Welcome to Uppsala.js
Saving a dane
or "How to detect malware, get scared and improve your JS security"
Disclaimer: I'm not a security expert.
Once upon a time...

"Unexpected token <"
"Can't find variable: webpackJsonp"
"Syntax error"
"null is not an object"
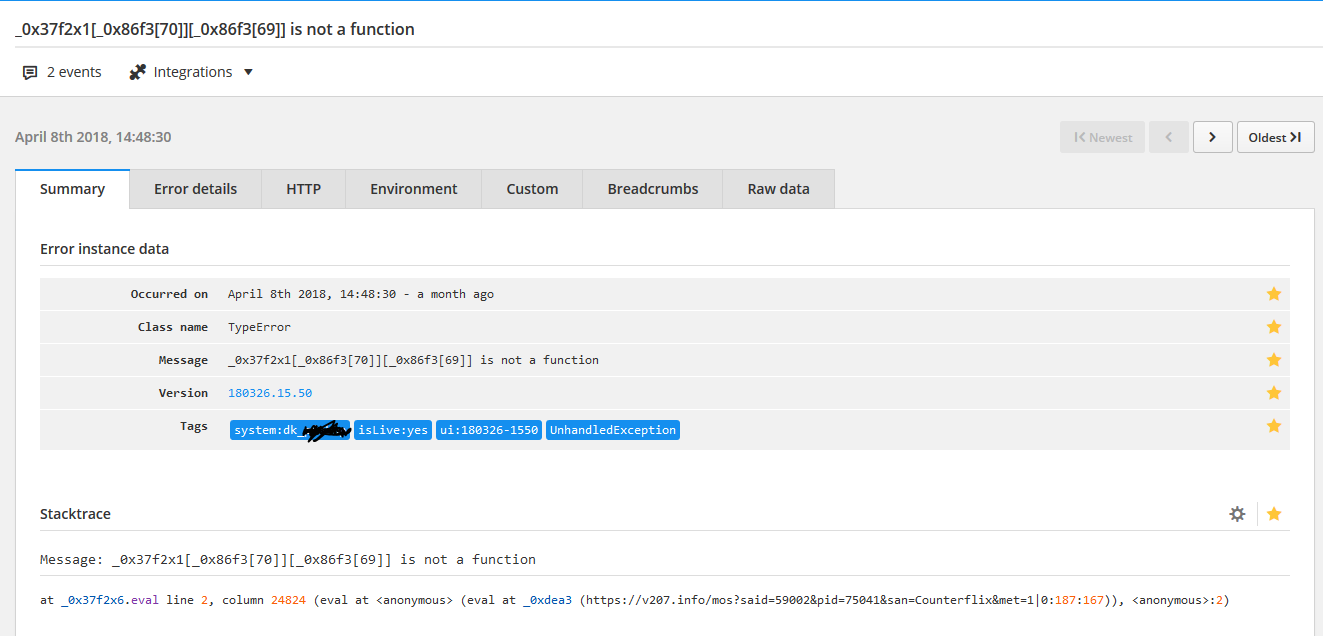
"_0x37f2x1[_0x86f3[70]][_0x86f3[69]] is not a function"
"Exception invoking info"
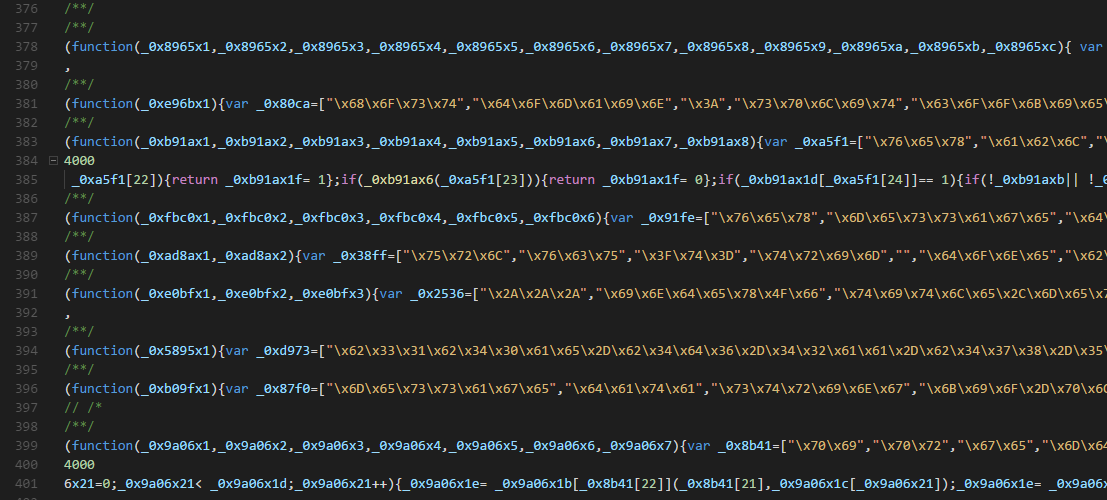
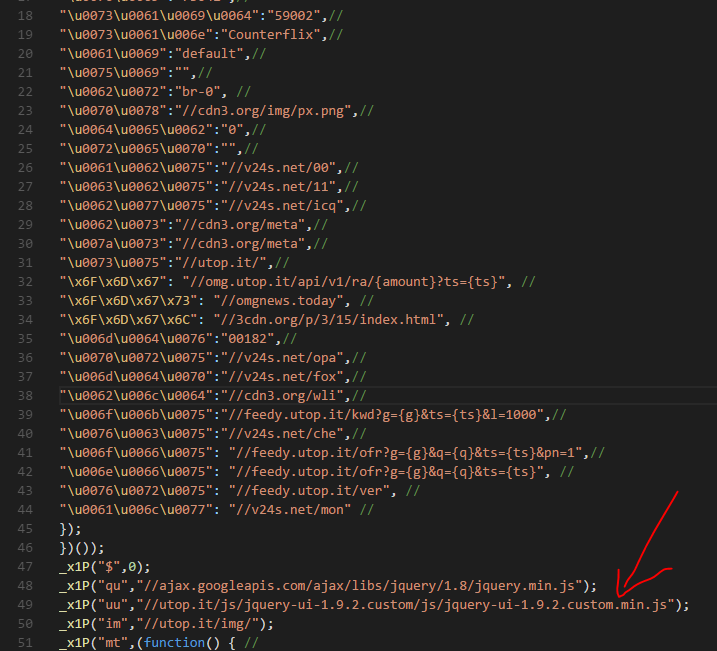
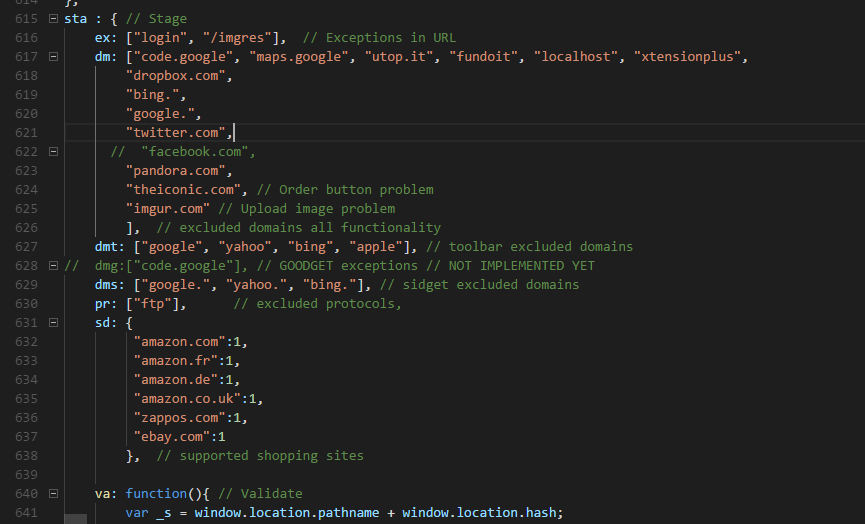
Technical Debt
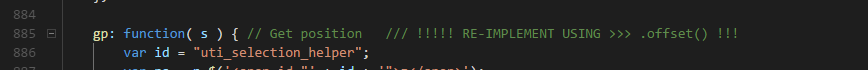
Error handling, plan for the worst

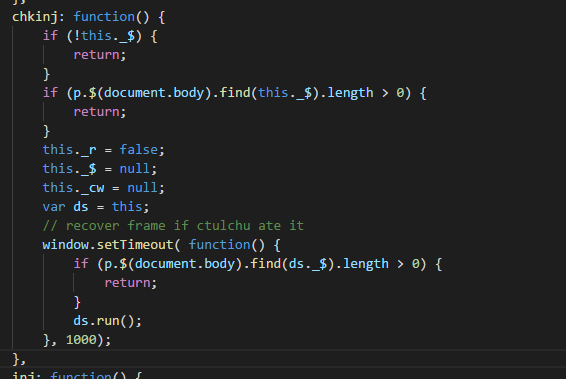
Are we h4cked?

Are we h4cked?
No. Probably not.
Improving Security
- Victims browser was compromised
- Our source code is compromised
- We got MITM
- A dependency got compromised
Scan your dependencies

$ snyk test
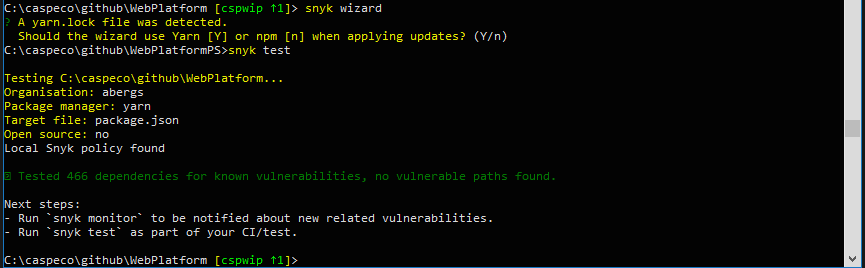
$ npm audit
npm, .net, java, scala, php, python etc...
Lock down your site with CSP
Content-Security-Policy: default-src 'self'
or
<meta http-equiv="Content-Security-Policy" content="default-src 'self';">
Benefits of CSP
- Browser feature - Makes XSS attacks a lot harder (almost 100%)
- Whitelisting: In control of running code / make outbound requests
- Force HTTPS on all resources
- Helps Mixed-Content warnings when moving to HTTPS (perfect for CMS's)
- ReportOnly: Test before you enforce
Making XSS harder
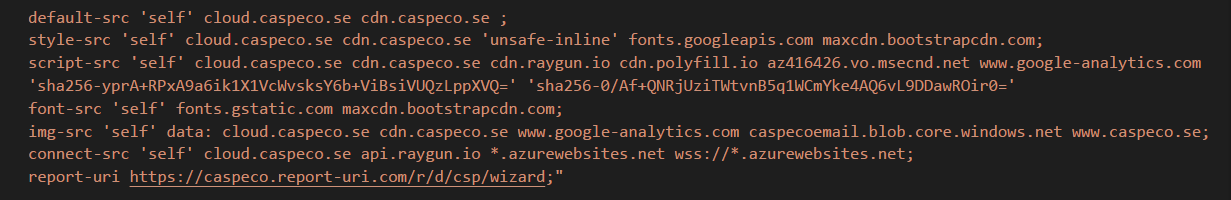
default-src 'self' cloud.caspeco.se cdn.caspeco.se
script-src cdn.raygun.io ... sha256-xxxxx
connect-src api.raygun.io ...
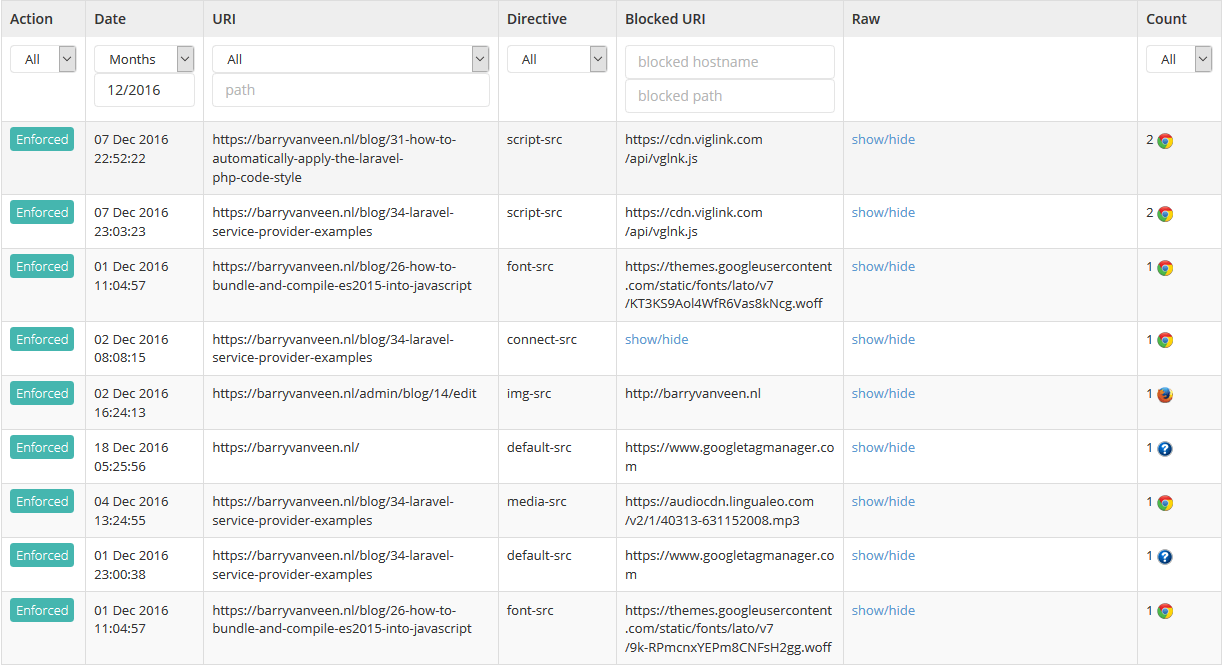
report-uri https://report-uri.com
Report (Only)
Content-Security-Policy-Report-Only: default-src 'self'
Helping with HTTPS
Content-Security-Policy:
upgrade-insecure-requests;
When you can't transform urls to use relative protocol, e.g: "//mydomain.com"
http://foo.bar -> https://foo.bar
Final links
It's almost a silver bullet
https://hackernoon.com/im-harvesting-credit-card-numbers-and-passwords-from-your-site-here-s-how-9a8cb347c5b5
What is a CSP?
https://developer.mozilla.org/en-US/docs/Web/HTTP/CSP
Supported by all modern browsers
https://caniuse.com/#search=CSP
Great tooling: report-uri.com
Thanks for listening!
(We're hiring!)
anders@caspeco.se - @andersaberg
deck
By abergs
deck
- 507



