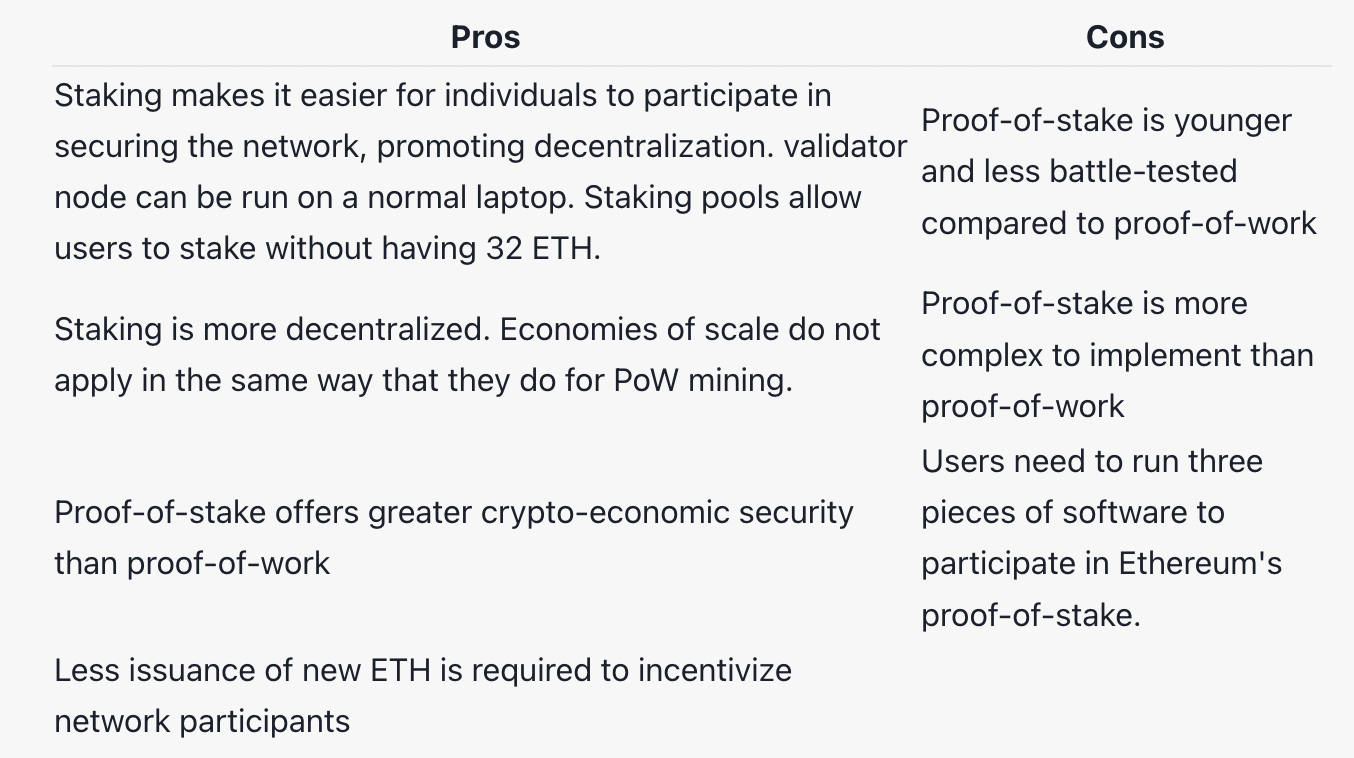
https://ethereum.org/en/developers/docs/consensus-mechanisms/pos/
Copy of Decentralized Finance: Introduction (MBA) Part 3
By zpoulos
Copy of Decentralized Finance: Introduction (MBA) Part 3
This is the slide deck that I use for a quick introduction to the Decentralized Finance class.
- 2,448



