Internet Security
- Amit Kumar Yadav, Sameer Sengar, Abhishek Bundela
- Computer Science & Engineering
By-

Internet & Network Attacks
- Personal data theft
- Ransomware
- Malicious links
What is Network ???
A network is defined as a group of two or more computer systems linked together. There are many types of computer networks, including the following:
- local-area networks (LANs): The computers are geographically close together (that is, in the same building).
- wide-area networks (WANs): The computers are farther apart and are connected by telephone lines or radio waves.
- campus-area networks (CANs): The computers are within a limited geographic area, such as a campus or military base.
- metropolitan-area networks ( MANs): A data network designed for a town or city.
- home-area networks (HANs): A network contained within a user's home that connects a person's digital devices.
What is network Management ???
- Network management is the process of administering and managing the computer networks of one or many organisations.
- Network management refers to the broad subject of managing computer networks.
IP Address(Internet Protocol address)
- Internet Protocol address, an IP or IP address is a number used to indicate the location of a computer or other device on a network using TCP/IP.
- Example:- 172.16.166.10
Type of IP address:-
- A class ( 0-127) [n . h . h . h]
- B class (128-191) [n . n . h . h]
- C class (192-223) [n . n . h .h]
- D class (224-234)
- E class (240-255
network
Host
Network & Broad Cast address
- 172.16.166.10
Network address : 172.16.0.0
Broad cast address : 172.16.255.255
Private IP Address:-
1. A class:- 10.*.*.*
2. B class :- 172.16.*.* to 172.31.*.*
3. 192.168.*.*
Rest all IP address public
Chocolate task Question
- Find private and public IP address:-
172.16.166.10
16.10.11.12
Time: one minute only


OSI Model
( Open Systems Interconnection )
:: 7 layers in OSI model :-
1. Application layer
2. Presentation layer
3. Session layer
4. Transport layer
5. Network layer
6. Data link layer
7. Physical layer
1. Physical layer:- This layer define the hardware equipment, cabling, wiring, cabling, wiring, frequencies, pulse used to represent binary signals etc. physical layer provides its services to Data-link layer.
2. Data link layer:- This layer is the protocol layer that transfers data between adjacent network nodes in a wide area network (WAN) or between nodes on the same local area network (LAN) segment.
Data link layer
LLC
(Logical link control )
MAC
(Media access control)
3. Network layer :- Network layer that provides data routing paths for network communication.
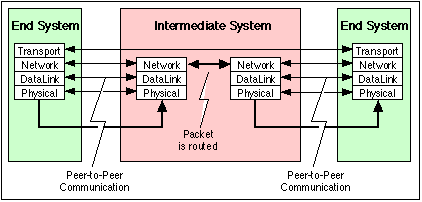
4. Transport layer :- It is responsible for end-to-end communication over a network.
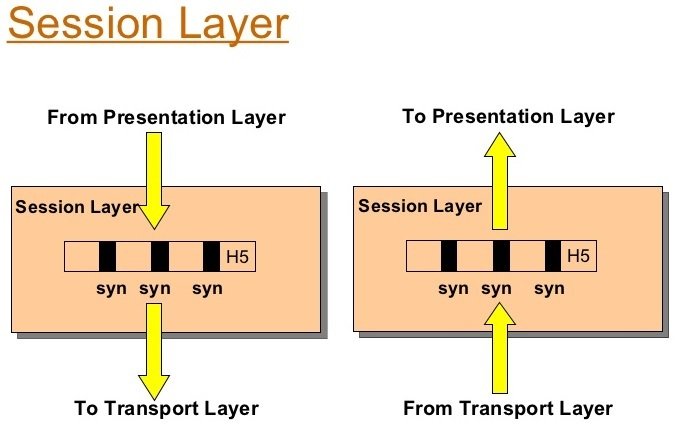
5. Session layer :- The session layer provides the mechanism for opening, closing and managing a session between end-user application processes.
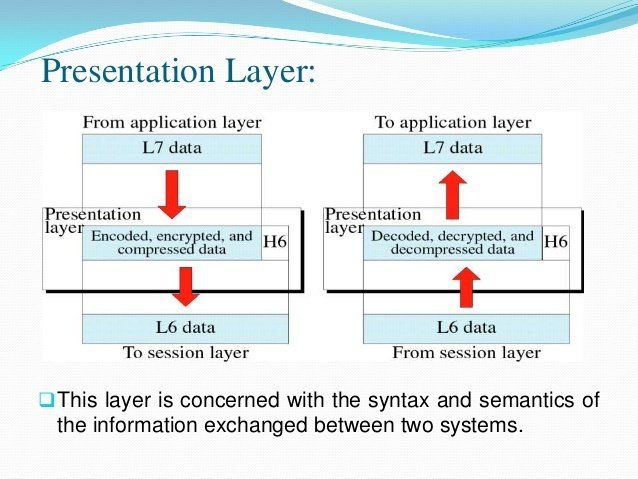
6. Presentation layer :- Presentation layer is serves as the data translator for the network. It is sometimes called the syntax layer.
7. Application :-It consists of protocols that focus on process-to-process communication across an IP network and provides a firm communication interface and end-user services.

Chocolate task Question
- How many numbers of bits and bytes in address:-
IPV6
MAC
Time: one minute only


SOME PORT NUMBERS
| 1. | FTP | 20,21 |
|---|---|---|
| 2. | Telnet | 23 |
| 3. | SSH | 22 |
| 4. | SMTP | 25 |
|---|---|---|
| 5. | DNS | 53 |
| 6. | DHCP | 67,68 |
| 7. | HTTP | 80 |
|---|---|---|
| 8. | HTTPS | 443 |
| 9. | POP3 | 110 |
| 10. | IMAP | 143 |
|---|---|---|
| 11. | SMB | 139 |
| 12. | SNMP | 161 |
WIRESHARK , CRYPTOGRAPHY & PHISHING

Introduction
- Phishing is the act of attempting to acquire information such as username, password and money card details as a trustworthy entity in an electronic communication.
-
Types :- Malware-based, DNS-based, Key-loggers, Screen-loggers etc.
- Gophish.
Introduction

-
Wireshark is an open source software project, and is released under the GNU General Public License.
-
Wireshark is a network packet analyzer.
-
Its originally named Etheral.
PURPOSE & FEATURES
- Capture live packet data from a network interface, Display packets with very detailed protocol information, Search for packets on many criteria.
- And many more…
- It is used for network troubleshooting, analysis, software and communication protocol development.
- A lot more…
Where we get, How installation & use ?

Introduction
- Cryptography comes from Greek kryptós “hidden” + gráphein “write”.
- Cryptography is the practice and study of techniques for secure communication in the presence of third parties (called adversaries).
- Symmetric
• Same key is used by both parties
• Key distribution problem
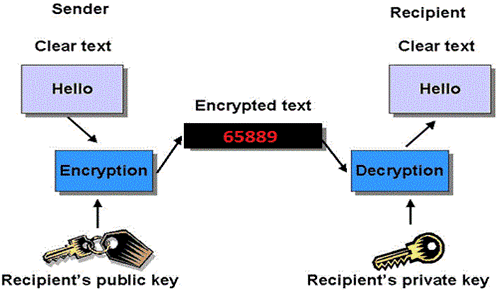
- Asymmetric
• Key pairs for encryption and decryption
• Public and Private Keys
TYPES
Examples and Questions
Decrypt it :- 4 6 7 11 2 9 3 2
CTF
Capture the Flag (CTF) is a special kind of information security
competitions. There are three common types of CTFs: Jeopardy, Attack-Defence and mixed.
Browser Security

"Our Best friend and worst enemy"
Exploiting Browser
Malicious javacript can be used in different ways to
compromise user's data and privacy.
Stegosploit
Tips for secure browsing
- Enable phishing and malware protection
- Configure content settings
- Cookies
- JavaScript
- Pop-ups
- Location
DEEP WEB
The deep web,invisible web,or hidden web are parts of
the World Wide Web whose contents are not indexed by
standard search engines for any reason. The deep web
is opposite to the surface web.
Final Chocolate task Question
1. Total ports possible in TCP/IP
1. 65534 2. 65535 3. 65536 4. 65537 5. 65538
Time: one minute only
2. Decrypt it :-
9996668877700266777793377700444777007774444448
Resources Link :
- https://en.wikipedia.org/
- https://ctftime.org/
- https://www.wireshark.org/
- https://haveibeenpwned.com/
- https://picoctf.com

Thank you
deck
By AMIT KUMAR YADAV
deck
- 1,377



