Week 4
Please sit on the right half of the room
--->
Static Analysis
(Ghidra)
Previously...
- Learned to
- statically triage files
- dynamically triage executables
- dynamically analyze executables
- Today: statically analyze binary files
Why static analysis?
- Introspection difficulties
- Re-hosting difficulties
- Functionality hidden from the debugger
- Long execution delays
- Anti-debugging tricks
- Detection of vulnerabilities
Fundamentally: debuggers only explore a single path of execution. We might want to reason about program logic.
What is a disassembler?
- Previously we used objdump
- Read and interpret the header structure of supported files (ELF, PE, etc)
- Search for strings, symbols, and other metadata
- Detect and disassemble compiled functions
- Lift assembly from multiple architectures into pseudo-c
- Type detection (int, string, pointer, etc)
Disassemblers implement analyses that are helpful when reverse engineering compiled software
Disassemblers
There are many disassemblers, most are either expensive, missing features, or unreliable
- Ida Pro
- Binary Ninja
- Hopper
- Cutter
- radare2
- rizin



Ghidra
- Project started by the NSA in 2003 (iirc?)
- Released as open-source software in 2019
- The only free and robust static analysis tool


User Interface Tour
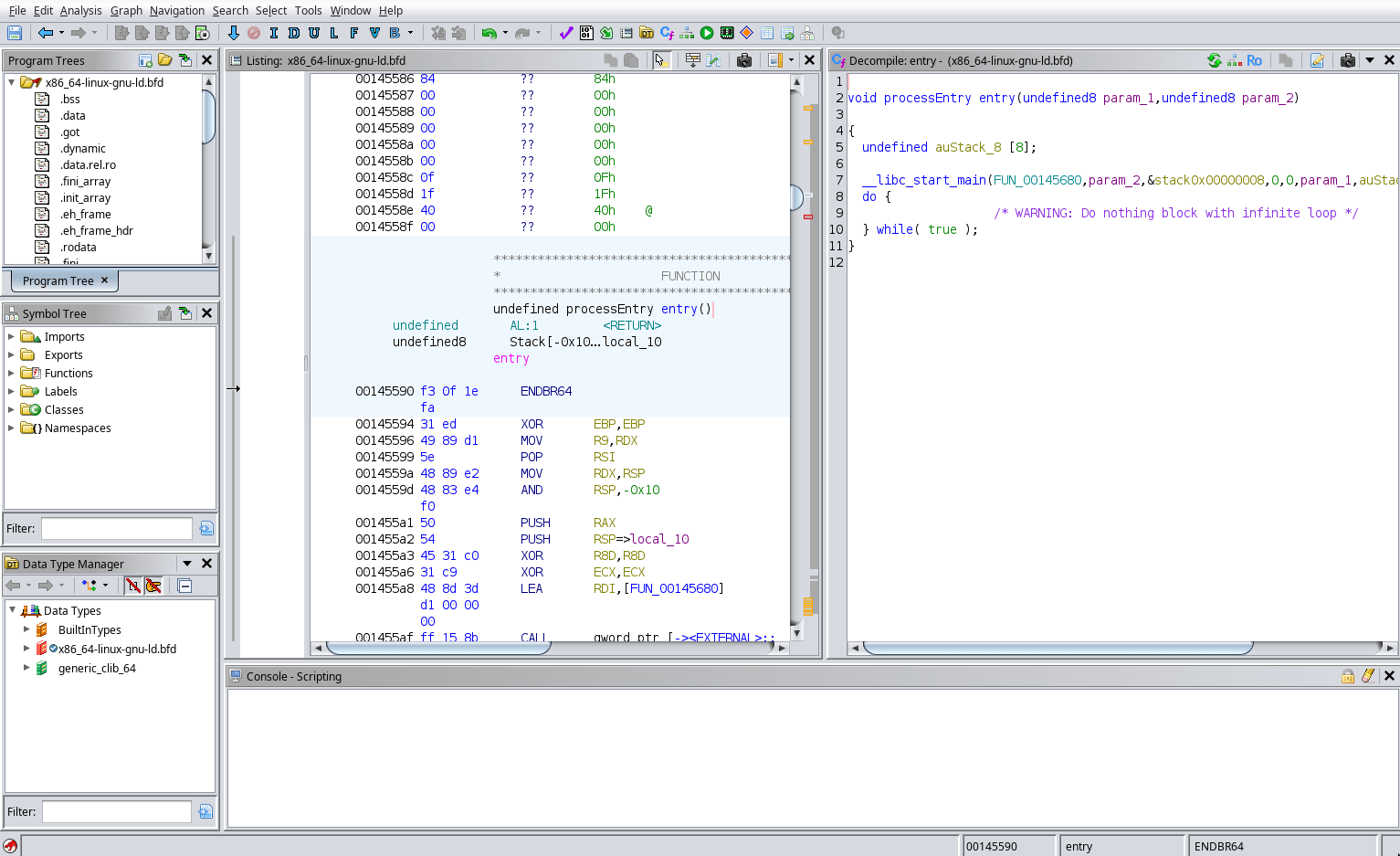
Disassembly
Decompiler
Sections
Functions
Data Types
Console
Toolbar
How the decompiler works
Input Program
Disassembly
CFG Generation
Data flow analysis
Lift to C
Lift to p-code
Expression simplification
Type Inference
Questions?
Demo
Let's statically analyze something as a group
Questions?
Lab 1
Demo / Lab 2
Demo / Lab 3
Homework and Quiz
Week 4
By Chase Kanipe
Week 4
- 212



