HTTPS, SSL/TLS, Certificados, PKI, SNI, Apache VHosts, K8s Ingress...
¿cómo encaja este puzzle?
By Álvaro Iradier
Lightning DTalks by DareCode
Security Tangram #1


PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI
What is security?

What is love?
What is the smell of clouds? ®
Let's focus on computer and information Security
Preventing unauthorized access, use, disclosure, disruption, modification, inspection, recording or destruction of information
ISO/IEC 27000:2009

Security Properties

Confidentiality
Information is not made available or disclosed to unauthorized individuals, entities, or processes
Availability
The computing systems used to store and process the information, the security controls used to protect it, and the communication channels used to access it must be functioning correctly
Integrity
Maintaining and assuring the accuracy and completeness of data over its entire lifecycle
Security Properties

Confidentiality
Information is not made available or disclosed to unauthorized individuals, entities, or processes
Availability
The computing systems used to store and process the information, the security controls used to protect it, and the communication channels used to access it must be functioning correctly
Integrity
Maintaining and assuring the accuracy and completeness of data over its entire lifecycle
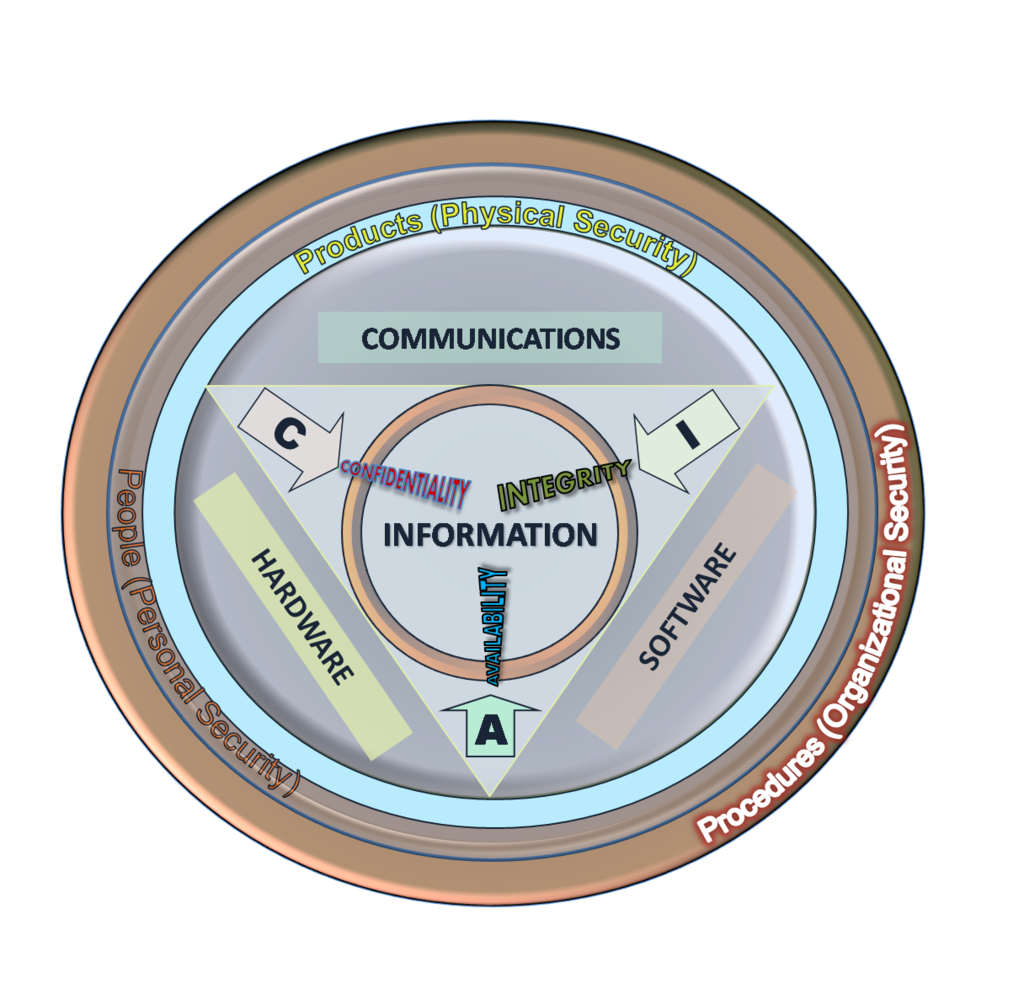
CIA triad, portions, and layers
Security properties

- Non-repudiation
- Authenticity
- Accountability
- Reliability
- ...
Security Risks

Snooping / eavesdropping
Unauthorized access to another person's or company's data. Snooping can include casual observance of a screen, watching someone typing, ...
Phising
Fraudulent attempt to obtain sensitive information (user/pass, credit card) by disguising as a trustworthy entity in an electronic communication
Tampering
The act of deliberately modifying (destroying, manipulating or editing) data through unauthorized channels
Denial or reception / service
Preventing service from receiving request / legitimate users from accessing specific computer systems, devices, services or other IT resources.
How to "implement" it?

Public algorithm cryptography. The key is secret.
- Hash functions: fast; one-way, collision-resistant
- Symmetric: slow; medium key size; shared key
- Asymmetric: slowest; big key size; public/private key (key pair)
Secret algorithms? Never. Security by obscurity.
Firewalls
- Application level
- Network level
What is cryptography?




Cryptography or cryptology
(from Ancient Greek: κρυπτός, translit. kryptós "hidden, secret"; and γράφειν graphein, "to write", or -λογία -logia, "study", respectively) is the practice and study of techniques for secure communication in the presence of third parties called adversaries.
Cryptographic Hash Functions

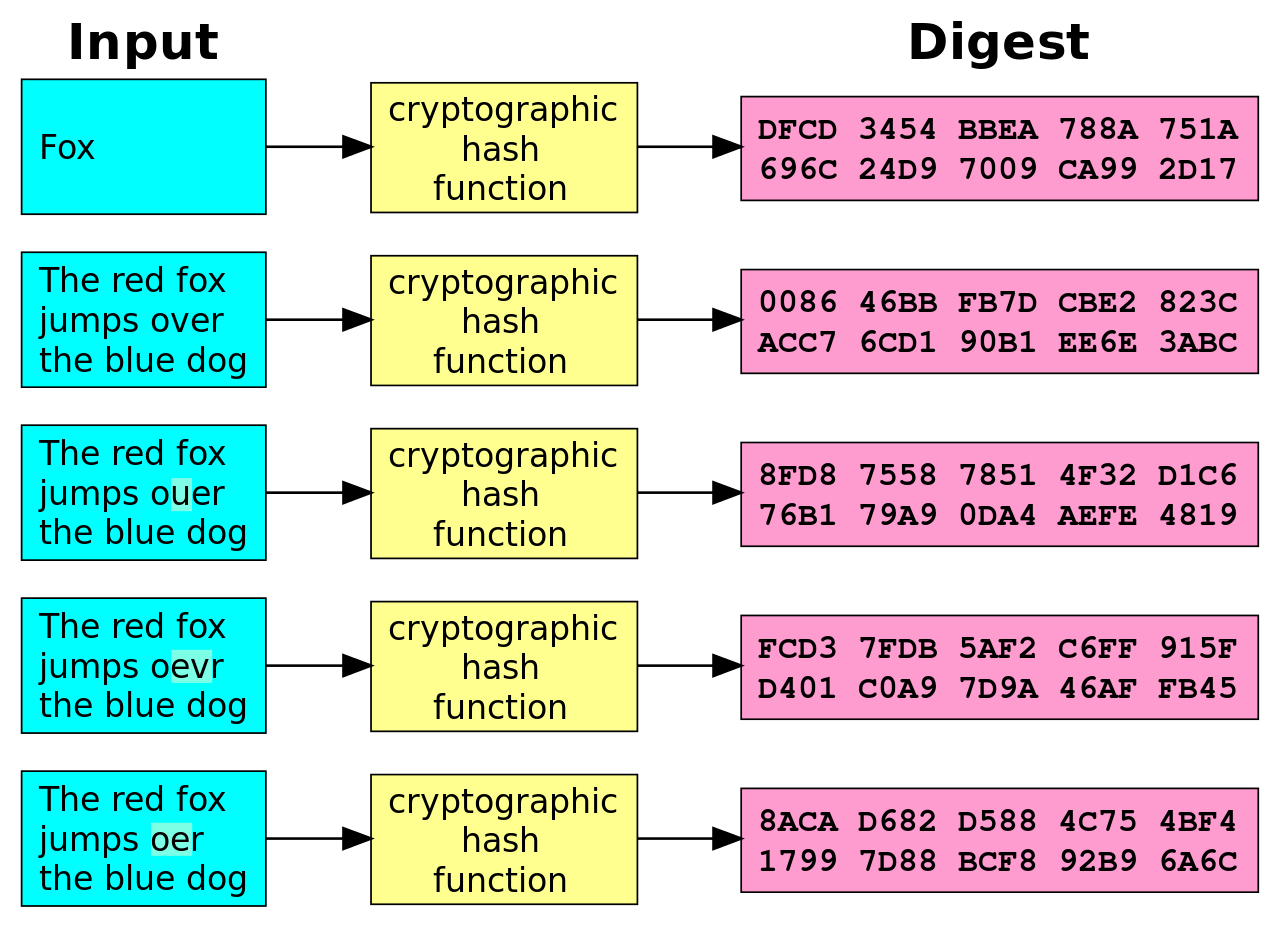
Cryptographic Hash Functions


- Fast: computed quickly for big inputs
- One-way: impossible to find input from digest
- Anti-collision: not computationally feasible to find a collision (2 inputs with same digest)
- Example: SHA1 (!)
- Others: MD5, SHA2/SHA-256, SHA-512, ...
Used for integrity
Symmetric Cryptography

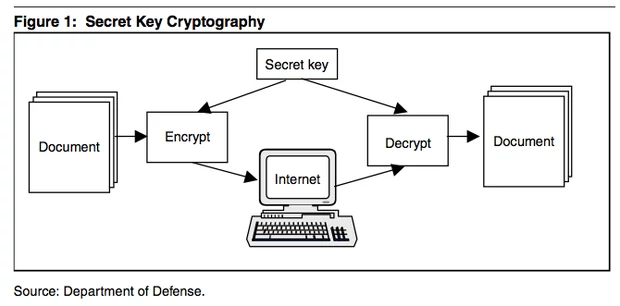
How to distribute the Secret key?
Algorithms: DES, 3DES, AES (Rijndael), Blowfish, RC4, IDEA, Twofish...
Asymmetric Cryptography

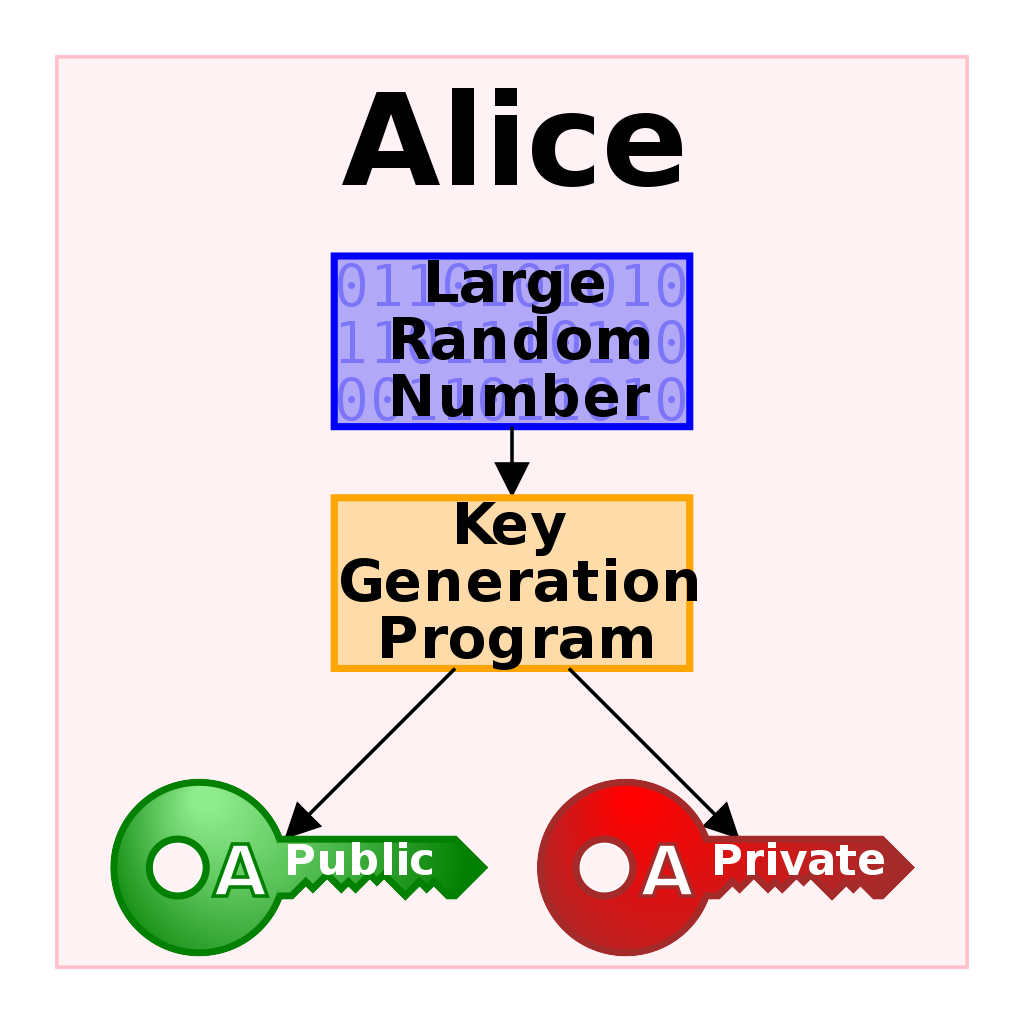
Public key
Can (and should) be distributed.
Private key
Must be kept secret.
Asymmetric Cryptography

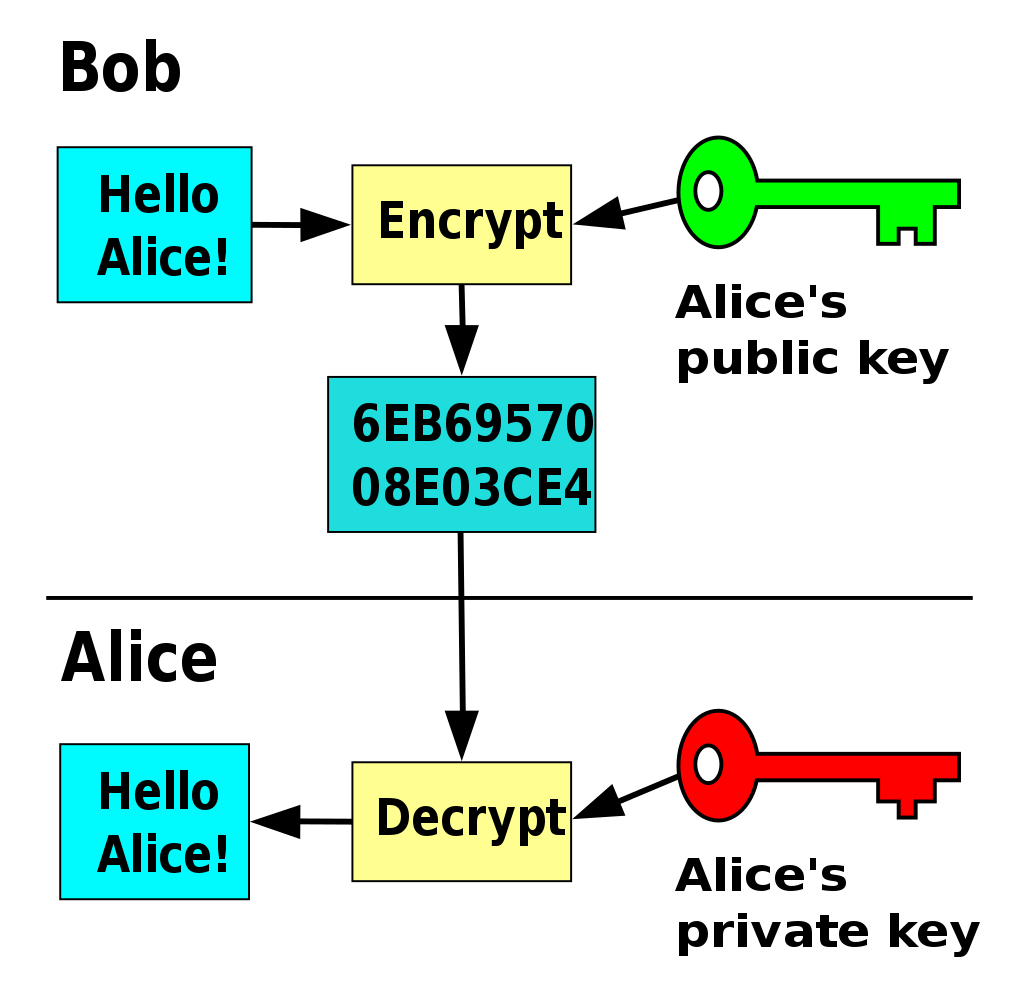
Asymmetric Cryptography

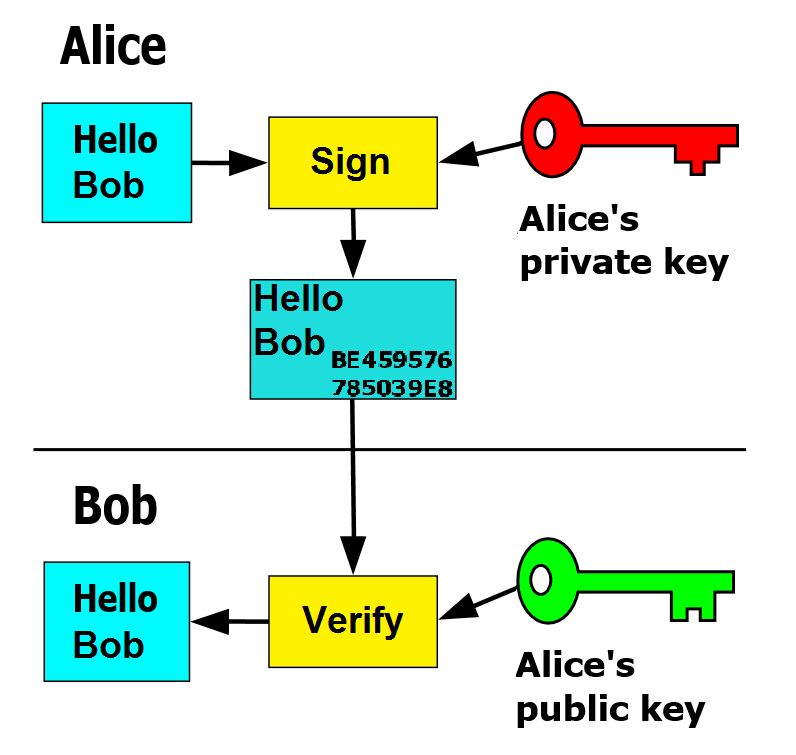
Asymmetric Cryptography


How to distribute the PUBLIC key?
What is PKI?
PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI
What is PKI?
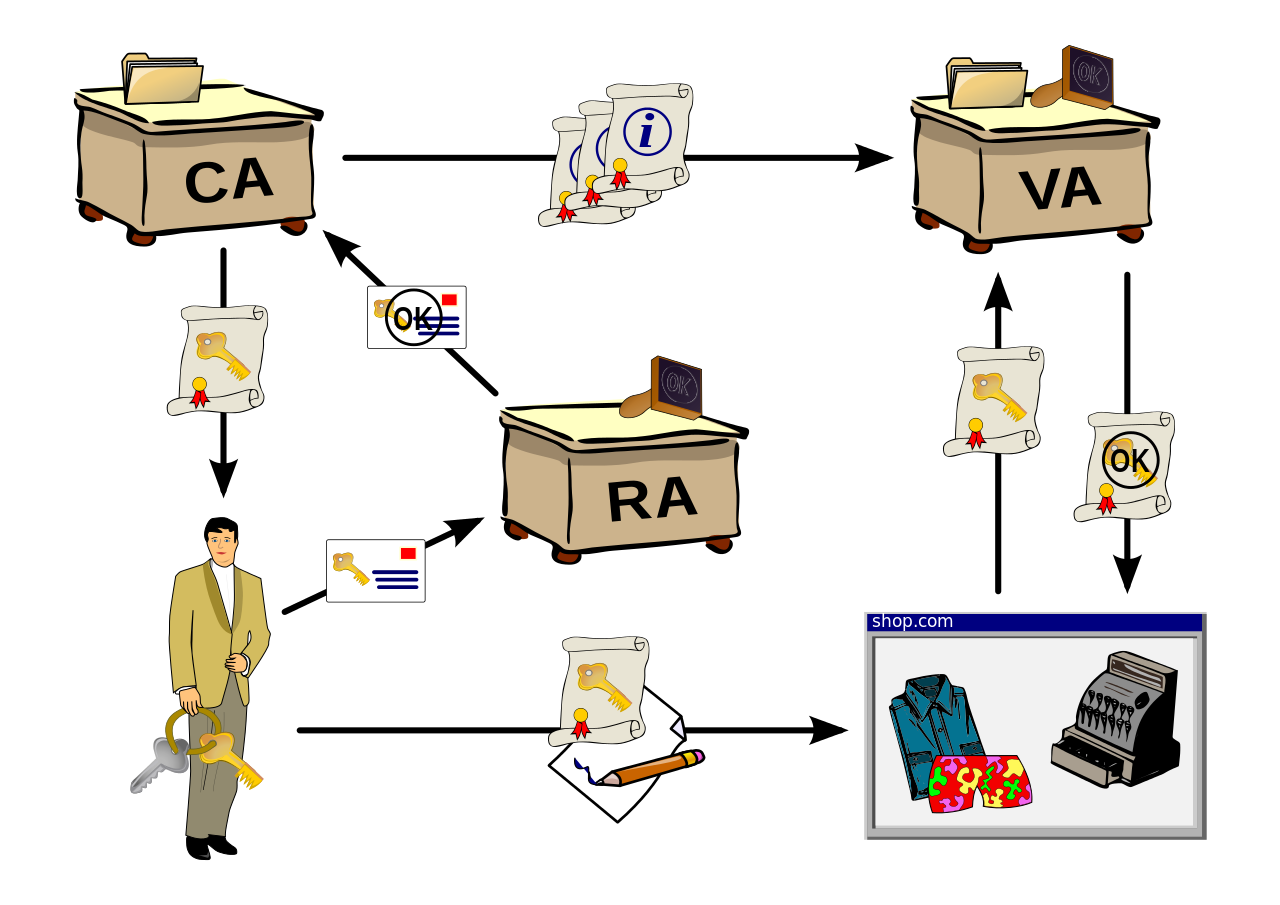
Public Key Infrastructure
How to bind identities to Public Keys
Entities: people, organizations, servers. Have an identity
RA: Registration authority. Accepts requests, validates identity
CA: Certification authority
Issuance of certificates. Binding of identity - public key
VA: Validation authority
Verify the validity of the certificate (via CRLs)
What is PKI?

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI

C.A. & Certificates
PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI
C.A. & Certificates

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI
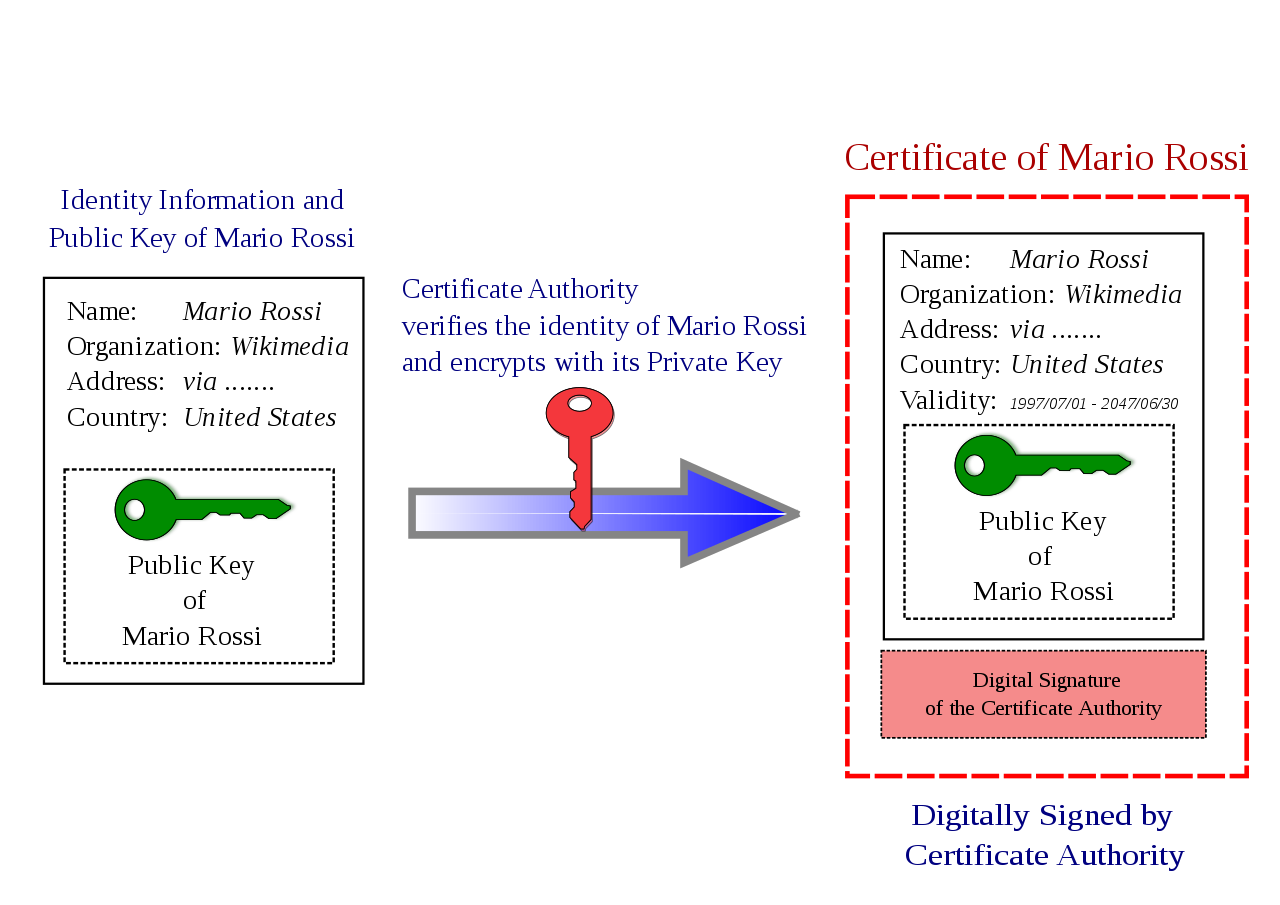
Let's make it simple. What is a digital certificate?
- A stream of bytes with a specific format (usually X.509, ASN-1)
- Encoding using some encoding (DER, PEM, ...)
- Containing a set of attributes:
-
Identity:
- CN (Common Name)
- Organization, department, city, country, ...
- Public Key
- Expiration date
- Issuer identity
- ...
-
Identity:
- And, most important: digitally signed by issuer
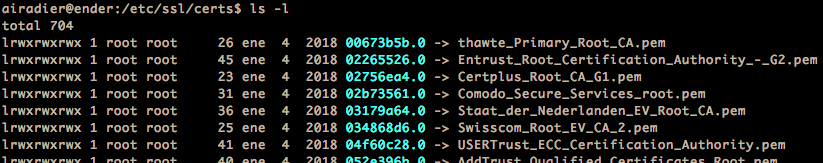
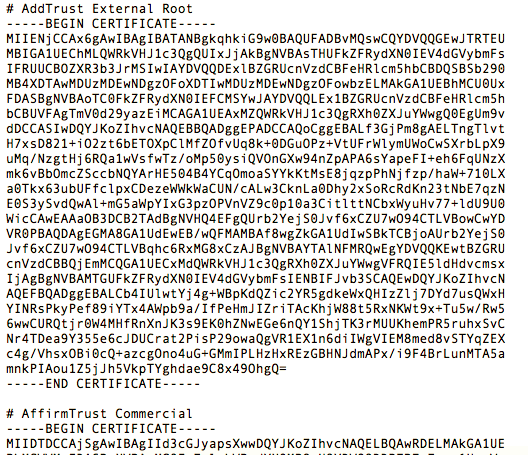
C.A. & Certificates
C.A. & Certificates
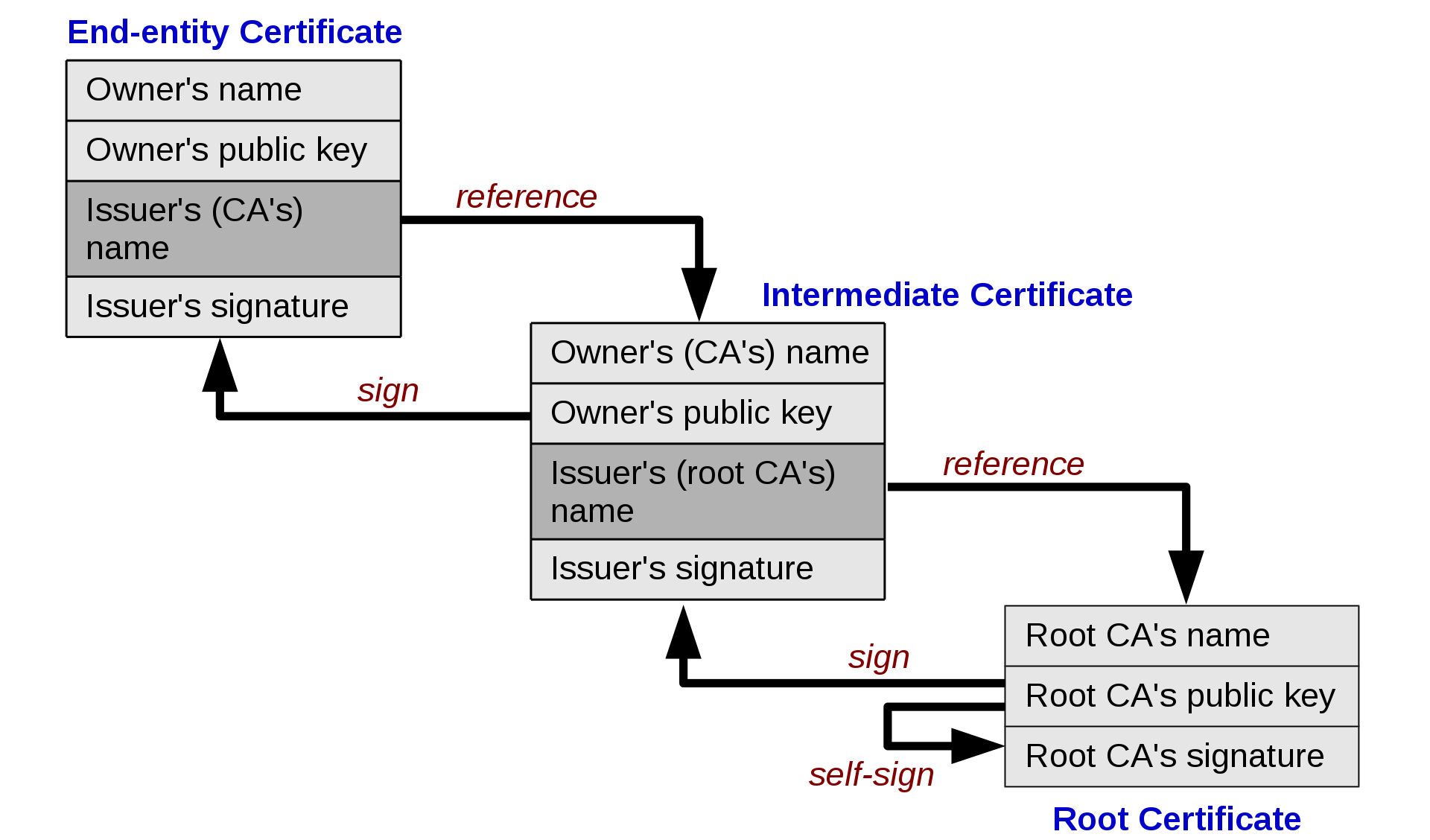
Chain of trust
and self-signed certificates
C.A. & Certificates
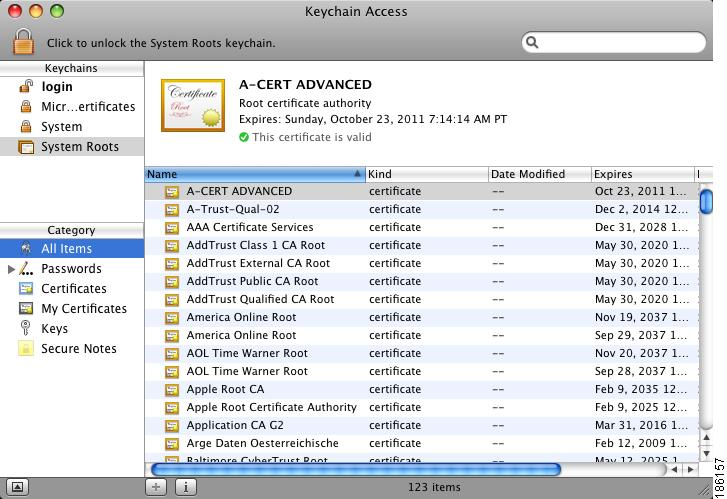
Root CA certificates are self-signed... trust?
C.A. & Certificates
Root CA certificates are self-signed... trust?
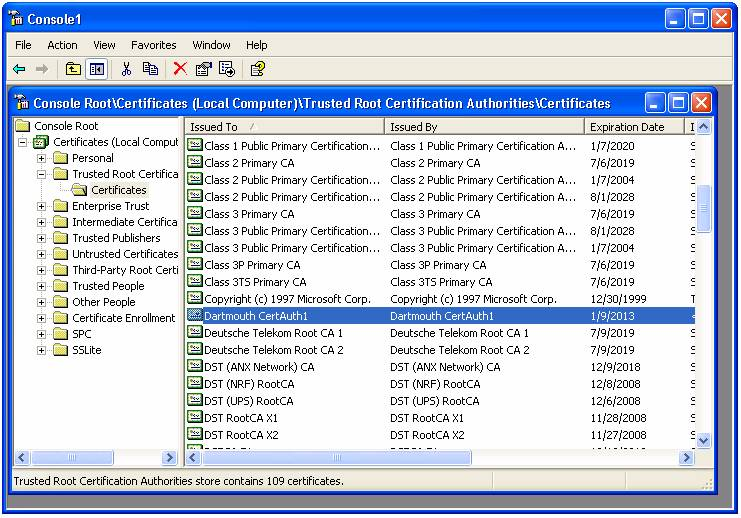
C.A. & Certificates
Root CA certificates are self-signed... trust?
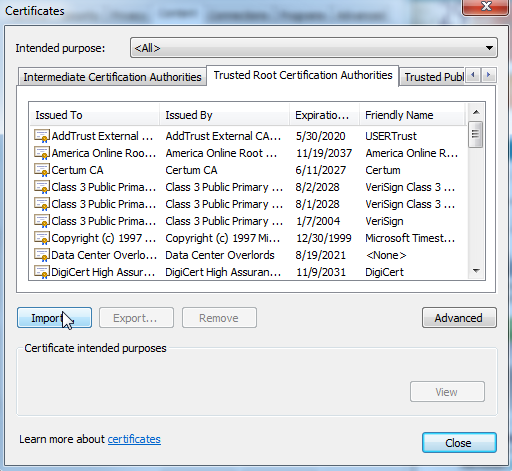
C.A. & Certificates
Root CA certificates are self-signed... trust?
SSL / TLS
PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI
SSL / TLS

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI
Transport Layer Security (TLS 1.3, 1.2, 1.1, 1.0), and its now-deprecated predecessor, Secure Sockets Layer (SSL 3.0, 2.0, 1.0), are cryptographic protocols designed to provide communications security over a computer network

SSL / TLS
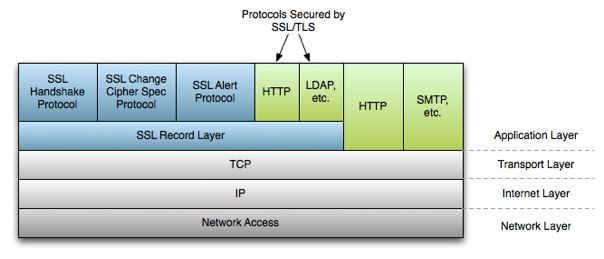
- Certificates are used for server, client or mutual authentication on the SSL Handshake (asymmetric cryptography)
- Supported ciphers and algorithms are negotiated
- Session key is generated and exchanged on handshake
- Symmetric cryptography is used for communication
HTTPS
PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI
HTTPS

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI

Vhosts
PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI
Vhosts

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI
Virtual hosting is a method for hosting multiple domain names (with separate handling of each name) on a single server (or pool of servers)
Port based
IP based
Name based
Name based Vhosts

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI
Use Host: header in HTTP request
Requires HTTP version 1.1 (not a problem)
Name based Vhosts

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI
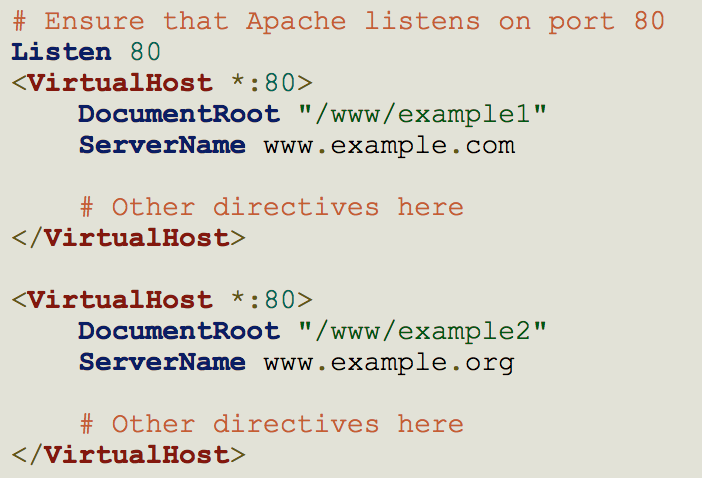
Name based Vhosts

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI
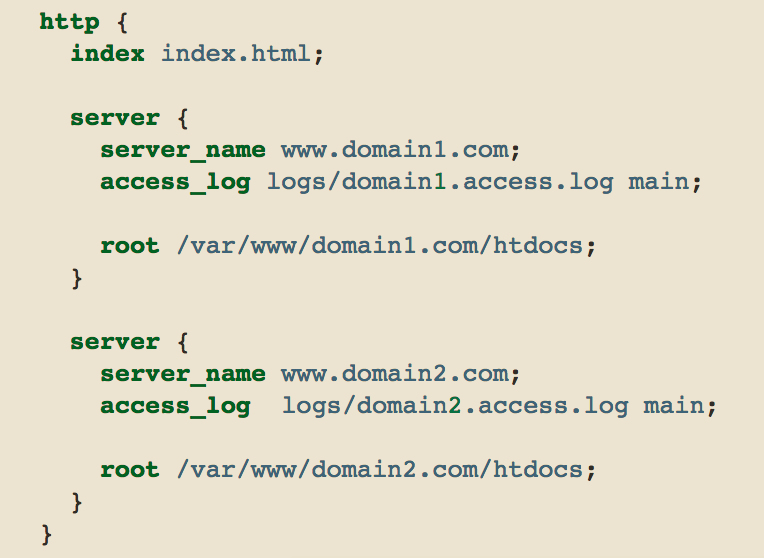
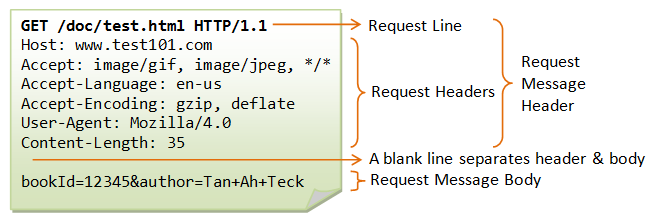
HTTPS and VHosts
IP
TCP
TLS/SSL
HTTPS
Network connectivity
Socket connected
TCP Handshake
TSL Handshake
Certificates exchanged
HTTP Request
HTTP Response
HTTPS and VHosts
IP
TCP
TLS/SSL
HTTPS
Network connectivity
Socket connected
TCP Handshake
TSL Handshake
Certificates exchanged
HTTP Request
HTTP Response
But what vhost? Host: header is in HTTP Request
Welcome SNI!
PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI
Welcome SNI!

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI
Server Name Indication (SNI) is an extension to the TLS computer networking protocol by which a client indicates which hostname it is attempting to connect to at the start of the handshaking process.[1] This allows a server to present multiple certificates on the same IP address and TCP port number and hence allows multiple secure (HTTPS) websites (or any other service over TLS) to be served by the same IP address without requiring all those sites to use the same certificate. It is the conceptual equivalent to HTTP/1.1 name-based virtual hosting, but for HTTPS. The desired hostname is not encrypted in original SNI extension, so an eavesdropper can see which site is being requested
https://en.wikipedia.org/wiki/Server_Name_Indication
Welcome SNI!

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
K8s Ingress
SNI
IP
TCP
TLS/SSL
HTTPS
Network connectivity
Socket connected
TCP Handshake
TSL Handshake
Host name via SNI
Certificates exchanged
HTTP Request
HTTP Response
K8s Ingress
PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
SNI
K8s Ingress
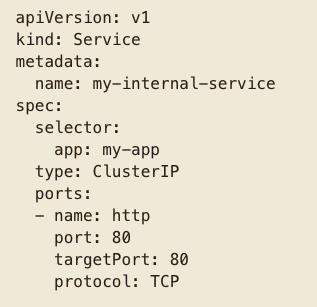
K8s Services - ClusterIP

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
SNI
K8s Ingress
Exposes the service on a cluster-internal IP. Choosing this value makes the service only reachable from within the cluster.
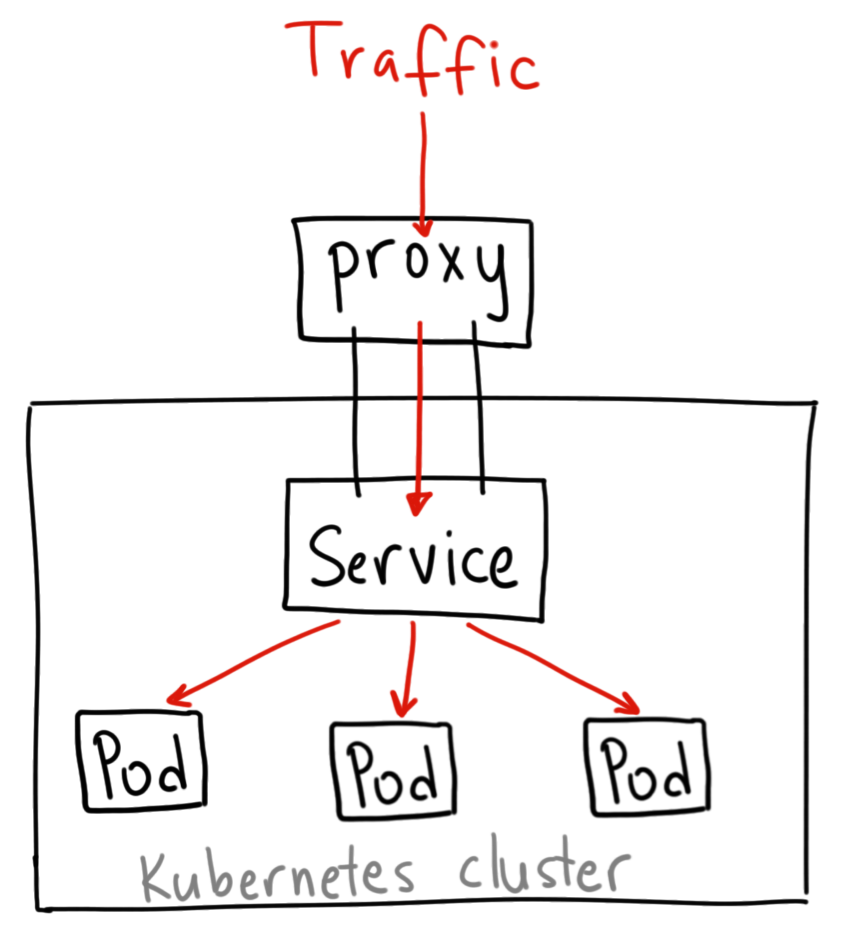
K8s Services - NodePort

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
SNI
K8s Ingress
Exposes the service on each Node’s IP at a static port (the NodePort). A ClusterIP service, to which the NodePort service will route, is automatically created. You’ll be able to contact the NodePort service, from outside the cluster, by requesting <NodeIP>:<NodePort>
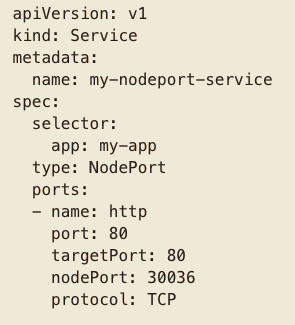
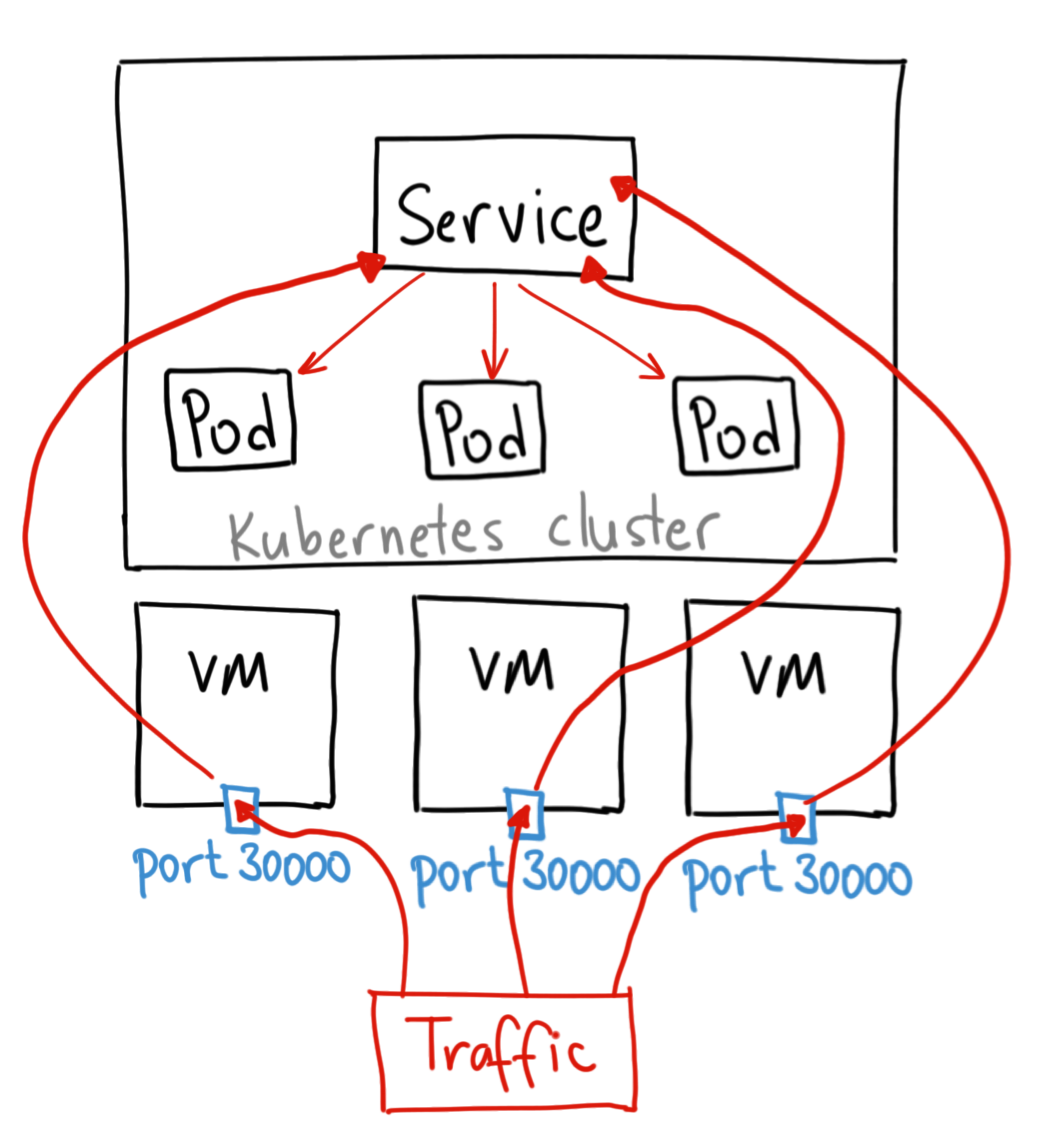
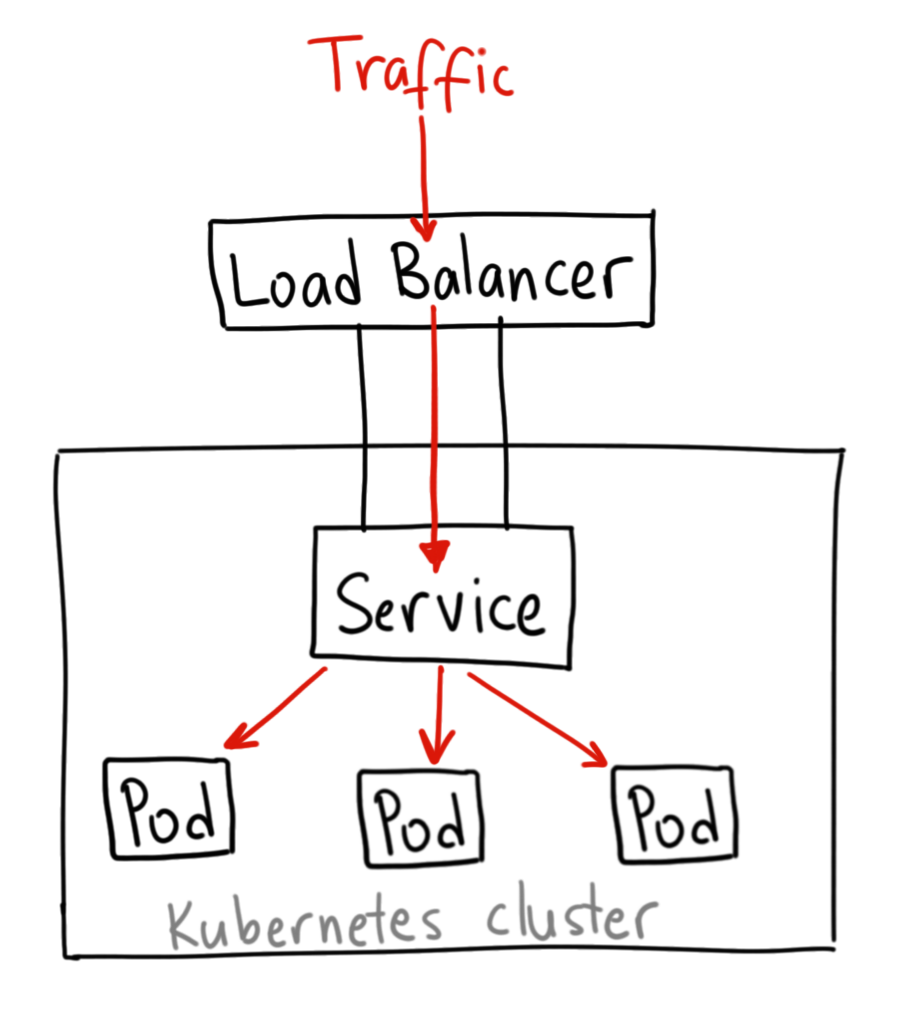
K8s Services - LoadBalancer

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
SNI
K8s Ingress
Exposes the service externally using a cloud provider’s load balancer. NodePort and ClusterIP services, to which the external load balancer will route, are automatically created.
Warning
NOT INCLUDED in K8s. Load Balancer is a service from provider, i.e. AWS, GKE, F5 Load Balancer, etc.
K8s Ingress Controller

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
SNI
K8s Ingress
Ingress exposes HTTP and HTTPS routes from outside the cluster to services within the cluster. Traffic routing is controlled by rules defined on the ingress resource.
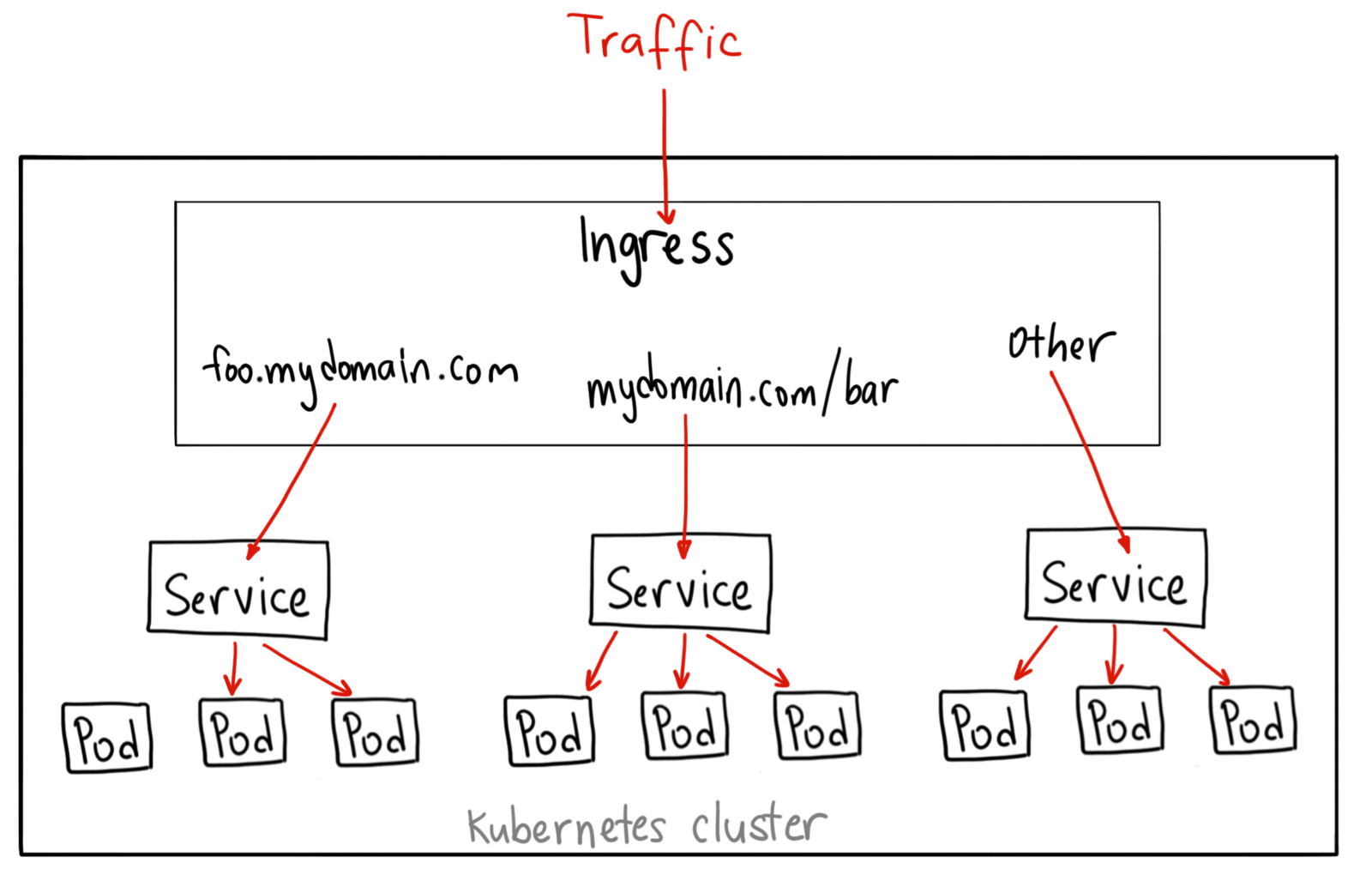
K8s Ingress Controller

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
SNI
K8s Ingress
Kubernetes as a project currently supports and maintains GCE and nginx controllers
NO MAGIC!

K8s Ingress Controller

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
SNI
K8s Ingress
https://kubernetes.github.io/ingress-nginx/how-it-works/
- A simple nginx service on every node
- Reconciliation Loop + K8s API
- Whenever something changes in cluster, nginx.conf is updated and reloaded
- TLS certificates can be set on ingress configuration
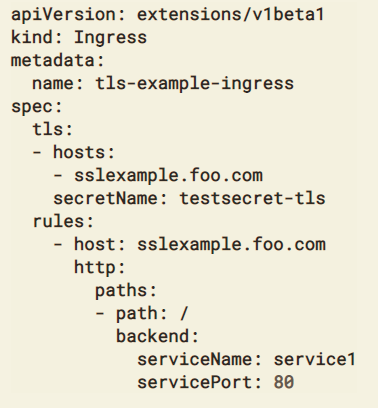
K8s Ingress Controller

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
SNI
K8s Ingress
Other Ingress Controllers
-
Ambassador: Open Source Kubernetes-Native API Gateway built on the Envoy Proxy
-
Contour is an Ingress controller for Kubernetes that works by deploying the Envoy proxy as a reverse proxy and load balancer. Unlike other Ingress controllers, Contour supports dynamic configuration updates out of the box while maintaining a lightweight profile.
- Traefik: A reverse proxy / load balancer that's easy, dynamic, automatic, fast, full-featured, open source, production proven, provides metrics, and integrates with every major cluster technology... No wonder it's so popular!

PKI
CA & Certs
SSL/TLS
HTTPS
Vhost
SNI
K8s Ingress
Security Tangram #1
By Álvaro José Iradier
Security Tangram #1
- 876



