Trusted Execution Environments
What is a TEE?
- Isolated environment in a main processor.
- It guarantees protection from main OS.
- Uses both software and hardware to protect
- Contrast with a Rich Execution Environment (REE)

Where are TEEs used?
- Smartphones
- Tablets
- IoT Devices


What goes in a TEE?
- Trusted OS
- Trusted Applications
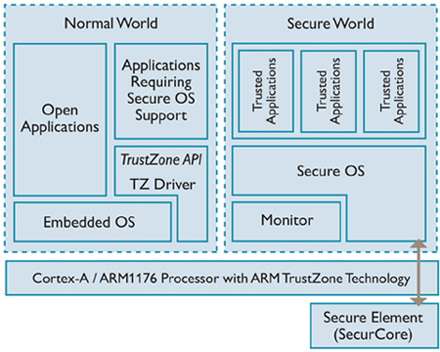
A schema from ARM depicting TrustZone, a hardware technology that can be used to support TEE implementations

Trustonic's Kinibi OS for ARM TrustZone
What Makes a TEE Trustworthy?
The Separation Kernel
Foundation component of TEE
- Simulates distributed system
- Enables coexistence of different systems with different levels of security on the same platform
- Divides the system into partitions, and guarantees a strong isolation between them, except for carefully controlled communication.
Security Requirements for the Kernel
- Data (spatial) separation
- Sanitization (temporal separation)
- Control of information flow
- Fault isolation
Another Definition for a TEE
Trusted Execution Environment (TEE) is a tamper-resistant processing environment that runs on a separation
kernel. It guarantees the authenticity of the executed code, the
integrity of the runtime states (e.g. CPU registers, memory
and sensitive I/O), and the confidentiality of its code, data
and runtime states stored on a persistent memory. In addition,
it shall be able to provide remote attestation that proves its
trustworthiness for third-parties. The content of TEE is not
static; it can be securely updated. The TEE resists against
all software attacks as well as the physical attacks performed
on the main memory of the system. Attacks performed by
exploiting backdoor security flaws are not possible.
- Tested by trustworthy lab
- Able to attest to its own trustworthy state
- Properly reproduced in production devices
Ideal TEE
- Able to attest to its own trustworthy state
- Refuses to offer service if signature checks fail
Real-World TEE
How Can We Measure Trust?
Static Trust
- Based on comprehensive evaluation against a specific set of security requirements
- Trustworthiness measured only once before deployment
Dynamic Trust
- Based on state of system
- Continually changes
- Measured throughout lifecycle
- Relies on secure and reliable evidence of trust status
Root of Trust
- Provides trustworthy evidence regarding state of system
- Composed of a trusted measurement and a function to compute a trust score
- Must be tamper-resistant hardware module
Trust in TEE
- Hybrid trust, both static and semi-dynamic
- TEE certified before deployment
- ROT assures certification each boot
- After boot, integrity protected by separation kernel
TEE Building Blocks
- Secure Boot
- Secure Scheduling
- Inter-Environment Communication
- Secure Storage
- Trusted I/O Path
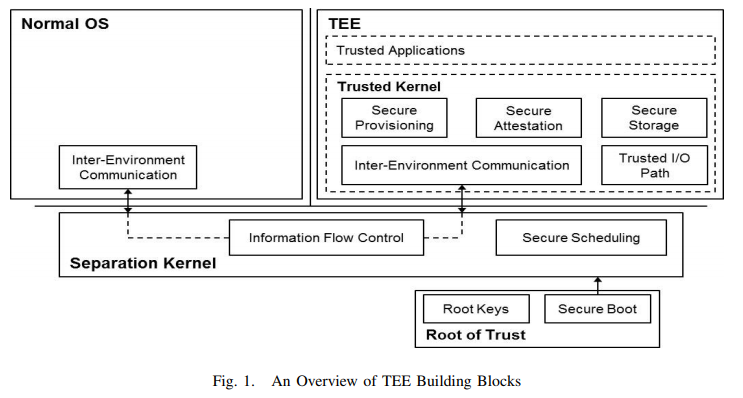
Secure Boot
- Only code of a certain property can be loaded
- Modifications interrupt the bootstrap process
- Consists of various stages, and each layer is checked through a cryptographic hash
- The initial boot code protected by hardware
- Appropriately authorized
- Authorization has been checked by other authorized code
- TA’s can only directly access their own data
Code Requirements
Secure Scheduling
- Assures balanced and efficient coordination between TEE and the rest of the system
- Tasks in TEE should not affect responsiveness of main OS
- Scheduler should take real-time constraints into consideration
Inter-Environment Communication
- TEE needs and interface to communicate with the rest of the system
- Mechanism must be reliable (memory/time isolation), with minimum overhead (unnecessary data copies and context switches), and must protect communication structures
Secure Storage
- Confidentiality, integrity, and freshness guaranteed
- Only authorized entities can access the data
- Based on : integrity-protected secret key that can be accessed only by the TEE, cryptographic mechanisms, such as authenticated encryption algorithms, and data rollback protection mechanism, such as replay-protected memory blocks (RPMB)
Trusted I/O Path
- Protects authenticity, and optionally confidentiality, of communication between TEE and peripherals
- Input and output protected against screen-capture, key logging, overlaying, and phishing
- Trusted path allows user to interact with applications running inside TEE
Runtime Isolation
- Trusted Applications (TA) in the TEE only have to trust the Trusted OS
- A TA’s assets are isolated from all other environments in the device.
- A TA has no method to open a file owned by another TA:
- If TA1 creates a file called “Secrets”, TA2 can also create a file called “Secrets”, but the Trusted OS treats them as two different files.
- Nothing in the REE can access the contents of either TA's file.
- TEE storage bound to device
An Example
Related Concepts
Secure Execution Environment (SEE)
- Guarantees authenticity, integrity, and confidentiality
- Does not involve RoT
Dynamic Root of Trust Measurement (DRTM)
- Enables some pieces of code to be executed in an isolated environment without trusting the previously loaded software.
- Not limited to the code running in the isolated environment
- Does not provide secure storage or include trusted mechanisms
- Needs to use the main memory as its runtime memory
Questions
- What separates a TEE from a Secure Execution Environment or a Dynamic Root of Trust Measurement?
Questions
- What separates a TEE from a Secure Execution Environment or a Dynamic Root of Trust Measurement?
- What attacks do TEEs protect against?
Questions
- What separates a TEE from a Secure Execution Environment or a Dynamic Root of Trust Measurement?
- What attacks do TEEs protect against?
- What attacks do TEEs fail to protect against?
Questions
- What separates a TEE from a Secure Execution Environment or a Dynamic Root of Trust Measurement?
- What attacks do TEEs protect against?
- What attacks do TEEs fail to protect against?
- What kind of app should be run in a TEE?
Questions
- What separates a TEE from a Secure Execution Environment or a Dynamic Root of Trust Measurement?
- What attacks do TEEs protect against?
- What attacks do TEEs fail to protect against?
- What kind of app should be run in a TEE?
- What is a TEE?
Bibliography
- Sabt, M; Achemlal, M; Bouabdallah, A (2015). "Trusted Execution Environment: What It Is, and What It Is Not". 2015 IEEE Trustcom/BigDataSE/ISPA (PDF). IEEE. IEEE. pp. 57–64.
- https://blog.quarkslab.com/introduction-to-trusted-execution-environment-arms-trustzone.html
- https://www.trustonic.com/technical-articles/what-is-a-trusted-execution-environment-tee/
Trusted Execution Environments
By ahfeng
Trusted Execution Environments
- 595


