Android Exploitation 101



@Arunthomas115
www.linkedin.com/in/arun1105


@Arunthomas115
www.linkedin.com/in/arun1105

Security Consultant @ IBM


Required Tools & Files
- APKTool
- Dex2jar
- JD-GUI
- Diva.apk
- example_obfuscated.apk
I want everyone of you to reverse the Diva.apk file along with me.
APKTool
APKTool
- APKTool is an open-source tool, specifically built for reversing Android APKs.
- Prerequisite : Java 1.7 or Higher.
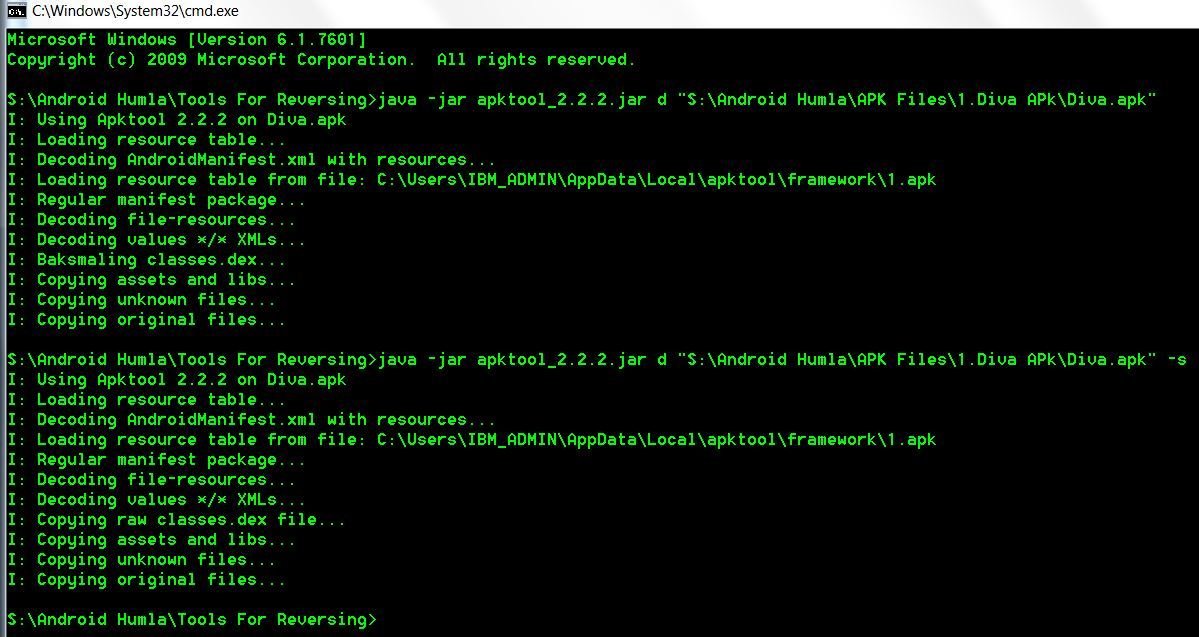
Syntax: java -jar apktool_x.x.x.jar d <.apk file path> -s
d - Tells the tool to decode the APK.
-s - This prevents the disassembly of the dex file and keeps the classes.dex file in the output folder.
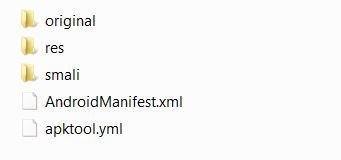
APKTool - Output
- The resulting output will be a directory with the same name as the source APK(Diva).
- During the decoding process, many of the essential files, including images, layouts, strings and xml are brought back to their original form.
- This includes making the AndroidManifest.xml more human-readable.
APKTool is extremly useful, when you don't have access to the original source code, such as during a "Black-Box" security assessment.
Using APKTool we easily reverse the APK to examine the final AndroidManifest.xml file.
APKTool Diff - Output
Dex2jar
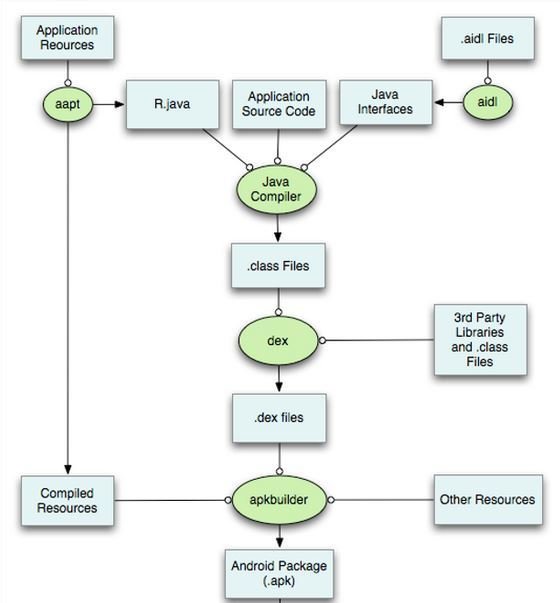
The dex2jar tool is an open-source project for working with .dex and .class files.
For our purposes, we will use it to convert the classes.dex file to a .jar file.
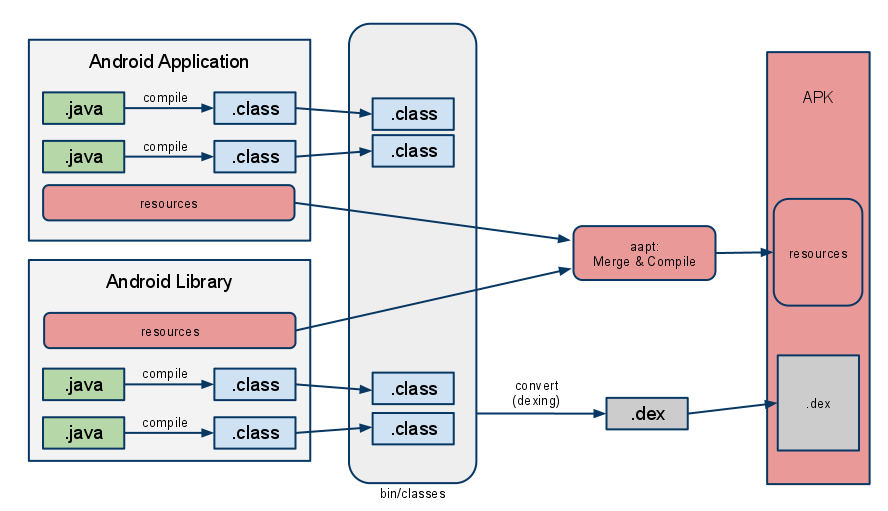
Dex2jar Process
The process of converting from a .dex to a .jar file is important because it allows the use of conventional Java decompiler tools to obtain a code similar to original source code written by the developer.
- Windows Users : You have to use .bat files.
- Linux/Mac Users: Have to use .sh versions.
- Linux/Mac Users : chmod -R 777 dex2jar-2.0
Dex2jar Cmd's
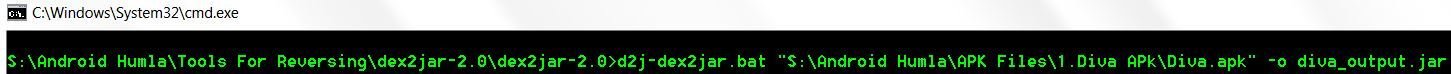
Windows: d2j-dex2jar.bat <.apk file path/classes.dex path> -o <outputfile.jar>
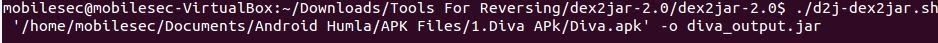
Linux/MAC: ./d2j-dex2jar.sh <../apk file path/classes.dex path> -o <outputfile.jar>
Note:
Sample cmd's
Windows:
Linux/Mac:
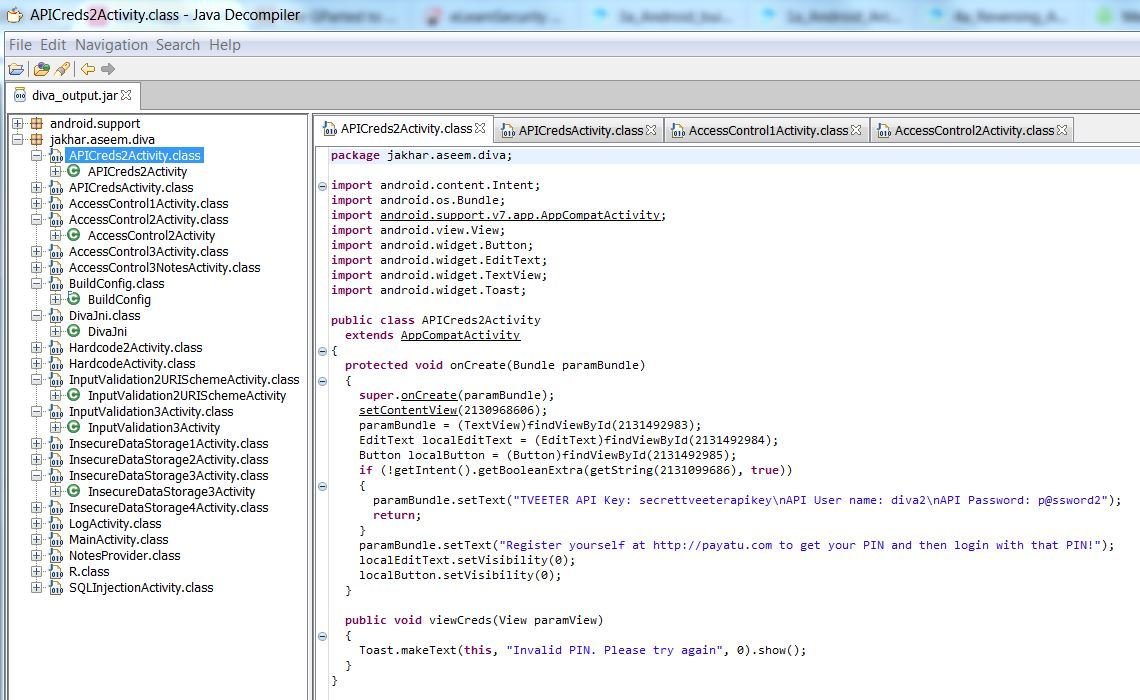
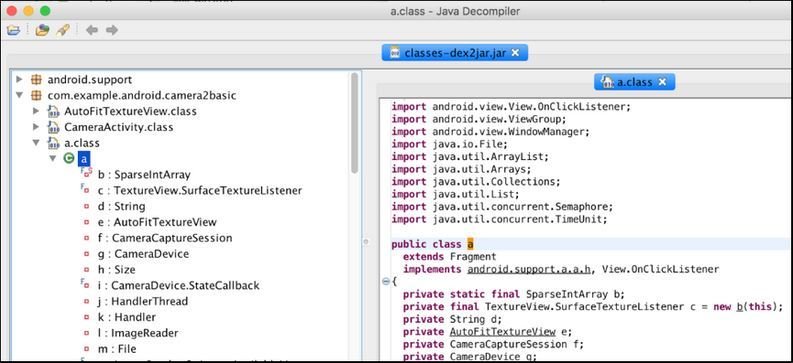
JD-GUI
JD-GUI
JD-GUI is a simple tool capable of decompiling Java .jar files and allows us to browse through the source code of the .class files contained within.
Alternative Tools : Procyon & Fernflower
JD-GUI
Original Code
Decompiled Code
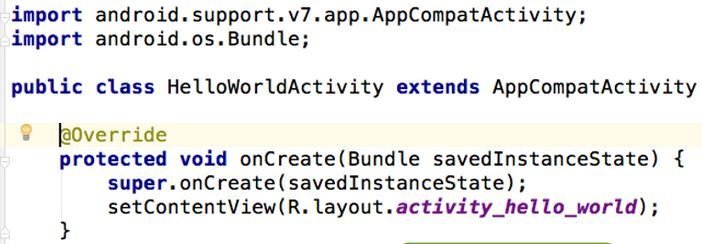
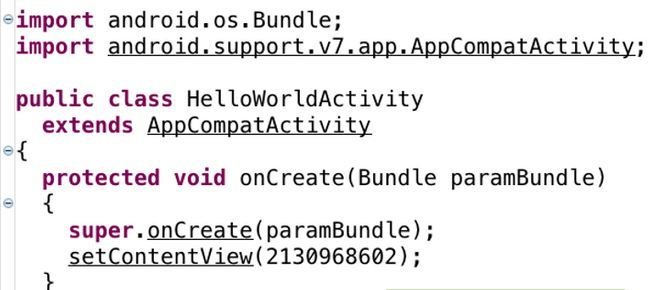
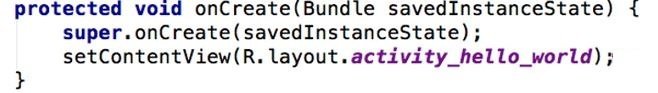
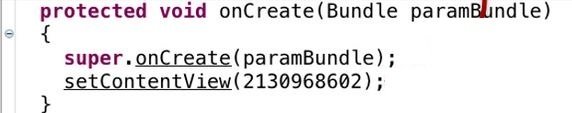
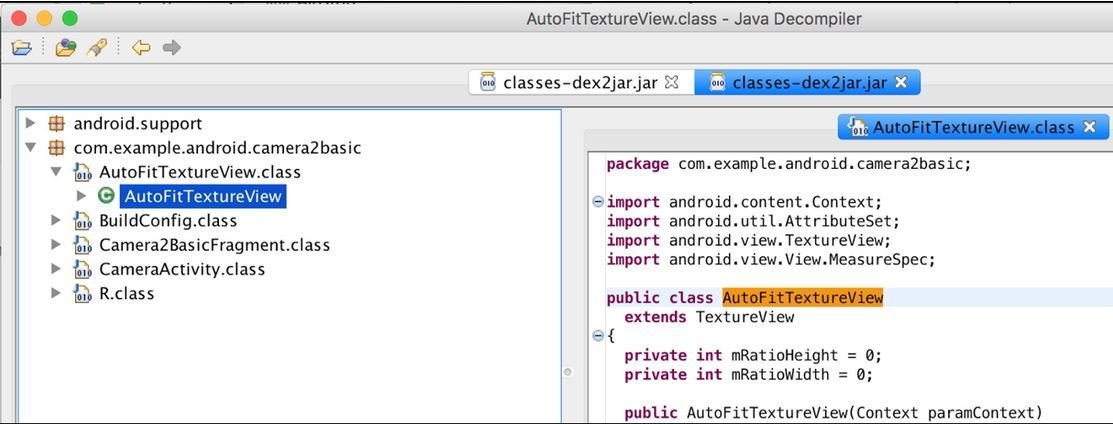
HelloWorld SourceCode
- In the original code the Fullname and Namespace is used, whereas in the decompiled version the value of the resource is specified in R.Class
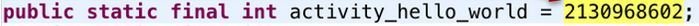
Original Code
Decompiled Code
Ref in R.Class
- It differs only in the resource directives.
Obfuscation
- Obfuscation is the process of intentionally making code harder to read for the purpose of making it more difficult to reverse.
Proguard
- It is usually done by developers wanting to protect their intellectual property, namely the code iteself, but it is also a side effect of optimizing and minifying the code.
- Obfuscation technique makes it harder to reverse an app.
- Proguard can be used to obfuscate the code.
- ProGuard also optimizes the bytecode, removes unused code instructions, and obfuscates the remaining classes, fields, and methods with short names.
Enabling Proguard
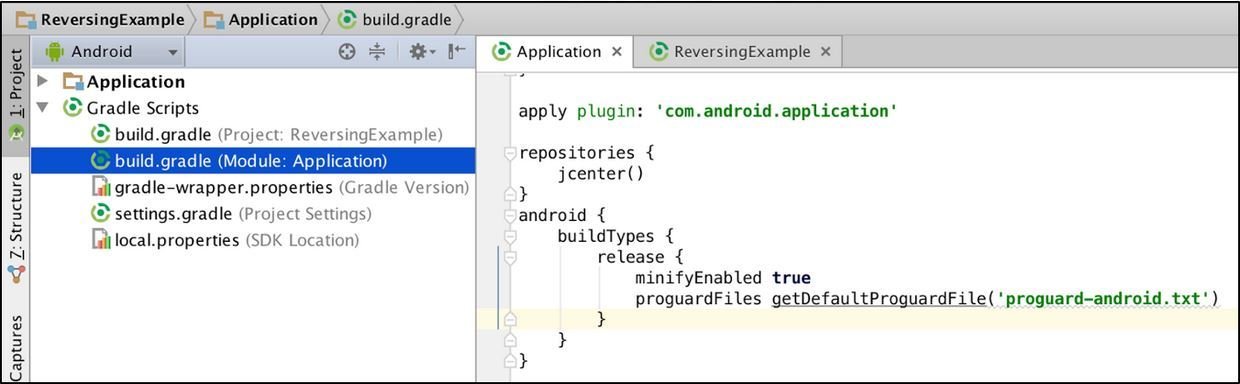
- Proguard will change class,field and method names into meaningless values. You may see names that are single letters, or a couple of letters.
- The purpose is more to remove the meaningful names and make the code smaller, not to "encrypt".
- Gradle is a build system. Build systems are software tools designed to automate the process of program compilation. Build systems come in various forms, and are used for a variety of software build tasks.
- Android Studio uses Gradle, an advanced build toolkit, to automate and manage the build process, while allowing you to define flexible custom build configurations.
What is Gradle?
Proguard Enabled
Proguard Not Implemented
Its time to try it out yourself!!!!
Reverse APK's:
-
Diva.apk
-
example_obfuscated.apk
Static Code Analysis
- Static Code Analysis is a process for programmatically examining the application code on the disk, rather than while it is running.
Static Code Analysis
Tools used for Static Code Analysis:
https://github.com/MobSF/Mobile-Security-Framework-MobSF
- MobSF (Mobile Security Framework)
2.Qark (Quick Android Review Kit)
https://github.com/linkedin/qark
Static Code Analysis Demo
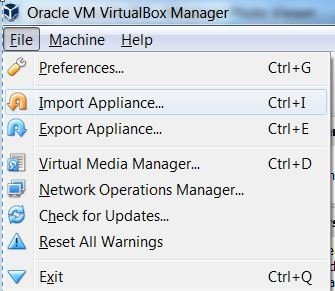
Option: File > Import Appliance > Browse and select the Null Humla.ova file
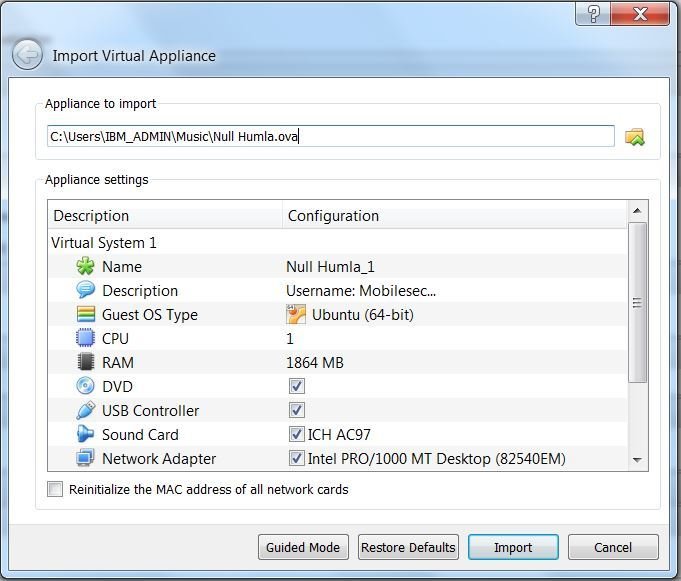
Step 1. Start the virtual machine and initiate the MobSF server using the following command;
#cd /home/mobilesec/MobSF/
#python manage.py runserver
Step 2. Access the MobSF Framework using the URL;
http://localhost:8000
Step 3. Upload any .apk file to initiate the scan from the following path;
/home/Documents/Android Humla/APK Files
MobSF
Qark
Step 1. Initiate the qark using the following command;
#cd /home/mobilesec/qark-master/qark
#python qarkMain.py
Step 2. Select option 1;
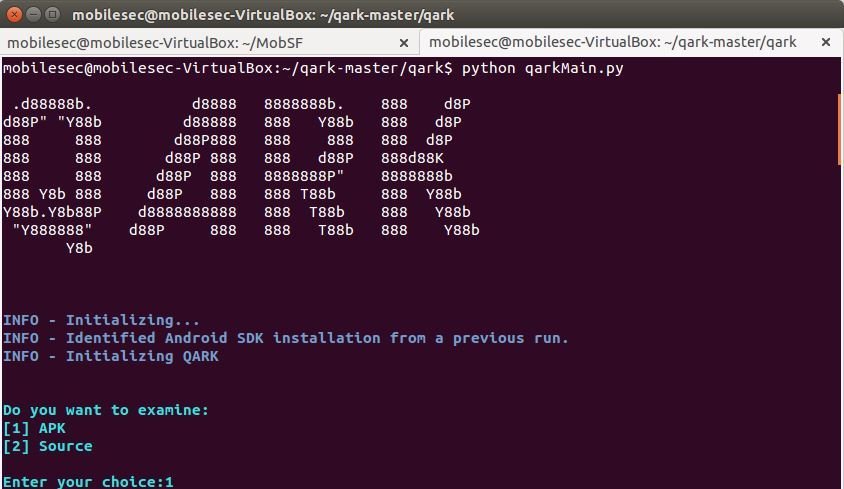
Qark
Step 3. select the path to the .apk file
/home/Documents/Android Humla/APK Files/1.Diva APk/Diva.apk
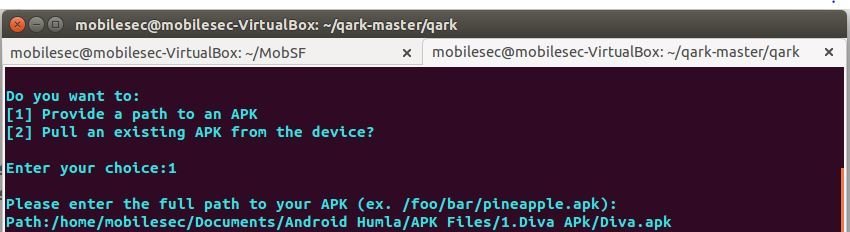
Qark
Step 4. select option 1 - to generate a custom APK for exploitation & Option 2 to exit and generate the scan report.
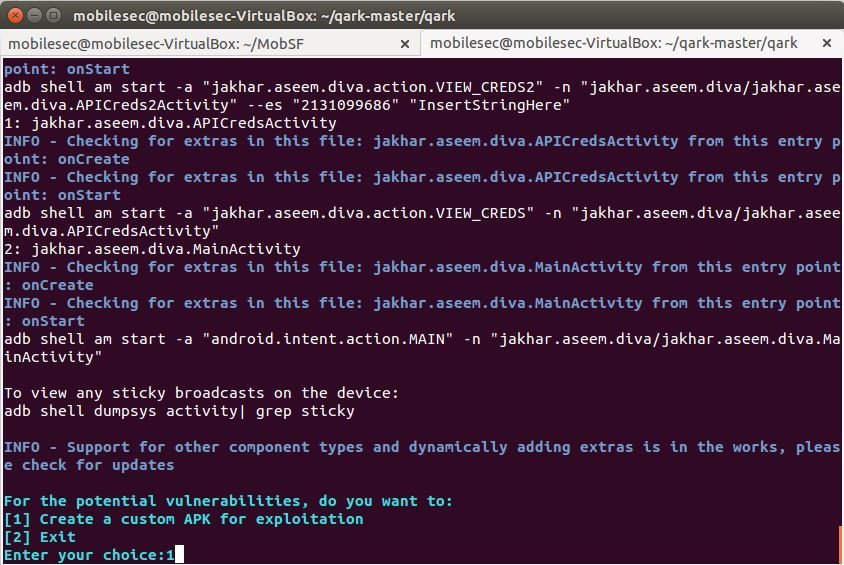

Qark
Step 5. View the scan report from the below shown path;

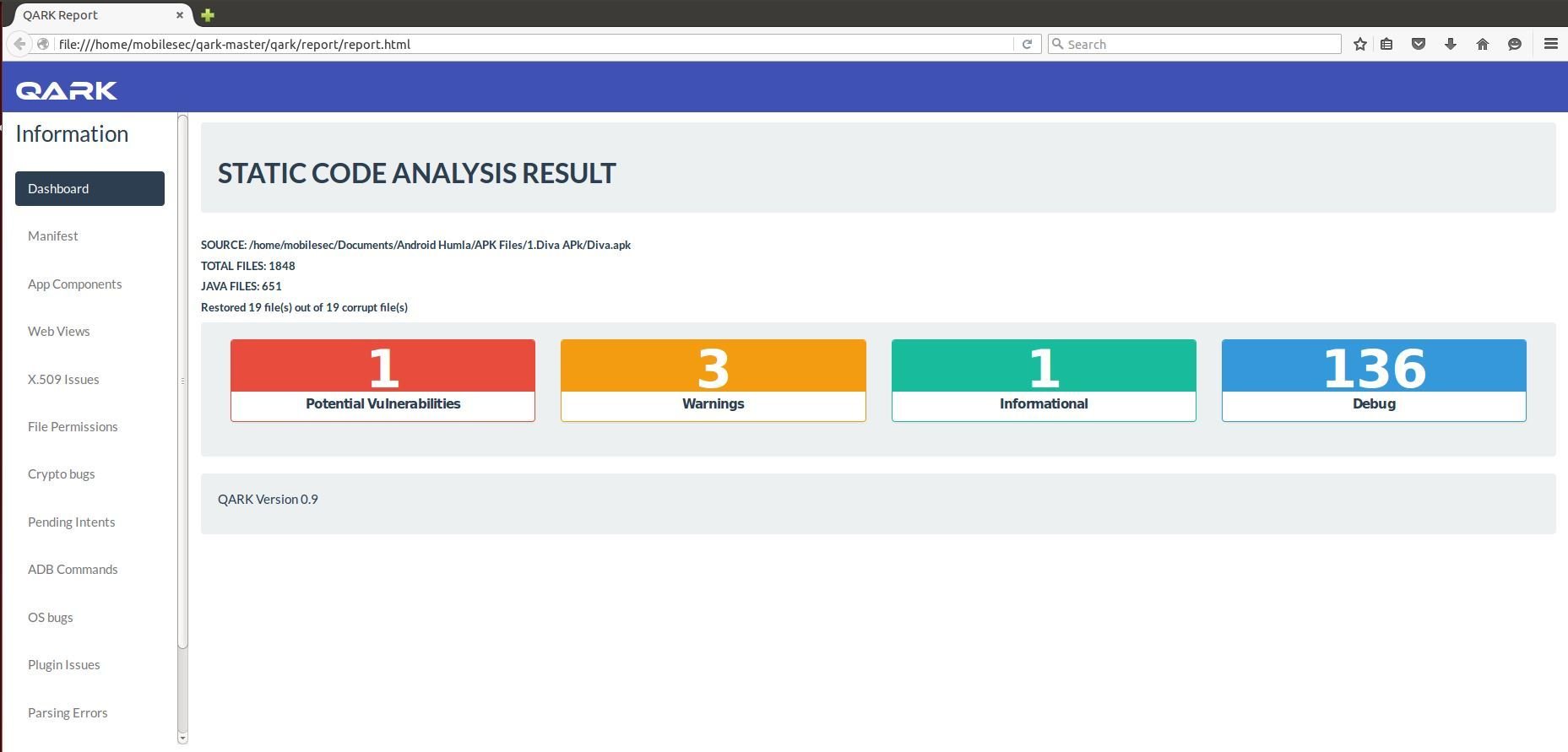
Dynamic Code Analysis
Dynamic Code Analysis
- Dynamic Code Analysis is the process by which code is reviewed for vulnerabilities by executing some or all of the code.
- This execution can occur in a normal environment, virutalized environment or in a debugger.
Dynamic Code Analysis Tools & Setup
1) MobSF - Dynamic Analyzer
- https://github.com/MobSF/Mobile-Security-Framework-MobSF/wiki/1.-Documentation
2) Droid Box
https://code.google.com/archive/p/droidbox/
3) NowSecure Mobile Appsec Toolkit

Any Questions?

Copy of Android Humla - Reversing APK's & Static Code Analysis
By Arunthomas
Copy of Android Humla - Reversing APK's & Static Code Analysis
- 816


