Metasploit DB Usage



Arun.S
Security Analyst @ Capgemini
Please Don't Expect
- How to Evade Firewalls & Antivirus
- How to do Privilege Escalation
- How to do Pivoting & Port Forwarding
- How to do Post Exploitation etc..,
TOC
- Metasploit Basics
- Initial Setup & Workspaces Configurations
- Importing & Exporting Scan Results
- Hosts & Services
- Setting up Modules
- CSV Export
- Creds & Loot.
Metasploit Basics
Metasploit
Not Just a Tool
An Entire Framework for Automating various tasks for Penetration Testing / Attacking
Metasploit Filesystem
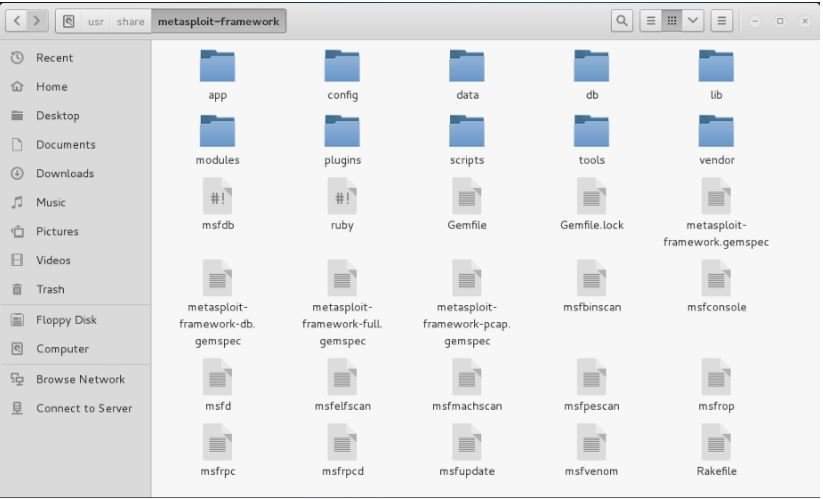
MSF File Architecture
- Data: editable files used by Metasploit.
- Documentation: provides documentation for the framework.
- External: source code and third-party libraries.
- Lib: the 'meat' of the framework code base.
- Modules: the actual MSF modules.
- Plugins: plugins that can be loaded at run-time.
Metasploit Basics
Metasploit Modules
Metasploit Interfaces
- Exploits
- Auxiliary
- Payloads
- Encoders
- Nops
- MSF CLI (Discontinued)
- MSF CONSOLE
- MSF WEB (Discontinued)
- ARMITAGE
- Metasploit Pro
Metasploit Modules
Exploits - Modules used for actually attacking the systems and grabbing the access.
Auxiliary - Exploit without payload. Used for scanning,Fuzzing & doing various tasks.
Payloads - A piece of code which executes on remote system after successful exploitation.
Encoders - Program which encodes our payload to avoid antivirus detection.
Nops - Used to keep payload size consistent.
Metasploit Interfaces - MSFCONSOLE
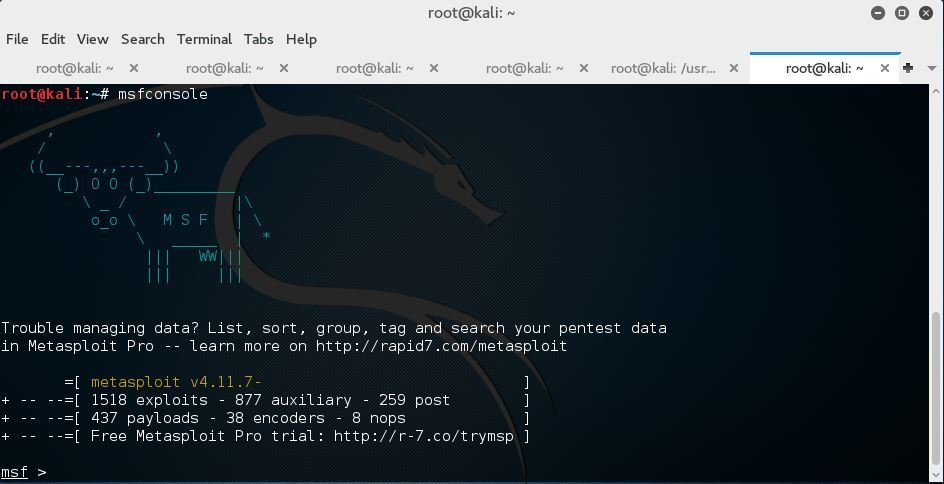
Metasploit Interfaces - MSFCLI
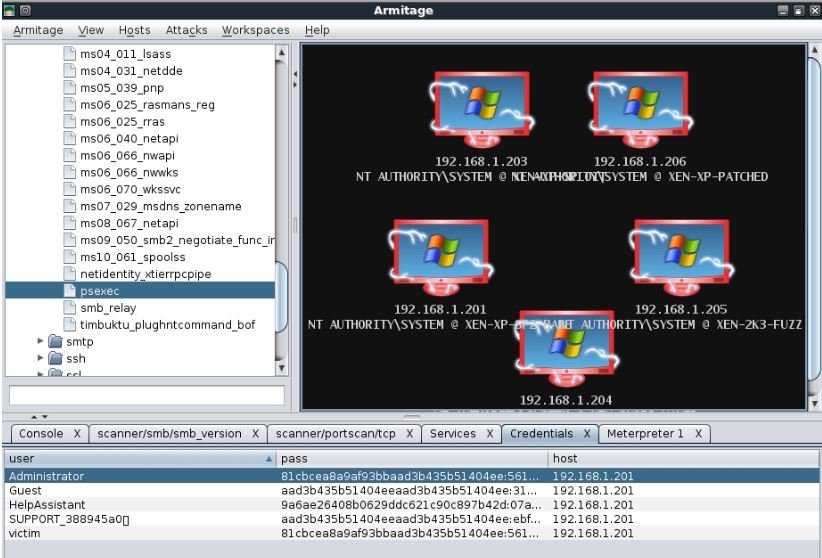
Metasploit Interfaces - Armitage
Note: Metasploit Community & Pro Editions are removed from Kali
Metasploit DB
Why should I use it?
I don't know how to keep track of all my works?
I get confused with Metasploit while working with multiple projects?
I want to import & export results and keep it organized?
-
Open source relational database management system (DBMS ) developed by a worldwide team of volunteers.
-
PostgreSQL is not controlled by any corporation or other private entity and the source code is available free of charge.

Metasploit Database
Metasploit keeps track of everything you have done to the target network within its database.

MSF Database Cmd's

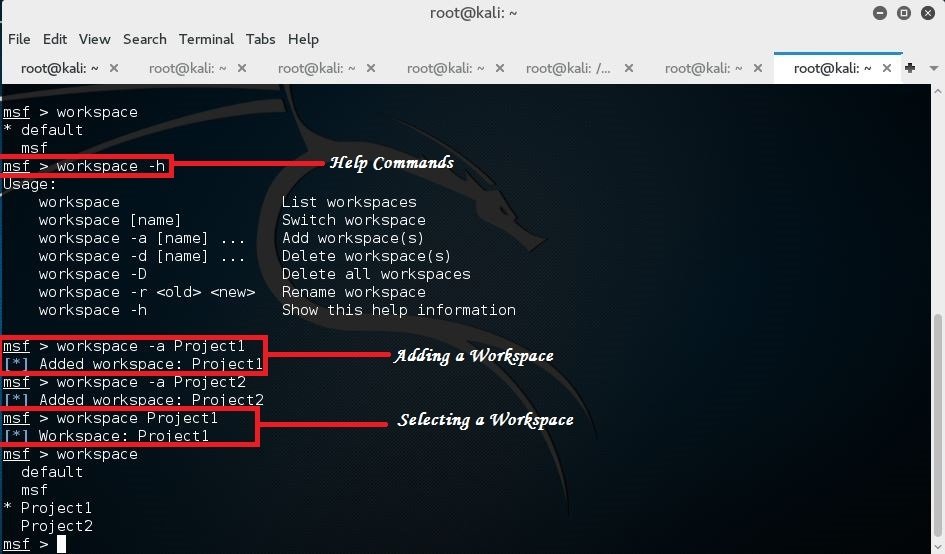
DB Workspaces
Useful to Organize our works in the form of workspaces.
Workspaces
Demo Setup

Kali Linux 2.0


MSF Workspaces
- Using Workspaces
- Importing - Nmap Scan Results
- Scanning - Using db_nmap
- Exporting - Workspace Results
Demo 1 !!!
Hosts & Services
Hosts
Services
- -a Add
- -d delete
- -c Columns
- -u Up
- -o Output
- -R Rhosts
- -S Search
Available columns: address, arch, comm, comments, created_at, info, mac, name, note_count, os_flavor, os_lang, os_name, os_sp, purpose, scope, service_count, state, updated_at, virtual_host, vuln_count
Available columns: created_at, info, name, port, proto, state, updated_at
Demo 2 !!!
Creds & Loot
The ‘creds’ command is used to manage found and used credentials for targets in our database. Running this command without any options will display currently saved credentials.
In the event of a successful hash dump, this information will be stored in our database. We can view this dumps using the ‘loot’ command.
Creds
Loot
Demo 3 !!!
Metasploit DB Usage
By Arunthomas
Metasploit DB Usage
- 2,421


