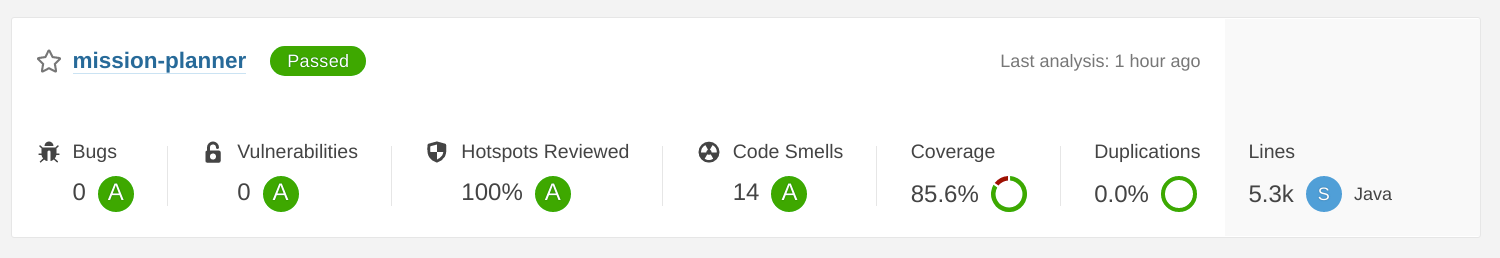
POPC Infrastructure
as GitOps Implementation
GitOps

GIT
Infrastructure as a Code
Terraform
Ansible
Infrastructure as a Code

resource "azurerm_resource_group" "dtm-dev" {
name = "dtm-dev"
location = "West Europe"
}
resource "azurerm_virtual_network" "dtm-dev" {
name = "dtm-dev"
location = azurerm_resource_group.dtm-dev.location
resource_group_name = azurerm_resource_group.dtm-dev.name
address_space = ["10.1.0.0/16"]
}
VM
LB
Resource Group
DevOps
Plan

GIT
push
apply
Container Management

Kubernetes
OpenShift
Rancher
Cloud Foundary
PKS
Container Management
Master
Node
Node
apiVersion: apps/v1
kind: Deployment
metadata:
name: notifications-gateway
labels:
app: notifications-gateway
spec:
replicas: 1
selector:
matchLabels:
app: notifications-gateway
strategy:
type: RollingUpdate
.....apply
Node
Deployment
ReplikaSet
POD
K8S (AKS) Deployment

DevOps

GIT
push
apply
node
node
node

LB
LB
VPN Gateway
AppUser
Dev
internal access
internal access
external access

AKS Plan
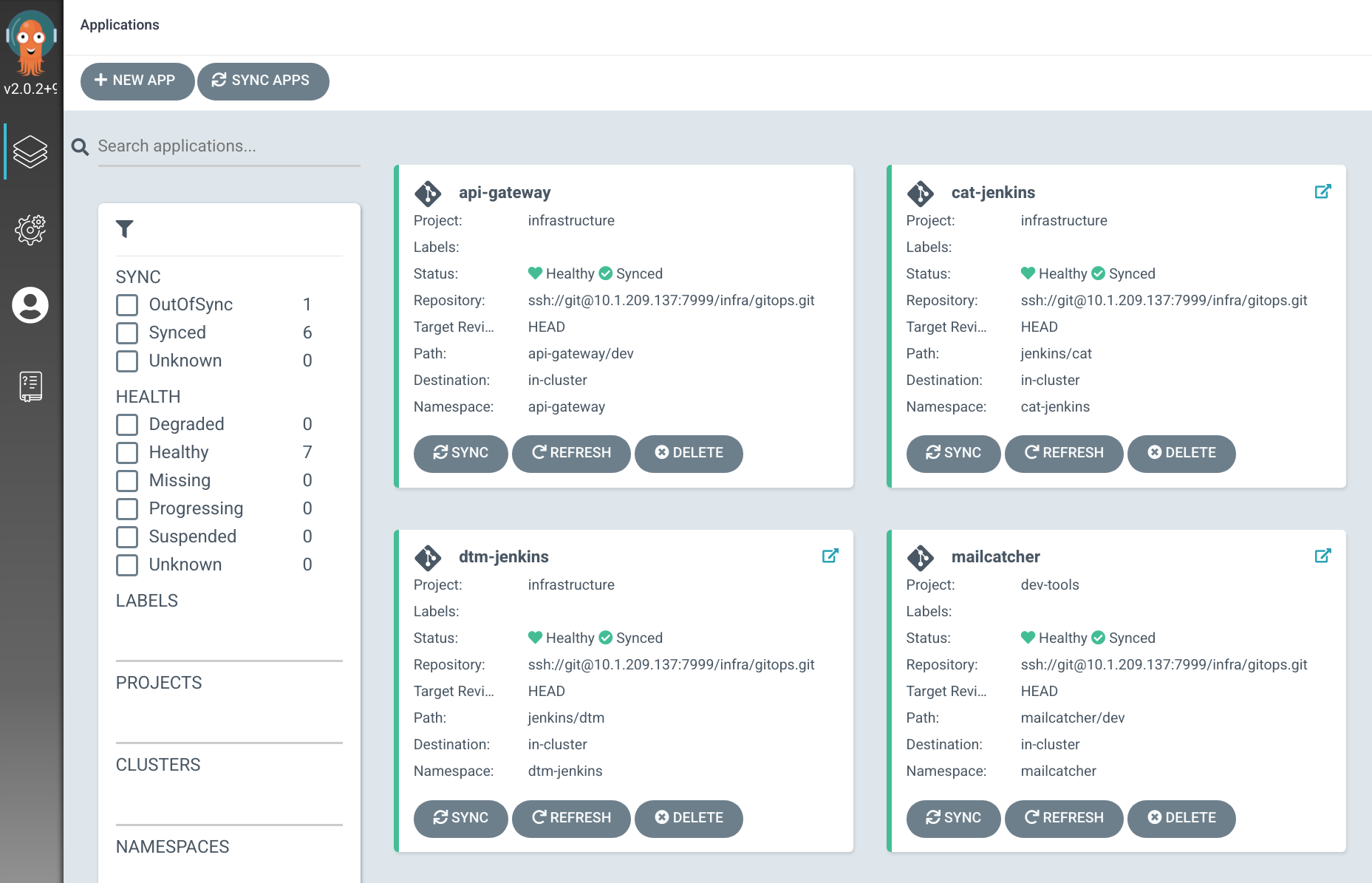
Manage K8S Resources
ArgoCD
FluxCD
Terraform
Ansible
Jenkins X
Manage K8S Resources
DevOps

GIT
node

K8s Resources

push
pull
node
node
synchronize
service
pod
secret

Manage K8S Resources
Manage K8S Resources
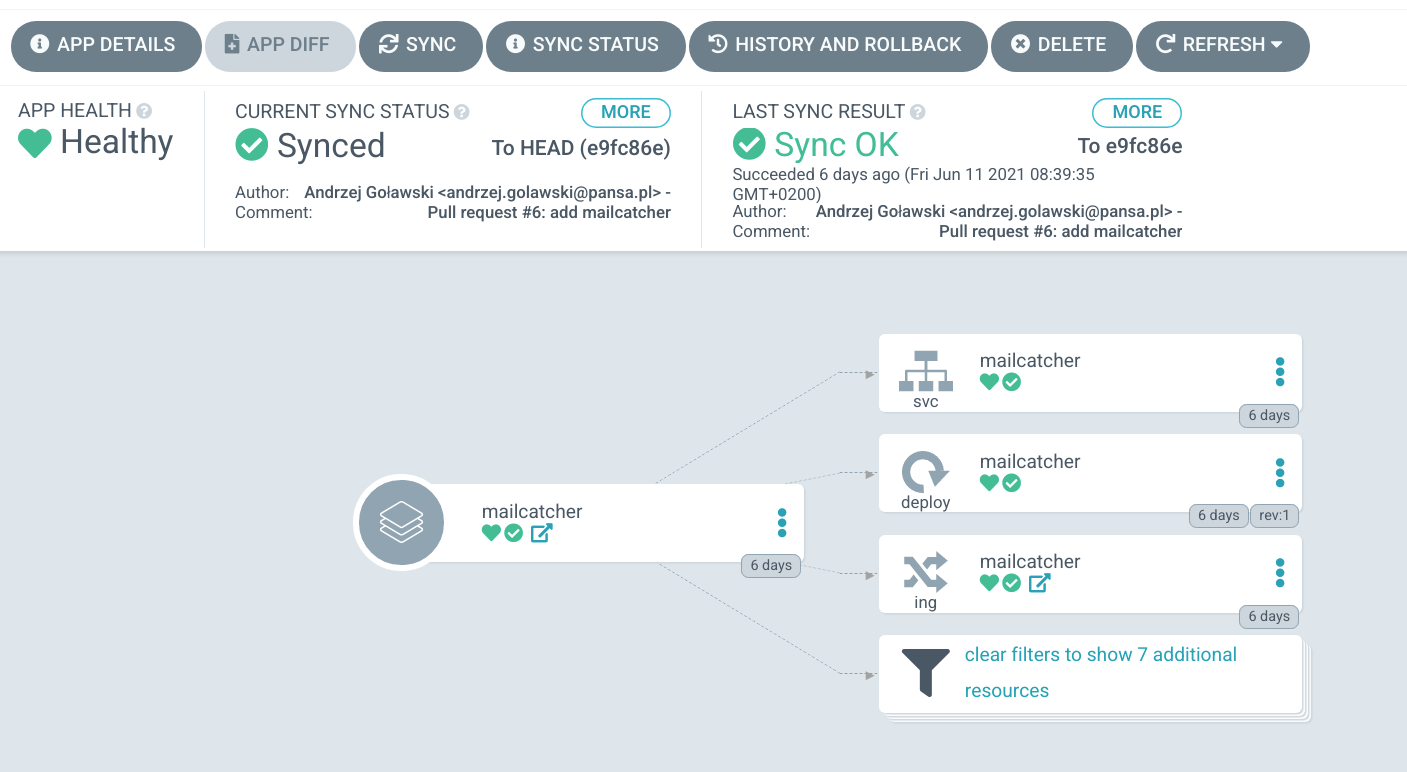
ArgoCD Deployment

DevOps

GIT
push
apply
node
node
node

LB
LB
VPN Gateway

access to ArgoCD

ArgoCD Plan
Logs
GrayLog
EFK (Elasticsearch Logstash Kibana)
ELK (Elasticsearch FluentD Kibana)
Data Dog
Logs
app
fluentD

elastic
kibana
app
fluentD

DevOps
logging
logging
query logs

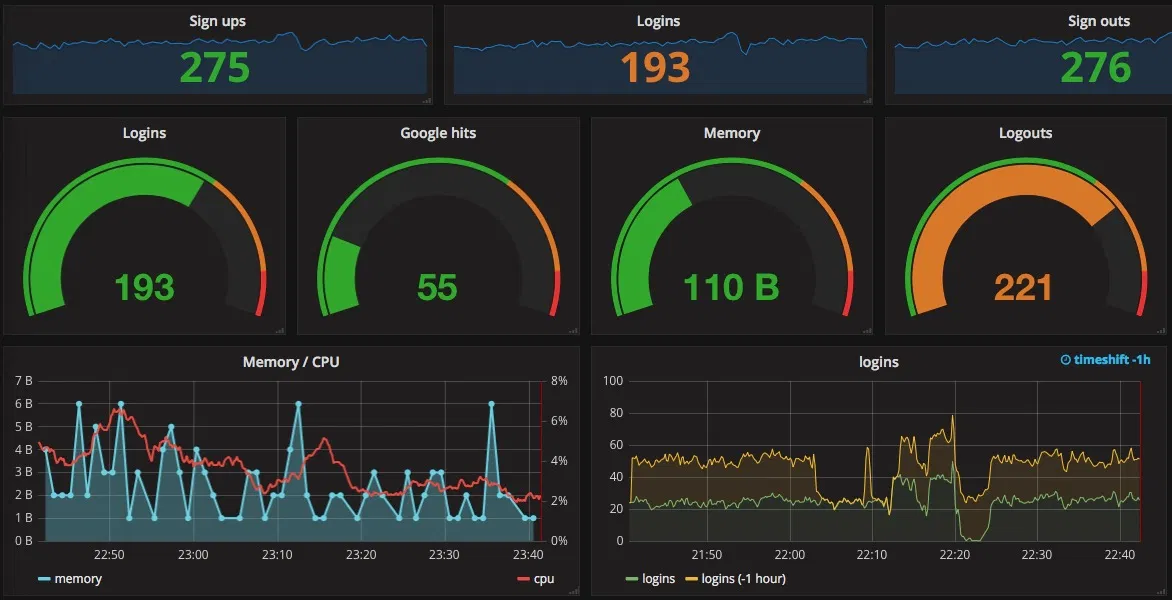
Logs
Metrics
Prometheus
Graphite
Zabbix
Grafana (UI)
Metrics
app
prometheus
grafana
DevOps
query metrics
app
svc
apiVersion: v1
kind: Service
metadata:
annotations:
prometheus.io/scrape: 'true'
prometheus.io/path: '/actuator/prometheus'
prometheus.io/port: '8081'
prometheus.io/scheme: 'http'
labels:
app: notifications-gateway
name: notifications-gateway
spec:
....scrape metrics
app
app
svc
scrape metrics

Metrics

GIT
push

Board Def
DevOps

grafana
board
puller
pull

node
Metrics
Secrets
Vault
Consule
SealedSecrets
Secrets
sealed controller
node
argoCD
sealed secret

GIT

Secret
DevOps
kind: Secret
metadata:
name: rabbitmq
namespace: rabbitmq
data:
password: dmVylY3JldA==
username: cmFml0kind: SealedSecret
metadata:
name: rabbitmq
namespace: rabbitmq
spec:
encryptedData:
password: AgBd6Kf...
username: AgA0KuM7...
template:
metadata:
name: rabbitmq
...
kubeseal

SealedSecret
secret
pull
create
notify
unseale

push
Secrets
node
Vault
DevOps
get secret

init

app
secrets
put secret
Secrets
node
apiVersion: apps/v1
kind: Deployment
metadata:
name: notifications-gateway
labels:
app: notifications-gateway
spec:
template:
metadata:
annotations:
vault.hashicorp.com/agent-inject: "true"
vault.hashicorp.com/agent-inject-secret-smsapi: kube-dev/data/smsapi
vault.hashicorp.com/agent-inject-secret-application.properties: kube-dev/data/rabbitmq
vault.hashicorp.com/agent-inject-template-application.properties: |
{{- with secret "kube-dev/data/rabbitmq" -}}
spring.rabbitmq.username={{ .Data.data.username }}
spring.rabbitmq.password={{ .Data.data.password }}{{ "\n" }}
{{- end -}}
{{- with secret "kube-dev/data/smsapi" -}}
notifications.sms.provider.token={{ .Data.data.token }}
{{- end -}}
vault.hashicorp.com/role: internal-appVault configuration:
CICD
node
Jenkins
Tekton
CircleCi
Jenkins X
Jenkins Configuration as a Code
node

GIT
push

Configuration
DevOps
argoCD
cofig map
pull
create
mount

jenkins

jenkins pod
Jenkins Pipelines as a Code
node

GIT
push

Pipelines
DevOps
pull

jenkins
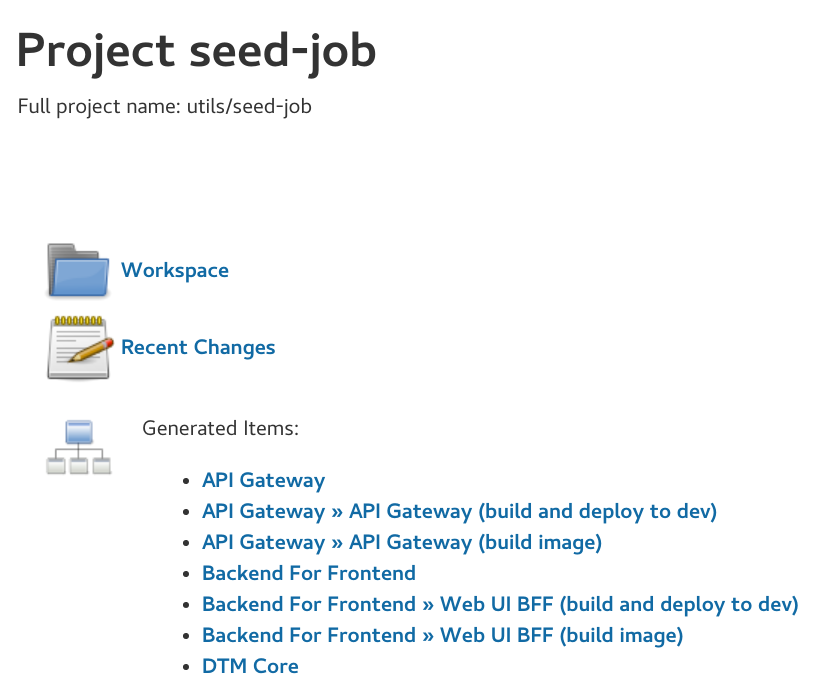
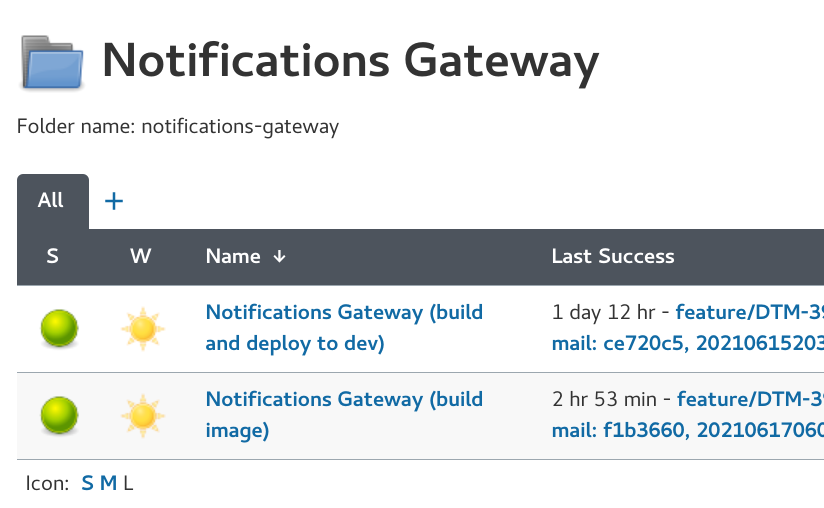
seed-job
CICD
node

GIT
push

code
Dev
trigger



jenkins
worker
creates
clone
build
unit tests
integration tests
check style
archunits
app:1.0
app:master

app
Image Registry
Thank You
DevOps
By andipansa
DevOps
- 253



