What is a secure model for implementing OAuth 2.0 like?
Ari-Pekka Koponen
Version 1.0
THIS PRESENTATION
- Overview: Research question
and contents of the study
- What is authorization?
- How does OAuth 2.0 work?
-
Research method and execution of the study
- Current state of the study
and personal experiences
Overview:
Research question
and
contentS of the study
RESEARCH QUESTION
The aim of the research is to construct a secure model for implementing OAuth 2.0.
In other words to answer the question:
What is a secure model
for implementing OAuth 2.0 like?
for implementing OAuth 2.0 like?
CONTENTS OF THE STUDY
(Development snapshot from 7.4.2014)
- INTRODUCTION
- PREVIOUS WORK
- SECURE AUTHENTICATION METHODS
- OAUTH 2.0 OVERVIEW
- RESEARCH METHOD
- A SECURE OAUTH 2.0 IMPLEMENTATION
- Security features
- Implementation
- Tests
- CONCLUSIONS
WHAT IS AUTHORIZATION?
SITUATION NOW
- A growing amount of data is stored in the cloud and the number of web services is soaring.
- This has created a need for users to authorize third party applications to access their resources.

AUTHORIZATION
- The purpose of authorization is to let users allow third party applications access their resources.
- The OAuth 2.0 authorization framework offers an open and standardized protocol for authorization.
-
OAuth 2.0 is used by e.g. Google, Microsoft and Facebook.
AN EXAMPLE: FACEBOOK CONNECT
-
Facebook Connect is a good example of an implementation of OAuth 2.0: An application is allowed to access e.g. the users email address and posts.

HOW DOES OAuth 2.0
WORK?
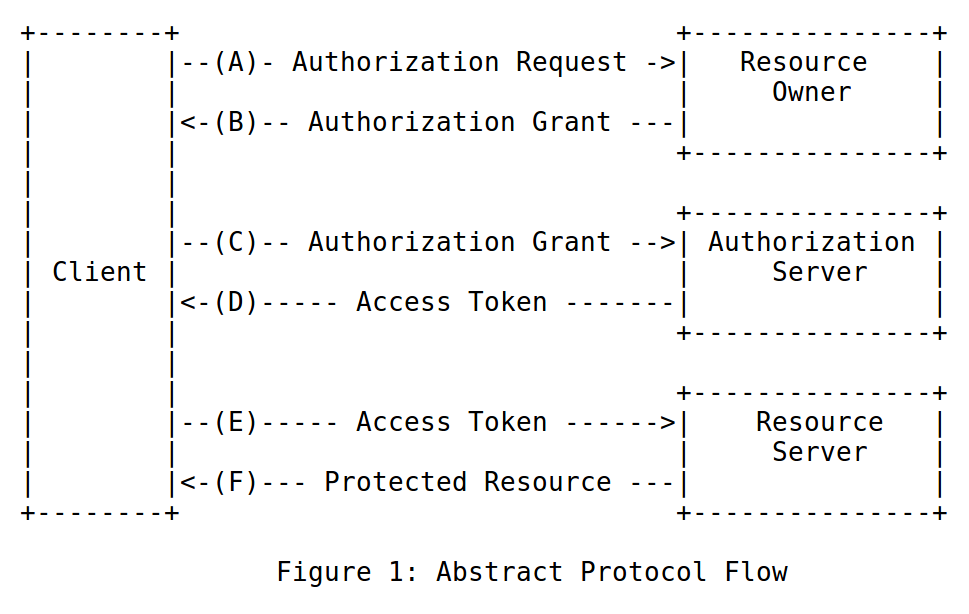
PROTOCOL FLOW
Research method
and execution
of the study
RESEARCH METHOD
The research will take a form of a design-science research study.
EXECUTION OF THE STUDY
- With the help of current literature the features of a secure OAuth 2.0 implementation are identified
- Available libraries for implementing these features are assessed.
- OAuth 2.0 is implemented.
- The security of the resulting implementation is extensively tested and the test results analyzed.
Current state of the study and personal experiences
CURRENT STATE
To-do:
Introduction [x]
The rest [ ]
PERSONAL EXPERIENCE
Most difficult so far:
Finding time and motivation.
Thank You!
Questions?
M. Sc: Secure OAuth 2.0
By apkoponen
M. Sc: Secure OAuth 2.0
Presentation for my Master's Thesis Seminar
- 570