STEGANOGRAPHY 101
ALBERT ZSIGOVITS


steganos (στεγανός):
graphein (γράφειν):
stegosaurus
MEANING
covered, concealed, or protected
writing
What is STEGANOGRAPHY
[~/stego] : This area is about hiding things
SIMPLY PUT?
Covert channel
Network steganography
IN What STEGANALYSIS
DIFFERS?
[~/stego] : Finding the hidden things
[~/stego] : The unsuspicious medium that draws low attention or no eyes at all
Stenography
Cryptography
Terms
Encoding
ENCRYPTION



WHAT IS WRONG WITH
If two knows the same secret, it is highly unlikely that at some point it will not get out
CRYPTOGRAPHY?
Steganography differs from cryptography in that cryptography conceals only the content of the message through encryption. Steganography conceals the presence of the message itself.
(other than NSA introducing backdoor into RSA, but psst....nobody knows that yet)

WHAT IS STEGANOGRAPHY
STRICTLY PUT?
Hide the actual existence of the message not the meaning of the message
Embedding covert communications within seemingly innocuous communications
The art of concealing data in a communication in such a way that only the sender and receiver know of its existance and method of access
(http://forensicswiki.org/wiki/Steganography)
(https://cyber-defense.sans.org/resources/papers/gsec)
(www.garykessler.net/library/fsc_stego.html)
WHAT IS STEGANOGRAPHY
Security via obscurity
WILDLY PUT?
1. Put money in a safe
2. Dig a hole for the safe in a forest
Nobody would suspect that someone would actually hide money in a forest, right?

3. Give specific intructions how to acquire
STEGANOGRAPHY
REFERENCES

PAST
PRESENT
FUTURE
enigma
Herodotus documented one of the earliest examples around 440 BC.

He tells the story of Histiaeus who shaved the head of his most trusted slave and tattooed it.
Once the slave’s hair had grown back, the message was hidden.
When the messenger got to their final destination,
PAST

SHY SHEN
their head would be shaved thereby disclosing the message.
- series of electro-mechanical rotor cipher machines
- polyalphabetic substitution cipher
- cryptographic weaknesses, operator mistakes, allied cryptologists
- HP Printers
- Invisible ink (lemon)
- Operation Shady RAT
- Alureon Trojan
- Russian Spy Case
- Al-Qaeda Capture

PRESENT
(http://www.wired.com/2010/06/alleged-spies-hid-secret-messages-on-public-websites/)
(https://threatpost.com/alureon-rootkit-morphs-again-adds-steganography-092611/75688/)
(http://www.darkreading.com/attacks-and-breaches/shady-rat-hid-malware-in-digital-images/d/d-id/1099530?)
FUTURE
ALIENS

SKA - square kilometre array
VLA - VERY LARGE array
HIDING TECHNIQUES
substitution
cover generation
distortion
statistical
prepending
APPENDING
LSB
WHERE TO HIDE?
THERE:
image
dvdrom
white space
document
natural text
folder
video
web
hidden OS
spam\email
C source code
alternate data stream
tcp\udp packet
HOW TO HIDE?
C2 activity
http://blog.trendmicro.com/trendlabs-security-intelligence/sunsets-and-cats-can-be-hazardous-to-your-online-bank-account/

ANDROID ICON
http://forensics.spreitzenbarth.de/2012/02/03/detailed-analysis-of-android-fakeregsms-b/

WIN FILE ASSOC
http://www.howtogeek.com/127154/how-hackers-can-disguise-malicious-programs-with-fake-file-extensions/



exiftool
DEMO
TIMESHIFTER
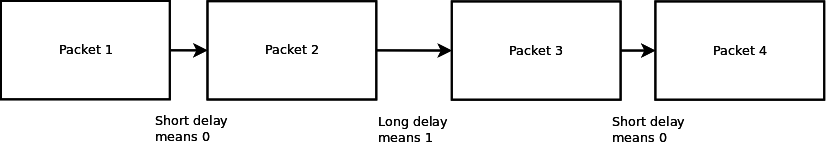
https://www.anfractuosity.com/projects/timeshifter/
RECOMMENDED LITERATURE
DATA hiding
THE CODE BOOK
Decrypted secrets





by Michael RAGGO
by FL BAUER
BY SIMON SINGH
by PETER WAYNER
DISAPPEARING
HIDING IN PLAIN SIGHT
BY ERIC COLE
QUESTIONS?
SECRET
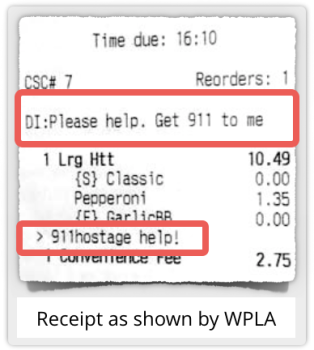
SMWTWWWSPPPFHSWTHACAFWETRHQ
837787848787878380808070728387847265676570876984827281
Steganography 101
By albertzsigovits
Steganography 101
The covert channel
- 528