IoT Pentesting
Arun.S
Security Consultant @ IBM
Email : aruns014@in.ibm.com
What can be expected in the future with IoT ???





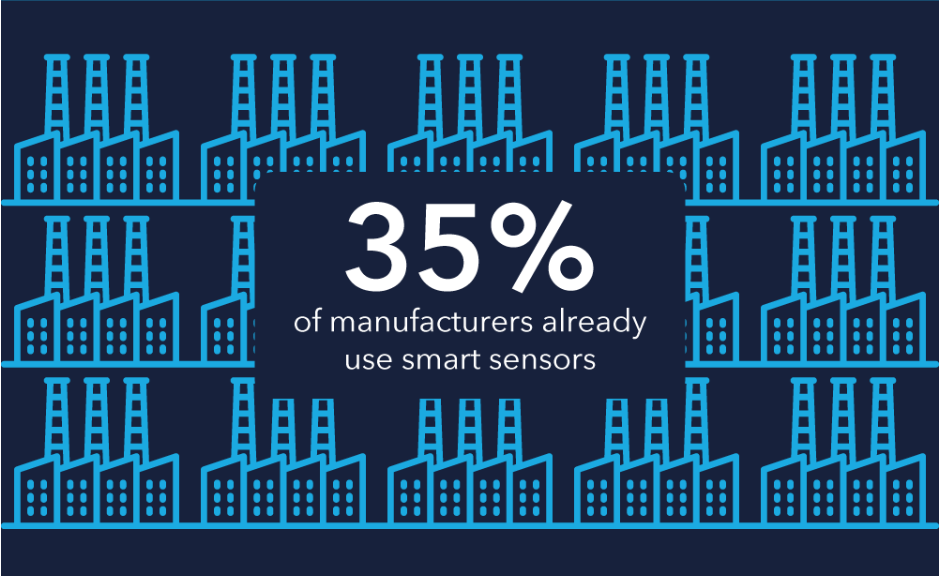

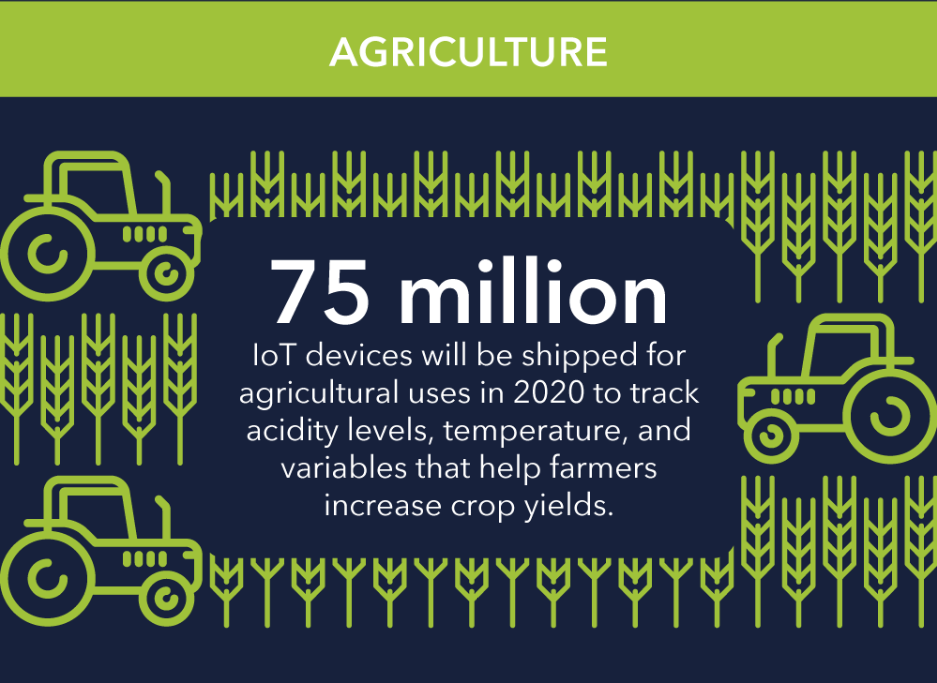
Let's see some products which already available in online !!!!



What about the security ???
What Needs to be Secured?
-
Misconception - IoT Security is != Device Security.
Hardware

Web/Mobile Interface

Communication Channel
- But, we can categories it as follows;
- There are many surface areas which needs to be evaluated for IoT Security.
Hardware Security?
- Embedded|H/W devices are often prone to numerous vulnerabilities.
- Firmware : A type of software that provides control, monitoring and data manipulation of engineered products and systems.
- It is held in Non-Volatile memory devices such as ROM, EPROM, or Flash memory.
- It is bit easy to reverse a Firmware for analyzing with the help of tools like binwalk/FirmwareModKit etc.,
- Firmware can be dumped cloned and backdoored as well.
Web/Mobile Interface Security?
Webapplication security Issues - OWASP Top 10 WebAppSec
Mobile Application Security Issues - OWASP Top 10 MobileAppsec
https://www.owasp.org/index.php/Top_10_2013-Top_10
https://www.owasp.org/index.php/Mobile_Top_10_2016-Top_10
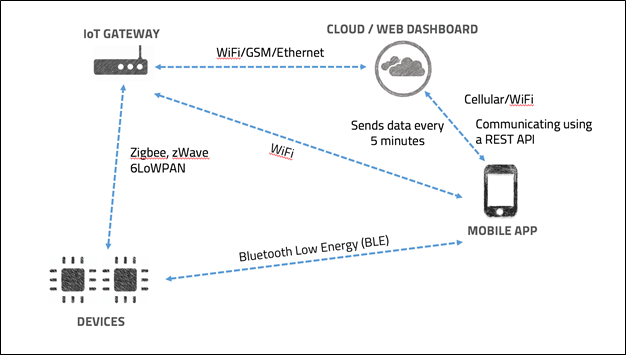
Communication Channel Security?
- Communication between the IoT products can happen through various channels.
- Commonly Used Communication Channels are:
- IoT devices are built upon really available components which are often insecure.
- Wireless
- Bluetooth Low Energy(BLE)
- Zigbee
- NFC
- RFID
So how to map the attack surface?
Mapping the Attack Surface
OWASP - IoT Top 10
- I1 : Insecure Web Interface.
- I2 : Insufficient Authentication/Authorization.
- I3 : insecure Network Services.
- I4 : Lack of Transport Encryption/Integrity Verification.
- I5 : Privacy Concerns.
- I6 : Insecure Cloud Interface.
- I7 : Insecure Mobile Interface.
- I8 : Insufficient Security Configurability.
- I9 : Insecure Software/Firmware.
- I10 : Poor Physical Security.
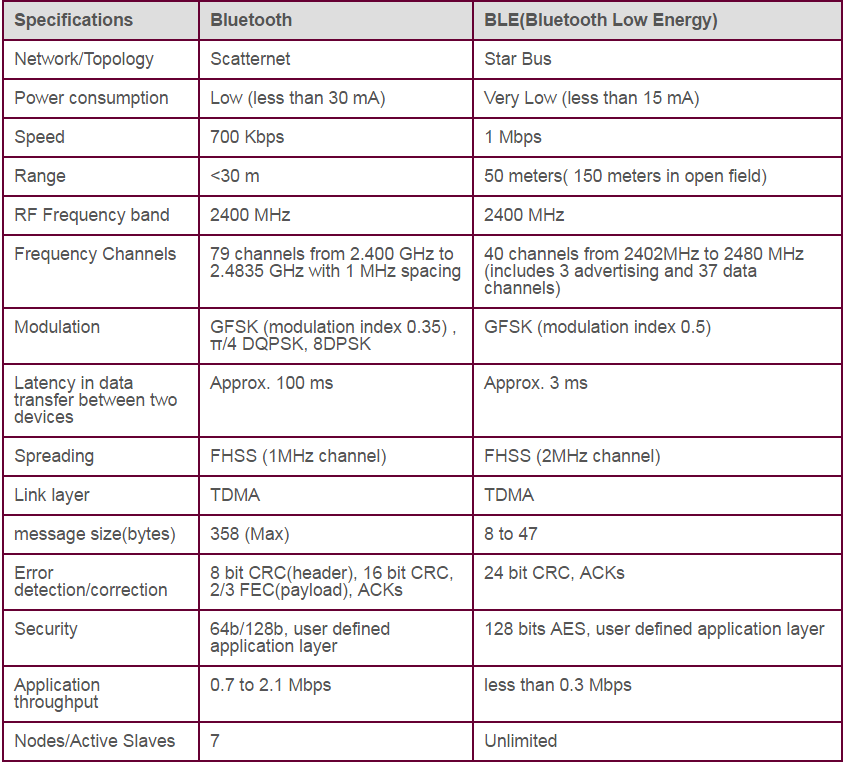
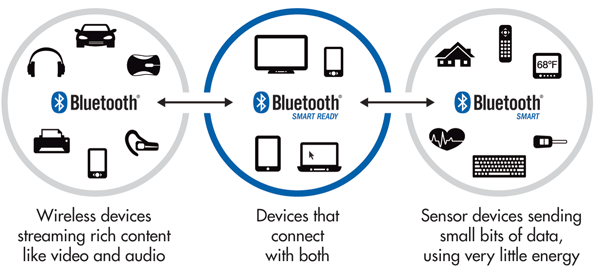
Bluetooth Low Energy
Bluetooth Low Energy
-
BLE is mainly used/preferred for low-resource consumption devices(Specs include running on a single battery coin for months-years).
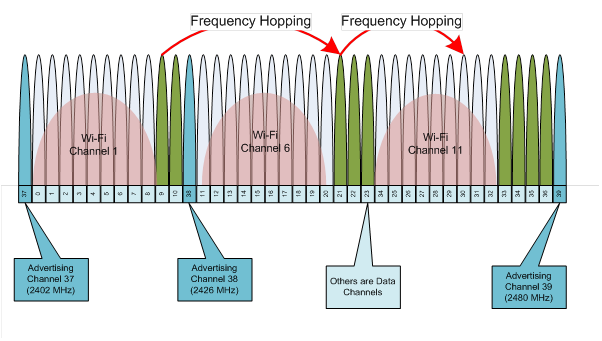
Two types of channels:
- 37 Data Channels
- 3 Advertisement broadcast channels
- BLE uses the Attribute protocol.
Bluetooth Vs BLE
Wifi Vs BLE
- Wifi works on 2 spectrum ranges - 2.4 GHZ and 5GHZ(New one)WiFi.
- 2.4 GHz wifi will support up to 450Mbps or 600Mbps depending on the class of the router. 5Ghz wifi will support upto 1300Mbps.
- When configuring three different WiFi networks the best solution is to use channels 1, 6 and 11. This helps to avoid the interference with Bluetooth Smart and between themselves.
- Other channels: 2, 3, 4, 13, 14 might cause interference with Bluetooth signal and it’s best to avoid them.
Are You an IoT
User?
What are all the ways a hacker can hack you ???
Some Interesting BLE Hacks



How does the mobile identify the exact BLE device to communicate with?
- By default every BLE devices will have a BLE ID/Bluetooth Address which is shown/advertised for us to find in our Mobile/Laptop.
- Devices use the custom service UUID to find the exact devices it wants to talk to and filter out other devices.
How the Connection is Established?
- Services, Characteristics and other things use UUID to uniquely identify each BLE Devices.
- Splitted as 4-2-2-2-6.
Device Roles
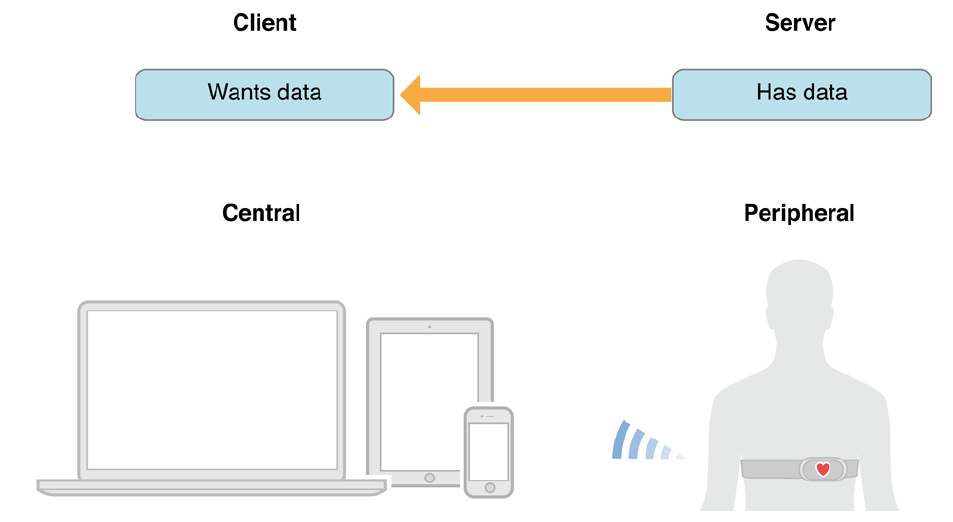
GAP - Generic Access Profile
- GAP Identifies what are the different roles are present in each devices.
- It is used to find which device acts as a broadcaster and receiver .

- GAP controls the connections & Advertising.
- Note: The Peripherals stops advertising as and when the communication is established.
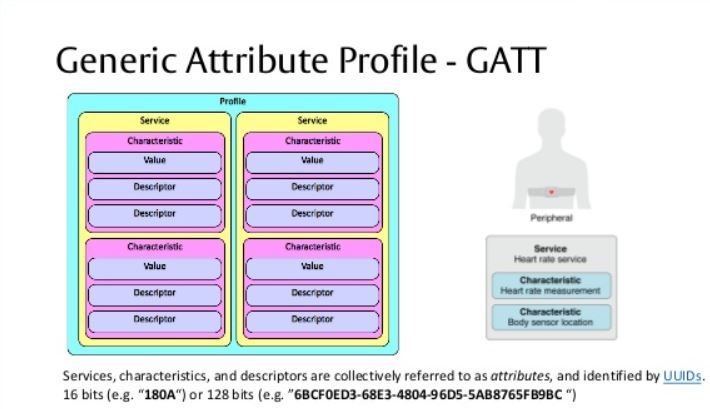
GATT - Generic Attribute Profile
- GATT defines the communication semantics between the client and server.
-
Uses concepts called Profiles, Services and Characteristics.
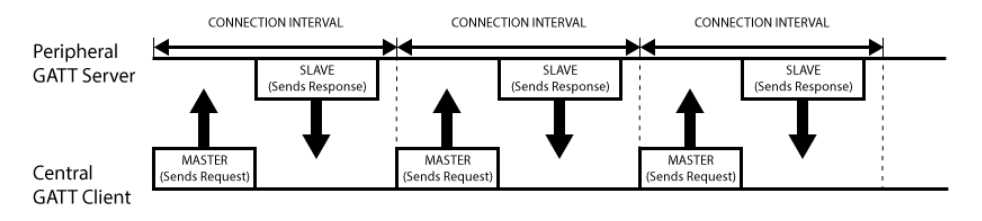
- Stores Services,Characteristics in lookup table using 16-bit ID's for each entry.
-
UUID Format
16-bit - officially adopted Bluetooth Services/Characteristics.
128-bit - Custom defined services/characteristics by vendors.
Prerequisites



Syska Rainbow - Smart LED
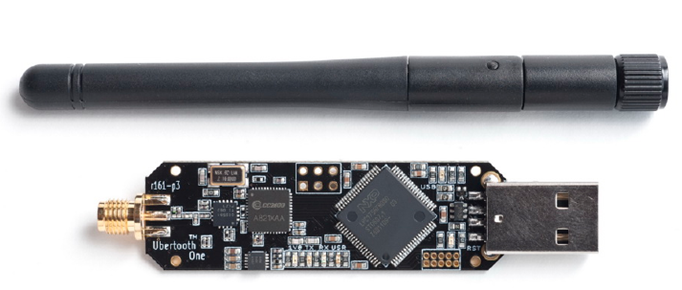
Ubertooth One
- Bluetooth Sniffer and injector.
- 2.4 GHz transmit and receive capabilities.
- Open source.
- By Michael Ossmann.
- Cost - 120$
- Easily integrates with Wireshark.
BLE 4.0 - nRF51822 - V3.0
- Bluetooth Adapter
- 2.4 GHz transmit and receive capabilities
- Supports BLE 4.0
- Freely Available on online shopping sites
- Cost effective compared to Ubertooth, Comes in 24$ -25$
- Easily integrates with Wireshark.

CSR Bluetooth Adapter
- Bluetooth Adapter
- 2.4 GHz transmit and receive capabilities
- Supports BLE 4.0
- Freely Available on online shopping sites
- Low cost effective, Comes in 4-8$
- Easily integrates with Wireshark.

BLE Vulnerabilities
- MITM
- Data being transmitted in clear text which could be sniffed.
- Using hcidump to dump all the communication between the phone(android) and the bluetooth device/chip.
- Advertisement spoofing leading to DoS - device not being able to scan the cloned device for services or the services doesn't respond.
- Replay based attacks
Pairing Modes
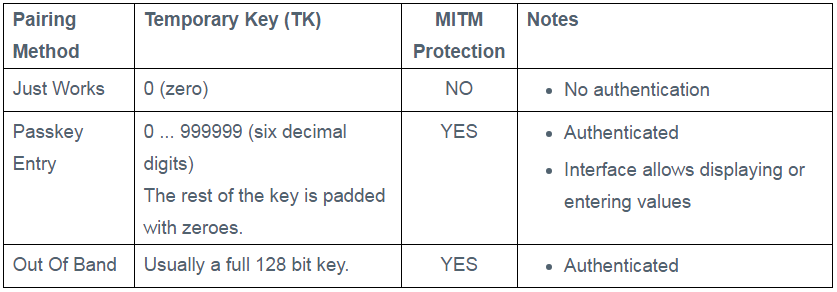
Pairing Modes
- Out of band : Still not widely used(Its a Secure way) - Sending the passkey via NFC(But requires NFC Transceivers).
- Note: My current demo is based on the first mode.
- JustWorks : TK(Temporary Key) all are Zeroes (000000).
- 6-digit passkey : 0-999,999 : can be bruteforced using tools such as Crackle.
(So only by entering the passkey the comm/Connectivity between the 2devices starts)
Decrypting the 6-digit passkey using Crackle
- 6-digit passkey : 0-999,999 : can be bruteforced using tools such as Crackle.
- Crackle by Mike Ryan - https://lacklustre.net/projects/crackle/
- Extract TK,STK(from TK and pairing data), LTK(from STK and key exchange)
- By obtaining the LTK we can decrypt the encrypted .pcap file

How did the color changed Just by Changing the Hex Values????
Lets see with our example Hex Value
Dissecting - Hex Code used for changing the LED Colour to RED
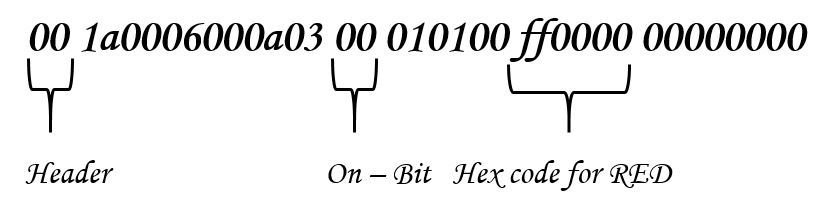
- We can perform fuzzing on the R/B/G Hex Code to change the color of LED to any desired color.


deck
By Arunthomas
deck
- 581


